Browser’s Anti-phishing feature: What is it and how it helps to block phishing attack?
Over the past four years, HKCERT has handled an average of about 8,900 local cyber security incidents per year, with phishing attacks accounting for 48% of all incidents in 2021 [1]. Even globally, phishing attacks account for 36% of total security incidents [2].

Introduction
The high volume of phishing attacks is attributed to the low-cost yet highly effective and sophisticated nature of such attack. Nowadays technology makes it easy for hackers to build fake emails and websites, which are hard for the users to distinguish solely from the site layout.
Apart from directly defrauding users’ sensitive personal information, if attackers successfully obtain the credentials of any internal systems of the organisations (for example VPN or SaaS), they can then attempt to obtain sensitive information stored in the system or perform lateral movements (i.e. the process of an attacker progressively moving from the entry point to the rest of the network [3]) and hack into other internal systems.
How to Prevent Phishing Attack
In addition to raising users’ cyber security awareness (e.g., how to identify suspicious emails and URLs, proactively reporting suspicious URLs), anti-phishing functions are generally provided by anti-virus software and web browsers to block the access to suspicious websites for users and organisations.
Anti-Phishing Website Function and Engine
Acting as the gateway to websites, browser has the ability to detect and identify phishing URLs, making it one of an important defense mechanisms. Common browsers usually come with a built-in anti-phishing website function. When the browser tries to access the page, the anti-phishing website engine will first compare and analyse the URL against the data in the database of the phishing website. If the analysis result is safe, the user can access the web page normally. Otherwise, a warning page will pop up to prevent the user from browsing.
Therefore, the comprehensiveness of the information in the database and the speed of update will have a significant impact on whether the browser can identify the phishing website. Some browser developers adopt the anti-phishing engine services from other browser developers. Below is a comparison of common browsers and the anti-phishing protection function:
| Chrome | Edge | Safari | Brave | Firefox | |
|---|---|---|---|---|---|
| Anti-phishing Function | Yes | Yes | Yes | Yes | Yes |
| Anti-phishing engine | Google Safe Browsing [4] | Microsoft Defender SmartScreen [5] | Google Safe Browsing [6] | Google Safe Browsing [7] | Google Safe Browsing [8] |
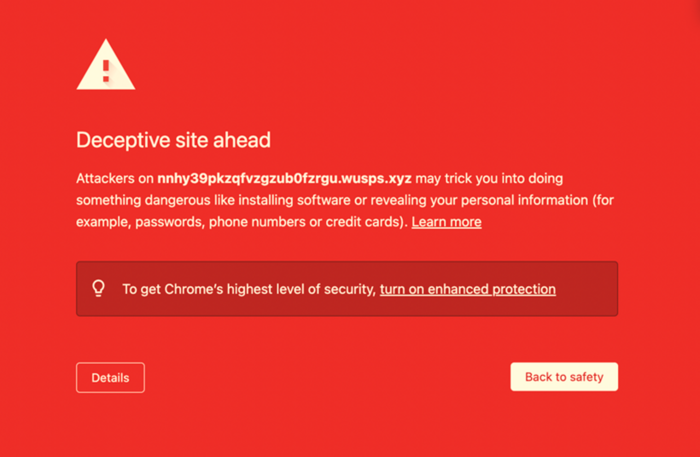
From the table above, the anti-phishing website engine is mainly divided into 2 groups: Google Safe Browsing and Microsoft Defender SmartScreen. Below is a sample warning displayed when these two engines identified a phishing site.
Google Safe Browsing
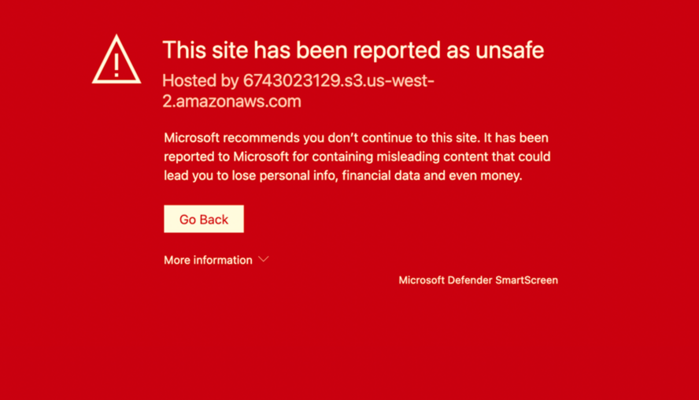
Microsoft Defender SmartScreen
Trends in phishing attacks in recent years
Phishing attack techniques have been evolving, from defrauding the users’ credentials in the past, to defrauding web cookies that is popular recently, and even the use of artificial intelligence customer service chatbot to obtain sensitive information from users.
However, although the technique has continued to evolve, it still relies on the use of similar domain name as the authentic one to trick user from accessing it. Due to the low cost and simple procedures for registering new domain names, the number of phishing website has also increased in recent years.
According to phishing intelligence organisation OpenPhish[9], there are around 1,000 new phishing websites every day. It is important for the browsers to identify them in a timely manner to protect users. In light of this, HKCERT analysed and tested the performance of anti-phishing website function of common browsers.
