Hong Kong Security Watch Report (Q3 2021)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the third quarter of 2021.
Highlight of Report
In 2021 Q3, there were 4,860 unique security events related to Hong Kong used for analysis in this report. Data were collected through IFAS1 , and not from the incident reports received by HKCERT.
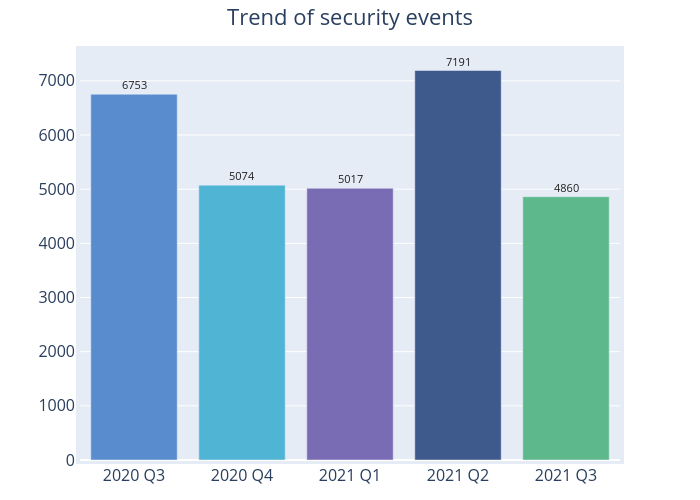
Figure 1 –Trend of security events
There were 4,860 cyber security events in 2021 Q3, down 32% from 2021 Q2 (7,191 events) (Figure 1). Among them, phishing events rose by 49%. On the other hand, Botnet (Bots) and Defacement events reported decreases of 43% and 7% respectively. There was no malware hosting and Botnet [Command and Control (C&C) Centres] event during the report period (Table 2).
Server-related security events
Server-related security events include malware hosting, phishing and defacement. Their trends and distributions are summarised below:
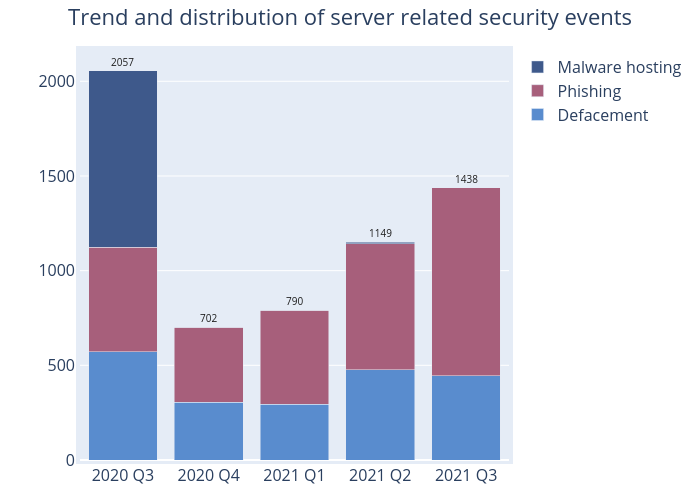
Figure 2 –Trend and distribution of server related security events
| Event Type | 2020 Q3 | 2020 Q4 | 2021 Q1 | 2021 Q2 | 2021 Q3 |
|---|---|---|---|---|---|
| Defacement | 571 | 305 | 295 | 476 | 445 |
| Phishing | 552 | 395 | 495 | 665 | 993 |
| Malware Hosting | 934 | 2 | 0 | 8 | 0 |
Table 1–Trend and distribution of server related security events
There were 1,438 server-related security events in this quarter, up 25% from 2021 Q2 (1,149 events) (Figure 2). As shown in Table 2, the number of phishing sites increased 49% to 993 sites in this quarter. The number of unique IP addresses involved in phishing sites also rose 3% to 232 (Figure 8). The URL/IP ratio went up 46% to 4.28 in 2021 Q3. On average, there were around 4 phishing sites per server (Figure 9).
Among the top 10 top-level domain name of phishing sites, “.org” was the most used domain name, accounting for 30% of all phishing sites (Figure 3). Almost all of the “.org” phishing sites were using a free dynamic DNS service provider. Mobile users were believed to be the targets of these sites since it would be relatively hard to spot the fake URLs in mobile or in-app browsers. The “.com” (29%) came a close second, with “.cn” (10%), “.top” (6%) and “.bar” (5%) rounding off the top five. Other rarely used domains such as “.shop”, “.cam”, “.monster” and “.icu” were also observed in this quarter. Although some of the phishing sites did not use specific well-known top-level domains, they would have the domain name embedded in the text in the URL to trick careless victims, e.g. hxxps://viewsnet[.]jp[.]dygfpq[.]shop/
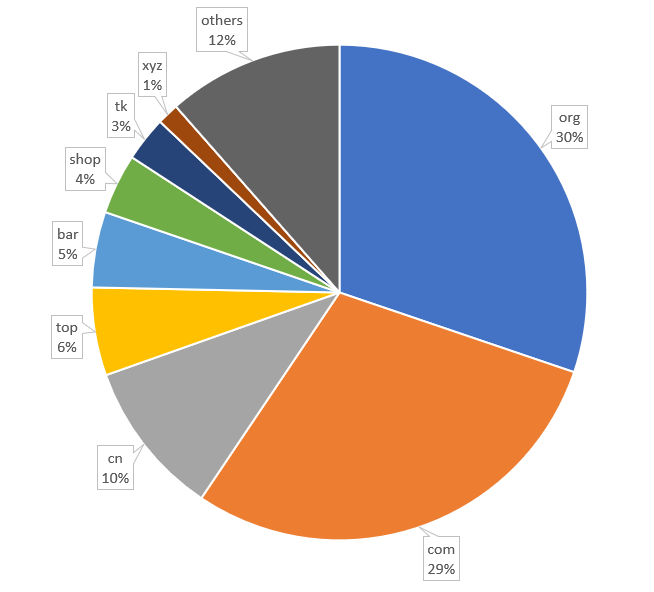
Figure 3: The most frequently used top-level domain of phishing sites
Defacement events fell 7% to 445 in 2021 Q3, while the number of unique IP addresses involved decreased by 2% to 235 (Figure 6). The unique URL/IP ratio also dropped by 5% to 1.89 (Figure 7). On average, there were 2 defacement events in each compromised server.
