All-Out Anti-Phishing

All-Out
Anti-Phishing
Handle Messages Carefully
Most people are easily misled by the "juicy" content, which leads them to follow the sender's instructions and ultimately be deceived.
Act CarefullyWhy Do Hackers Like To Use Phishing Attacks?
The cost and technical barrier are low, but the benefits are high and are difficult to track.
Know MoreHackers Technique
The core of phishing attacks, like deception, is a psychological game.
Psychological weaknessesRelated Knowledge
The Importance of Personal Information, HKMA Response to Phishing Attacks Targeting Banks and More
Learn MoreWhat Is Phishing Attack?
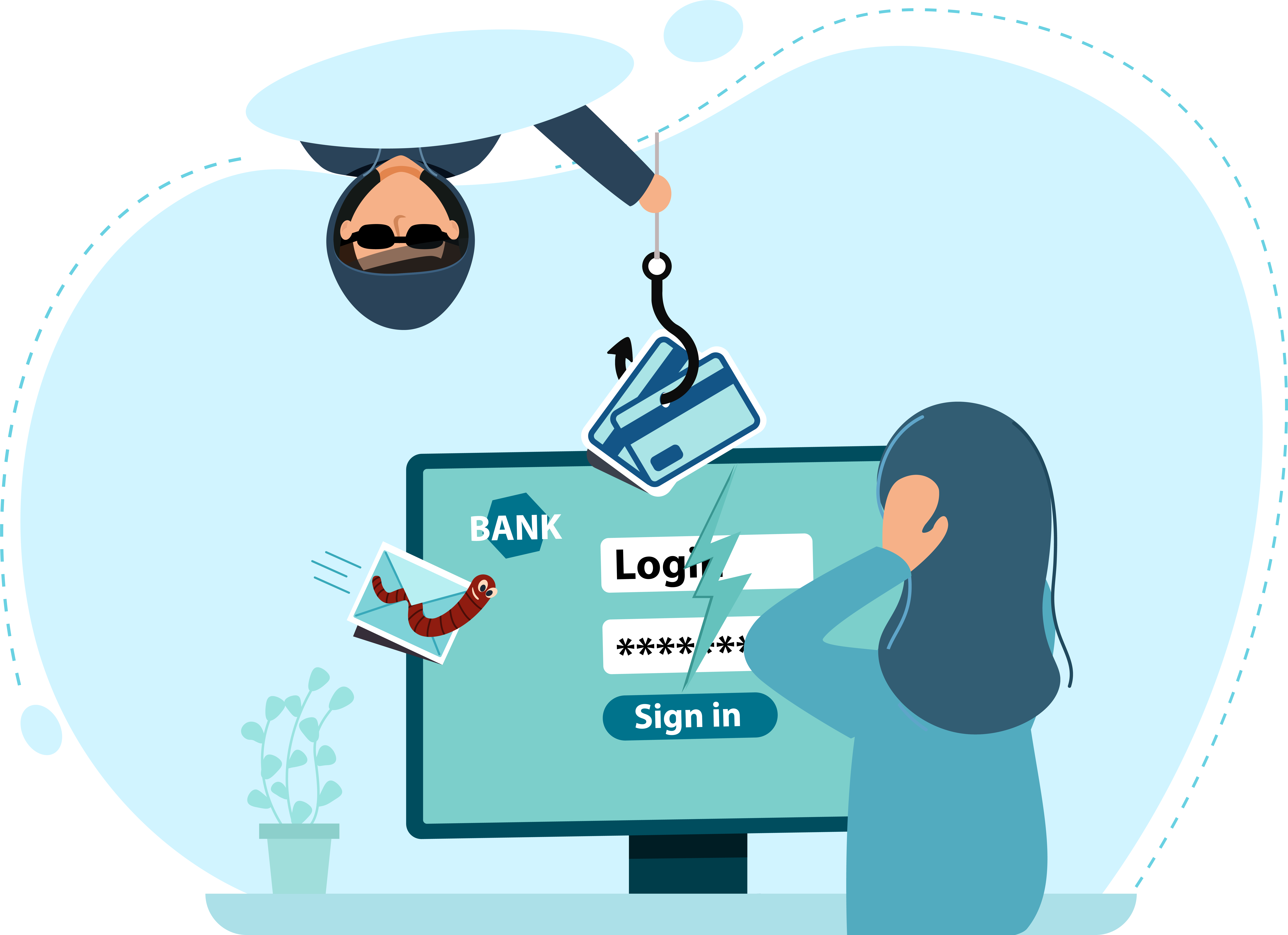
Phishing attack is one of the most common "scams" on the internet. Scammers will impersonate others or companies, and then send various cleverly crafted messages, even using threats and enticements, to trick victims into clicking malicious links, downloading suspicious attachments or providing sensitive information unconsciously such as credit card information, identity information, account passwords, etc.
