FAQ
Information Security refers to all aspects of protection for information. Most often, these aspects are classified in five categories: confidentiality, integrity, availability, non-repudiation and authentication of information. Confidentiality refers to the protection of the information from being disclosed to unauthorised parties while integrity refers to the protection of information from being changed by unauthorised parties. Availability refers to the information being available to authorised parties when requested. Non-repudiation refers to the provision of proof of the origin such that the sender cannot deny sending the message, and the recipient cannot deny the receipt of the message. Authentication refers to a process or method to identify and to prove the identity of a user / party who attempts to send message or access data.
There is no exact definition, but the general idea is to protect of any IT information and resources with respect to confidentiality, integrity, availability, non-repudiation and authentication.
It is recommended to use a systematic approach by first considering the security interest of the organization or department as a whole. You can first identify the security requirements of your organization, then establish your security policy followed by enforcement. But periodic and continuous review and monitoring are definitely necessary in order to have an effective and efficient security policy.
You can first identify what you are going to protect such as your equipment and assets. Then you can find out the threats, the impact of each threat and the chance of their occurrence. To identify the threats which are often of different natures, a process namely risk analysis is normally used. Through this process, you can identify what assets to protect, their relative importance, and the priority ranking for urgency and level of protection required. As a result, a list of security requirements can be defined for your organization.
Security policy sets the basic mandatory rules and principles on information security. It should be observed throughout an organization and should be in accordance with your security requirements and organization's business objectives and goals. Security standards, guidelines and procedures are tools to implement and enforce security policy such that more detailed managerial, operational and technical issues can be considered. Standards, guidelines and procedures may require more frequent reviews than security policy.
These include:
- Goals and direction of the organization
- Existing policies, rules, regulations and laws of the Government
- Organization's own requirements
- Implementation, distribution and enforcement issues
Developing a Security Policy requires an active support and ongoing participation of individuals from multiple ranks and functional units. You can form a working group or task force to develop the Policy. But the exact group of personnel required depends on your organization's requirements. In general, this group may include empowered representatives from management, technical personnel, system developers, operational personnel, officers or users. Management represents the interests of the organization's goals and objectives, and can provide the overall guidance, assessment and decision making. Technical personnel can provide technical support for various security mechanisms or technological aspects. Users represent the users of related systems who may be directly affected by the Policy. Sometimes, a third party may get involved to review the Policy drafted.
You may first identify the group of people involved in developing the Policy. Second, make all necessary plans for activities, resources acquired and schedules. Then determine your security requirements, and establish your own Security Policy. You may need to go through several iterations of review and refinement for your Policy before a complete one can be established. As technology, environment and your requirements often change, you may need to continuously review and monitor your Security Policy in order to make it effective and useful for your organization.
Typical contents may include the policy objectives and scope, the assets to be protected, the roles and responsibilities of the involved parties, the DO and DON'T rules and security incidents reporting and handling. However, the exact contents and level of details depend on your security requirements and your organization's business objectives. Before drafting your security policy, you should also consider the goals and directions of HKSAR Government, the existing policies, rules, regulations and laws, and your implementation, distribution and enforcement issues.
As mentioned before, you and your staff can clearly understand what is and is not permitted in your organization relating to the protection of IT resources. This also helps to raise the level of security consciousness and to provide a baseline on which detailed guidelines and procedures can be established. It may also help to support the decision of prosecution against security violations.
Of course, you must first observe your organization's procedures, rules and regulations for implementation. However, no policy is considered to be implemented unless users or related parties have commitment and communication. This can be done through briefing, orientation and ongoing training. Make them aware that the Policy can create benefits to their daily work and if possible, invite them to participate in the process of developing the Policy. This can gain their commitment and acceptance of the Policy.
Security assessment here is defined as the methods to assess the security of the network or system. A security assessment software is specially designed to reduce the chance of internal abuse by searching and eliminating unnecessary security risks and vulnerabilities on internal hosts and workstations. These assessment tools are often used for security audit.
A security audit is performed in order to check and review the effectiveness and completeness of your security controls, your security policy, standards, guidelines and procedures. It will identify any inadequacies of the policy and related standards, and will find out if there are any security vulnerabilities of IT resources. Recommendations and remedy actions on security measures will be provided. In fact, a security audit should be an on-going process which should be performed periodically or regularly as there may be new vulnerabilities coming up daily.
A Security Audit only provides a snapshot of the vulnerabilities revealed at a particular point of time. But technology and your environment changes daily. There may be vulnerabilities found in the future even if all existing vulnerabilities have been identified. So periodic and ongoing review is inevitably required.
As Security Audit is a complex task and requires skilled and experienced personnel accommodated with existing system administrators, it must be planned carefully. A third party is recommended to perform the audit. This third party can be another group of in-house staff or an external audit team depending on your staff's skills and the sensitivity of the information being audited.
An IT Security Incident is any event that could pose a threat to the availability, integrity and confidentiality of a computer system. Such incidents can result in the destruction of data and disclosure of information.
A security incident handling plan should be defined to identify as far as possible all kinds of security incidents that may occur. The plan should be set up with a set of goals and objectives. When a security incident occurs, try to follow the procedures stated in the security incident handling plan. The plan may list all the activities such as the person to notify, the actions to protect the evidence and logs, the ways to limit the effect of the incident and the recovery procedures with minimal user impact. Evaluation of the incident should not be omitted as this can review the existing security measures, and ensure the completeness of these security measures.
An intrusion is a set of actions which attempt to compromise the availability, confidentiality and integrity of an information resource. Generally speaking, intrusion detection is the methodology by which intrusions are detected. This includes detection of intruders breaking into a system or users misusing the system resources.
Firewalls are only part of the total integrated security system. They do have limitations. They can neither alert on ALL intrusions nor stop ALL security breaches. They are frequently and easily misconfigured. Organizations are dynamic. People, technology and process often change. Unless you are constantly monitoring for intrusions, you cannot know if your firewall is working properly. Hence, the IDS is a vital tool to monitor your network 7 days x 24 hours per day. But bear in mind that IDS is just an addition to the firewall.
Intrusion Detection cannot help you to solve or fix the problem. It can neither tell you exactly who and how the attack occurred nor the intention of the attacker. It can only provide you with logs about the origin of the attack and who is making the attack, but most often these logs may not be able to tell you who is the real attacker.
A firewall is a group of systems that enforce an access control policy between two networks. In principle, the firewall can block traffic from the outside to the inside and permit traffic from the inside to communicate to the outside world. The firewall can also provide logging and auditing functions to record all traffic passing through it. In other words, a firewall can protect the internal network against any attacks from outside by defining an access control policy to permit or deny traffic. However, the firewall cannot protect against attacks that do not go through it and cannot protect against things like viruses or data driven attacks. It should be noted that firewalls are only part of the overall network security and the proper configuration of the firewall plays a very important role as well. Next Generation Firewall (NFFW) is a all-in-one solution included network firewall, Deep packet inspection ( DPI ) , Intrusion Prevention System ( IPS ) , Application control , SSL/SSH Detection , Web Filtering , Qaulity of Server (QOS) , etc.
