Malicious Information Gathering - Now I See You
The rapid development of information and communication technology, coupled with the COVID-19 pandemic, has led to an increasing demand for Internet usage. While online shopping and investment have become part of life for the general public, SMEs are building their own computer network systems or use cloud services to handle their daily business and transactions. As a result, a lot of valuable information can be accessed on the networks and systems, resulting in frequent cybercrimes and hacking incidents.
We often hear about hackers attacking other people's servers, but how do they do it? Of course, hackers carry out network attacks in various ways, such as launching phishing attacks, or sending malware to users. But often before the attack, the hacker will do some reconnaissance and research to collect intelligence. This time, we will dissect the behaviour of one of the hacker’s approach - Malicious Scan.

What is the Malicious Scan?
"Malicious Scan", as the name suggests, is scanning against the victim’s networks and systems unauthorisedly .
First of all, hackers would use a port scanning tool to scan a large number of target companies' domains at the same time to see if the company's servers have network ports opened that could be used for exploitation. Ports can be viewed as a network entry point. They are presented with a number and function. The following are some common examples.
- Port 20:File Transfer Protocol (Transfer data) (FTP)
- Port 21:File Transfer Protocol (Control) (FTP)
- Port 22:Secure Shell (SSH) and Secure File Transfer Protocol (SCP/SFTP)
- Port 23:Telnet
- Port 25:Simple Mail Transfer Protocol (SMTP)
- Port 80:Hypertext Transfer Protocol (HTTP)
- Port 443:Hypertext Transfer Protocol Secure (HTTPS)
When hackers successfully collect the relevant intelligence, they will try to connect to the port remotely to conduct the attacks, such as using password brute force attacks to gain access, or continue to collect and attack to the system vulnerabilities for intrusion. The following example is the screen of the port scanning tool. It showed that ports 21, 22, 25 and 80 are opened, which means that hackers can use these “entrance” to conduct network intrusions (Figure 1).
Figure 1. Port Scanner
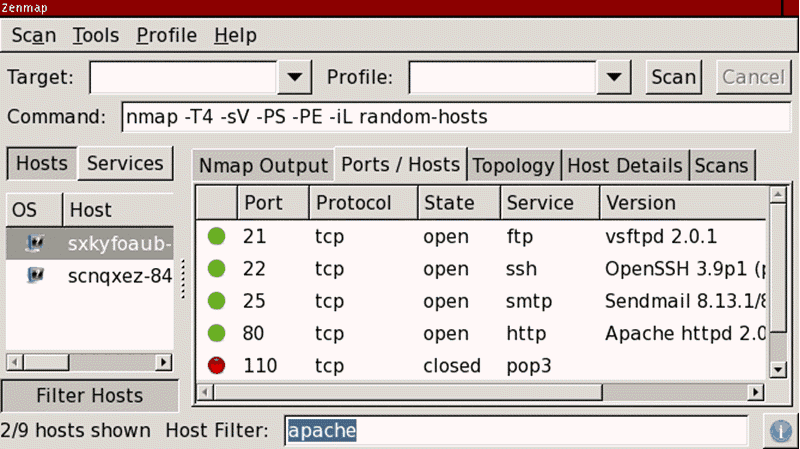
Source: https://phoenixnap.com/kb/nmap-scan-open-ports [1]
If the target is a web server (port 80 or 443 is opened), hackers can also brute force the directories and file names on the web server through directory scanning tools. The tool will try to append commonly used directories and files name (for example: /index.php, /login.php or /images/) to the end of the URL in order to check what further information could be collected in the reconnaissance stage (Figure 2).