Phishing attacks have always been one of the most common cyber-attacks encountered by the public. Have you ever seen any suspicious messages when reading an email or using a smartphone?
Below are some examples:
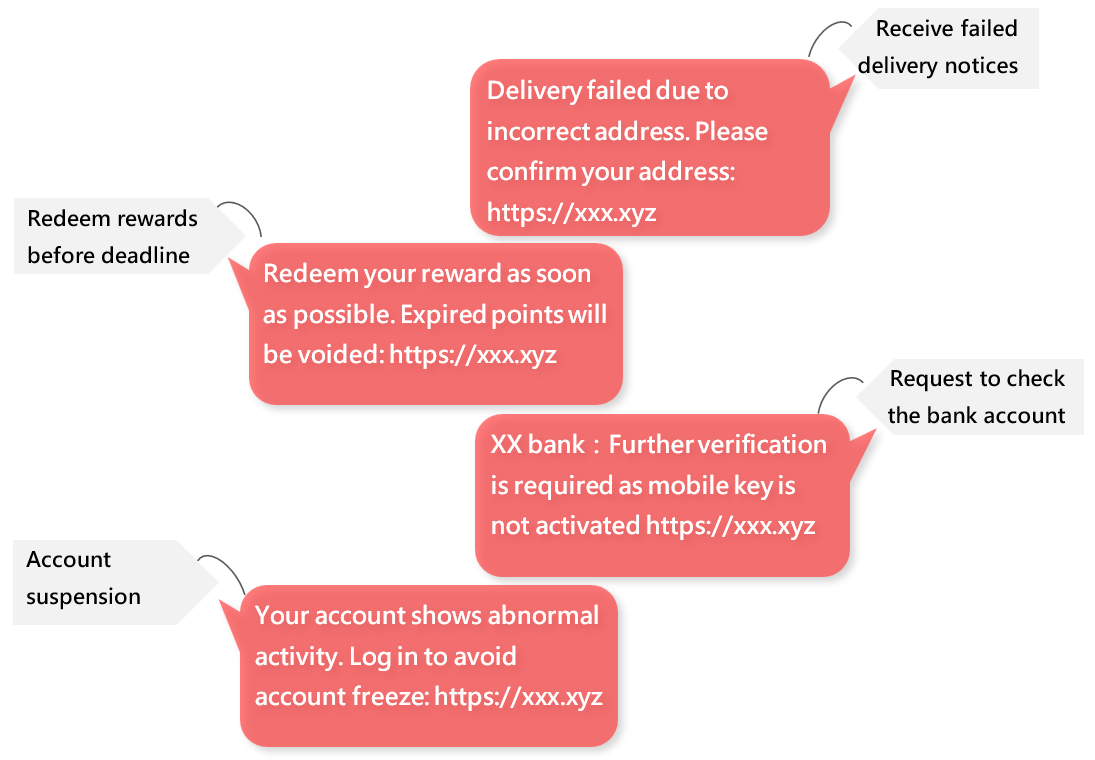
Messages usually have a link that takes you to a fake website that looks similar to a certain organisation's website. Usually, these kinds of fake websites only have one function, which is to ask for personal information such as account passwords or credit card numbers. This is a typical phishing attack!