Once you install a Web server at your site, you have opened a door into your local network for external visitors. From the view of the network administrators, you are opening up potential security hole. You have to bear the risks associated with this opening. Bugs or misconfiguration of the Web server can allow unauthorised remote users to access information which is not intended for them. Hackers may even execute server commands to modify the system, gain information about the Web server's host machine or launch attacks. Client side browsers may be attacked by these hackers and their personal information may be retrieved by these hackers through the hole. Network data sent from browser to Web server or vice versa may be intercepted by eavesdropping. Hence, all your information is vulnerable to interception if there is no proper system security on both browser and server sides.
In general, there are many precautions you should take. Say for example, you can limit the number of user accounts available on the machine. Try to ensure that users select good passwords. Remove all unused services, shells and interpreters. Configure your web servers correctly and ensure that the file permissions are granted to those authorised parties. Regularly check for system and Web logs for suspicious activity.
Malware is a piece of code that can replicate itself and spread to other computers via USB drive or data communication channels such as emails. It is recommended to install a memory-resident anti-virus program to continuously monitor the microcomputer. Virus protection should also be done on servers as well. Administrators are required to install some server-based anti-virus package into the servers with proper settings. A virus scanning software should be installed into the server's boot-up drive, and be activated at all times to prevent boot sector from infection. Administrators should also include a virus prevention and detection process into their daily routine. Of course, regular updates on the version of the virus prevention and detection software are essential to ensure the accuracy of detection and coverage for new classes of virus.
The security of multiple systems are of same magnitude of importance as the security of the interconnecting network. It is desirable to limit the connection to outside networks to those hosts which do not store sensitive information. All access to and from the local network must be made through a single host computer that acts as a firewall. Keep the network simple by minimizing the number of network interface points between the internal and external network. Only authorised traffic is allowed to pass via the internal network. If possible, use multiple authentication systems to monitor the users. However, network security only covers a small area in the overall security system, the data owner is also responsible for the security of the data.
Physical security refers to the protection of hardware and computer equipment from external physical threats.
Application security refers to the additional security measures built in the application itself to provide a more secure environment. It is highly related with system developers.
Internet security covers a wide range of issues such as identification and authentication, malware protection, software licensing, remote access, dial-up access, physical security, firewall implementation and other aspects relating to the use of Internet.
There are many ways to protect your privacy online. For example, you should not share your personal information such as your name and address with anyone online, unless you want them to know. Think carefully before giving out your personal information online, as this information about yourself may end up being used for other purposes. Secure your email by digitally signing and encrypting it before transmission and storage. Safeguard your personal computer at work and at home because it is physically open to attack or theft. Often change your password and keep it secret. Try not to use passwords that are your obvious names or easy to guess.
This depends on the password mechanisms and how the user himself keeps his own password. User should select a password that is difficult to guess and keep the password as secret as possible. He should also change his own password immediately after system recovery or upon receipt of the new password. Administrator should ensure that each new user is granted with a good initial password instead of using a default one. Procedures should be set up to ensure that only the real person is requesting the new or change password and gets that password. No passwords should be displayed on the screen at any time. User passwords which are used for authentication and administration should be encrypted before stored.
A password policy is a set of rules created to improve account security which usually cover the following rule -
- at least 12 characters long
- should not contain any personal information
- password should change periodically
- should not use previous password
- contain uppercase, lower case letters, numbers and symbols
- enable Multi Factor Authentication (MFA)
Peneteration Test is a simulated cyber attack against system to check for exploitable vulnerabilities.
Vulnerabilities Assessment evaluates the system for any known vulnerabilities, assigns severity levels to those vulnerabilities and recommends remediation or mitigation.
Red teams are offensive security professionals who break the system defenses.
Blue teams are defensive security professionals who response and defense in cyber attacks and threat.
Purple teams have 2 forms. They can be the mix of red and blue teams who break the system and fix it for improve incident response, or take the role to oversee and optimise the red and blue team exercise
Data encryption allows the people with access to a secret key or password can read the data.
Encrypted data is commonly referred to ciphertext, unencrypted data is referred to plaintext.
The data encryption should focus on two scenarios generally.
Encryption at rest - encryption of stored data, for example, the hard drive of database
Encryption in transit - encryption to protect data during data transfer to another location
Cybersecurity and Infrastructure Security Agency (CISA) of the US recommends that individuals and businesses use the 3-2-1 strategy.
3: Create one primary backup and two copies of your data
2: Save your backups to two different types of media (Disk, Tape, Cloud Storage, etc.)
1: Keep at lease one backup file offsite
An information technology disaster recovery plan (IT DRP) should be developed in conjunction with the business continuity plan (BCP). Priorities and recovery time objectives for information technology should be developed during the business impact analysis (BIA). Technology recovery strategies should be developed to restore hardware, applications and data in time to meet the needs of the business recovery.
IoT devices have made our lives convenient and more efficient. Organisation should aware of the security risks and threats of IoT devices.
To enhance the security of IoT devices, IT admin should
- Changing the default setting
- Disconnect IoT devices when not in use
- Set a strong password
- Avoid using UPNP
- Keep software firmware up-to-date
For more detail, please refer to https://www.hkcert.org/blog/implementing-iot-security-best-practice
Managed Security Service Provider (MSSP) provides outsourced monitoring and management of security devices and systems. Common services include managed firewall, intrusion detection, virtual private network, vulnerability scanning and anti-viral services. MSSPs also provide 24/7 services designed to reduce the number of operational security personnel an enterprise needs to hire, train and retain to maintain an acceptable security posture.
Privileged access management (PAM) is the combination of tools and technology used to secure, control and monitor access to an organization's critical information and resources. PAM include such as shared access password management, privileged session management, application access management.
Security Information and Event Management (SIEM) is a set of tools and services offering a holistic view of an organization’s information security by combining two technologies:
- Security information management (SIM), which collects data from log files for analysis and reports on security threats and events,
- Security event management (SEM), which conducts real-time system monitoring, notifies network admins about important issues and establishes correlations between security events.
Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data. Organizations use DLP to protect and secure their data and comply with regulations.
Organizations typically use DLP to:
- Protect Personally Identifiable Information (PII) and comply with relevant regulations
- Protect Intellectual Property critical for the organization
- Achieve data visibility in large organizations
Mobile device management (MDM) is software that allows IT administrators to control, secure and enforce policies. In general, MDM components should included device tracking, mobile management, application security, identity & access management, endpoint security to ensure the device is secure to the orgranisation.
