Hong Kong Security Watch Report (Q2 2021)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the second quarter of 2021.
Highlight of Report
In 2021 Q2, there were 7,191 unique security events related to Hong Kong used for analysis in this report. Data were collected through IFAS1 , and not collected from the incident reports received by HKCERT.
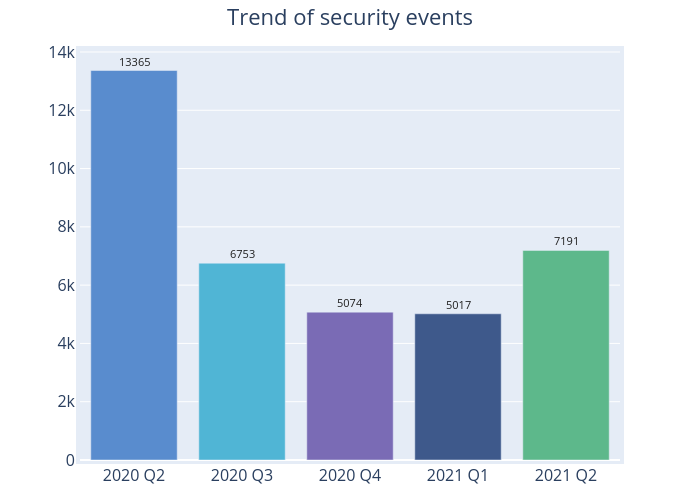
Figure 1 –Trend of security events
There were 7,191 cyber security events in 2021 Q2, up 43% from 2021 Q1 (5,017 cases) (Figure 1). All the security events had recorded increases of around 34% to 61%, except Botnet (C2) event, which had remained zero. Although the number was around half that of the same quarter of the preceding year, it has risen again after having fallen for four consecutive quarters (Table 1).
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trends and distributions are summarised below:
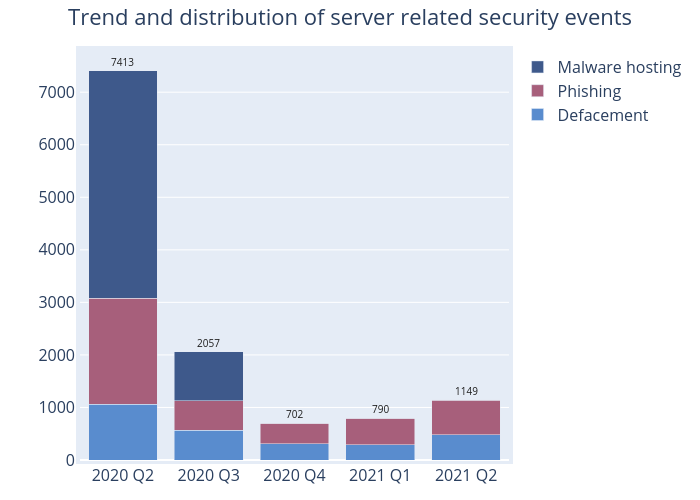
Figure 2 –Trend and distribution of server related security events
| Event Type | 2020 Q2 | 2020 Q3 | 2020 Q4 | 2021 Q1 | 2021 Q2 |
|---|---|---|---|---|---|
| Defacement | 1,062 | 571 | 305 | 295 | 476 |
| Phishing | 2,017 | 552 | 395 | 495 | 665 |
| Malware Hosting | 4,334 | 934 | 2 | 0 | 8 |
Table 1–Trend and distribution of server related security events
There were 1,149 server related security events in this quarter, up 45% from 2021 Q1 (790 cases) (Figure 2). As shown in Table 2, the number of phishing sites increased 34%, from 495 sites in 2021 Q1 to 665 sites this quarter. The number of unique IP addresses involved in phishing sites had also increased ~64% to 226 (Figure 8), almost returning to the same level as 2020 Q2. However, the URL/IP ratio went down 18% from 3.59 in 2021 Q1 to 2.94 in 2021 Q2. It showed on average there were around 3 phishing sites per server (Figure 9). Of these phishing sites, 238 disguised themselves as one of the large online store or cloud service provider (e.g. hxxps://www[.]amazon[.]co-jp-aizmnoanm[.]xyz/, hxxp://amazon[.]storecool[.]cn). And 97 of them abused a free dynamic DNS service and added the name of victim organisation in URL or a well-known social media platform and instant messaging app (e.g. hxxps://dmbugmlbb[.]duckdns[.]org/login/facebook, hxxp://grup-whatsapp186[.]duckdns[.]org/). The hackers were believed to have crafted a fake group chat invitation link to trick the victims into providing sensitive information.
