
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the fourth quarter of 2019.
Nowadays, many networked digital devices, such as computers, smartphones, tablets, are being compromised without the user's knowledge. The data on them may be mined and exposed every day, and even be used for various criminal activities.
The Hong Kong Security Watch Report aims to raise public awareness of the problem of compromised systems in Hong Kong, enabling them to make better decision in information security. The data in this quarterly report focuses on the activities of compromised systems in Hong Kong which suffer from, or have participated in various types of cyber attacks, including web defacement, phishing, malware hosting, botnet command and control centres (C&C) or bots. "Computers in Hong Kong'' refer to those whose network geolocation is Hong Kong, or the top level domain of their host name is ".hk'' or “.香港”.
Correction Notice
In the earlier published report, there was an error in the Botnet (Bots) security events. The number of security events of Nymaim, Virut, ZeroAccess, Pushdo, Nivdort, Bedep and Corebot bots were missing. The affected contents in the report are as below:
- The total number of Botnet (bots) security events should be 7,878 instead of 6,831 in Table 2 and Figure 4.
- The total number of Nynaim and Virut security events were 786 and 175 respectively, ranked 3rd and 6th in major
botnet families in Hong Kong network in Figure 12 and Table 3. - The quarterly figures of Nynaim bot should make it as one of Top 5 botnet families in Figure 13 and Table 4.
All related contents of this report have been corrected.
Highlight of Report
In 2019 Q4, there were 9,911 unique security events related to Hong Kong used for analysis in this report. Data were collected through IFAS1 with 11 sources of information2, and not collected from the incident reports received by HKCERT.
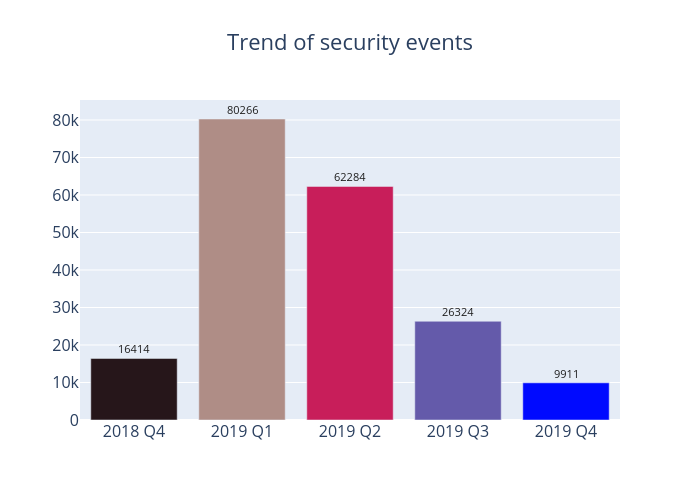
Figure 1 –Trend of security events
In the last quarter of 2019, all types of security events have fallen back to relatively low levels as the total number of security events amounted to 9,911, down almost two-thirds on the previous quarter’s figure. The most notable decline was seen in malware hosting events, which fell by more than 93%, while a 70% decrease was reported in phishing events.
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trends and distributions are summarised below:
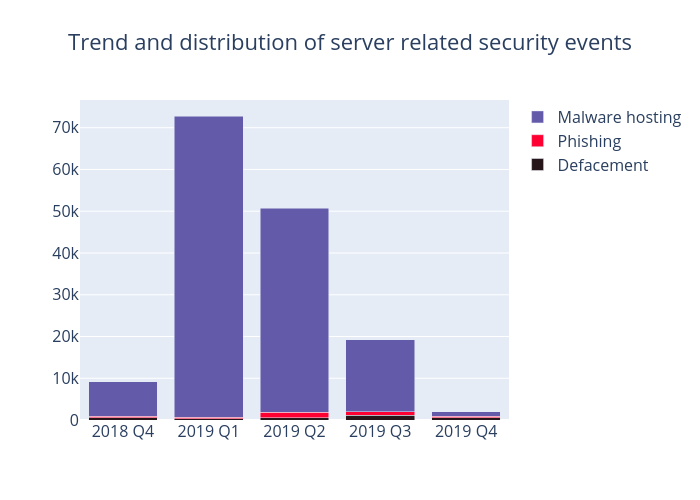
Figure 2 –Trend and distribution of server related security events
| Event Type | 2018 Q4 | 2019 Q1 | 2019 Q2 | 2019 Q3 | 2019 Q4 |
| Defacement | 590 | 318 | 532 | 1,120 | 591 |
| Phishing | 365 | 289 | 1,306 | 849 | 257 |
| Malware Hosting | 8,152 | 72,201 | 48,892 | 17,273 | 1,185 |
Table 1–Trend and distribution of server related security events
As shown in Table 1, having reached a peak of 72,201 events in the first quarter of 2019, malware hosting fell continuously to the lowest point of the year with 1,185 events only. The number of malware hosting IP addresses involved has also dropped sharply to 63, the first time since the first quarter of 2018 that double digits are recorded for its occurrence.
Phishing events also declined by nearly 600, while the number of phishing IP addresses involved fell from 196 in the previous quarter to 55. After analysing the data, we observed that while Apple iCloud continued to be the main target of such attacks, eBay-related phishing events have also increased. The rise might be attributed to the end-of-year sales, with fraudsters usually taking this opportunity to conduct phishing attacks against the branded online shopping platforms.
Meanwhile, defacement events and the number of defacement IP addresses involved fell by nearly half and 36% in this quarter respectively. Further analysis of these IP addresses in Zone-H and Shodan
3 revealed that around a quarter of servers on these IP addresses still carry security vulnerabilities, and some of them are even using End-of-Support (EOS) operating systems, which are deemed the possible main causes of defacement incidents.

