How to Mitigate New Cyber Security Risks Arising from the Growing Use of Technology in Industrial Operations
In recent years, more enterprises and public utilities are leveraging 5G and Internet of Things (IoT) technologies to connect their industrial operation technology (OT) systems to the information technology (IT) systems or the Internet. This enables the operation data of factory machines and critical infrastructure equipment to be sent back to the IT systems instantly, making it more convenient to monitor and analyse their operation in real time, and even automatically adjust their operation parameters, so as to improve efficiency and productivity, and enhance management.

Previously, OT systems and IT systems were in two completely separated networks without any interconnection. OT systems have their own communication protocols such as Modbus, which are different from the TCP/IP protocol used in IT systems, making these two systems working independently without interaction. Nowadays, these two systems have gradually adopted the same standardised protocol or used Internet of Things (IoT) devices to connect the two systems and share data. In the future, OT systems and IT systems will be converged to bring automation and intelligence to the industry.
Source: Cigref
The convergence of OT systems and IT systems brings not only opportunities, but also new cyber security risks. One example is that once the two systems are connected, malware risks that only affect IT systems previously will now extend to OT systems.
Indeed, such risks are already materialising. According to an IBM report, manufacturing industry suffered the most cyber attacks in 2021. Ransomware was one of the most common cyber attacks on OT systems. The reason was that OT systems help generate income. Once hackers use ransomwares to paralyse the operations of OT systems, organisations suffer heavy losses directly. The affected organisations are more likely to pay the ransom in order to resume operations. If the affected organisations are critical infrastructures sector, such as electricity, public utilities, transportation, etc., the impact will be extended to the public. Hackers can even coerce the affected organisations to pay a larger amount of ransom.
For example, in March 2021, hackers used the remote software TeamViewer to gain access to the computer system of Oldsmar in Florida, United States and tried to change the concentration of chemicals in the city’s water supply facilities, which was enough to seriously harm the human body.
This blog will discuss the security challenges of IT/OT convergence and the preparations before and after the convergence, and introduce measures to reduce the risks.
Source: IBM Security X-Force Threat Intelligence Index 2022
Challenges arisen from IT/OT convergence
A major challenge for i4.0 is how to connect OT systems and IT systems (IT/OT Convergence) securely. These two systems have different priorities on security considerations: IT system security focuses on protecting user data and usually uses the concept of CIA (confidentiality, integrity, and availability) to formulate security controls, with protecting data against unauthorised access and being tampered as its main goals. On the other hand, OT systems rarely process user data, but emphasises more on system availabilities, physical safety of operations of machines and ensuring configuration data is intact.
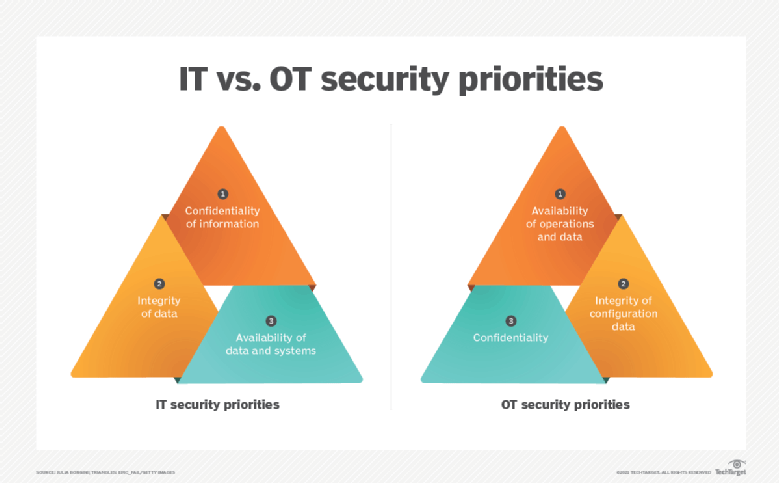
Source:https://www.techtarget.com/searchitoperations/definition/IT-OT-convergence
In addition to the above two major differences, OT systems and IT systems also have the following differences:
- Lifecycle
IT systems generally have a relatively short life cycle of about 3 to 5 years. In contrast, OT systems can have a life cycle of more than 20 years. It is not difficult to see legacy OT systems that are still in operation in factories. The companies and the labour market also lack technical professionals who understand these old systems, and it is easy to cause technical faults when performing convergence of IT and OT systems.
- Cyber Security Standards and Operating Systems
Information technology systems have been connected to the Internet for a long time. Mature security technologies are in place to prevent hackers’ attacks such as data encryption, etc.
However, OT systems are generally located in an isolated network environment. Therefore by design they have no requirement to use strong encryption or even no encryption for data transmission.
In addition, most OT systems run a customised operating system, and any major changes may affect the operation of different machines, so it is difficult to update the system to fix security vulnerabilities.
Furthermore, OT systems have not taken security into consideration during the design phase to prevent cyber attacks, so there are few protective measures and the development of related cyber defence is relatively backward, such as measures to detect intrusions, the ability to recover and respond after security incidents, etc.
- Maintenance Requirements
IT systems are generally designed with a concept of resilience in mind. Even if the primary system needs to be restarted during maintenance, the secondary system can continue to serve.
