Hong Kong Security Watch Report (Q1 2021)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the first quarter of 2021.
Highlight of Report
In 2021 Q1, there were 5,017 unique security events related to Hong Kong used for analysis in this report. Data were collected through IFAS1 with 10 sources of information2, and not collected from the incident reports received by HKCERT.
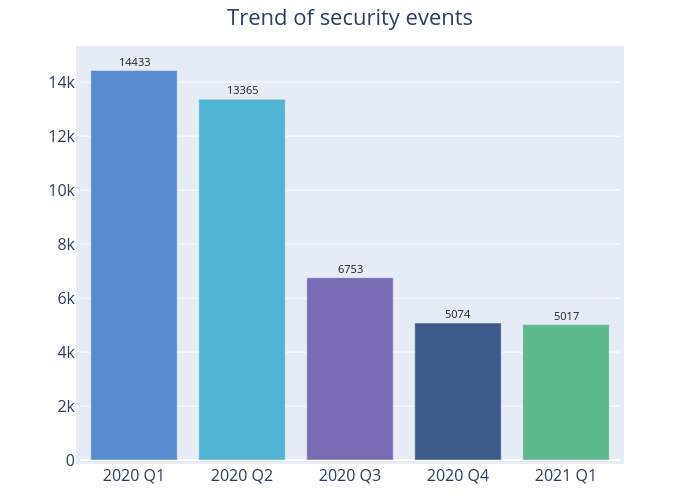
Figure 1 –Trend of security events
There were 5,017 cyber security events in 2021 Q1, marginally down 1% from 2020 Q4 (5,074 cases) (Figure 1). Except phishing sites, all other security events recorded a drop this quarter. Also, for the first time, there was no malware hosting security event (Table 1).
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trends and distributions are summarised below:
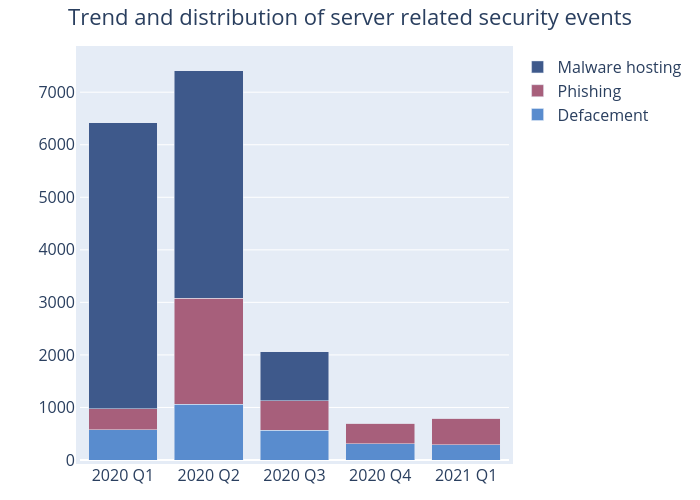
Figure 2 –Trend and distribution of server related security events
| Event Type | 2020 Q1 | 2020 Q2 | 2020 Q3 | 2020 Q4 | 2021 Q1 |
|---|---|---|---|---|---|
| Defacement | 572 | 1,062 | 571 | 305 | 295 |
| Phishing | 399 | 2,017 | 552 | 395 | 495 |
| Malware Hosting | 5,445 | 4,334 | 934 | 2 | 0 |
Table 1–Trend and distribution of server related security events
As shown in Table 1, the number of phishing sites increased by 25%, from 395 sites in 2020 Q4 to 495 sites this quarter. However, the number of unique IP addresses involved in phishing sites fell 7% to 138, similar to that of 2020 Q1. As the number of unique IP addresses decreased, the unique URL/IP ratio went up 35% from 2.65 in 2020 Q4 to 3.59 in 2021 Q1. Of these phishing sites, as usual, most would impersonate financial institutions and online shops. However, over 30 of them were related to cryptocurrency. In addition, the proportion of phishing sites with SSL certificates has risen from 56% in the last quarter to 80% in this quarter. This has become a new norm for phishing sites.
Also, phishing sites using the “.com” domain name came top with 179 of such sites, followed by “.xyz“ with 53. Launched in 2014, the easy-to-remember “.xyz“ domain name has been favoured by hackers due to its low registration cost. Meanwhile, “.cn“, “.buzz“ and “.org“ occupied third to fifth places and only one phishing site used “.hk“ domain name.