| HKCERT urges system and application administrators to protect the servers. |
- Patch server up-to-date to avoid the known vulnerabilities being exploited
- Update web application and plugins to the latest version
- Follow best practice on user account and password management
- Implement validation check for user input and system output
- Provide strong authentication e.g. two factor authentication, administrative control interface
- Acquire information security knowledge to prevent social engineering attack
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving a small number of powerful computers, mostly servers, which give commands to bots
- Botnet security events - involving a large number of computers, mostly personal computers which receive commands from C&Cs.
Botnet Command and Control Servers
The trend of Botnet C&C security events is summarised below:
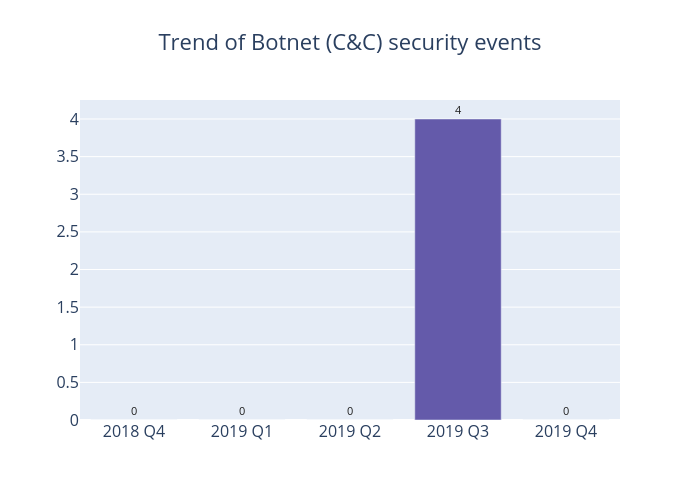
Figure 3 –Trend of Botnet (C&Cs) related security events
There was no Botnet Command and Control Centers (C&C) security events in this quarter.
Botnet Bots
The trend of botnet (bots) security events is summarised below:
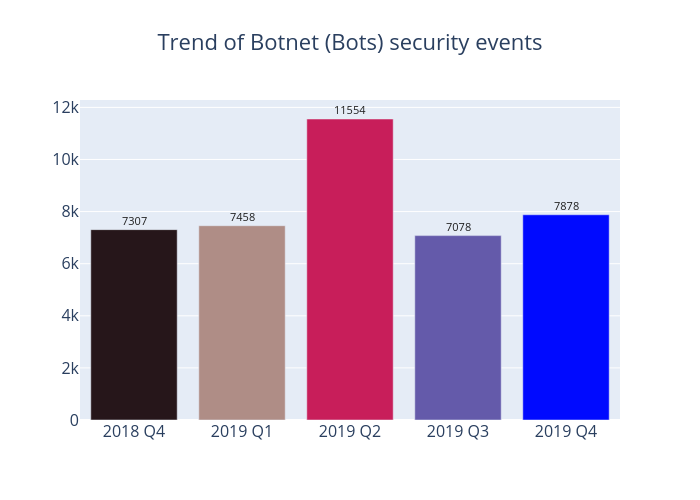
Figure 4 - Trend of Botnet (Bots) security events
In 2019 Q4, the number of Botnets (bots) in Hong Kong network has increased by 11.3%, or 800. Most Botnet events show a downward trend, with WannaCry bots falling by nearly half to just 354. On the other hand, both Nymaim and Avalanche bots have hiked dramatically by more than 6 and 3 times respectively (see Table 3). Avalanche is a cyber crime hosting platform serving multiple malware families. Hackers can use it to deliver various malwares (such as Nymaim, Gamarue, Tinba, and Matsnu, etc.). After further analysis, it emerged that the number of unique IP addresses attemping to connect the Avalanche sinkhole from the end of November to December was persistently high, which was consistent with the rising trend shown by Nymaim sinkhole data. In addition, by comparing the Avalanche Botnets data of the previous three quarters, there have been notable increases in Nymaim and Matsnu malware events. These two malwares are trojan and both can be used as a springboard for further intrusions, such as ransomware attacks.

| HKCERT urges users to protect computers so as not to become part of the botnets. |
- Patch their computers
- Install a working copy of the security software and scan for malware on their machines
- Set strong passwords to avoid credential based attack
- Do not use Windows, media files and software that have no proper licenses
- Do not use Windows and software that have no security updates
- Do not open files from unreliable sources
|
HKCERT has been following up the security events received and proactively engaged local ISPs for the botnet cleanup since June 2013. Currently, botnet cleanup operations against major botnet family Avalanche, Pushdo, Citadel, Ramnit, ZeroAccess, GameOver Zeus, VPNFilter and Mirai are still ongoing.
HKCERT urges general users to join the cleanup acts, ensuring their computers are not being infected and controlled by malicious software, and protecting their personal data for a cleaner cyberspace.

| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 Shodan is a search engine for Internet-connected devices: https://www.shodan.io/