Among the security incidents handled by HKCERT every year, incidents involving phishing attacks have always been among the top. Scammers know how to create fake messages using hot or juicy topics, and they are also familiar with bypassing security measures. Therefore, new and fake content and websites appear daily.
Why is it called a phishing attack?
The term "phishing" first appeared in an American publication, “2600: The Hacker Quarterly”, in 1996. It is spelt with "Phreaking" and "Fishing", and hackers hope to deceive users through this spelling error. The term “fishing” is a metaphor because the methods used by hackers are similar to the fishing activity: They first impersonate someone else and send fake messages to the target group like “a fisherman casting a net” and then wait for the target to fall into the trap.
The world’s earliest phishing attack
This type of attack has existed since the existence of the internet. Some early phishing attacks could be traced back to the late 1990s.
At that time, hackers used AOL's instant messaging tool to impersonate AOL employees and sent users fake messages pretending official, asking them to provide personal information. These early phishing attacks may be one of the earliest known examples.
What other forms of online "scams" are there? How are they different from phishing attacks?
Just like in the real world, many cybercriminals are looking to deceive others for personal gain. Other scam techniques include fake online stores, counterfeit trademarks, fake buyers, fake investments, online lover scams, fake job advertisements, fake information, and many more.
Unlike phishing attacks, these types of cases sometimes require direct contact with the victims, which increases the chance of being caught or exposed. However, phishing attacks are generally more indirect, and criminals will wait for the right time to use the stolen information to commit the crimes, such as using stolen credit cards for purchases or illegally accessing online banking or company accounts to divert funds.
Cyber Scammers vs Hackers
Cyber scammers are people who use computers or the Internet as a channel to commit fraud and make a profit.
Hackers, on the other hand, generally refer to people who use computer technology to invade systems or obtain information. Among them, there are white hat (security experts) and black hat (criminals) hackers, but this article will not provide a detailed explanation. Readers can search for information on their own.
The difference between cyber scammers and hackers lies in the methods used by the criminals to achieve their goals.

Why Do Hackers Like To Use Phishing Attacks?
The cost and technical barrier are low, but the benefits are high and are difficult to track.
Templates of fake messages, software for establishing fake websites, tools for generating fake domains, overseas hosting services, and emails or phone numbers of the targeted groups can all be easily found or purchased on the Internet anonymously or with a fake name. After sending a large number of phishing messages, all the hackers need is to wait for the victims to fall into the trap, without the need for direct contact, making it difficult to track.
The Targets
Credit card information, which can be used for transactions;
Account passwords, which can be used to gain access to systems of the organisations to steal confidential information or destroy data;
Personal information such as ID, phone, address, etc., which can be used to impersonate the victim;
Social platform passwords, which can be used to fully control victims’ accounts to post false comments or delete data;
Moreover, many fake websites are hosted overseas. Even if the victim organisation quickly discovers and reports it, the organisation still needs to take time to contact the relevant overseas’ organisations for assistance. Many people have already fallen victim unknowingly. Even the phishing website has been taken down, hackers can launch another phishing campaign easily.
