Taking Security Best Practice During Festive Season
Heading to the year's end means that most people would plan their long holidays to gather with families and friends, buy new goods, or travel abroad. Online services have become more and more popular. We should stay vigilant on cyber security risks during the festive season while we enjoy the convenience.

Phishing Attacks
In addition to buy goods to be festive presents, people can pay for their trip online to receive sales and discounts for flights and hotels in the Internet. Hackers may find this as the opportunity to launch attacks towards the Internet users. From the hackers’ point of view, launching phishing attacks would be low-cost and low-effort tactics when compared to launching other kinds of cyber attacks. Generally, people would easily get tricked and fall into the trap of phishing attacks because hackers can easily create phishing content that looks very similar to the official one, which is not easy to distinguish. From sending a phishing message or email, hackers aim to trick the targeted user to open a malicious URL link or even a malicious attachment that may contain malware. Recent phishing attacks in Hong Kong have been observed that hackers have been creating phishing pages impersonating local membership platforms. They were tricking users into entering login credentials on the phishing page and stealing sensitive information, such as credit card information, from the account after a successful login. Below is an example of recent discovered phishing webpage impersonating the common membership platforms in Hong Kong.
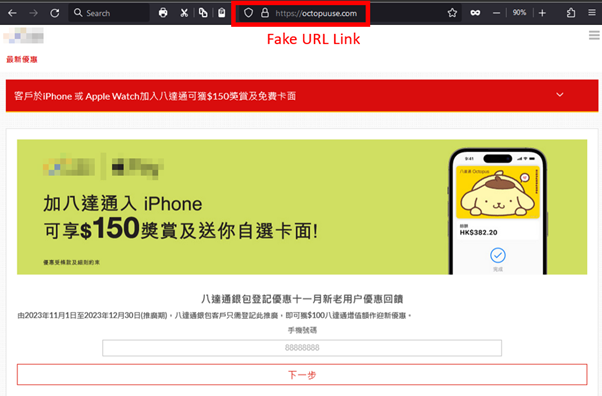
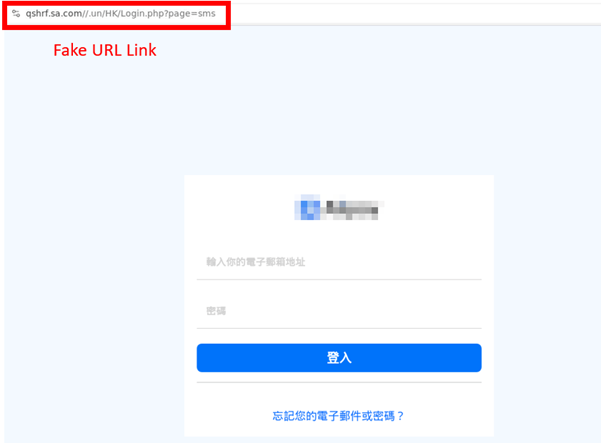
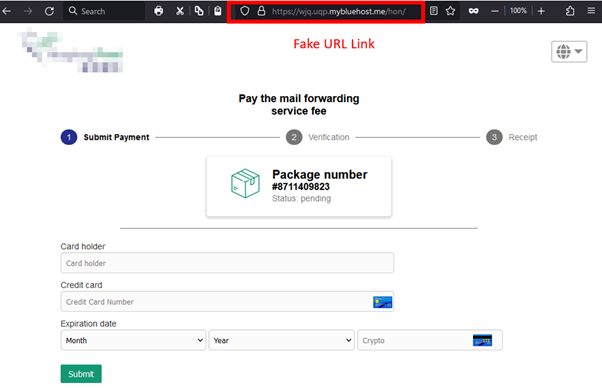
Besides of phishing websites, many fake travel and retail agencies have appeared on social media pages, offering a large number of discounts such as “Big Sale”, “Up to 70% off”, “Limited-time/Limited-quantity promotion at 90% off”, etc, to attract citizens to inquire and defraud them of their money and a large amount of personal information, including name, ID card, credit card information, phone number, and family information. How can citizens distinguish whether the social media pages and the contents of their advertising messages are genuine or not? In addition to paying attention to the blue verification badge or the blue tick mark, the number of likes and followers on the page, they can also keep an eye on the following points to prevent online shopping scams:
- The pixels of the company logo or image are low: Most of the images used by hackers are obtained by screenshots or stolen from other websites, and they are not the original images, so the pixels are lower. In addition, citizens could use Google Images to search if similar photo was found on other websites.
- Contact information is not detailed: The contact information displayed is not detailed, and the provided contact information is personal email or phone.