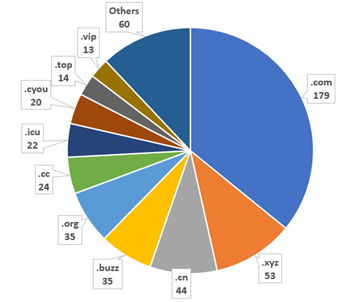
Figure 3: The most frequently used top-level domain of phishing sites
Against last quarter, although defacement events decreased slightly to 295, the number of unique IP addresses involved rose by 35% to 215. The unique URL/IP ration dropped 29% to 1.37. The increase of IP addresses reflected that more servers have been compromised which might be related to unpatched vulnerabilities in software. HKCERT has issued several bulletins of vulnerabilities in operating systems and content management systems and their handling methods in 2021 Q1, and urges server administrators to subscribe its Security Bulletin to get the latest security information (https://www.hkcert.org/getrss).
Also, from the statistics, most of the compromised servers were running on the open source and free Linux operating systems, though some were still running Windows 2003 and Windows 2008 versions which had already reached end-of-support. Since the manufacturer would no longer release security updates for them, the servers would become more vulnerable to cyber attacks. HKCERT urges owners of these servers to upgrade the operating systems or migrate to a supported version.
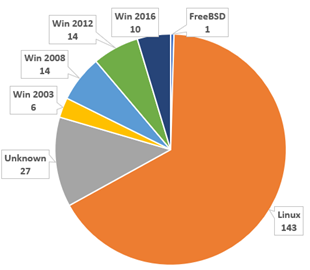
Figure 4: Distribution of operating systems in defacement events
There was no malware hosting security events in this quarter.
| HKCERT urges system and application administrators to protect the servers. |
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving a small number of powerful computers, mostly servers, which give commands to bots
- Botnet security events - involving a large number of computers, mostly personal computers which receive commands from C&Cs.
Botnet Command and Control Servers
The trend of Botnet C&C security events is summarised below:
There was no Botnet Command and Control Centers (C&C) security events in this quarter.
Figure 5 –Trend of Botnet (C&Cs) related security events
The trend of botnet (bots) security events is summarised below:
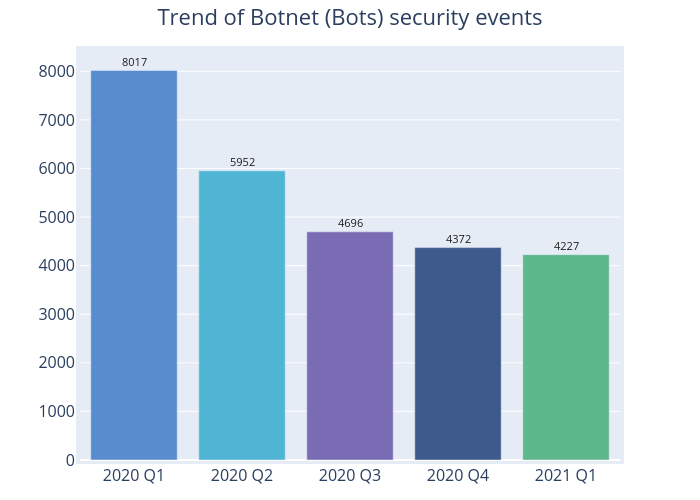
Figure 6 - Trend of Botnet (Bots) security events
The number of botnet (bots) event only decreased by 3% from 4,327 in the last quarter to 4,227 this quarter (Figure 6). Although the number of Mirai botnets has decreased continuously, falling by 19.2% from 2,801 in 2020 Q4 to 2,264 this quarter, it still came top in the Major Botnet Families in Hong Kong Network. Nymaim, Zeus and Avalanche had the largest percentage rises with increases of 276.8%, 130% and 43.2% respectively. Avalanche even climbed to second in the major botnet table
Most botnet families have recorded a decrement. The top 5 botnet families are Mirai, Avalanche, WannaCry, Conficker and Bymaim, accounting for 84% of the total count.
Avalanche botnet first appeared in 2009. Infected devices would receive commands from the server to conduct malicious activities (e.g. sending out fraudulent emails, conducting money laundering activities). In order to hide the server’s actual locations, it would make use of proxy server as well as “double fast flux” techniques, i.e. changing both DNS and IP address of a malicious domain every 5 minutes, for infected devices to connect to the platform. A device infected with Avalanche may also be subject to other cyber attacks, such as theft of banking and credit card information, ransomware, unauthorised access, etc. The compromised device may also be used to launch distributed denial-of-service (DDoS) attacks. In case of infection, please refer to the HKCERT guideline for handling and prevention:
https://www.hkcert.org/blog/hk-victims-reported-in-global-takedown-of-avalanche-cybercrime-hosting-platform
| HKCERT urges users to protect computers so as not to become part of the botnets. |
|
| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 Shodan is a search engine for Internet-connected devices: https://www.shodan.io/
Related Tags
Share with