Test Purpose
The purpose is to test the browser with default settings for end users, record the anti-phishing performance of common browsers in desktop and mobile platform.
Test Method
For 14 consecutive working days (from July 11 to July 28), randomly select the latest phishing URLs published on that day. The URLs are provided by OpenPhish, which updates the list of phishing URL every twelve hours.。
Testing Environment and Browsers Types
Since there are two anti-phishing engines used in common browsers, HKCERT chooses one of the browsers in each engine to test it on desktop and mobile platforms.
To simulate the real usage of general users, all tested browsers use default security settings. The results are based on whether the browser, which acts as the first layer of defence, can block the phishing websites.
| Windows 10 21H2 | MacOS 12.4 | Android 11 | iOS 15.5 | |
|---|---|---|---|---|
Chrome | ✔ | ✔ | ✔ | ✔ |
Edge (Vesion 103) | ✔ | ✔ | ✔ | ✔ |
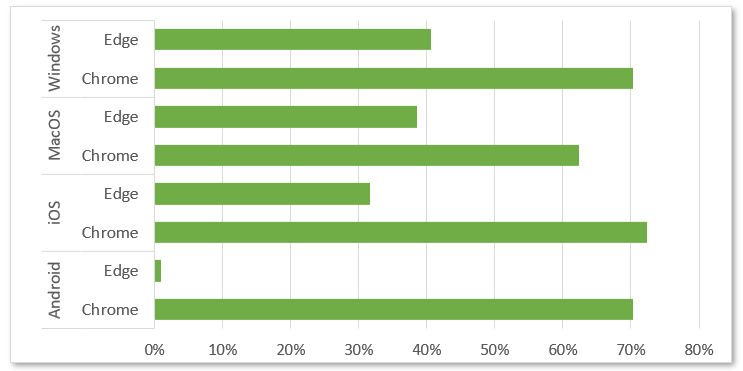
Result
| Windows | iOS | Android | MacOS | |||||
|---|---|---|---|---|---|---|---|---|
| Browser | Chrome | Edge | Chrome | Edge | Chrome | Edge | Chrome | Edge |
| Success rate of blocking latest phishing website | 70.30% | 40.60% | 72.30% | 31.70% | 70.30% | 0.99% | 62.40% | 38.60% |
1. The test results showed that Chrome achieved a higher success rate of blocking phishing websites across all platforms than Edge.
2. The same browser performs differently in the operating systems tested. This may have to with how the software vendor implements the anti-phishing website engine in specific platform.
3. Edge had a lowest success rate in Android. HKCERT has made inquiries with Microsoft in this regard, and received a reply that the problem would be fixed in a future version of the SDK. Microsoft also stressed that the test conducted by HKCERT was based on Microsoft Defender Smartscreen’s default settings, and the test results may be different if using its advised settings. It recommends users to contact the company for any inquiries.
4. In addition, HKCERT has sample tested other browsers in Android, and found that the anti-phishing performance of these browsers in different mobile brands (such as Samsung, Sony, etc.) are not consistent with the desktop version, and may even achieve a low success rate.
Recommendation and Conclusion
HKCERT recommends Android users to enable Chrome browser Enhanced Protection to enhance the success rate of blocking phishing web pages. They can refer to the following URL to enable the Enhanced Protection:
https://support.google.com/chrome/answer/9890866?hl=en&co=GENIE.Platform%3DAndroid
Since the anti-phishing function of the browser requires time to collect and analyse the phishing URLs, the successful detection rate of new phishing website would be lower.
Anti-phishing function can only reduce the chance of users accessing phishing web pages to some extent. Combining it with strong user’s cyber security awareness is the only best way to combat phishing attacks. Users are advised to:
- Pay attention to the spelling of domain names of websites and check their authenticity;
- Do not assume a website that uses HTTPS is a legitimate site. A phishing site may also use HTTPS;
- Do not click any link or open any attachment casually and do verify the legitimacy of a website before providing any personal information;
- Do not log in to your account through a link provided by email or an unknown website. Use the bookmark function of browser to save the account login link instead.
In summary, the anti-phishing function is analogous to wearing a face mask in real life. It can prevent the infection of viruses (i.e. phishing attacks), but once the virus passes through the mask, it ultimately relies on the users’ immune system (i.e. cyber security awareness) to protect oneself from virus infection.
Reference
- https://www.hkcert.org/press-centre/cyber-attacks-become-more-complex-and-diversified-phishing-attacks-reach-new-high-hkcert-calls-on-public-to-raise-awareness-of-information-security
- https://www.phishingbox.com/resources/phishing-facts
- https://www.cloudflare.com/learning/security/glossary/what-is-lateral-movement/
- https://safebrowsing.google.com/
- https://support.microsoft.com/en-us/microsoft-edge/how-can-smartscreen-help-protect-me-in-microsoft-edge-1c9a874a-6826-be5e-45b1-67fa445a74c8
- https://www.apple.com/legal/privacy/data/en/safari/
- https://brave.com/privacy/browser/
- https://support.mozilla.org/en-US/kb/safe-browsing-firefox-focus
- https://openphish.com
Related Tags
Share with
