
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the third quarter of 2020.
Nowadays, many networked digital devices, such as computers, smartphones, tablets, are being compromised without the user's knowledge. The data on them may be mined and exposed every day, and even be used for various criminal activities.
The Hong Kong Security Watch Report aims to raise public awareness of the problem of compromised systems in Hong Kong, enabling them to make better decision in information security. The data in this quarterly report focuses on the activities of compromised systems in Hong Kong which suffer from, or have participated in various types of cyber attacks, including web defacement, phishing, malware hosting, botnet command and control centres (C&C) or bots. "Computers in Hong Kong'' refer to those whose network geolocation is Hong Kong, or the top level domain of their host name is ".hk'' or “.香港”.
Highlight of Report
In 2020 Q3, there were 6,753 unique security events related to Hong Kong used for analysis in this report. Data were collected through IFAS1 with 10 sources of information2, and not collected from the incident reports received by HKCERT.
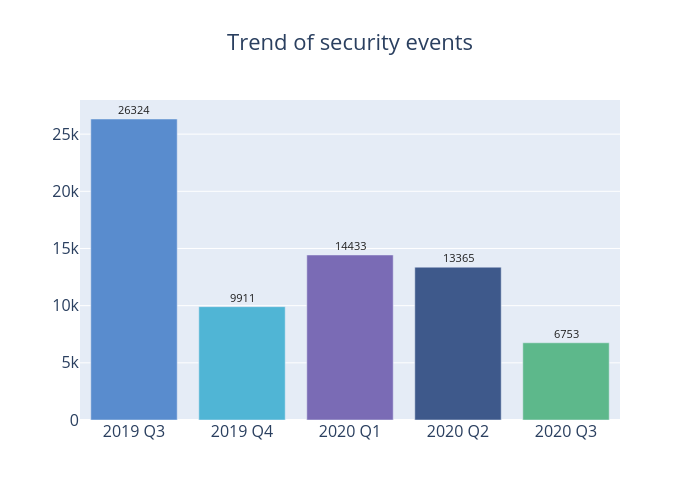
Figure 1 –Trend of security events
The total number of cyber security events in the third quarter of 2020 fell by nearly 50%, from 13,365 in 2020 Q2 to 6,753 in this quarter. There are significant reductions in web defacement, phishing, malware hosting or botnet events.
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trends and distributions are summarised below:
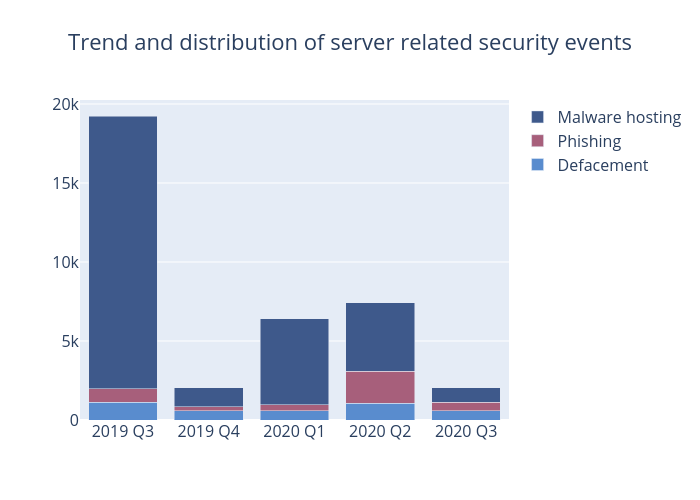 Figure 2 –Trend and distribution of server related security events
Figure 2 –Trend and distribution of server related security events
| Event Type | 2019 Q3 | 2019 Q4 | 2020 Q1 | 2020 Q2 | 2020 Q3 |
|---|
| Defacement | 1,120 | 591 | 572 | 1,062 | 571 |
| Phishing | 849 | 257 | 399 | 2,017 | 552 |
| Malware Hosting | 17,273 | 1,185 | 5,445 | 4,334 | 934 |
Table 1–Trend and distribution of server related security events
As shown in Table 2, the number of phishing attacks has fallen by more than 70%, from 2017 cases in Q2 2020 to 552 cases in this quarter, and the number of unique IP addresses involved has also decreased by 38% to a total of 145 (Figure 7), while the unique URL/IP ratio decreased by 38% to 3.81 (Figure 8).
Compared with last quarter, the number of defacement event decreased by 46% to 571 cases. The number of unique IP addresses involved in defacement events also decreased by 32% to a total of 311 (Figure 5). The unique URL/IP ratio also decreased by 19% to 1.84 (Figure 6).
Although the phishing and defacement events have recorded a decrease, it only returned to the pre-COVID-19 level. Overall, the situation has not improved when compared with the beginning of this year.
In this quarter, the number of malware hosting events dropped by 88%, from last quarter’s 4,334 cases to 934 cases, and the number of related unique IP addresses was also down 68% to 157 (Figure 9). The unique URL/IP ratio has also shortened from 8.81 to 5.95 (Figure 10). The data reveals that, besides targeting computers, a portion of malwares is targeting mobile devices, e.g. mobile phone, tablet, etc. Users are advised to verify the apps before downloading and installing. HKCERT recommends users to always download mobile applications from official apps store.