Traditionally, companies have used URL filtering as a tool to prevent employees from accessing unproductive sites. With today's URL filtering, firms enable secure web access and protection from increasingly sophisticated threats, including malware and phishing sites.
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack or the revealing of sensitive information.
According to Coalition Against Unsolicited Commercial Email (CAUCE), most commonly seen unsolicited commercial emails (UCEs) are:
- Chain letters
- Pyramid schemes (including Multilevel Marketing, or MLM)
- Other "Get Rich Quick" or "Make Money Fast" (MMF) schemes
- Offers of phone sex lines and ads for pornographic web sites
- Offers of software for collecting email addresses and sending UCE
- Offers of bulk emailing services for sending UCE
- Stock offerings for unknown start-up corporations
- Quack health products and remedies
- Illegally pirated softwa
Every time a spammer sends out spam email, the entire Internet community has to bear the cost, in particular the recipients and the ISPs at the receiving end. Some Internet users are paying for their Internet access time by the minute, so they are forced to spend extra online time and, therefore, money in downloading unwanted spam email.
Spam is also disruptive to email users, wasting their time, and ultimately making the email as a convenient tool less useful if the amount of spam continues to grow. Spam email also ties up bandwidth and resources on computers and routers all over the Internet. Every unwanted email message adds to the total cost of operating the networks of computers that form the path of delivery to recipients. Spam email can disrupt a network by crashing mail servers and filling up hard drives. It also constitutes an invasion of Internet users' online privacy
Most spam is commercial advertising. Companies and advertisers rarely send spam directly. They would hire some spammers to do the work. Spammers obtained mailing lists from some email address harvesters. The harvesters can collect email addresses via scanning web sites, newsgroups and email lists. In addition, harvesters can also develop programs to generate random email addresses lists.
With these lists, harvesters can bombard a domain with messages and the harvesters can obtain validated email addresses if the recipients respond to the messages. With the mailing lists, spammers can start their work using spamming tool available in the Internet. When spammers first started, they used to send bulk mails from their own IP addresses. However, as email administrators learn from experiences and start to blocking email from their sites, spammers have to find a way of sending unsolicited commercial emails. Finally, they found an easy way to accomplish this - Third Party Mail Relay or Open Relay.
A third party mail relay is an email server receiving email from an unknown sender and then sending it on to a recipient or recipients that are not users of that email system. Some email systems enable this relay feature in the default installation. Taking into account the large number of mail servers that exist on the Internet, this is still a considerable number of servers which allow the relay.
Spammers can simply collect lists of third party mail relay in the Internet through some scanning programs. With the lists, spammers can configure the spamming tool with a relay's address, so it obscures their identity from the recipients and places the burden of the work on an email server that they don't worry about overloading or crashing.
Almost all ISPs operating in Hong Kong have included in their service agreements provisions to prohibit users from abusing their services for the purpose of email spamming. Spammers will face warnings or even suspension or termination of services with forewarnings.
Furthermore, ISPs commonly adopt technical measures to combat spamming problem. For example, their email servers may refuse the transmission of emails not composed by the sender (such as rejecting to forward an email received by the subscriber to the third party); or they may maintain a blacklist of email servers (i.e. reject to take in emails sent from blacklisted servers); or they may limit the quantity of emails sent from prepaid accounts.
SPF, DKIM and DMARC are the technology to tackle email spoofing and phishing.
Sender Policy Framework (SPF) is used to specify which IP addresses and domains are permitted to send email on behalf of your domain.
To backfill the share IP of email server security, DomainKeys Identified Mail (DKIM) provides a mechanism to cryptographically sign the email body and certain headers.
Domain-based Message Authentication Reporting and Conformance (DMARC) provides regular reports let the email sender know how many emails are potentially spoofed. Conformance helps email receiver how to treat non-conforming emails.
A typical "delete" command merely deletes the pointer to a file. The data will not be overwritten until the storage area is reallocated and re-used. By using commonly available utilities, it is possible to retrieve the deleted data in a computer.
The "format" command in many cases merely creates an empty root directory and a new blank indexing scheme for all allocation units on the storage media making it available for the storage of new files. There are commercially available utilities to recover lost data from storage media caused by accidental execution of the "format" command.
Commercial software and services are available in the market to perform secure data deletion by means of writing over the storage media a number of times and with different patterns. Those software packages which overwrite the data space with a character, the complement of that character, then a random character can be considered as reliable and follow current industry best practice for secure data deletion. However, you may need to evaluate the capability and features of such products and consult their respective product vendors for details to see if they fulfill your specific requirements. Also, besides technical solution, necessary checks and balances should be in place to ensure that the secure deletion process is performed and is successful. Some of the possible measures which you may consider include proper approval/logging of the whole process, sample check/verification of erase hard disks, etc.
Yes, commercial tools are available for data recovery. However, the prime objective of those tools is to address the disaster recovery need, e.g. when the data or its media is deleted or damaged by accident or natural disaster such as fire rather than after the application of the secure deletion procedures.
To recover or reconstruct data that has been deliberately overwritten usually requires specialised devices and/or environment. Data recovery and/or guessing would likely be uneconomical and hence impractical after the secure deletion procedures that follow the industry best practices are adopted.
In fact, Secure data deletion is one form of security risk management, similar to other information security topics. The security risk level associated with data deletion and recovery would be related to the value of the data being protected, the resources required to delete/undelete the data, and the cost of the equipment to be reused.
According to international/industry practices, degaussing is considered an acceptable technical solution for secure data deletion for magnetic media such as hard disks, floppy disks and magnetic tapes if properly employed. During the degaussing process, the magnetic flux of the media is reduced to virtually zero by applying a reversing magnetizing field. Properly applied, degaussing renders any previously stored data on the media unrecoverable by keyboard or laboratory attack.
An intrusion is a set of actions which attempt to compromise the availability, confidentiality and integrity of an information resource. Generally speaking, intrusion detection is the methodology by which intrusions are detected. This includes detection of intruders breaking into a system or users misusing the system resources.
- The resistance of a magnetic media to demagnetization is the coercivity of the magnetic media and is measured in Oersteds. In order to completely erase the content on the magnetic media (e.g. hard disk), the degausser should produce a sufficiently strong magnetic field. It is recommended that the magnetic field should be at least 1.5 times higher than the coercivity of the media. Typical figures for various types of magnetic media are given below:
| Typical Media Coercivity Figures | |
|---|---|
| Medium | Coercivity |
| 5.25" 360K floppy disk | 300 Oe |
| 5.25" 1.2M floppy disk | 675 Oe |
| 3.5" 720K floppy disk | 300 Oe |
| 3.5" 1.44M floppy disk | 700 Oe |
| 3.5" 2.88M floppy disk | 750 Oe |
| 3.5" 21M floptical disk | 750 Oe |
| 1/2" magnetic tape | 300 Oe |
| 1/4" QIC tape | 550 Oe |
| 8 mm metallic particle tape | 1500 Oe |
| DAT metallic particle tape | 1500 Oe |
| 4mm DDS-1 tape | 1550 Oe |
| 4mm DDS-2 tape | 1650 Oe |
| 4mm DDS-3 tape | 2300 Oe |
| 4mm DDS-4 tape | 2350 Oe |
| Older (1980's) hard disks | 900-1400 Oe |
| Newer (1990's) hard disks | 1400-2200 Oe |
| Newer (2000) hard disks | 2000-3400 Oe |
- During the degaussing process, the degaussers have to be operated at their full magnetic field strength. The product manufacturer's directions must be followed carefully since deviations from an approved method could leave significant portions of data remaining on the magnetic media.