It is difficult to implement the resilience in OT systems because the increase in costs means the decline in production efficiency. If an OT system needs to be shut down for maintenance, it can take a toll on productivity. Even after maintenance is completed, security testing is required before returning to production.
Compared with IT systems, OT systems need to consider more factors during maintenance, resulting in relatively less frequent maintenance, which is likely to leave security risks.
The difference in system design between two systems will cause different risks.
Preparation before and after IT/OT convergence
Before converging OT systems and IT systems, sufficient preparations are required to reduce the risks. After the convergence, it is necessary to update the company's security, operation and maintenance policies. The Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) has the following suggestions:
- Conducting Network and Security Assessments
Conduct an in-depth assessment of the entire OT systems and IT systems, including network and security assessments. Network assessment is a review of all system assets, network structures and data flows within an organisation. Security assessment is to analyse the login account, remote access method, system loopholes and network services;
- Writing a Risk Assessment Report
From the perspective of operation and information security, identify and classify risks in operations, processes, and systems. Formulate recommendations and solutions for all risks, and write a comprehensive assessment report;
- Formulating an Implementation Plan to Follow Strictly
Before formulating an implementation plan, clarify the roles and responsibilities of stakeholders. Before the convergence of OT and IT systems, the risks mentioned in the assessment report should be promptly addressed. A detailed and clear convergence plan with a realistic timetable must be developed. Operators need to strictly follow the implementation plan and conduct evaluation tests after the operation is completed.
When planning for implementation, one of the common challenges is to design a secure architecture, which involves how different devices should be layered and partitioned. The industry has different standard models for reference, with the Purdue model being one of most frequently referred;
This computer-integrated-manufacturing model was proposed by scholars of Purdue University, Indiana, United States, back in the 1990s. It is divided into seven layers, each of which has its own functions and related systems. Each layer is also a network segmentation with access being controlled by different security measure to prevent attackers from intruding from one network (e.g. IT network) to another (e.g. OT network).
For example, layer level 3.5 is to prevent horizontal lateral threat movement between IT and OT, and security systems such as firewalls and proxies are generally placed. Users can design an appropriate structure architecture according to the actual situation of the organisation.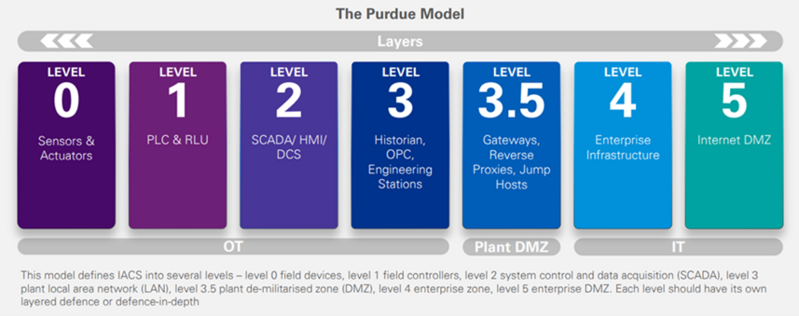
Source: KPMG - Securing Operational Technology (OT) networks
Apart from the Purdue reference model, another security architecture that can be referred to is the "Zero Trust" architecture, which promotes the principle of micro-segmentation, data encryption, and authentication and adoption of least-privileged principle for access to any data and system services. For more information about "Zero Trust" and the implementation of "Zero Trust" architecture in OT, please refer to the "Reference" section. - Updating Operation Policies
After the convergence, the IT and OT teams will interact with each other very often. Organisations can consider reorganising these two teams, or even recruiting experts with both IT and OT skillsets to streamline the operations. In terms of maintenance, since OT systems are connected to IT systems, both teams need to have a common understanding and standardise information security standards. In addition, unmanaged systems in the past must be immediately controlled to identify any suspicious activities which may be an indication of compromise.
Moreover, as convergence of IT/OT systems usually requires IoT networks and uses different IoT devices as sensors or data collection, security measures for IoT devices can also be applied. To this end, HKCERT has released the “IoT Security Best Practice Guidelines” in 2020 to cover network security issues when using IoT devices. You may refer to the Guidelines as a reference.
Reference
- Cigref – IT/OT CONVERGENCE 2019 DECEMBER A FRUITFUL INTEGRATION OF INFORMATION SYSTEMS AND OPERATIONAL SYSTEMS
- IBM – X-Force Threat Intelligence Index 2022 Full Report
- FBI, other agencies issue warnings after Oldsmar water system attack (tampabay.com)
- What is IT/OT Convergence? Everything You Need to Know (techtarget.com)
- A Conceptual Model of an ICS: Safety and Security Goals (Adapted from... | Download Scientific Diagram (researchgate.net)
- Vertech – 2018 BRIDGING THE IT/OT DIVIDE:5 PRACTICAL STEPS FOR MANAGING CRITICAL CONTROL NETWORKS
- KPMG – Securing Operational Technology (OT) networks
- Purdue Model for ICS Security - Check Point Software
- What Is the Purdue Model for ICS Security? - Zscaler
- Cyber Security Operational Technology | eXcelsior Safety
- Implementing IoT Security Best Practice
- Information Security Utopia Starts with Zero Trust Architecture
- IT, OT, and ZT: Implementing Zero Trust in Industrial Control Systems
Related Tags
Share with
