Hong Kong Security Watch Report (Q2 2015)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the second quarter of 2015.
Nowadays, a lot of “invisible” compromised computers are controlled by attackers with the owner being unaware. The data on these computers may be mined and exposed every day and the computers may be utilized in different kinds of abuse and criminal activities.
The Hong Kong Security Watch Report aims to provide the public a better "visibility" of the situation of the compromised computers in Hong Kong so that they can make better decision in protecting their information security.
The report provides data about the activities of compromised computers in Hong Kong which suffer from, or participate in various forms of cyber attacks, including web defacement, phishing, malware hosting, botnet command and control centres (C&C) and bots. Computers in Hong Kong is defined as those whose network geolocation is Hong Kong, or the top level domain of their host name is “.hk” or “.香港”.
Highlight of Report
This report is for Quarter 2 of 2015.
In 2015 Q2, there were 21,787 unique security events related to Hong Kong used for analysis in this report. The information is collected with IFAS1 from 19 sources of information2. They are not from the incident reports received by HKCERT.
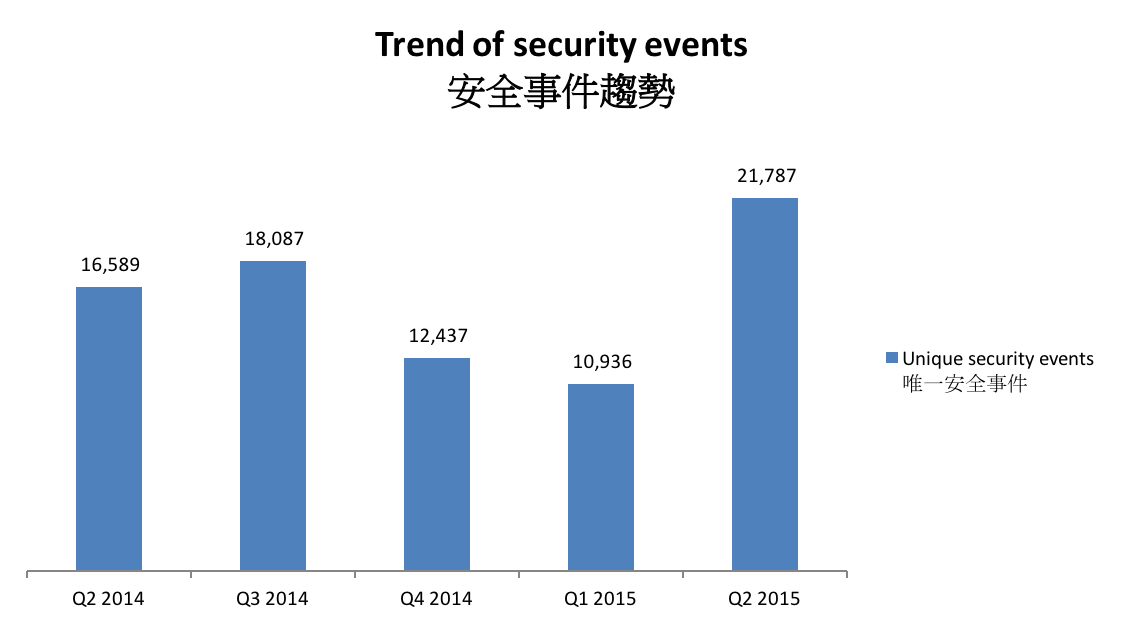
Figure 1 –Trend of security events3
The total number of security events in Q2 2015 increased dramatically by 99% or 10,851 events, reached a record high since Q2 2013. The increase was due to server events.
