Do you know what is Identity/Credential Theft?
Cyber theft of identity and credentials is not a new phenomenon. However, the COVID-19 pandemic has accelerated people’s growing reliance on online services for work and personal tasks, creating more opportunities for cyber criminals to steal our personal information for their own gains. As a result, HKCERT has made Identity/Credential Theft one of the top five information security risks for 2023.

Introduction
To improve public awareness of identity security, this article will aim to define cyber attacks on identity and analyse the trend of such attacks in recent years. It will also introduce several identity attack methods that are popular at present. After understanding these techniques, you will have better knowledge on how cyber criminals conduct this attack, and the timely precautions you could take upon encountering similar situation.
What are Identity Authentication and Identity Attack
Identity Authentication refers to the process of validating authorisation to access information or services. It is used to confirm and ensure users have permission to access the information or services. The most common example of identity authentication is the use of username and password login. Thanks to technology advancements, fingerprints and faces can now be used for identity recognition as well. Although most authentication techniques are trustworthy, they may have limitations whom cyber criminals can take advantage of to launch attacks.
As for Identity Attack, as its name implies, it is an attack on identity authentication, using credentials as attack vectors to obtain passwords, keys, session tokens, account information and other personal information to impersonate users’ identities. If those high-privileged identity in an organisation is stolen, it can be used for different malicious acts, such as distributing ransomware or invading the system to steal confidential files, etc., resulting in greater losses.
Trends in identity attacks in recent years
Phishing has been one of the most popular types of identity attacks that have occurred at increased frequency recently. In the latest quarterly report of the Hong Kong Security Watch Report released by HKCERT, local phishing events have exceeded 10,000 for the first time, totalling 13,574 in 2022 Q4, with a quarter-on-quarter increase of 90% and a year-on-year increase of over 11 times[1]. The proliferation of such attacks has been attributed to the spread of open-source phishing toolkit such as Evilginx2 which can evade multi-factor authentication (MFA) for session hijacking. It can be seen that attacks against identity are rife, and are expected to remain a major threat to cyber security in the foreseeable future.
Identity attacks in various ways
Attacks against identity come in various forms. Learning more about them could protect you from falling victims to these scams.
- Adversary-in-the-middle (AiTM) Attack
Cyber criminals will send links to phishing websites that are similar to the actual website via emails, SMS and other channels to deceive individuals into signing in. The login requests are proxied to and from the actual website, allowing cyber criminals to bypass their victim’s multi-factor authentication (MFA). After successful authentication, the victim is sent to the actual website to continue browsing, whereas in the background, cyber criminals have already obtained account information and Session Cookies for use in illicit activities.
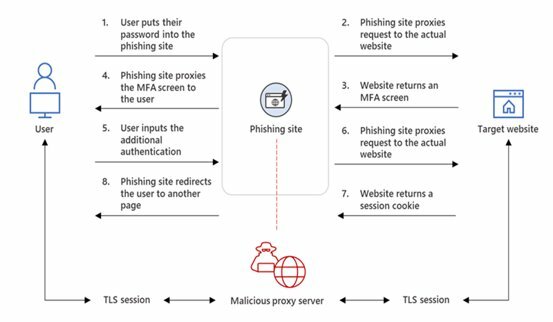
Figure 1: AiTM phishing website intercepting the authentication process
- MFA Fatigue
Cyber criminals will use various means, such as utilising breached data or brute-force attacks, to continuously test possible password combinations to find out account passwords[2]. Then they will repeatedly bombard their targets with identity verification confirmation prompts until the requests are accepted.
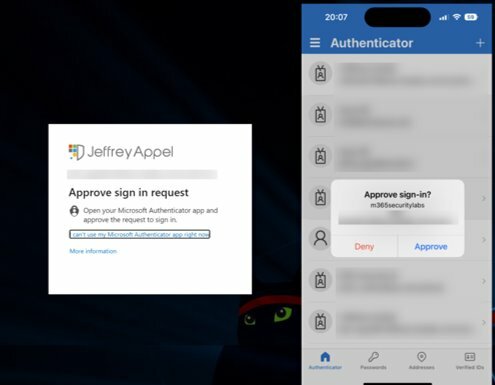
Figure 2: Microsoft authentication page
Source: https://jeffreyappel.nl/mfa-prompt-spamming-mfa-fatigue-what-can-you-do-to-prevent-detect-attacks/
- Fake Ads
Cyber criminals will use Google Ads to push malicious websites to the top of the search result, misleading users to believe as trusted websites. Such malicious websites may entice users to download and install malicious applications or engage in AiTM phishing.