- For degaussing hard drives, all shielding materials (e.g. castings, cabinets, and mounting brackets), which may interfere with the degausser's magnetic field, must be removed from the hard drive before degaussing. Hard disk platters must be in a horizontal direction during the degaussing process. For degaussing hard drives with very high coercivity ratings, it may be necessary to remove the magnetic platters from the hard drive's housing.
- Sufficient checks and balances mechanisms should be in place for the degaussing process such as requiring the individual who performs the degaussing to certify the completion of the degaussing by affixing a signed verification label to the hard drive or the computer housing the hard drive indicating the date and degaussing product used for the procedure. Sample check of the degaussed media should also be performed by another party to ensure that the degaussing is done properly. Besides, the degausser should also be periodically tested accordingly to manufacturer's directions to ensure that they function properly.
Solid state drives use an electric charge to store data on individual transistors. For this reason degaussing an SSD will not erase the data and no effect on the SSD because the data is not stored magnetically. Organisation who want to erase the SSD data should consider low-level formatting or any other SSD secure erase software.
Malware is a short for "malicious software", it is any intrusive software developed by hackers to steal data, damanage computer systems. Common malware includes virus, worm, Trojan, spyware, adware and ransomware.
Malware affects the health of your computer just like their biological counterparts make you sick. Typical payload of malware creates backdoor of your system which allow hacker to remote your system for stealing confidential data such as credential, credit card information.
CARO - Computer Anti-Virus Researchers Organisation. An invitation-only group of technical researchers, mostly representing anti-virus vendors. CARO approves ' standard ' names for viruses. Some people tend to mistrust the fact that CARO members often share virus samples: however, CARO membership is a convenient yardstick by which other members can judge whether an individual can be trusted with samples. In general, users at large benefit this way: anti-virus vendors with CARO members can include most known viruses in their definitions databases.
EICAR - European Institute for Computer Anti-Virus Research. Membership of which comprises academic, commercial, media, governmental organisations etc., with experts in security, law etc., combining in the pursuit of the control of the spread of malicious software and computer misuse. Membership is more open, but members are expected to subscribe to a code of conduct. And yes, this is the origin of the EICAR test file. EICAR has a web page at http://www.eicar.com.
The Wild List is a list of the most common viruses infecting computers worldwide, and is compiled by the well-known antivirus researcher Joe Wells. Wells works closely with antivirus research teams around the world to update the list regularly.
A product that detects 90 percent of ' in the wild ' viruses will detect 90 percent of the viruses on this list - or 90 percent of the most common viruses circulating.
Malware is around you and me. Nevertheless, we could minimize the chance of being infected by taking sufficient preventive measures. The following provides some guidelines on preventing computer virus:
- DO NOT use Illegal software under any circumstances.
- Connection to Internet / external BBS should be controlled.
- DO NOT run programs downloaded from Internet / doubtful origin. If it is necessary to do so, you should scan the file with an up-to-date virus scanner.
- Scan files attached in e-mails with up-to-date anti-virus program before use.
- Set C: as the default boot up drive (by changing the settings in the CMOS setup). This will decrease the chance of infecting boot sector virus.
- Check USB drive and files (especially those of unknown origin) with a virus scanning programs before use.
- Write-protect all portable drive that you do not expect to write to and remove floppy diskettes from drive slots when they are not being referenced.
- Make sure that you backup your files regularly so that you can recover them after a virus attack.
Malware is being developed every day. New techniques may render existing preventive measures insufficient. The only truth in malware and anti-virus field is that there is no absolute security. However, we can minimize the damage by identifying malware infections before they carry out their payload. The following lists some ways to detect malware infections:
- Watch out for any changes in machine behaviour. Any of the following signs could be symptoms of malware activity:
- Programs takes longer time than usual to execute,
- Sudden reduction in system memory available or disk space
- A memory-resident anti-virus program can be employed to continuously monitor the computer for malwares.
- Scan your hard disk with an anti-virus utility. You should make sure that an up-to-date virus signature has been applied and you should update the signature at least once a month.
- Employ server-based anti-virus software to protect your network. You should also consider employing application-based anti-virus software (e.g. those running on Lotus Notes) to further protect your machine.
Although a malware can write to (and corrupt) a PC's CMOS memory, a malware can NOT ' hide ' there. The CMOS memory is not ' addressable '. Data stored in CMOS would not be loaded and executed on a PC. A malicious virus can alter the values in the CMOS as part of its payload causing the system to be unable to reboot, but it cannot spread or hide itself in the CMOS.
A malware could use CMOS memory to store part of its code, but executable code stored there must first be moved to the computer's main memory in order to be executed. Therefore, a malware cannot spread from, or be hidden in CMOS memory. And there is no known virus that stores code in CMOS memory.
There had been reports of a trojanized AMI BIOS. It is a ' joke ' program which does not replicate. The malware is not on the disk, nor in CMOS, but was directly coded into the BIOS ROM chip on the system board. If the date is the 13th of November, it stops the boot up process and plays ' Happy Birthday ' through the PC speaker.
Theoretically, it is possible to have a malware that hide in BIOS and be executed from BIOS. Current technology enables programs to write codes into BIOS. BIOS is the place for storing the first piece of program to be executed when a PC boots up.
Malware has been found? Don' t panic! The following is some pieces of advice about removing computer malware:
- All activities on infected machine should be stopped (and it should be detached from the network) as the payload may be triggered at any time. Continuing the use of the infected machine help the suspected malware spread further.
- Recover from backup is the most secure and effective way to recover the files.
- In some cases, you may recover the boot sector, partition table and even the BIOS data using the rescue disk.
- In case you do not have the latest backup of your files, you may try to remove the malware using anti-virus utilities
Malwares are not Devils. They are just computer programs with self-replication function. That means they are able to make copy of itself. Since the process is automatic, the program is able to spread inside a computer or inside a network. Anti-virus software is designed by international companies to detect and clean such virus programs. With up-to-date signature, almost all viruses can be detected and removed easily. For new viruses not detected by anti-virus software, a new virus signature update will usually be available within a week.