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trends and distributions are summarized below:
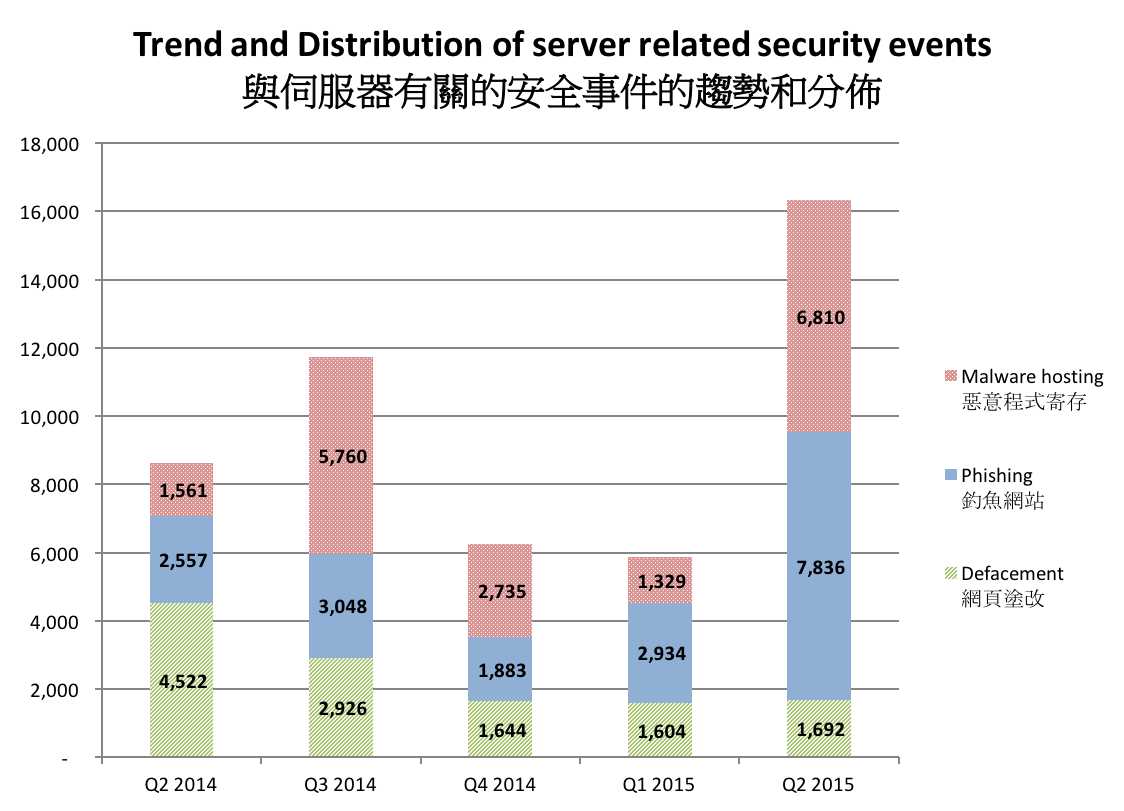
Figure 2 –Trend and distribution of server related security events4
The number of server related security events increased dramatically from 5,867 to 16,338 (increased by 178%) in Q2 2015. The number of server related security events, phishing events and malware hosting events all reached a record high.
In this quarter, the number of defacement events increased slightly by 5% but the number of phishing events and malware hosting events increased dramatically by 168% and 412% respectively.
The increase of phishing events was contributed by a few phishing campaigns. In this quarter, the top phishing target was a Japanese gaming site hiroba.dqx.jp. This campaign utilized more than 10 IP addresses and 3200 URLs, which equals more than 40% of all phishing events. The second and third phishing targets were both Chinese online merchants, namely taobao.com and xzhjia.com, more than 1600 and 1200 URLs were targeting them respectively. As of the time of writing, most of these phishing URLs were no longer accessible.
Among the malware hosting events, about 41% or 2828 events were hosting HTML/Drop.Agent.AB malware. It was found that this malware was related to the Ramnit botnet.