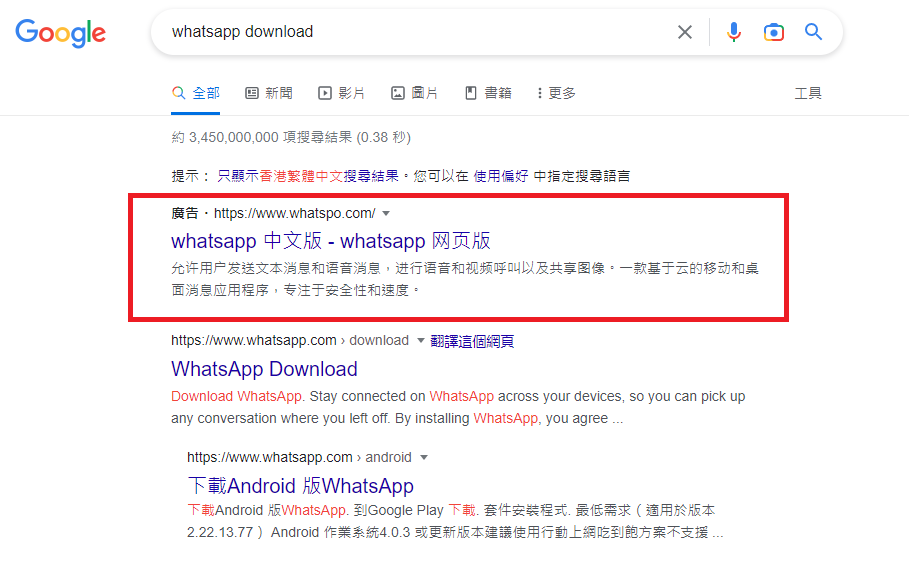
Figure 3: Pinned malicious websites (circled in red)
Source: Google Search Engine (such fake ads had already been removed)
- OAuth phishing attack
Cyber criminals deceive users to permit malicious applications, allowing them to access account information and perform actions through OAuth 2.0 application. Once the malicious applications obtain the permissions, it can access user data anytime. Microsoft has also cautioned O365 users to be alert about this kind of authorisation [3].

Figure 4: OAuth apps gain permission by displaying a “Permissions requested” dialog
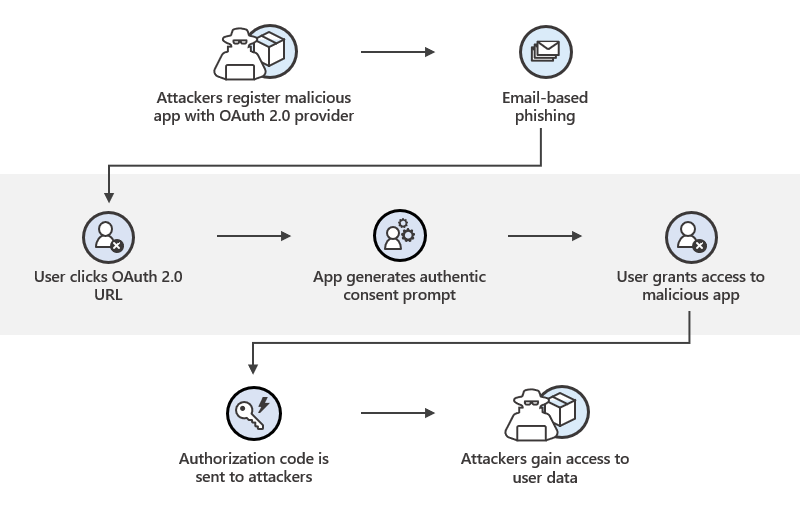
Figure 5: OAuth “Consent” phishing attack flow
- Social Engineering Attack
Cyber criminals will take advantage of people’s empathy to conduct fraud. For example, they may examine the victims’ social media posts to learn about their background and then pose as their friends or acquaintance to obtain their victims’ personal information for illegal activities.