Among the top 10 top-level domain name of phishing sites, “.com” was the most used domain name, accounting for 31% of all phishing sites (Figure 3). “.cn” came second, up from 8% in 2021 Q1 to 23% in 2021 Q2, with “.org”, “.top” and “.xyz” rounding off the top five. Although some of the phishing sites did not use specific well-known top-level domains, they would have the domain name embedded in the text in the URL to trick careless victims, e.g. hxxps://ticxosw[.]cn/www[.]amazon[.]co[.]jp/
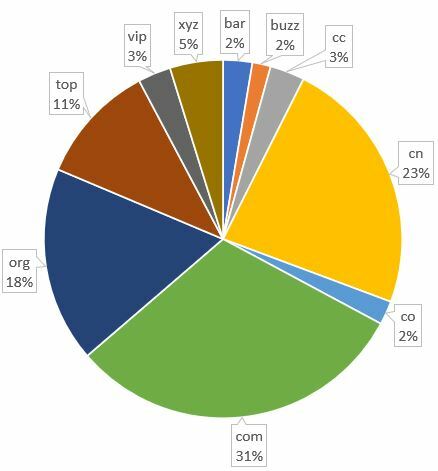
Figure 3: The most frequently used top-level domain of phishing sites
The defacement events increased 61%, from 295 in 2021 Q1 to 476 in 2021 Q2, while the number of unique IP addresses involved rose by 11% from 215 to 239 (Figure 6). The unique URL/IP ratio also went up 45% from 1.37 to 1.99 (Figure 7). On average, there were 2 defacement events in each compromised server.
Among the compromised servers, the open source Nginx platform was the most targeted web server type (Figure 4). Although the version(s) was not known, it was believed that the servers were running an out-dated version as most of them were compromised by the malicious exploit of unpatched vulnerability. The latest two Nginx vulnerabilities were CVE-2017-20005 and CVE-2021-23017 published in June 2021, which affected versions before 1.13.6 and 0.6.18 – 1.20.0 respectively. Remote attackers may exploit these vulnerabilities to trigger remote code execution. The issue of the exploitation of known vulnerability was also observed in all other types of web server with a total of 172 servers suffering from it. Hackers would actively scan for unpatched systems through automated tool and exploit the vulnerabilities found. It showed the security risk of unpatched system was very high particularly for Internet-facing servers. Users are advised to set up a comprehensive patch management policy to cover system inventory and support period, regular vulnerability monitoring or scanning and patch testing and deployment.
The 2nd most frequently used attack technique was “File Inclusion”, a common developer mistake. This is mainly due to developers not validating users’ inputs, allowing hackers to execute code in the hacker-controlled path. Other methods include SQL Injection and brute force attack which can be mitigated by proper input validation and adoption of multi-factor authentication. Apart from outdated software, 21 servers were also running on the end-of-support Internet Information Services (IIS) versions 6.0 and 7.5. HKCERT urges owners of these servers to upgrade the operating systems or migrate to a supported version.
