Trust of website certificate questioned - reflection of the Comodo and DigiNotar incidents
We are educated to check the validity of a website when we need to provide sensitive information to them, e.g. online banking, webmail, by identifying the "padlock" (i.e. secure HTTPS connection) and the name of the organization shown beside the URL in the browser.
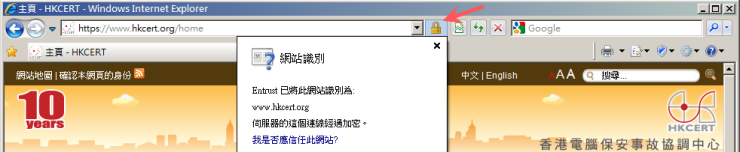
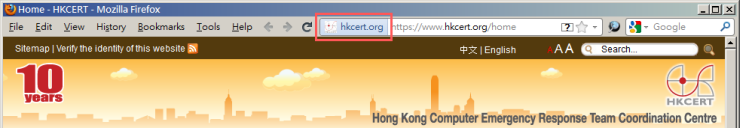
We trust our browser to tell us whether the website is genuine. However, would you wonder if one day the browser could not be trusted? The Comodo and DigiNotar incidents tell us this trust cannot always be taken for granted.
Source of all trust - certificate authority
Suppose Bank ABC owns a website on www.abcbank.com.
- They declare that www.abcbank.com belongs to them by getting a digital certificate with the domain www.abcbank.com written on the certificate.
- The certificate is embedded in the website.
- When a browser accesses www.abcbank.com, it will check whether the domain written on that embedded certificate matches the URL which the browser is accessing.
- If they match, the browser will indicate the website as genuine.
As you see, the bank should get their certificate from a trusted party. That party is called "certificate authority" (CA), which issues certificate signed with its "root certificate" for the sake of proving identity. When browser verifies a certificate, it must first check whether the certificate is issued by a CA which is trusted (i.e. signed) with CA's root certificate.
The information of trusted CAs and their root certificates are managed by the OS (e.g. Windows, Mac, Linux) or the browser (e.g. Firefox, Chrome). The information are the source of all trust.
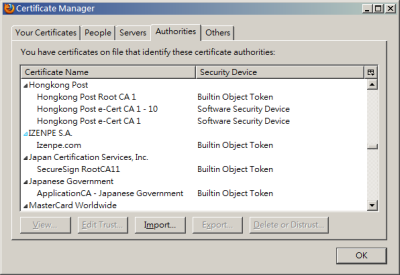
But what if someone can cause a trusted CA to issue fake certificates? That is how the "Comodo and Diginotar incidents" come into the scene.
Fake certificates in reality - Comodo and Diginotar incidents
In Mar and Sep 2011, two CAs Comodo and Diginotar were reported being hacked. Fake certificates were being issued under their name to spoof Google and Yahoo. There were already victims whose Google or Yahoo accounts were compromised. Because hackers set up phishing sites with certificates issued by a genuine trusted CAs, the browser could not warn the users about the phishing sites as usual.
To response to those incidents, OS and browser vendors issue patches swiftly to remove the CAs from their list. Under such verification process, this is the only way to protect users. To prevent you from becoming a victim:
- You should now check whether you have applied the latest patches to your OS and browsers. Check our blog and security bulletin to get more details.
- Patches for mobile devices addressing the incidents are not yet available, so you should avoid performing sensitive online transactions in those devices.
- As usual, always have the necessary basic protection measures on your computer to deter any malware, which may also be able to inject fake root certificates into your OS and browser.
Share with