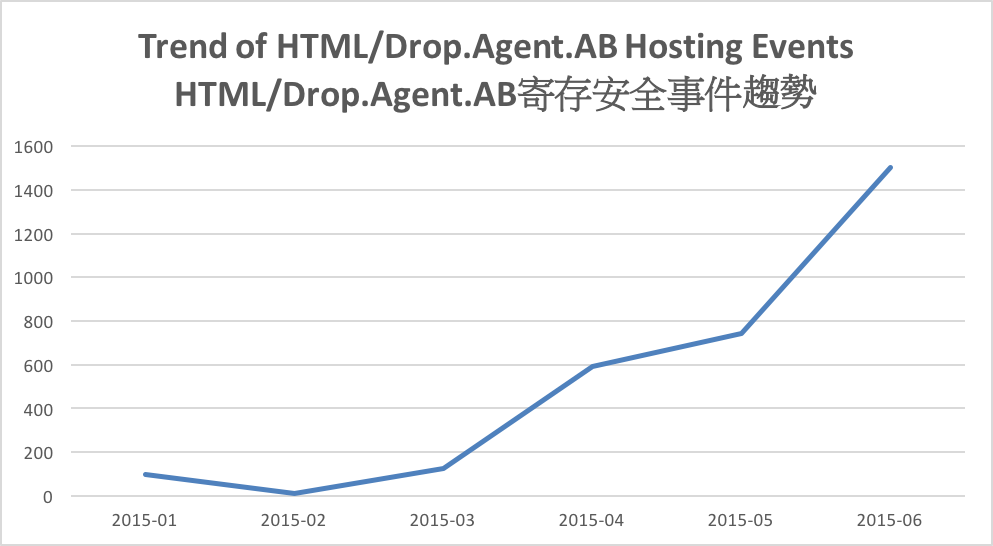
Figure 3 –Trend of HTML/Drop.Agent.AB Hosting Events
As shown in Figure 3, the HTML/Drop.Agent.AB events started rising in March. In February, a takedown operation was carried out against the Ramnit botnet, a lot of bots were identified and cleared. The sudden increase of Ramnit related malware hosting events may reflect that the cybercriminals behind were working hard to recover the botnet. More about the Ramnit botnet will be described in the botnet section.
| HKCERT urges system and application administrators to protect the servers. |
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving small number of powerful computers, mostly servers, which give commands to bots
- Bots security events – involving large number of computers, mostly home computers, which receive commands from C&C.
Botnet Command and Control Servers
The trend of botnet C&C security events is summarized below:
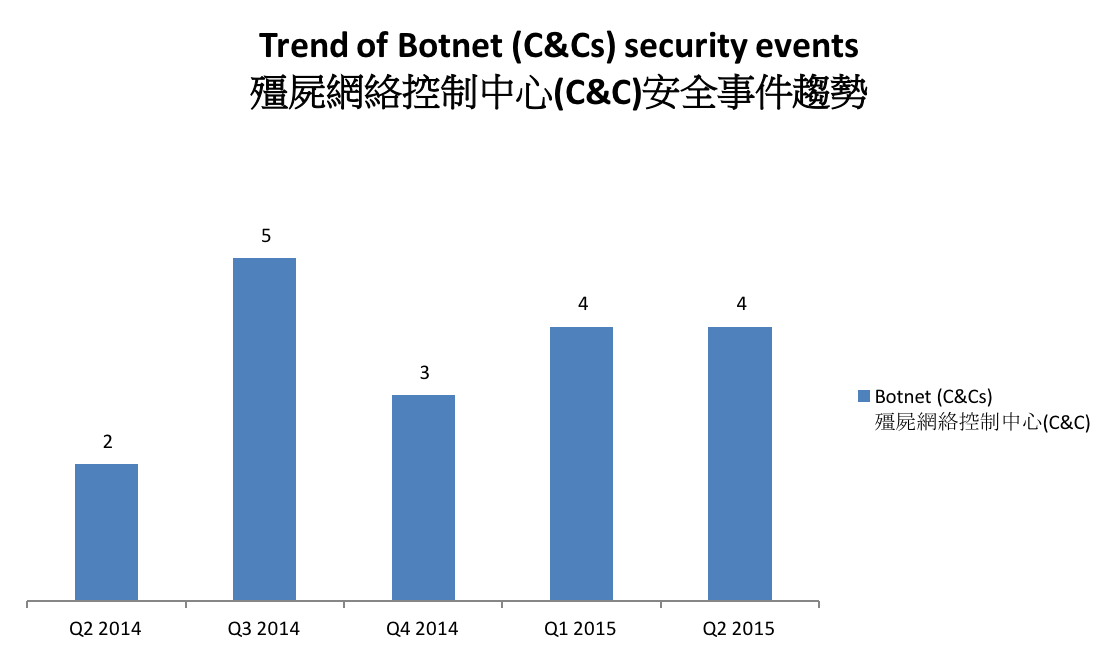
Figure 4 –Trend of Botnet (C&Cs) related security events
The number of botnet Command and Control Servers remains unchanged this quarter.