Figure 2. OWASP DirBuster
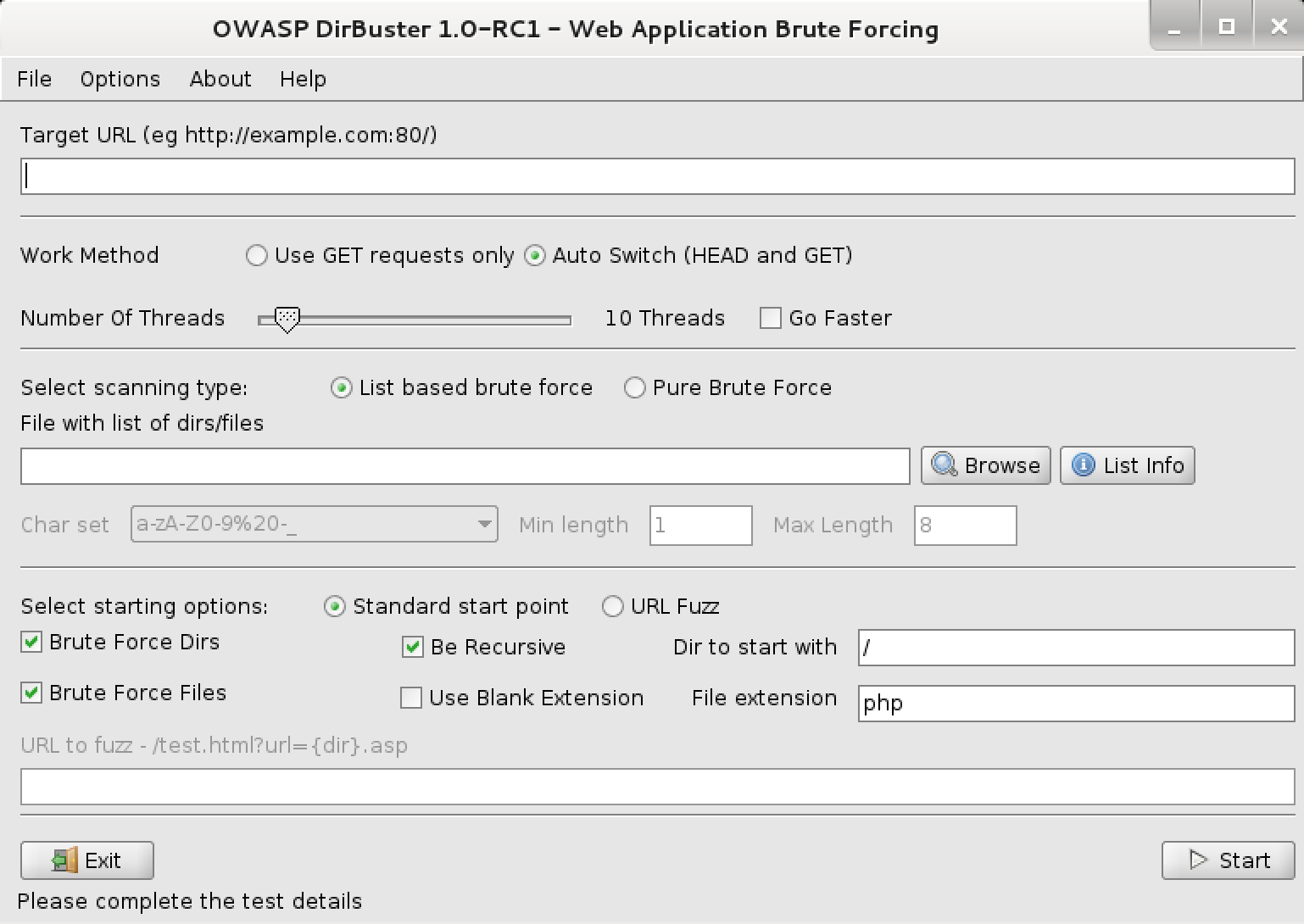
Source: https://www.kali.org/tools/dirbuster/[2]
Learn about Brute Force Attack Methods
Brute-force attack is a popular method of password cracking. This attack accounts for 5% of security breaches worldwide. It involves guessing the usernames and passwords in order to gain unauthorised access to the system. The principle is simple but the success rate is high. Some advanced hackers use automated tools or scripts for brute forcing. In other cases, hackers try to access web applications by searching for the active session ID. Hackers use this approach to steal information, plant malware to websites or disrupt services.
In 2021, NordPass, a password management company, conducted a research and published 200 commonly used passwords used. It was found that the first 10 passwords on the list had been used over 9,000,000 on average (Figure 3). Although some passwords consist of 10 characters, it only takes less than 1 second for hackers to crack these kind of simple combinations. The detailed list is as follows:
Figure 3. Top 10 Commonly Used Passwords
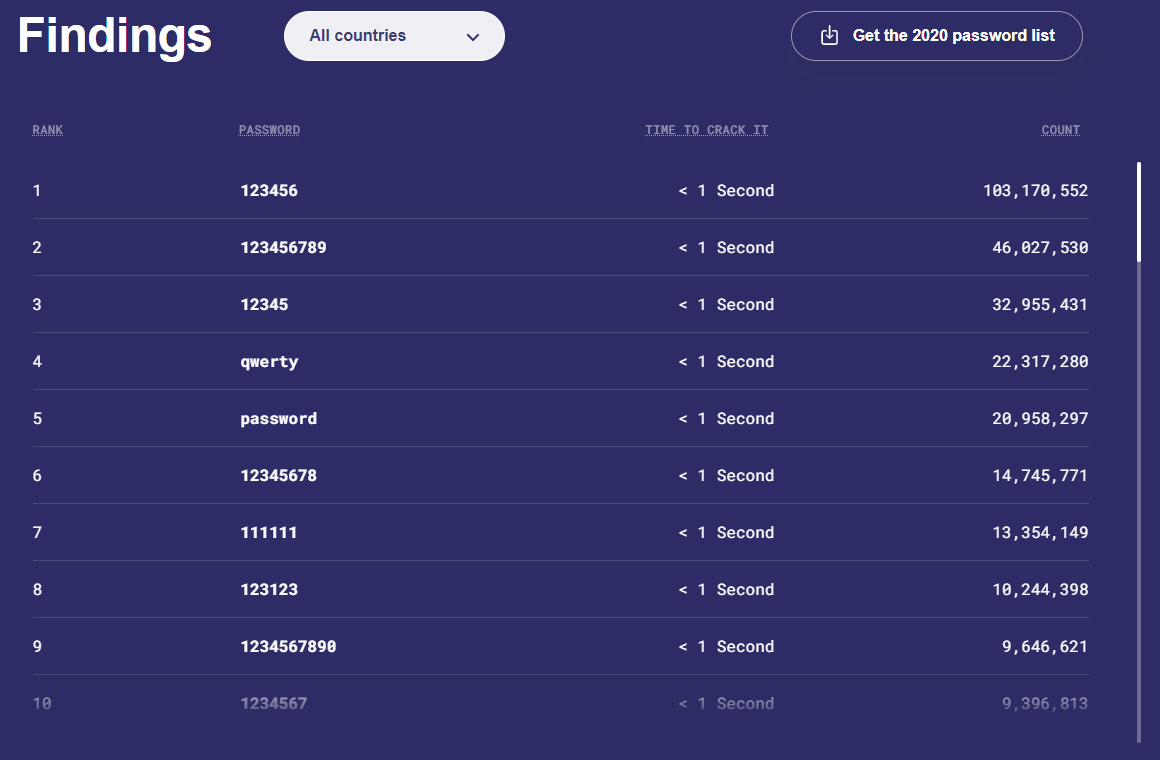
Source: https://nordpass.com/most-common-passwords-list/[3]
Other Password-related Attacks
- Dictionary attack
A dictionary attack is a kind of brute force attack. This method uses many common words and passwords to guess the system password. Hackers try using the most common passwords, popular pet names, fictional characters, or extensive lists of words from a dictionary.
- Information Leakage