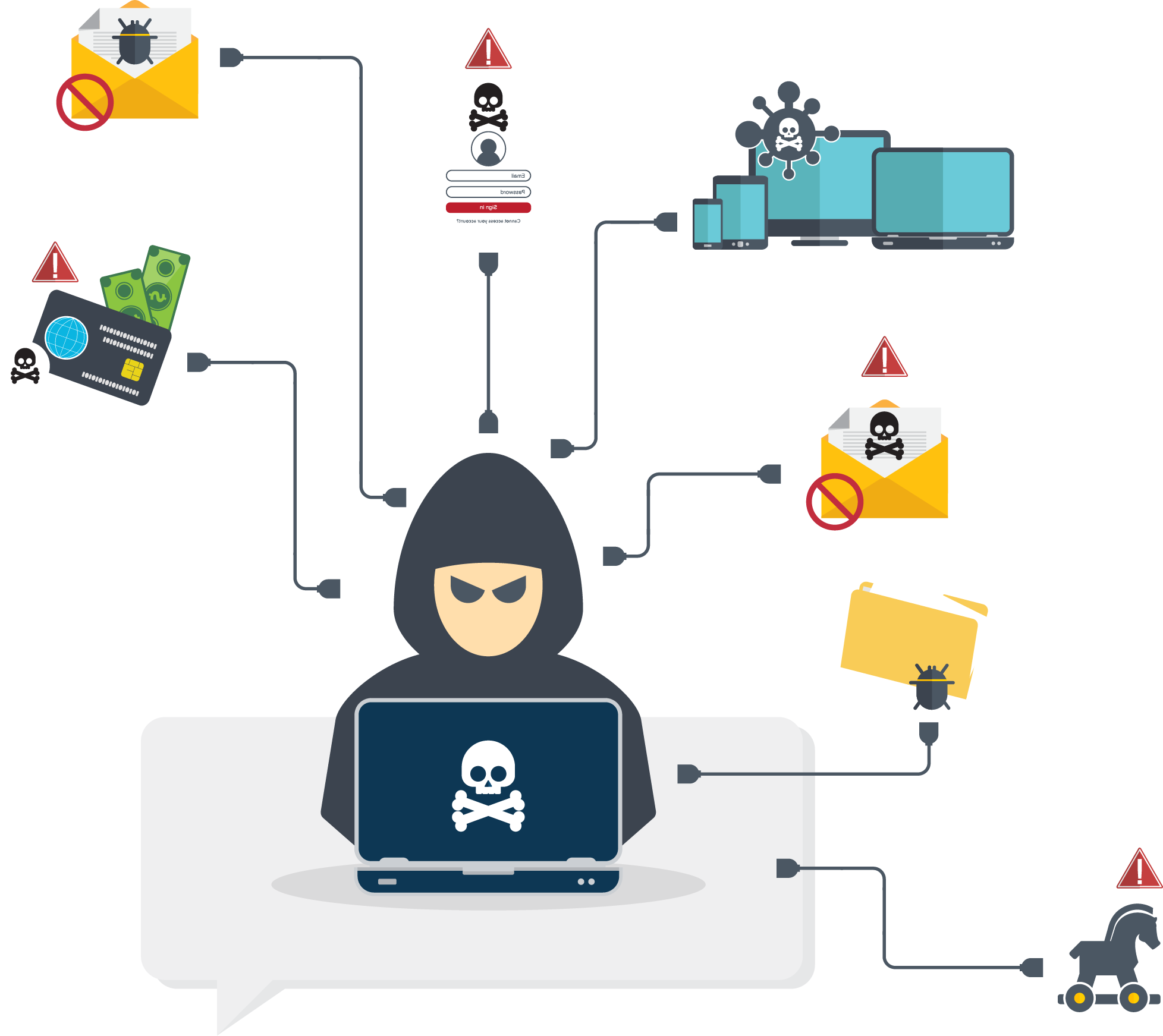
Attack Methods And Channels
Any communication channels can be used for phishing attacks. The following communication methods are some examples:
- Instant messaging such as SMS, WhatsApp, etc.
- Social media platforms
- Online advertising
- QR Code
- Phone
error
Warning
How do hackers obtain our email addresses or phone numbers?
- Collect from the Internet, for example, many users set their contact information as public on social media platforms. In addition, they can also be collected from the telephone directory of organisations.
- Data breach of any organisation.
- Data leaked by any earlier phishing attack.
- Black market, where hackers can buy data stolen by other hackers.
error
Hint
🏫 In addition, there are other forms of luring users to phishing websites, such as websites that have been compromised and have fake links inserted, compromised domain name servers, and Wi-Fi hotspots set up by hackers.
ℹ️ With help of AI, hackers use generative AI tools, such as ChatGPT, to create the content of phishing emails, looking more alike the official one. Apart from making phishing emails, hackers use AI or deepfake to generate vishing (i.e. voice phishing attacks), zishing attacks (i.e. use deepfakes on Zoom in phishing attack). A fraud case occurred in Anqing, China in Apr-2023. The scammer used deepfake to pretend an acquaintance of the victim in a video call, making the victim relax his vigilance and commit fraud.