Mobile phones that do not allow user to install new applications on the device and are limited to using only the on-board applications burned into ROM (read only) or Flash memory chips are not susceptible to classical computer malware attacks. However, the new generation of smart phones are essentially mobile-enabled PDAs. These devices permit the user to install new software on the device at any time. Therefore, as with any computing platform, smart phones are also susceptible to malware attacks. Thus far, there have already been some reports of minor malwares attacks on mobile devices.
Usually not. The exception is data files that contain executable code, which can be infected by viruses. A good example of this is a Microsoft Word file (.DOC, .DOT). Although Word files are technically data files, they may contain macros, which are executable and therefore susceptible to infection.
Macro viruses are special macros that self-replicate in the data files of applications such as Microsoft Word and Excel. The majority of macro viruses infect Word document files. When a file containing infected macros is opened, the virus usually copies itself into Word's global template file (typically NORMAL.DOT). Any document opened or created subsequently will be infected.
Macro viruses become part of the document itself, and are transferred with the file via floppy disks, file transfer, and e-mail attachments.
Like all computer viruses, macro viruses can destroy data. For most users, the worst thing a macro virus might do is to reformat their computer hard drives. While most of the known macro viruses are not destructive, many cause a considerable loss of productivity and time.
Of course the most secure method is to backup your data regularly and use antivirus software that is able to scan your documents before Word startup.
If you' re only viewing web pages written with HTML only (i.e. no Active X, active scripting, JAVA, etc.) and that your computer has been patched with the latest security patches, the answer is ' No ' . However, if your computer is not fully patched or if you run Active X controls, active scripting and JAVA applets, or run programs downloaded from the Internet, it is possible that these programs contain malware and affect your machine. Computer users should take the following security measures when surfing the Internet:
- Ensure that the operating system and software on your computer have been applied with the latest security patches.
- Enable real-time scanning of anti-virus software and use the latest virus signature.
- Avoid visiting suspicious/untrusted websites.
- Do not execute unsigned ActiveX control or ActiveX control from un-trusted sources.
- If possible, disable running active scripting in browser setting.
- Avoid downloading programs from un-trusted websites, since they have high risk of causing malware infection.
Plain electronic mail messages with pure text containing no executable code will not be infected. However, HTML e-mails which can contain executable scripts as well as files attached to the e-mail message may be infected. Most anti-virus software nowadays can be configured to scan e-mails and their attachments.
A boot disk is one which contains the necessary operating system files (e.g. MSDOS.SYS, IO.SYS) to boot up the machine. It is useful when scanning and cleaning virus, because even if the hard disk becomes inaccessible, you can still boot up the machine to attempt some repairs.
If you want to create a recuse disk, you could refer to the operation system suggestion. Some computer manufacturer or backup software vendor also supports the user to create the rescue disk manually.
Many anti-virus and disk repair utilities can make a (usually bootable) rescue disk for a specific system. This needs a certain amount of care and maintenance, especially if you have made more than one of these for a single PC with more than one utility. Make sure you update *all* your rescue disks when you make a significant change, and that you understand what a rescue disk does and how it does it before you try to use it. Don' t try to use a rescue disk made from one PC on another PC, unless you' re very sure of what you' re doing, otherwise you may risk losing valuable data/files on your computer.
A malware scanning engine is the program that does the actual work of scanning and detecting malwares while signature files are the ' fingerprints ' used by the scan engines to identify malwares. New scan engine versions are released for a number of reasons. New malwares are found everyday around the world. New types of malwares may not be detected by the old engine. New versions of scan engine usually also enhance scanning performance and detection rates. Some vendors provide updates for both the scan engine and signature file in a single file while others will provide them in separate files.
Anti-virus software not only detect malwares, but also other types of malicious codes, which may not be cleanable. For example, trojan horse is a type of malicious code that should be deleted instead of cleaned. In other cases, the virus may have corrupted the file and made it impossible to be cleaned / recovered. Nevertheless, there are some tips you can do to maximize the likelihood of recovering the file using anti-virus software:
- Check whether the virus signature files and scan engine are up-to-date.
- Make sure there is enough free space on the disk.
- Check if removal instructions or automatic removal tool is available from anti-virus vendor web sites.
- If still unsuccessful, obtain a virus sample and send it to anti-virus vendors for recommended actions.
Ransomware is malware that employs encryption to hold a victim’s information at ransom. A user or organization’s critical data is encrypted so that they cannot access files, databases, or applications. A ransom is then demanded to provide access. Ransomware is often designed to spread across a network and target database and file servers, and can thus quickly paralyze an entire organization.
To prevent unauthorized Wi-Fi access, you can consider implementing the following measures on your wireless access point (AP).
- Change the default setting such as, user name and password of Access Point (AP).
- Turn on wireless data encryption WPA2-PSK (Preshared key) or above with AES protocol; with minimum 20 characters passphrase contains at least one capital letter and one numeric letter.
- Enable the MAC address filtering feature on AP and only allow devices with pre-registered MAC address to connect.
- Do not broadcast the service set identifiers (SSID).
- Turn off the AP when not in use.
To prevent unauthorized Wi-Fi access, you can consider implementing the following measures on your wireless access point (AP).
- Change the default setting such as, user name and password of Access Point (AP).
- Turn on wireless data encryption WPA2-PSK (Preshared key) with AES protocol; with minimum 20 characters passphrase contains at least one capital letter and one numeric letter.
- Enable the MAC address filtering feature on AP and only allow devices with pre-registered MAC address to connect.
- Do not broadcast the service set identifiers (SSID).
- Turn off the AP when not in use.
Use WPA2-PSK (Preshared Key) or above with AES protocol for the data encryption. WPA2 is more secure than WPA and WEP and those algorithms had been broken. To protect against brute force attacks, minimum 20 characters should be used and passphrase should contains at least one capital letter and one numeric letter. Apart from the data encryption, user should disable the service (SNMP and WPS) which is not in use and upgrade the firmware regularly.
Some AP has built-in function to isolate connection between clients. This function has different name in different products (e.g. AP Isolation, Privacy Separator). In addition, make sure you use https connection as possible while browsing the Internet.
If you provide Wi-Fi connection to guest, you should separate them into an isolated Wi-Fi network. Guest should have limited access to Internet only (Web browsing) and not able to access internal resources, such as file server. System administrator should review the traffic and audit log regularly, as it can help in the detection of security incident.
Below are some suggestions that you can implement to minimize the exposure of internal Wi-Fi.
- Change the AP default user name and password.
- Do not broadcast the SSID of the AP.
- Only allow registered wireless network devices to connect.
- Turn on wireless data encryption.
- Classified Wi-Fi networks as untrusted networks and password protect your computers and files.
- Use firewall and network intrusion detection to detect and defend network attack.
- Periodically check AP logs for abnormal traffic and rogue users.