In addition, data leakage is also one of the reasons for the leakage of passwords. Hackers use this to obtain system passwords for login. According to information from the Information Security Network, the reasons for data leakage can be attributed to phishing, software or system loopholes, misconfiguration, insider threats and user negligence. [4]
- Credential stuffing
Hackers will use botnets to repeatedly attempt to log in to network services with stolen account passwords in an automated fashion. This method uses many leaked email addresses and passwords, coupled with automated tools, to continuously try to log in to the network service until a match is found.
Since many users re-use the same credential across different web services, therefore, if hacker manages to steal one of these, he could hack into all victim’s accounts easily.
Exploit System Vulnerabilities
Hackers can use vulnerability scanners to scan the target organization's system versions to see if organisation is using a vulnerable version. Hackers will also use Nmap to check whether the target system is online and which the port is opened in order to check the system version information.
Figure 4. Nmap network scanning tool
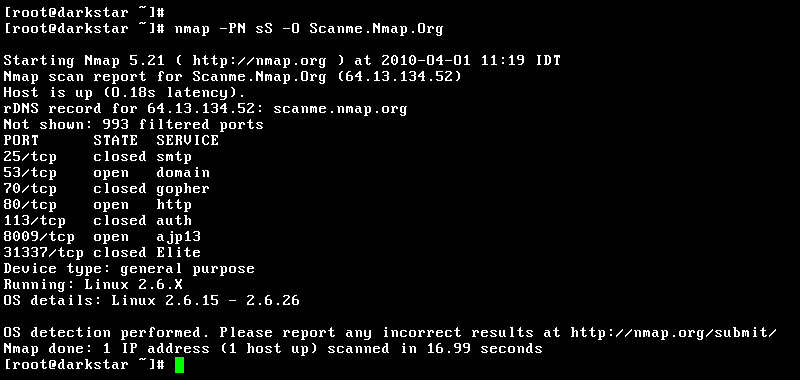
Source: https://zh.wikipedia.org/zh-hk/Nmap#/media/File:Nmap-5.21.png[5]
Here are the results of some other vulnerability scanner tools:
Figure 5. The scanning tool shows the difference between the version used by the target system and the latest official version
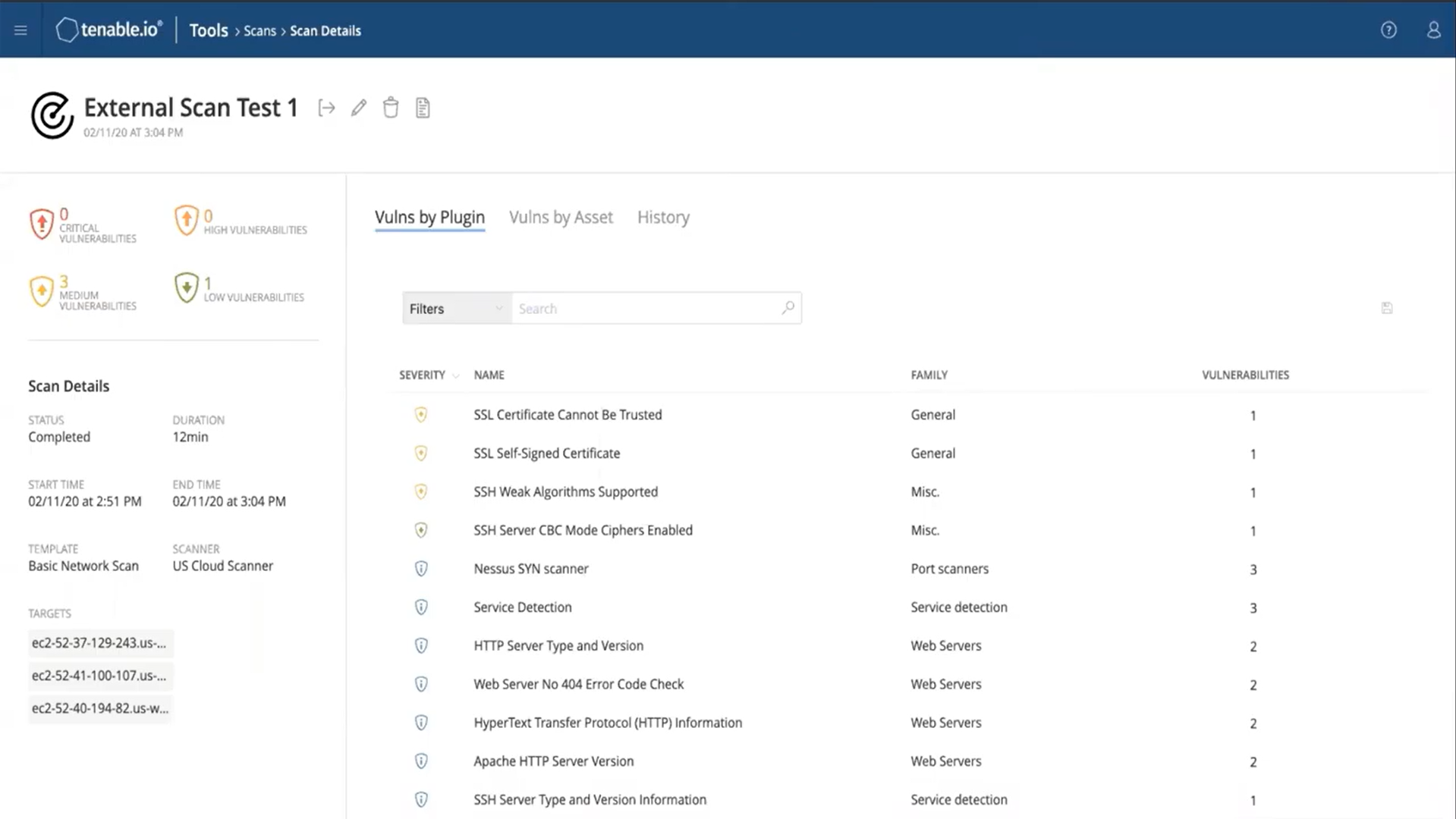
Source: https://www.youtube.com/watch?v=tWF9Fzf0cA4[6]