There were 4 C&C servers reported in this quarter. One of the reported servers was identified as Zeus C&C server, while the other three were identified as IRC bot C&C servers.
The trend of botnet (bots) security events is summarized below:
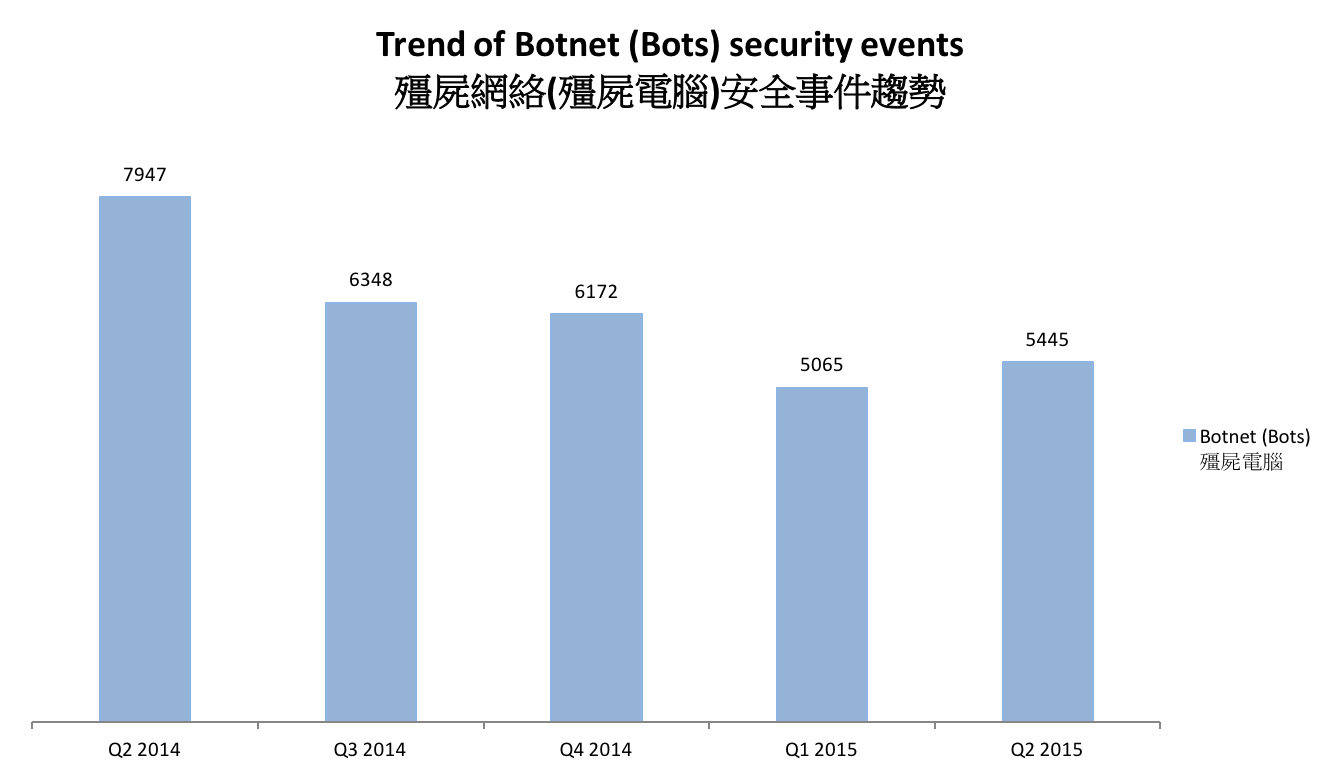
Figure 5 - Trend of Botnet (Bots) security events
Number of Botnet (bots) on Hong Kong network slightly increased in this quarter, stopping the dropping trend since Q3 2014.