- Turn off wireless cards and APs when not in user.
Wireless network provides the mobility for user to work within the company. It also provides a way for you to allow visitors to access Internet with their mobile devices. Planning and deploying is more complicated than just plug in the wireless AP within your corporate. You need to establish policies for the usage and control of Wi-Fi network, select the security measure to minimize the risk in Wi-Fi networks and secure Wi-Fi communications.
You may reference the below for planning and deploying Wi-Fi network.
Security Polices:
- Define the usage of the Wi-Fi network and security requirement of the Wi-Fi connection
- Define the type of information that is not allowed to send over wireless network.
- Define the procedure of reporting the loss of WLAN device.
- Keep an accurate inventory of all WLAN devices
- Remove all configuration and sensitive information from the WLAN device before disposal.
Wi-Fi location and network design:
- Wireless site survey should be conducted to tune the power of APs to provide just sufficient coverage and roam capability.
- Treated Wi-Fi network as untrusted network and segment the wireless traffic in a separate network.
Security protection:
- Deploy Network Intrusion system (WIPS/WIDS) which support rouge AP Identification and Denial of Service protection such as AP flooding.
- Disable all insecure and unused management protocols of AP and configure it for least privilege.
- Enable the AP access threshold parameters, such as inactivity timeouts and maximum supported associations.
- Enable the AP logging features and forward the log entries to a remote logging server
- Disable the ad-hoc mode of wireless client device.
- Incorporate the enterprise login system (such as RADIUS and Kerberos) for authentication
- Adopt the latest authentication option, such as Extensible Authentication Protocol (EAP) to get the higher protection level.
- Limit the services provided in WLAN, especially guest WLAN. Apply access control and quality of service control to ban unallowed traffic or unwanted overuse of bandwidth.
Ongoing maintenance:
- Wireless vulnerability assessment should be performed regularly to look for the enforcement of security policy, unknown wireless devices or security threat due to mis-configuration or device vulnerability.
- Regular review of access and traffic of AP for abnormal traffic and rogue users.
- Update the firmware of wireless devices periodically.
Security requires ongoing maintenance and education, it is important to regularly maintain the wireless network for highest level of security.
- Regular review of access and traffic of AP for abnormal traffic and rogue users.
- Update the firmware of wireless devices periodically
- Perform wireless vulnerability assessment regularly to look for the enforcement of security policy, unknown wireless devices or security threat due to mis-configuration or device vulnerability.
- Subscribe wireless security newsletter and alert and attend security seminar to keep abreast of new security trend.
You should avoid using free public Wi-Fi without encryption, if you do so, you should avoid login to your email, online shopping or e-banking web sites.
To avoid connecting to malicious Wi-Fi AP, you should be aware of the SSID you are connecting. Do not connect to a SSID called “Free Public Wi-Fi”, this is usually an ad-hoc network created by another laptop or a trap that trick you to connect to a harmful network and then infect your laptop or steal personal data. Some wireless AP requires you to accept the usage agreement on the landing page, you should verify their certificate by clicking the SSL Lock icon ( ) before you accept the usage agreement. Finally you should turn off the Wi-Fi device when it is not in use to avoid it automatically connect to unknown AP.
Public Wi-Fi access is generally treated as insecure connection. Many public Wi-Fi are completely unencrypted so that users can connect to it easily. Intruder could easily see all data being transmitted if it is unencrypted. Therefore, you should only connect to a Wi-Fi hotspot with encryption enabled. Below are some tips which help you access public Wi-Fi safely.
- Avoid sending financial / personal information over public Wi-Fi network. If you must enter your sensitive information, make sure you are connecting to https web site. There is a lock icon in the browser windows and the site’s address begins with “https”
- Turn off file and printer sharing on computer when connecting to public network.
- Make sure your Internet browser, computer and antivirus signature are up-to-dated and turn on your system firewall.
We do not recommend sending sensitive information such as financial information and bank account, at public Wi-Fi hotspot. If you do, make sure you are connecting to a legitimate hotspot and web sites with encryption enabled.
DDoS amplification attacks leverage the characteristics of protocols to amplify the DDoS attack traffic volume to overwhelm victims’ server or network. For example, when 1 byte of request sending to a Network Time Protocol (NTP) service, the server will respond with more than 500 bytes of data. When attackers initiate DDoS attack traffic to a open NTP ports on the Internet, the reflected traffic volume will be 500 times the originating volume. This causes a severe impact on the victims network service.
Since DDoS amplification attacks leverage open ports exposed to the Internet due to misconfiguration, it is advised to harden the open ports and minimise the points of exposure to the Internet. This can reduce the risk of being leveraged by the attacker.
1. Ensure your organisations get prepared with a related contingency plan and playbook for DDoS incident;
2. Ensure network monitoring and security detection are in place and ready to carry out immediate incident response if any abnormal network activities are detected;
3. Harden the network infrastructure and minimise the points of exposure to the Internet;
4. Consider DDoS protection solution or service to defend against DDoS attacks;
There are 16 common types of open ports vulnerable to DDoS amplification attack. The corresponding security advice of different types of misconfiguration is summarized in the table below:
S/N | Types of Misconfiguration | Amplification Ratio | Involved Port | Methods for Blocking Each Type of Amplified Reflection Attack |
1 | Accessible Apple Remote Desktop | 35.5 | 3283 | Turn off the Remote Management in Setting |
2 | Accessible CoAP | 50 | 5683 | Device whitelisting |
3 | Accessible Ubiquiti Service Discovery | 35 | 10001 | Block source port |
4 | Open Chargen | 358.8 | 19 | Block source port |
5 | DNS Open Resolvers | 54 | 53 | 1) Disable recursion / Limit recursion to trusted clients 2) Response Rate Limiting (RRL) |
6 | Open Netbios | 3.8 | 137 | Block source port |
7 | NTP Monitor | 556.9 | 123 | 1) Upgrade to Version 4.2.7 or above; or |
8 | NTP Version | 40 | 123 | Block external request |
9 | Open LDAP Services | 55 | 389 | Block source port |
10 | Open mDNS Servers | 10 | 5353 | Block source port |
11 | Open MS-SQL Server Resolution Service | 25 | 1434 | Block source port |
12 | Open Portmapper | 28 | 111 | Block source port |
13 | Open TFTP Servers | 60 | 69 | Block source port |
14 | Open QOTD | 140.3 | 17 | Block source port |
15 | Open SNMP | 6.3 | 161 | Block source port |
16 | Open SSDP | 30.8 | 1900 | Block source port |
Description: The attackers are leveraging the Apple Remote Management Service (ARMS) that is a part of the Apple Remote Desktop (ARD) feature. When users enable the Remote Desktop capability on their macOS systems, the ARMS service starts on port 3283 and listens for incoming commands meant for the remote Mac.
