DigiNotar CA security breach resulting in issuance of fake certificates
DigiNotar, a Dutch Certificate Authority (CA) reported that their company had a security breach in July 2011 which resulted in fraudulent issuance of public key certificates. DigiNotar issues SSL (Secure Sockets Layer) and EVSSL (Extended Validation) certificates. When a user visits a website, the web browser helps validating the legitimacy of the website by examining the identity presented against the certificate.
Impact
DigiNotar admitted that fake certificates were issued for Google, Yahoo, Mozilla, Wordpress and the TOR project. The extent of impact is still unclear as the incident is still under investigation.
A web browser is designed to validate if a certificate is signed by a trusted CA. The fake certificates compromise such trust and may allow fraudsters to conduct man-in-the-middle attack in encrypted communications.
Vasco, the parent company of DigiNotar, issues security tokens for two-factor authentication used by online businesses. Vasco stated in the press release that “the technological infrastructures of VASCO and DigiNotar are completely separated, meaning that there is no risk for infection of VASCO’s strong authentication business.”
Solution
1. Revoke DigiNotar root certificate
Google, Microsoft and Mozilla have announced security update to revoke DigiNotar root certificate.
- Mozilla Firefox has released an update for Firefox, Thunderbird and SeaMonkey
http://blog.mozilla.com/security/2011/08/29/fraudulent-google-com-certificate/ - Microsoft Security Advisory (2607712)
http://www.microsoft.com/technet/security/advisory/2607712.mspx - Chrome released an update 13.0.782.218
http://googlechromereleases.blogspot.com/2011/08/stable-update.html
MacOS users may delete DigiNotar root certificates manually.
- Go to /Application/Utilities. Start Keychain Access.
- In the Keychain pane select “System Roots”
- Search for “DigiNotar Root CA” certificate.
- Choose “Delete” from the “Edit” menu. You’ll be prompted for an admin username and password.
- Ensure the “DigiNotar Root CA certificate” is deleted.
Note: it has been reported that distrusting DigiNotar certificate does not work for EVSSL certificates in MacOS. So deletion of DigiNotar root certificate is the only solution.
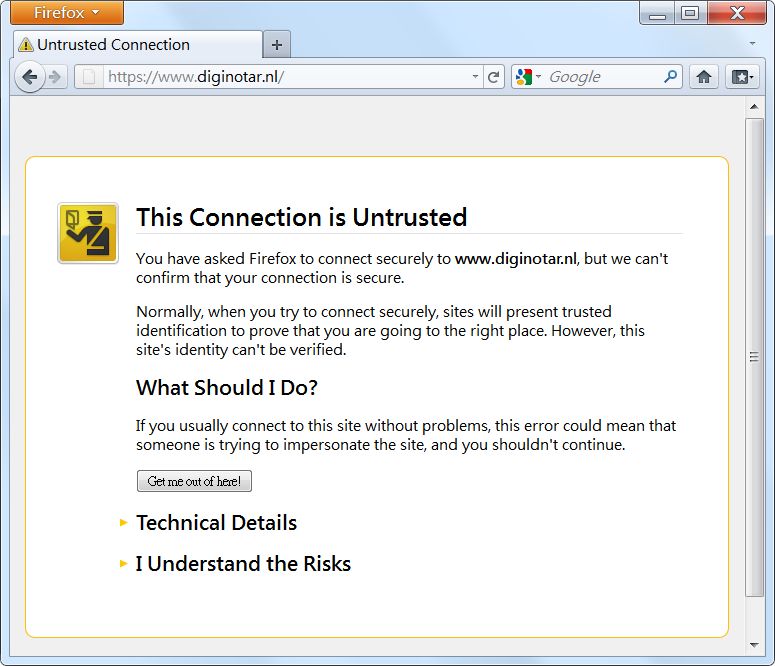
2. After revoking DigiNotar root certificate, visit the DigiNotar SSL website (https://www.diginotar.nl) to verify. The browser should warn you (as illustrated below) that the website certificate is problematic or that the connection to the website is untrusted.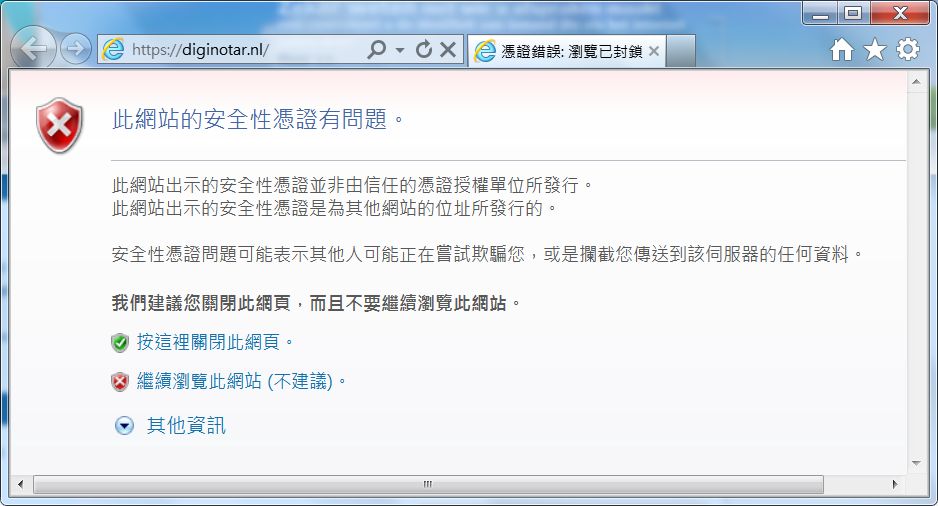
Reference
Vasco press release (30 August 2011): DigiNotar reports security incident
http://vasco.com/company/press_room/news_archive/2011/news_diginotar_reports_security_incident.aspx
Steps to disable trust of the DigiNotar root CA in MacOS
http://www.coriolis-systems.com/blog/2011/08/diginotar-certificate-security.php
Mac OS X Can't Properly Revoke Dodgy Digital Certificates
http://www.pcworld.com/businesscenter/article/239269/mac_os_x_cant_properly_revoke_dodgy_digital_certificates.html
Share with