ℹ️ Another less commonly used method is to directly request sensitive information in an email.

Technique
In simple terms, the core of phishing attacks, like deception, is a psychological game. It involves utilizing the weaknesses of humans, luring victims to trust the criminals, and voluntarily handing over sensitive information.
Hackers will find ways to break through and blur our weaknesses in "trust". Since everyone's weaknesses are different, even the same or similar tactics can always have victims who fall for them.
error
Note
Psychological weaknesses
- Exploiting human nature such as desire for small gains, anxiety/fear, as well as curiosity and self-esteem.
Cognitive weaknesses
- Insufficient self-protection awareness, such as not understanding the purpose and importance of personal information, and not realising that the online world is just as "dangerous" as the real world.
- Lack of knowledge, such as not being able to distinguish between genuine and fake messages and websites, and not knowing the latest techniques used by hackers.
Bad cyber hygiene
- Habitually opening any links and attachments in messages.
- Determining the authenticity of a website based on its appearance, but not other important details.
error
Note
🪄Example
A hacker sets up a fake website, claiming that entering personal information will receive valuable prizes. If only a name is required, most people would likely fill it in; if a phone number and email address are also needed, perhaps half of the people would be hesitant; if the hacker further demands an address and proof of identity, everyone would begin to question whether it is worth trusting.
This is related to our understanding of the importance of personal information and to our risk management. For example, if just providing a name and telephone number gives a chance to be offered a coupon, most users would think that even if the party is a scammer, having their names and telephone number stolen are not a big deal. As a result, they would judge the potential benefits outweigh the potential risks, and therefore, most people would "fall in the trap" and be lured in.
Potential Benefits/Impact Outweigh Suspicion
Hackers falsely claim significant potential benefits/impacts to lower our suspicion: They don't use any special techniques, but put effort into the content, making it closer to people's psychological weaknesses and market environment. The most common method is to impersonate familiar organisations or individuals, imitating their websites, emails, or instant messages to contact us.
- Pretend your supervisor, colleague, business partner, or an organisation to issue instructions, share file links, or send document, such as:
- "The payment is overdue; please settle the outstanding payment within 3 days."
- "Thank you for your purchase; we have received your payment. Please check the attached receipt."
- "Your colleague has shared a file with you."
- "Job offers from our company."
- Make up an emergency situation that leave us no time to verify the legitimacy, such as:
- Threatening - "Your phone bill is overdue; please pay immediately, otherwise your account will be suspended."
- Urgency - "Last day for the special offer for selected customers; log in now to claim."
- Emergency - "Your credit card points are about to expire; redeem now!" or "You have a package not picked up; please pay the additional charge within 3 days."
- Create phishing messages based on hot topics, such as:
- Curiosity - "Sign up now to join the cryptocurrency analysis channel."
- Offers - "First 3 months free trial."
Taking Hong Kong as an example, recent phishing attacks have mainly targeted some well-known loyalty programs, luring victims to click on fake websites in phishing messages by claiming that their rewards are about to expire.
In addition, there has also been an increasing trend of phishing attacks impersonating telecommunications companies recently, which may be due to the impact of the Real-name Registration Programme for Subscriber Identification Module (SIM) Cards.

How to Prevent Phishing Attacks?
There are many security tools available for preventing phishing attacks. As long as we use them properly, we can greatly reduce the risk and impact of phishing attacks.
error
Note
Make use of Anti-phishing features in email and browsers: Email service provider will automatically detect phishing email characteristics and block them; When accessing web pages, browsers will analyse URLs. If it's a phishing site, a warning page will pop up, advising users not to browse.
- Make use of the "Report Phishing" function of the mail client software, and the email system will record and block the subsequent message.
- DO NOT browse any webpage which marked as "Suspicious" by the browser.
- Enable the "Block pop-ups" function of browsers to block the malicious online ads or unsolicited login request.
Enable multi-factor authentication to enhance account security: Online service providers implement multi-facor authentication requiring users to enter verification codes or additional authorization to log in, preventing account theft if the users accidentally disclose their password.