| HKCERT urges system and application administrators to protect the servers. |
- Patch server up-to-date to avoid the known vulnerabilities being exploited
- Update web application and plugins to the latest version
- Follow best practice on user account and password management
- Implement validation check for user input and system output
- Provide strong authentication e.g. two factor authentication, administrative control interface
- Acquire information security knowledge to prevent social engineering attack
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving a small number of powerful computers, mostly servers, which give commands to bots
- Botnet security events - involving a large number of computers, mostly personal computers which receive commands from C&Cs.
Botnet Command and Control Servers
The trend of Botnet C&C security events is summarised below:
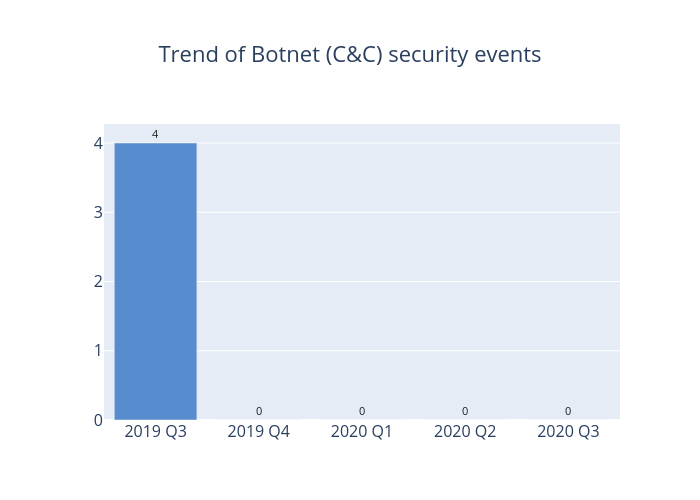 Figure 3 –Trend of Botnet (C&Cs) related security events
Figure 3 –Trend of Botnet (C&Cs) related security events
There was no Botnet Command and Control Centers (C&C) security events in this quarter.
Botnet Bots
The trend of botnet (bots) security events is summarised below:
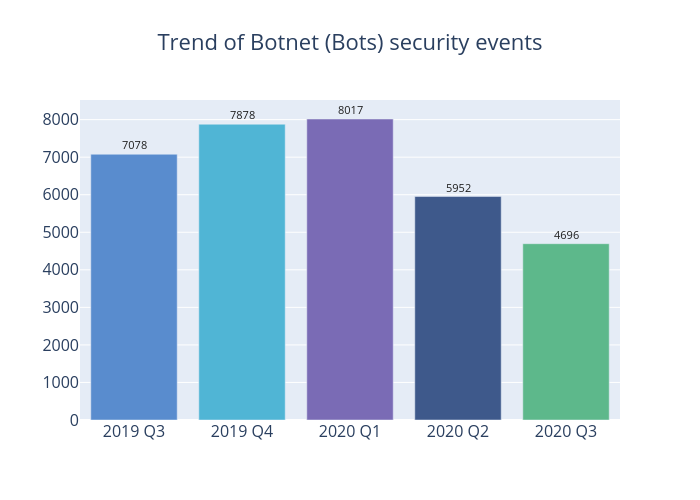 Figure 4 - Trend of Botnet (Bots) security events
Figure 4 - Trend of Botnet (Bots) security events
The number of botnet (bots) event decreased by 21% to 4,696 this quarter. Most botnet families have recorded a decrement. The ranking remains unchanged for most botnet families, while the Nymaim, Virut and Sality have swapped positions.
Although Mirai was the botnet family with the largest decline during the quarter, down 28% to 2,859, it is still the most numerous botnet family. The botnet family with the largest increase or decrease was Nymaim, with the number nearly doubled to 166 cases.
Nymaim is designed to distribute other viruses, such as ransomware, information stealers, and other exploit kits. It mainly spread via phishing email and website. HKCERT reminds users not to open suspicious attachment and file from an unknown sender or on the Internet.

| HKCERT urges users to protect computers so as not to become part of the botnets. |
- Patch their computers
- Install a working copy of the security software and scan for malware on their machines
- Set strong passwords to avoid credential based attack
- Do not use Windows, media files and software that have no proper licenses
- Do not use Windows and software that have no security updates
- Do not open files from unreliable sources
|
HKCERT has been following up the security events received and proactively engaged local ISPs for the botnet cleanup since June 2013. Currently, botnet cleanup operations against major botnet family Avalanche, Pushdo, Citadel, Ramnit, ZeroAccess, GameOver Zeus, VPNFilter and Mirai are still ongoing.
HKCERT urges general users to join the cleanup acts, ensuring their computers are not being infected and controlled by malicious software, and protecting their personal data for a cleaner cyberspace.

| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 Shodan is a search engine for Internet-connected devices: https://www.shodan.io/

 Figure 2 –Trend and distribution of server related security events
Figure 2 –Trend and distribution of server related security events Figure 3 –Trend of Botnet (C&Cs) related security events
Figure 3 –Trend of Botnet (C&Cs) related security events  Figure 4 - Trend of Botnet (Bots) security events
Figure 4 - Trend of Botnet (Bots) security events