Social media is also leveraged by hackers as a channel to find out which kind of systems the company is using. For example, on a job search website, it gives hackers the hint of the brand of devices the company is using by looking at the opening job description.
Figure 6. Example of requirement in job search website

From the above example, the hackers could guess that the company may be using Cisco firewalls, Exchange mail server and other software. If the company doesn't have the latest version installed, hackers can conduct cyber attacks on known vulnerabilities, such as modifying system settings and executing malware.
Security Advice
- For all systems and devices, always update the latest security patch
- Replace end-of-support systems or devices
- Disable or block unused ports and IP addresses
- Review business requirements regularly to minimize the number of opened ports
- Avoid disclosing excessive or unnecessary information on the Internet
- Limit the number of failed login attempts to reduce the impact of brute-force attack
- Examine logs for unusual network traffic originating from unknown IP addresses
- Use multi-factor authentication and complex passwords (For example, use a mixture of symbols, numbers, upper and lowercase letters, and the recommended length is at least 8 characters)
- %iW2e!f1@5
- F1o^i78.593!8as*(
- 1!@*CSvw219)#/?
Reference Links:
[1] https://phoenixnap.com/kb/nmap-scan-open-ports
[2] https://www.kali.org/tools/dirbuster/
[3] https://nordpass.com/most-common-passwords-list/
[4] https://www.infosec.gov.hk/tc/knowledge-centre/data-breach
Share with