- Enable multi-factor authentication and do not share the verification code to the others.
- Do not reuse the same password across different accounts.
Update your system and antivirus software frequently: Phishing message sometimes attach or lead to the download of malware. These malwares may exploit system vulnerabilities to infect affected systems.
- Set up automatic update for computers, mobile devices, broswers and anti-virus softwares.
- If any software support automatic update function, it should be enabled. Otherwise, you should always check whether there is an update available. Commonly used software usually release an update every month.
- Stay tuned to HKCERT website or Facebook to obtain the latest security bulletins.
Verification platforms: It allows the public to check whether the link or email address is suspicious.
- Use reliable online platforms to check if links or email addresses are suspicious. If deemed suspicious, DO NOT reply or click the link in the email.
Participate in Anti-Phishing drill: Familiarize yourself with the charactisitcs of phishing messages and how to deal with them correctly.
- Organizations can regularly organise drills and provide latest security information for employees to enhance their ability to identify phishing messages and encourage them to report suspicious messages they receive.
- Test your knowledge of phishing attacks by completing the phishing quiz at the bottom of this page.
error
Note
Why We Should Not Rely on Technology to Prevent Phishing Message?
No. On the contrary, without the help of technology, we would receive much more phishing messages. But...
As the Chinese saying goes, "As virtue rises one foot, vice rises ten". Hackers evolve with time and find new vulnerabilities, such as:
- Targeting specific groups with phishing content, makes it difficult for security systems to collect enough data to determine authenticity.
- Concealing phishing links in images or malicious code.
- Increasing attachment file sizes to try to bypass malware scanning systems.
- Using shortened links to hide the real phishing link.
- Pretending replies (i.e. reply-chain attack) or adding a lot of meaningless text to phishing messages to confuse security systems.
- Hijacking users' email accounts to send phishing messages and deceive their friends and colleagues.
- Using fake domain names that resemble the target organisation for phishing links.
- Phishing messages or websites have not been reported.
- To balance security and usability and prevent legitimate emails from being blocked, system administrators generally do not set the highest security level, but the side effect is that some phishing emails may enter users' mailboxes.
- Computer data may not be updated in time, making it unable to recognize the latest phishing sites.
- Other communication channels like SMS have varying security levels and are more vulnerable.
error
Warning
❌ Common Misconception vs ✔️ Reality
❌ Phishing attacks come from computer systems and they should be more effectively detected by security systems instead of humans.
✔️ Security systems already effectively block most phishing messages, but users still need to handle those that bypass the security measures
❌ Users are not security experts and should not have to take on additional responsibilities for cyber security.
✔️Cyber security is the responsibility of every user. And in fact, you are protecting yourself.
❌ Technology should reduce manual work, users should not have to verify the authenticity of messages manually.
✔️ AI may achieve this goal perfectly in the near future. But for now, users should continue to learn how to verify the authenticity of messages.

How To Detect Phishing Attacks?
In general, phishing messages are often disguised as other organizations or individuals to gain trust and deceive people. However, due to technical limitations, some areas cannot be completely imitated, users can identify suspicious messages by paying attention to details.
Many grammar or spelling errors in content
Phishing messages may contain poor English grammar, incorrect words, mixed traditional and simplified Chinese, typos, and disorganized formatting.
- Reason:Hackers use the same phishing message to attack users from different countries and rely on translation software to convert it to Chinese or English, resulting in varying quality.
- Reality:Messages sent by legitimate organisations to users are generally proofread, so there are few instances of obvious grammar errors or disorganized formatting.
Misleading or unfamiliar links
To make the phishing links look more real, hackers use the target organisation’s look-alike domain names to confuse users, such as hkcert852.org, hlcert.org, hkcert.xyz, hkcertorg.dyndns.org, etc. Another method is to use URL shortening services to create short versions of the links, like tinyurl.com/ydehjpnm, making it difficult to distinguish between real and fake.
- Reason:Due to technical limitations, hackers cannot use an organisation's domain name in a phishing attack. For example, they cannot use hkcert.org as a phishing link.