Among the compromised servers, the open-source “Nginx” platform remained the most targeted web server type (Figure 4) even though security events related to the platform have decreased by 42% to 179 in 2021 Q3. “Apache” came second with 159 events, up 218% from 2021 Q2. Of these two server types, “known vulnerability” and “file inclusion” were the most serious issues. However, it was also noted that the “Configuration / admin. mistake” was another major cause of the compromise. HKCERT urges system administrators of these servers to maintain a proper configuration management database and review the change management process in order to eliminate the risk of human error. Other affected platforms include Microsoft IIS 5.0, 6.0, 7.5, 8.5 and 10.0, Tengine and LiteSpeed.
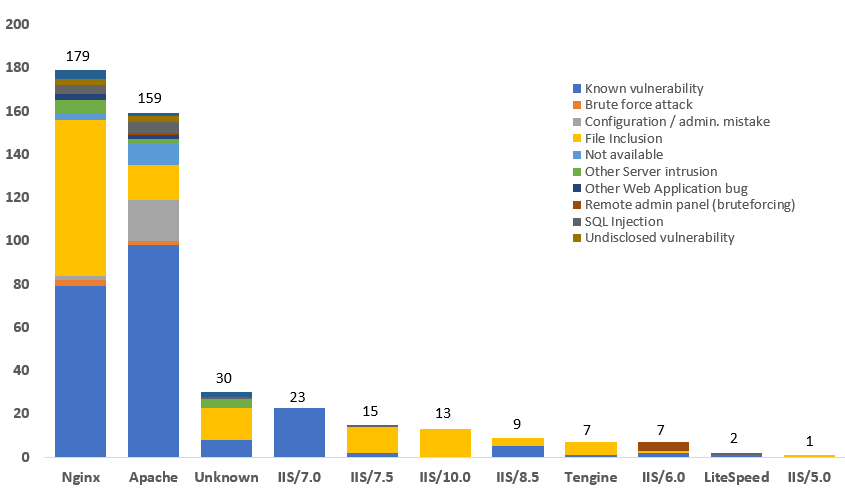
Figure 4: Distribution of operating systems in defacement events
There was no malware hosting security event in this quarter.
| HKCERT urges system and application administrators to strengthen the protection of servers |
|
Botnet-related security events
Botnet-related security events can be classified into two categories:
- Botnet Command and Control (C&C) Centres security events – involving a small number of powerful computers, mostly servers, which give commands to bots
- Botnet security events - involving a large number of computers, mostly personal computers which receive commands from C&Cs.
There was no Botnet Command and Control (C&C) Centres security events in this quarter.
The trend of botnet (bots) security events is summarised below:
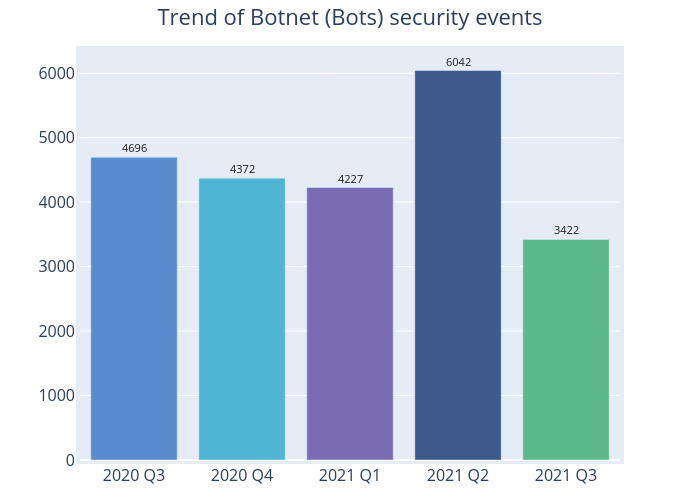
Figure 5 - Trend of Botnet (Bots) security events
The number of botnet (bots) events decreased by 43% to 3,422 in 2021 Q3 (Figure 5). Mirai botnets continued to top the Major Botnet Families in Hong Kong Network despite falling by 10% from 1,713 events in 2021 Q2 to 1,542 events in 2021 Q3. Avalanche (425 events) and Conficker (309 events) were second and third respectively, with the former reporting a decrease of 75% and the latter a 2% increase (Table 3).
The top 5 botnet families in Hong Kong network in this quarter were Mirai, Avalanche, Conficker, WannaCry and Virut (Table 4). They contributed 79% of all botnet (bots) events in this quarter.
| HKCERT urges users to protect computers so as not to become part of the botnets. |
|
| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 Shodan is a search engine for Internet-connected devices: https://www.shodan.io/
Related Tags
Share with


