Microsoft Monthly Security Update (February 2024)
RISK: High Risk
TYPE: Operating Systems - Windows OS

[Updated on 2024-02-16]
Exploit in the wild has been detected for CVE-2024-21410, affecting Microsoft Exchange Server. The vulnerability could be exploited by sending a crafted request to steal user's NTLM hash.
Proof of Concept exploit code is publicly available for CVE-2024-21413, affecting Microsoft Outlook. The vulnerability could be exploited by clicking on a malicious URL and execute arbitrary code.
[Updated on 2024-02-29]
Exploit in the wild has been detected for CVE-2024-21338, affecting Microsoft Windows. To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system.
Microsoft has released monthly security update for their products:
| Vulnerable Product | Risk Level | Impacts | Notes |
| Browser |  Medium Risk Medium Risk | Remote Code Execution | |
| Azure |  Medium Risk Medium Risk | Remote Code Execution Elevation of Privilege Spoofing | |
| Developer Tools |  Medium Risk Medium Risk | Remote Code Execution Denial of Service | |
| Windows | 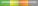 High Risk High Risk | Denial of Service Elevation of Privilege Information Disclosure Remote Code Execution Security Restriction Bypass Spoofing | CVE-2024-21351 is being exploited in the wild. The vulnerability allows a malicious actor to inject code into SmartScreen and potentially gain code execution, which could potentially lead to some data exposure, lack of system availability, or both.
CVE-2024-21412 is being exploited in the wild. The vulnerability could bypass Mark of the Web (MoTW) warnings in Windows.
[Updated on 2024-02-29] CVE-2024-21338 is being exploited in the wild. To exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application that could exploit the vulnerability and take control of an affected system. |
| Extended Security Updates (ESU) |  Medium Risk Medium Risk | Denial of Service Information Disclosure Remote Code Execution Elevation of Privilege Spoofing | |
| Microsoft Dynamics |  Medium Risk Medium Risk | Spoofing Information Disclosure | |
| Microsoft Office | 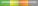 High Risk High Risk | Remote Code Execution Elevation of Privilege Information Disclosure | [Updated on 2024-02-16] CVE-2024-21413 Proof-Of-Concept is available in public. The vulnerability could be exploited by clicking a malicious URL and execute arbitrary code. |
| System Center |  Medium Risk Medium Risk | Elevation of Privilege | |
| Exchange Server | 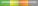 High Risk High Risk | Elevation of Privilege | [Updated on 2024-02-16] CVE-2024-21410 is being exploited in the wild. The vulnerability could be exploited by sending a crafted request to steal user's NTLM hash. |
| Mariner | 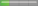 Low Risk Low Risk |
Number of 'Extremely High Risk' product(s): 0
Number of 'High Risk' product(s): 3
Number of 'Medium Risk' product(s): 6
Number of 'Low Risk' product(s): 1
Evaluation of overall 'Risk Level': High Risk
Impact
- Remote Code Execution
- Security Restriction Bypass
- Elevation of Privilege
- Denial of Service
- Information Disclosure
- Spoofing
System / Technologies affected
- Browser
- Azure
- Developer Tools
- Windows
- Extended Security Updates (ESU)
- Microsoft Dynamics
- Microsoft Office
- System Center
- Exchange Server
- Mariner
Solutions
Before installation of the software, please visit the vendor web-site for more details.
- Apply fixes issued by the vendor.
Vulnerability Identifier
Source
Related Link
Related Tags
Share with