- Reality:Organisations have dedicated domain names that usually include the organisation's name and the nature of their business for branding purposes. They will not use other domain names to provide online services.
Unfamiliar senders or suspicious email addresses
Using other email addresses, such as [email protected], [email protected], [email protected], or directly using free email services like gmail.com.
- Reason:Email security systems have mechanisms to check the sender and will block emails impersonating other organisations.
- Reality:Similar to website links, organisations have their own dedicated domain names with their names for branding purposes. They will not use other domain names as email addresses.
Using urgent or intimidating headlines
Impersonating authoritative organisations, such as governments, law enforcement agencies, and financial institutions, using urgent or threatening words to induce panic in victims and prompt them to follow instructions.
- Reason:Please refer to the "Technique" section above regarding "Psychological Weaknesses".
- Reality:Organisations generally treat their customers politely; if there is any special situation requiring notification, they usually provide detailed explanations and ways to inquire. The website links will also be the correct official websites.
error
Hint
- Generally, organisations' online services will register a unique dedicated domain name using their organisation's name, business nature, and region. For example, our centre uses "hkcert" as the beginning part of the domain name; the tail part for commercial organisations is usually ".com," non-commercial organisations use ".org," government departments use ".gov," and those located in Hong Kong will add ".hk," etc.
- Since domain names cannot be impersonated, hackers can only use similar domain names to mislead users. In other words, checking domain names is one of the effective ways to detect phishing attacks.

Handle Messages Carefully
Most people read the title of a message first, and they are easily misled by the "juicy" content, which leads them to follow the sender's instructions and ultimately be deceived. However, we suggest that users should:
Check the sender's email address domain
If the sender's email domain is different from the official domain of the organisation they represent, there is a high chance that it is a phishing email. If a public mailbox is used to represent the organisation, users should pay extra attention, as large organisations generally would not do this. If the email is from an unfamiliar organisation, it is best to call the organisation to verify the sender's identity.
Always remember "There's no free lunch"
Don't let excitement, urgency, or panic override your judgment. Remember that in the online world, as in the real world, overly favourable offers don't happen for free.
Conversely, organisations generally do not send notification messages without detailed explanations or in a threatening manner with severe consequences, and then attach a link for customers to click on.
Check the link domain in the content
Misleading links or links that do not match the organisation's name are very likely to lead to phishing websites. The official domain of an organisation cannot be impersonated; hackers can only mislead users by making a fake link similar to the real one. For example, hkcert852.org, hlcert.org, hkcert.xyz, hkcertorg.dyndns.org, etc., are all not our centre’s official domain. Another technique is using look-alike characters or other language alphabets to confuse users, for example, “1” to pretend “l” (a lowercase of “L”), “0” to pretend a letter “o” or “O”, using Cyrillic alphabet “а” to pretend the English alphabet “a”, etc.
error
Warning
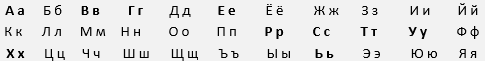
What is Cyrillic alphabet?
It is used by various Slavic (e.g. Russia), Turkic, Mongolic, Uralic, Caucasian and Iranic-speaking countries. Below are the examples of Russian Cyrillic alphabet. The highlighted letters look the same as English letters:
The free search tool " Scameter" launched by "CyberDefender" can identify scams and online traps. It supports checking email addresses, URLs, and IP addresses, and the results will be displayed in different colour warnings.
Check the website you are led to
Double-check the URL domain displayed in the browser for any suspicious elements.
Although the appearance of a phishing website may be identical to the official one, it usually lacks functionality or content, for example, clicking on other pages within the site might result in error messages, or the site contains outdated information. These situations are considered suspicious.
If there is any suspicion, do not open any link or attachment in the message (including those from emails, SMS, WhatsApp, social media posts, etc.) or provide any information to suspicious websites.
Then report the issue to us and delete the related message.
What Can You Do If You Fall Victim?
- Change the passwords for all compromised accounts and contact the relevant service providers to report the incident.
- Set different account passwords for different services.
- Suspend the stolen credit card.
- Closely monitor your accounts for any suspicious transactions or activities.