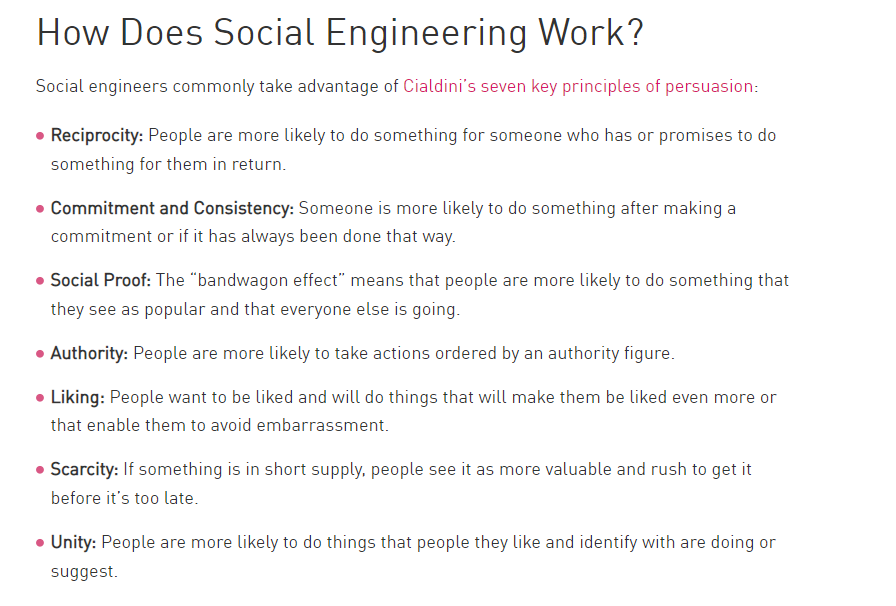
Figure 6: How Does Social Engineering Work
Source: https://www.checkpoint.com/cyber-hub/threat-prevention/social-engineering-attacks/#HowDoesItWork?
Example: Adversary-in-the-middle (AiTM) attack Facebook Accounts
Below is an example of the AiTM attack, cyber criminals use open-source tools to reproduce a fake Facebook login page to steal account information. Open-source phishing toolkit and Typosquatting [4] are used in the fake login page to provide a more genuine appearance of the page. While users are inputting their account information and completing MFA on the fake page, cyber criminals would obtain their account information and Session Cookies in the backend. Cyber criminals then use the captured information to login the victims’ accounts and commit fraud to victims’ friends and family.
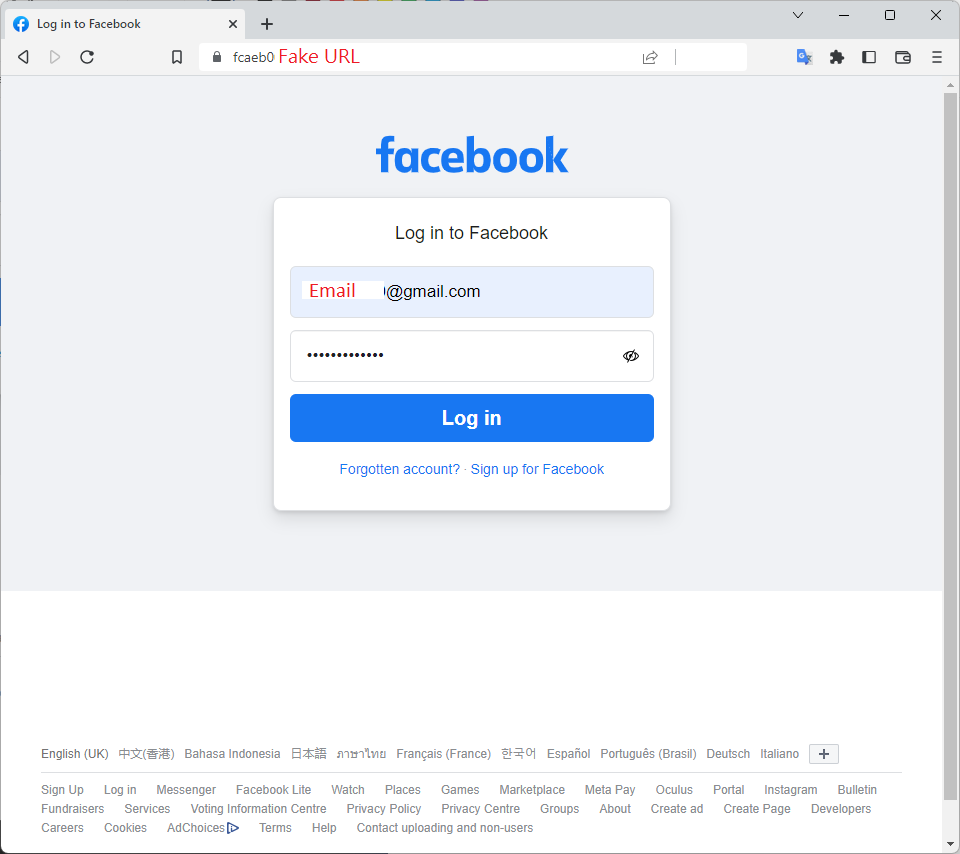
Figure 7: Phishing website that used Typosquatting to deceive users to enter credentials and MFA