Security Advice:
In macOS -- > Setting -- >Sharing -- > Remote Management -- > Turn off the Management
Description: One of the main threats associated with exposed CoAP services is their possible usage as reflectors for DDoS amplification attacks. Also found that many of these CoAP services can leak information (including authorization credentials to services, such as wifi networks). For certain devices, in some cases, it may even be possible to issue remote instructions using CoAP.
Security Advice:
At the very least CoAP instances should therefore be either firewalled to only communicate with necessary devices.
Description: These services have the potential to be used in amplification attacks by criminals that wish to perform denial of service attacks. In addition, they expose a large amount of information about the system running the service
Security Advice:
Blocking incoming connections to relate port on firewall. (Ubiquiti Service Discovery commonly used port 10001)
Description: CHARGEN is a debugging and measurement tool and a character generator service. It can make use of UDP port for traffic. Attack via CHARGEN was first addressed in 1996
Security Advice:
A) Setting for Chargen service enabled Server (Linux)
Method 1:
Blocking incoming connections to relate port on firewall (Chargen services commonly used Port 19)
Method 2:
In Linux Terminal, execute the following commands for disable the chargen service:
cd /etc/xinetd.d/
nano chargen
In nano, found service chargen and type "disable = yes"
B) Setting for Chargen service enabled Server (Windows)
Modify the Registry and set the values of the following two entries to 0
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableTcpChargen
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\SimpTCP\Parameters\EnableUdpChargen
C) Best Practice for Managing the Chargen service enabled Servers
Use a firewall to restrict access to the Chargen service.
Description: Identify DNS servers that will send a reply to any IP address for domains that the DNS server is not authoritative for and report them back to the network owners for remediation.
Security Advice:
A) Setting to disable recursion or limit recursion to trusted clients in the DNS server
Bind 9
Add the following to the global options:
options {
allow-query-cache { none; };
recursion no;
};
Windows
In the Microsoft DNS console tool:
- Right-click the DNS server and click Properties.
- Click the Advanced tab.
- In Server options, select the “Disable recursion” check box, and then click OK.
B) Limiting Recursion to Authorized Clients
Bind 9
In the global options, include the following:
acl corpnets { 192.168.1.0/24; 192.168.2.0/24; };
options {
allow-query { any; };
allow-recursion { corpnets; };
};
Windows
It is not currently possible to restrict recursive DNS requests to a particular client address range in Microsoft DNS Server. To approximate the functionality of the BIND access control lists in Microsoft’s DNS Server, a different caching-only name server should be set up internally to provide recursive resolution. A firewall rule should be created to block incoming access to the caching-only server from outside the organization’s network. The authoritative name server functionality would then need to be hosted on a separate server, but configured to disable recursion as previously described.
C) Setting Response Rate Limiting (RRL)
Bind 9
On BIND9 implementation running the RRL patches, include the following lines to the options block of the authoritative views:
rate-limit {
responses-per-second 5;
window 5;
};
Windows
Set RRL parameters on a DNS server using PowerShell:
Set-DnsServerResponseRateLimiting -WindowInSec 7 -LeakRate 4 -TruncateRate 3 -ErrorsPerSec 8 -ResponsesPerSec 8
D) Best Practice for Managing the Open DNS Servers
Reduce the total number of open DNS resolvers
An essential component of DNS amplification attacks is access to open DNS resolvers. By having poorly configured DNS resolvers exposed to the Internet, all an attacker needs to do to utilize a DNS resolver is to discover it. Ideally, DNS resolvers should only provide their services to devices that originate within a trusted domain. In the case of reflection based attacks, the open DNS resolvers will respond to queries from anywhere on the Internet, allowing the potential for exploitation. Restricting a DNS resolver so that it will only respond to queries from trusted sources makes the server a poor vehicle for any type of amplification attack.
Source IP verification – stop spoofed packets leaving network
Because the UDP requests being sent by the attacker's botnet must have a source IP address spoofed to the victim’s IP address, a key component in reducing the effectiveness of UDP-based amplification attacks is for Internet service providers (ISPs) to reject any internal traffic with spoofed IP addresses. If a packet is being sent from inside the network with a source address that makes it appear like it originated outside the network, it’s likely a spoofed packet and can be dropped.
Description: NetBIOS defines a software interface and a naming convention. The NetBIOS name service uses port 137/udp.
Openly accessible NetBIOS name services can be abused for DDoS reflection attacks against third parties. Furthermore, they allow potential attackers to gather information on the server or network for preparation of further attacks.
Security Advice:
Blocking incoming connections to relate port on firewall. (Netbios services commonly used Port 137)
Description: NTP is short for Network Time Protocol. It is one of the standards for time synchronization in the Internet. Its purpose is to synchronize the clock of the computer to the international standard time, and the machine connected to the Internet will calibrate the time through the protocol.
NTP includes a monlist function, also known as MON_GETLIST, which is mainly used to monitor NTP servers. The monlist function has a security vulnerability. After the NTP server responds to the monlist, it returns the IPs of the last 600 clients that have performed time synchronization with the NTP server; the response packages are split every 6 IPs, and there will be up to 100 response packets eventually.
Security Advice:
A) Setting for NTP Server (Linux)
Method 1:
- Upgrade the NTP Server to 4.2.7 or above
Method 2:
- In Linux NTP Server, in a Terminal window, and execute these commands:
- nano /etc/ntp.conf
- In nano, scroll down a page or two to find the two "restrict" lines highlighted below, and remove # signs to comment them out:
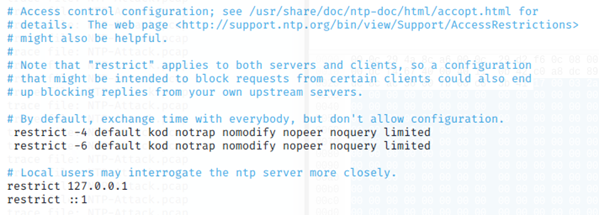
B) Setting for NTP Server (Windows)
This misconfiguration is not available on Windows Server.
C) Best Practice for Managing the Open NTP Servers
Use Multiple NTP Servers
The easiest thing for a network operator to do is simply configure their clients to use multiple NTP servers on the network.
This NTP configuration can process multiple time sources at the same time and discard one if it disagrees with the rest. This makes an attacker’s job harder, because they will need to attack the NTP traffic from a majority of the servers to impact the NTP clients.
Monitor Servers From The Client’s Perspective
Another Best Practice is to have NTP client nodes devoted to monitoring the health of the NTP servers on the network. Monitoring an NTP server directly is important, but it will only tell you if there is a problem with that particular server. If you monitor it from the client side, you can look at the time transfer process from the client's perspective and see whether there is anything suspicious happening after the packets leave the server.