- Watch out for any suspicious instant messages, impersonating your identity.
- Report to HKCERT.
- Enable two-factor authentication.

Related Knowledge#1
The Importance Of Personal Information
Compared to financial information, such as credit cards and bank accounts, the general public has a lower awareness to personal information protection. This is because we often need to provide personal information in our daily lives, such as opening accounts, registering for promotions, and online shopping. The disclosure of this information seemingly has no consequences.
error
Note
📖The Personal Data (Privacy) Ordinance
According to The Personal Data (Privacy) Ordinance, Personal Data means information which relates to a living individual and can be used to identify that individual. It must also exist in a form in which access to or processing is practicable.
However, this is only because the information you provide is used legitimately by authorized organisations. If the information is obtained by cyber criminals, they can:
- Impersonate your identity to conduct illegal activities
- Hijack accounts to manipulate transactions or steal other information
- Invade personal privacy
Therefore, protecting personal information is extremely important.
Related Knowledge#2
HKMA's Response to Phishing Attacks Targeting Banks
Users' online banking accounts have always been one of the targets for hackers. Hackers impersonate banks to send phishing messages and create fake websites to deceive users into providing login information, then manipulate their online accounts. Often, when users receive messages claiming to be from banks, they tend to become more anxious and less suspicious, making it easier for them to believe the messages are genuine.
Hong Kong Monetary Authority (HKMA) has issued regulatory requirements to banks, requiring banks not to use SMS or email hyperlinks to direct customers to any websites or mobile applications for transactions. Moreover, they are not allowed to request any sensitive personal information (including login passwords and one-time passwords) through hyperlinks.
error
Note
 Messages from Banks
Messages from Banks
Check your bank's SMS messages and other messages in a timely manner and verify your transaction records. Inform your bank immediatelt in case of any suspicious situations, regardless of the amount. Banks will not ask for any sensitive personal information (including passwords) through phone calls or emails.
https://www.hkma.gov.hk/eng/smart-consumers/internet-banking/#using-internet-banking-servicesIn a press release issued in July 2021, HKMA and the Hong Kong Association of Banks once again reminded the public that banks would not use SMS or email hyperlinks to direct customers to websites and apps for transactions or to provide personal information.
error
Note
In accordance with the HKMA’s supervisory requirements, banks will not send SMS or email messages with embedded hyperlinks directing customers to their websites or mobile applications to carry out transactions. Nor will they ask customers to provide sensitive personal information, including login passwords and OTPs, via hyperlinks. So if members of the public receive SMS or email messages with embedded hyperlinks requesting them to input internet banking login credentials, these messages should not originate from banks. The public should think twice before clicking any hyperlinks purportedly sent by banks.
https://www.hkma.gov.hk/eng/news-and-media/press-releases/2021/07/20210706-3/We suggest that if citizens receive messages and links claiming to be from banks, which directly prompt users to conduct transactions or provide personal information, they should verify and report this to the relevant bank.
Citizens can also pay attention to the fraudulent website announcements issued by HKMA and banks to learn more about fake bank websites and avoid losses.
Related Knowledge#3
Phishing Attacks Also Highlight the Issue of Reusing Passwords
With the increasing digitalisation of businesses, we have more and more online accounts. Many platforms use the user's email address and a self-defined password as authentication. Some people use a Password Manager to record account passwords, but some users, to avoid hassle and forgetting passwords, have the bad habit of setting the same password for different accounts.
If a user accidentally falls for a phishing attack and exposes their account and password, hackers can use this stolen login information to attempt to access the user's other accounts, causing cascading losses. If the user also sets the same password for internal company systems, it can even give hackers the opportunity to infiltrate the company, with serious consequences.
We suggest users:
- Do not reuse passwords and change them regularly.
- Keep passwords absolutely confidential; do not share them with anyone and beware of phishing attacks.
- Enable multi-factor authentication to enhance account security.
Phishing Example and Quiz
We compiled some examples of phishing messages and webpages into the following collection, and also made a quiz, hoping to deepen users' understanding of phishing attacks and prevent accidents.