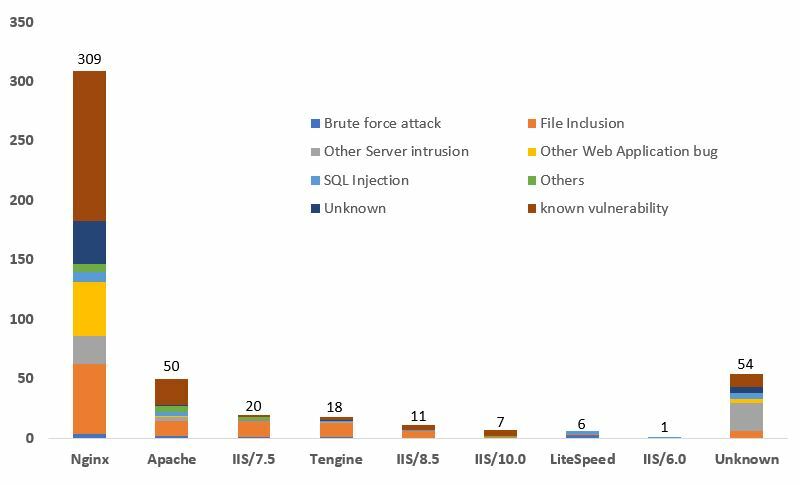
Figure 4: Distribution of operating systems in defacement events
For malware hosting, after no security events were observed in 2021 Q1, there were 8 in 2021 Q2, involving 4 IP addresses (Figure 10). The unique URL/IP ratio was 2 (Figure 11).
| HKCERT urges system and application administrators to strengthen the protection of servers |
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving a small number of powerful computers, mostly servers, which give commands to bots
- Botnet security events - involving a large number of computers, mostly personal computers which receive commands from C&Cs.
Botnet Command and Control Servers
There was no Botnet Command and Control Centres (C&C) security events in this quarter.
The trend of botnet (bots) security events is summarised below:
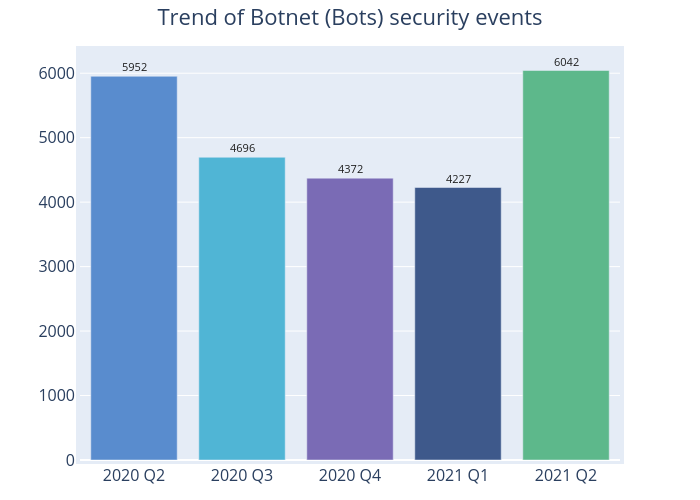
Figure 5 - Trend of Botnet (Bots) security events
The number of botnet (bots) events increased 42% from 4,227 in the last quarter to 6,042 in this quarter (Figure 5). Although the number of Mirai botnets continued to drop, falling by 24.3% from 2,264 events in 2021 Q1 to 1,713 this quarter, it still came top in the Major Botnet Families in Hong Kong Network. The 2nd and 3rd major botnet were Avalanche (1,702 events) and Nymaim (1,392 events), with both of them reporting the largest percentage rises of 266.8% and 559.7% respectively (Table 3).
Nymaim is a high risk trojan which has different variants. Originally designed as a malware downloader, it mainly targets Windows platform. Its most severe impact is that cyber criminals could use it to spread ransomware, one of the most devastating type of cyber attacks in recent years. HKCERT had issued various advisories over the years to remind users of the related security risks and precautionary measures. The latest publication analysed the multi-extortion techniques deployed by cyber criminals. Please visit https://www.hkcert.org/blog/ransomware-keep-evolving-multiple-extortion for more information.
| HKCERT urges users to protect computers so as not to become part of the botnets. |
|
| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 Shodan is a search engine for Internet-connected devices: https://www.shodan.io/
Related Tags
Share with