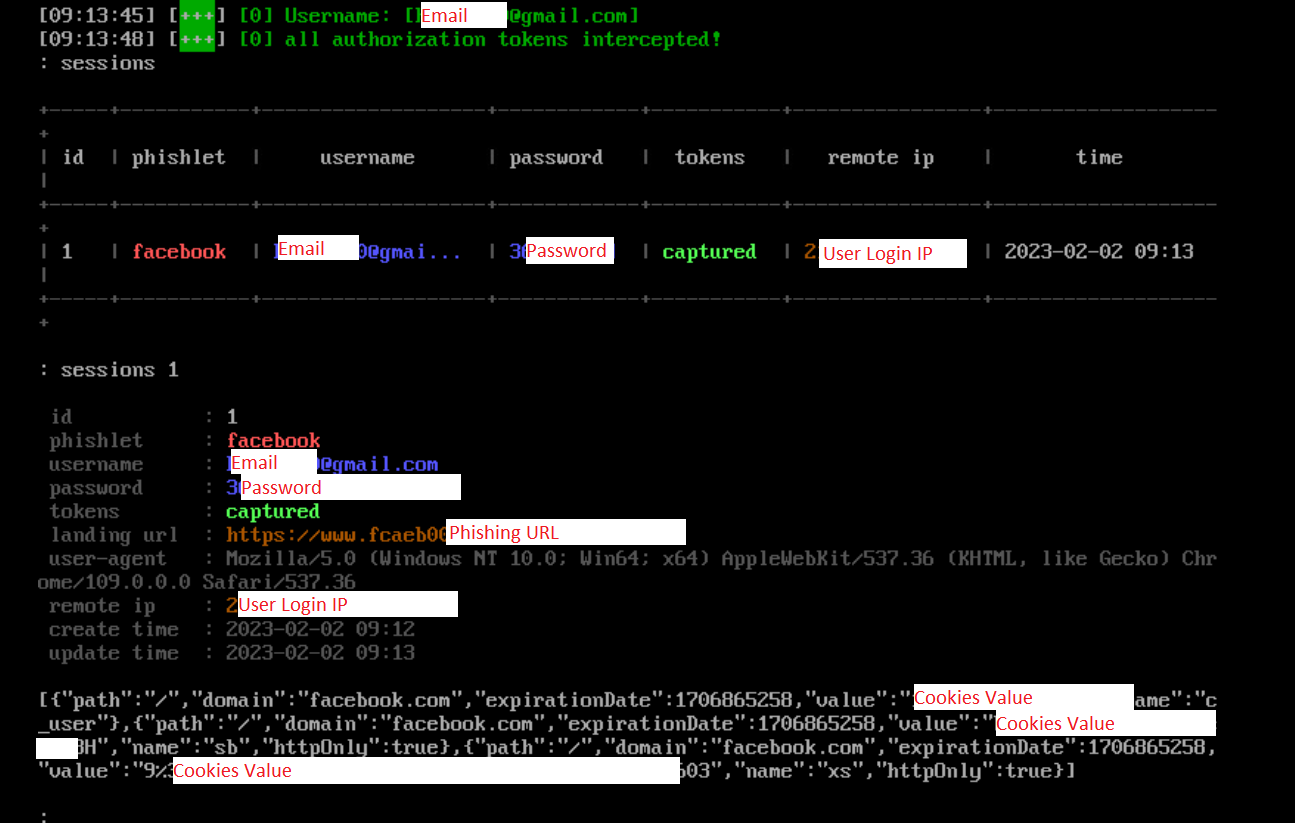
Figure 8: Cyber criminals obtain account information and Session Cookies in backend
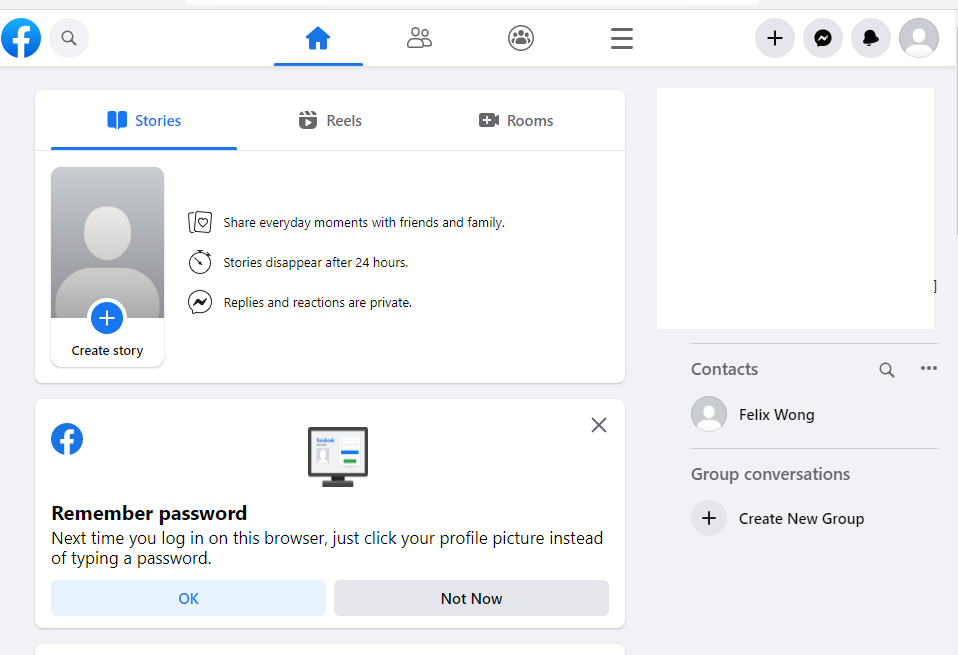
Figure 9: Cyber criminals use obtained credentials and Session Cookies to login users’ account successfully
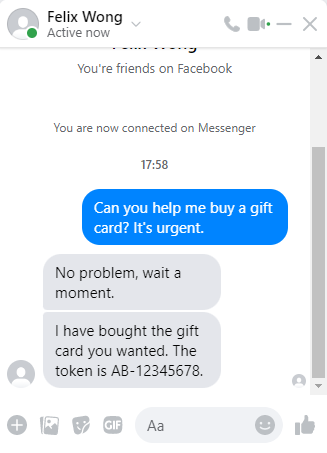
Figure 10: Contact users’ friend to defraud money
Conclusion and Recommendation
With continued technology advancements, these identity attack methods will become more diverse. To prevent the theft of personal information or accounts, extra vigilance is required when using online services. To this end, HKCERT offers the following security advice:
- Do not assume websites that use the HTTPS protocol are authentic and credible;
- Never assume all the search engine results are legitimate;
- Carefully check the spelling of the URL, and verify the authenticity of the website;
- Do not open any URLs or attachments from suspicious emails or SMS; use the “Scameter” of Cyberdefender.hk to identify frauds and online pitfalls through email, URL or IP address, etc.
- Carefully consider before providing personal information to any person or organisation;
- Use hardware-based FIDO (Fast IDentity Online) password-free login authentication;
- Avoid using the same account and password for different platforms or services;
- Logout and close the browser after using the online service.
Reference:
- https://www.hkcert.org/tc/watch-report/hong-kong-security-watch-report-q4-2022
- https://www.fortinet.com/resources/cyberglossary/brute-force-attack
- https://www.zdnet.com/article/microsoft-warns-about-this-phishing-attack-that-wants-to-read-your-emails/
- https://support.microsoft.com/en-us/topic/what-is-typosquatting-54a18872-8459-4d47-b3e3-d84d9a362eb0
- https://cyberdefender.hk/en-us/scameter/
Share with