Use NTP Encryption Options
The NTP peering packets (as well as the mode 6 "ntpq"-style queries) contain sensitive information that can be used in an attack. When using these services, operators are advised to either use NTP encryption options (such as symmetric keys) or use other means (such as access control lists) to control who can access these NTP queries. This will prevent this information from leaking out to unauthorized parties who could use them in a cyberattack.
Description: NTP servers that have the potential to be used in amplification attacks by criminals that wish to perform denial of service attacks.
The NTP version command is a Mode 6 query for READVAR.
Security Advice:
A) Setting for NTP Server (Linux)
- In a Terminal window, and execute these commands:
- nano /etc/ntp.conf
- In nano, scroll down a page or two to find the two "restrict" lines highlighted below, and remove # signs to comment them out:
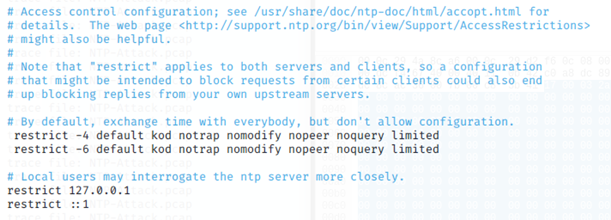
B) Setting for NTP Server (Windows)
This misconfiguration is not available on Windows Server.
C) Best Practice for Managing the Open NTP Servers
Use Multiple NTP Servers
The easiest thing for a network operator to do is simply configure their clients to use multiple NTP servers on the network.
This NTP configuration can process multiple time sources at the same time and discard one if it disagrees with the rest. This makes an attacker’s job harder, because they will need to attack the NTP traffic from a majority of the servers to impact the NTP clients.
Monitor Servers From The Client’s Perspective
Another Best Practice is to have NTP client nodes devoted to monitoring the health of the NTP servers on the network. Monitoring an NTP server directly is important, but it will only tell you if there is a problem with that particular server. If you monitor it from the client side, you can look at the time transfer process from the client's perspective and see whether there is anything suspicious happening after the packets leave the server.
Use NTP Encryption Options
The NTP peering packets (as well as the mode 6 "ntpq"-style queries) contain sensitive information that can be used in an attack. When using these services, operators are advised to either use NTP encryption options (such as symmetric keys) or use other means (such as access control lists) to control who can access these NTP queries. This will prevent this information from leaking out to unauthorized parties who could use them in a cyberattack.
Description: The Lightweight Directory Access Protocol (LDAP) is a networking protocol for accessing and maintaining distributed directory information services.
Openly accessible LDAP servers can be abused for DDoS reflection attacks against third parties. Furthermore, they allow potential attackers to gather information on the server or network for preparation of further attacks.
Security Advice:
Blocking incoming connections to relate port on firewall. (LDAP services commonly used Port 389)
Description: Multicast DNS (mDNS) is used for resolving host names to IP addresses within small networks that do not include a local DNS server. mDNS uses port 5353/udp.
Openly accessible mDNS services can be abused for DDoS reflection attacks against third parties. Furthermore, they allow potential attackers to gather information on the system or network the service is running on for preparation of further attacks.
Security Advice:
Blocking incoming connections to relate port on firewall. (mDNS commonly used Port 5353)
Description: This report identifies hosts that have the MS-SQL Server Resolution Service running and accessible on the Internet.
These services have the potential to expose information about a client’s network on which this service is accessible and the service itself can be used in UDP amplification attacks.
Security Advice:
Blocking incoming connections to relate port on firewall. (MS-SQL Server Resolution Service commonly used Port 1434)
Description: The Portmapper (portmap, rpcbind) is required for mapping RPC requests (remote procedure calls) to a network service. It is needed e. g. for mounting network shares using the Network File System (NFS).
Openly accessible Portmapper services can be abused for DDoS reflection attacks against third parties.
Security Advice:
Method 1:
Blocking incoming connections to relate port on firewall. (Portmapper commonly used Port 111)
Method 2:
The portmapper service can be disabled using the following command:
systemctl disable rpcbind
systemctl disable rpcbind.socket
systemctl stop rpcbind
systemctl stop rpcbind.socket
Method 3:
The portmapper service can be removed using the following command:
# apt-get remove rpcbin
Description: This report identifies hosts that have the TFTP service running and accessible on the Internet. Our probe tests to see if the TFTP service is accessible and will either return the file that we are asking for or return an error code. Note, we are not testing to see if file upload is enabled.
Security Advice:
Blocking incoming connections to relate port on firewall. (TFTP commonly used Port 69)
Description: This report identifies hosts that have the Quote of the Day (QOTD) service running and accessible on the Internet.
These services have the potential to be used in amplification attacks by criminals that wish to perform denial of service attacks. The service is tested by sending a UDP packet containing a single carriage return to UDP port 17.
Security Advice:
Blocking incoming connections to relate port on firewall. (QOTD commonly used Port 17)
Description: The Simple Network Management Protocol (SNMP) is a networking protocol for device management and monitoring.
Openly accessible SNMP servers using the default 'public' community can be abused for DDoS reflection attacks against third parties. Furthermore, they allow potential attackers to gather information on the server or network for preparation of further attacks.
Security Advice:
Blocking incoming connections to relate port on firewall. (SNMP commonly used Port 161)
Description: SSDP is used by some consumer-level equipment for network discovery. It does not have any real use on public servers and is used for reflection DDoS attacks on dedicated servers.
Security Advice:
Method 1:
Blocking incoming connections to relate port on firewall. (SSDP commonly used Port 1900)
Method 2:
If the SSDP server is not required, disable or deinstall it.
User following command: iptables -I INPUT 1 -p udp -m udp --dport 1900 -j DROP
- Purchase webcams from official channel
- Change the default password of webcam
- Password should be changed regularly with complexity
- Do not monitor or administrate the webcam in public network
- Download the mobile application for webcam only from official app stores
- Check the webcam settings regularly
- Update firmware of webcam to the latest version.
- Do not set the webcam to monitor private or sensitive areas
- Turn off the webcam when not in use
- Regardless of the connection method used (such as RTSP, HTTP(S)), the authentication function should be enabled
- Beware of security alerts of webcams
- If not absolutely necessary, do not connect NAS devices to the Internet
- If necessary, use a virtual private network (VPN) before access
- Change the default protocol and port for the web admin interface
- Change the default administrator password or create a new administrator account
- If not necessary, do not install or enable additional functionalities
- Periodically backup files
- Continuously update the system
- Notice the security alerts for their devices
- Change the router default password
- Update router firmware regularly
- Unless it is definitely required, do not expose any remote management services
- Turn off all unusual or unnecessary services (such as file transfer, virtual private networks)
- If the manufacturer has stopped support for the router model, you should consider replacing it with models that have continuous support
- Please do not convert to open source firmware
"Source from the Office of the Government Chief Information Officer (OGCIO) of the Government of the Hong Kong Special Administrative Region"