In Q2 2015, the number of botnet infections in Hong Kong increased by 8%. The Virut botnet increased significantly by 87%. It took over Zeus to become the second largest botnet in Hong Kong.
Other than Virut, three botnets, namely Ramnit, Tinba and Dyre, entered the top 10 the first time.
Ramnit
Ramnit is a fully-featured worm. It can steal various types of sensitive information including web credentials, FTP credentials, browser cookies and files, etc. It can allow the attackers to access the victim’s file system and take control of the computer. It can also download additional malwares.
Ramnit first appeared in 2010 and spreaded quickly. Now it has infected more than 3.2 million computers worldwide. On 25 Feb, an operation driven by law enforcement, led by the Europol and assisted by industry partners Symantec, Microsoft, and others, seized the servers and other infrastructure owned by the cybercrime group behind the Ramnit botnet. A large amount of victims were identified that it became the 6th botnet this quarter.
Ramnit spreads through file infection, exploit kits hosted on websites and social media, public FTP servers and bundle with other software.
Tinba
Tinba is a banking Trojan that can perform Man in the Browser (MiTB) attack to steal banking credentials. Tinba was first identified in 2012. It first targeted the users in Turkey and then users in Czech. But now it targets a large scope of banks worldwide.
Tinba employed some interesting anti-sandboxing tricks to evade analysis. First it detects user interactions by checking the mouse movement and the active window. If Tinba is running inside a sandbox, the mouse location and the active window will always be the same, it will not execute the main routine until some user interaction is detected. Moreover, it will detect the disk capacity. If the disk is too small, it is likely to be a sandbox environment. Tinba will just quit in this case.
Tinba spreads through exploit kits and spam emails.
Dyre
Dyre is a banking Trojan that successfully stole millions in 2015. It monitors the website visited by the victims. Once a victim logins to one of the targeted banks websites, Dyre will display a fake screen claiming the site is experiencing issues and asks the victim to call a number. In the phone call, the criminals would try to social engineer critical information from the victim. With this information, the criminal will transfer money from the victim’s account to offshore accounts. To make things worse, the criminals will immediately launch a DDoS against the victim for distraction.
Like Tinba, Dyre also employed anti-sandboxing trick. But instead of using a few tricks, Dyre use only one – by checking how many processor cores the system has. If the machine has only one core, it will terminate. As most sandboxes were configured with only one core and most modern computers have multicores, this simple trick was proven to be highly effective. Researchers tested a Dyre sample with eight sandboxes, all of them failed to analyze the malware.
Dyre spreads through spam emails.
| HKCERT urges users to protect computers so as not to become part of the botnets. |
|
HKCERT has been following up the security events received and proactively engaged local ISPs for the botnet clean up since June 2013. Currently, botnet cleanup operations against major botnet family - Pushdo, Citadel, ZeroAccess and GameOver Zeus are still in action.
HKCERT urges general users to join the cleanup acts. Ensure your computers are not being infected and controlled by malicious software.
Protect yourself and keep the cyberspace clean.
| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Watch Report >
1 IFAS Information Feed Analysis System is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 The numbers were adjusted to exclude the unconfirmed defacement events
4 The numbers were adjusted to exclude the unconfirmed defacement events
Share with