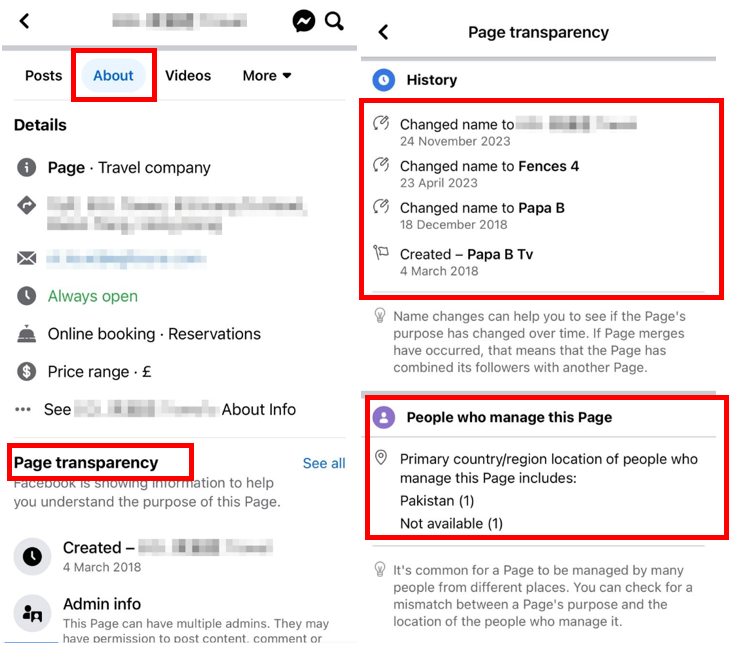
- The location of the management personnel is overseas: Citizens can check the location of relevant management personnel through this path "About" > "Page transparency" on the page. If the location of some management personnel is different from the location of the page, it is necessary to be vigilant about the authenticity of the page.
- Whether the page name is frequently changed and the establishment time: Fake pages often change their names and are established for a short period of time because their fraud methods are different each time.
Photo Caption 1: Citizens can check the location of management personnel and establishment time through this path "About" > "Page transparency" on the page |
- The page only has a small number of posts: Most of the posts on fake pages are copied from the past one to two months.
- Abnormal amount of likes/comments: Pay attention to whether the likes/comments come from countries outside the target group and whether the content of the comments is roughly the same.
To learn more about phishing attacks and how to prevent them, HKCERT has introduced a thematic page, “All-Out-Anti-Phishing”. The public can visit the page with all essential information about phishing, including attack techniques, prevention, identification, and handling procedures for suspicious messages, as well as highlighting some important points to note.
Identify/Credential Theft
Other than launching phishing attacks to lure users to provide personal information, hackers could expand their scale of attacks if they successfully stole the users’ login credentials. This let hackers to impersonate the user to launch attacks to their families and friends. Especially during holidays, it is not surprising to receive messages from friends with whom you rarely communicate, and therefore, our vigilance may be lowered. Hackers can launch identify attacks in various ways, including Adversary-in-the-middle (AiTM) Attacks, Fake Ads, Social Engineering Attacks, etc. Most hackers would aim to compromise a targeted user’s account and perform malicious activities within the compromised account. The recent tactic of Identify Attack is that hackers would create fake WhatsApp login sites and push the malicious webpages to the top of the search results in search engines. If users carelessly browsed the malicious webpages and conducted login action, hackers could obtain the account session and gain access to all of the information in the WhatsApp account to launch further attacks.
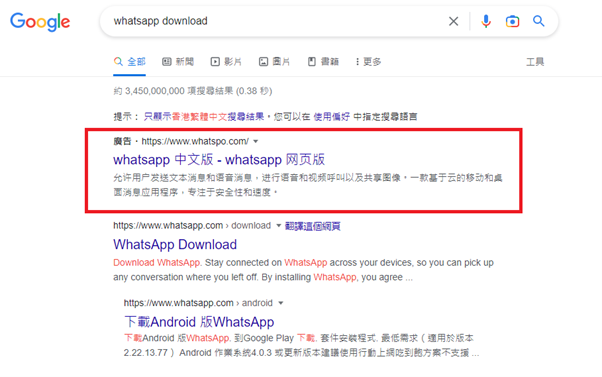
To understand more about identity credential theft, please visit the blog article “Do you know what is Identity/Credential Theft?” here.
Security Best Practices
To have safer travel and enjoy shopping with less worries in the digital era, people should consider following the security best practices below.
For security best practices when travelling abroad:
- Use personal device to log into personal accounts and avoid using public devices;
- Use trusted public Wi-Fi connections, avoid to connect to Wi-Fi hotspots with low security settings;
- Check any malicious logins in your online accounts;
- Check carefully when purchasing goods using mobile payments; verify the payment receiver and the amount before confirming and proceeding with the payment;
- If required to access a webpage or scan QR code, verify if the URL of the website is legitimate before entering any information;
- Do not open any links or attachments sent to overseas SIM cards. It might be related to phishing attacks;
- If necessary, install applications only from official websites and app stores;
- Do not charge your device at unknown public charging port to avoid Juice Jacking attacks;
- Do not leave your device unattended; and
- Power off your devices at home and office if they are no use, and power off your portable devices when it is not in use overnight during travel.
For security best practices when shopping online:
- Don't click on any links or attachments from an unknown sender. Always enter the URL of the online shopping platform directly in your browser or use bookmarks. Be careful with the legitimacy of the links and emails. For example, check for spelling and grammatical errors in the URL, or whether the sender is trustworthy. If the website does not use HTTPS for encryption, please be careful and do not provide sensitive information;
- Change the account password of the online shopping platform regularly. Use different passwords for different accounts to prevent a cascading impact if one of them is compromised;
- If the platform supports multi-factor authentications, enable it to enhance security;
- Place orders or check order status from the official website or mobile app only;
- Do not save any sensitive information, such as credit card information, in online accounts;
- Check your online payment records regularly for suspicious transactions;
- If you receive a suspicious email or instant message, please verify the details at official channels. Do not provide sensitive information to an unknown sender;
- Adopt anti-phishing features in web browsers to help block phishing attacks, and
- Use the free search engine “Scameter” of Cyberdefender.hk to identify frauds and online pitfalls through email, URL or IP address, etc.
Related Tags
Share with