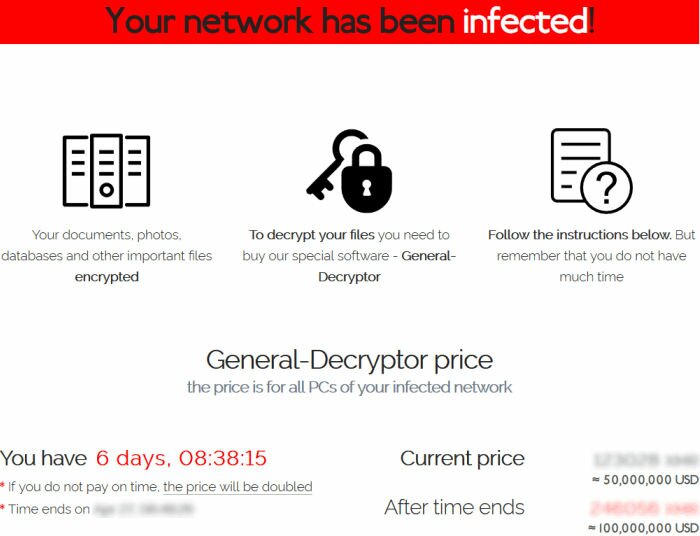
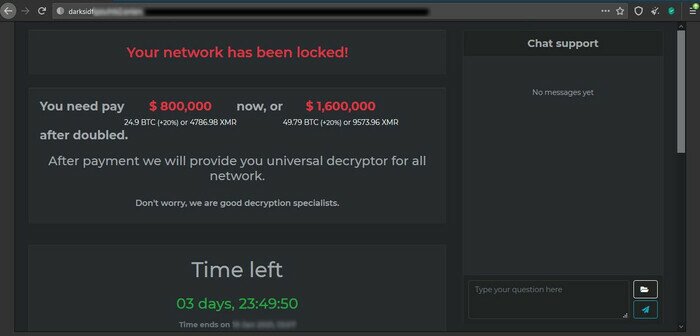
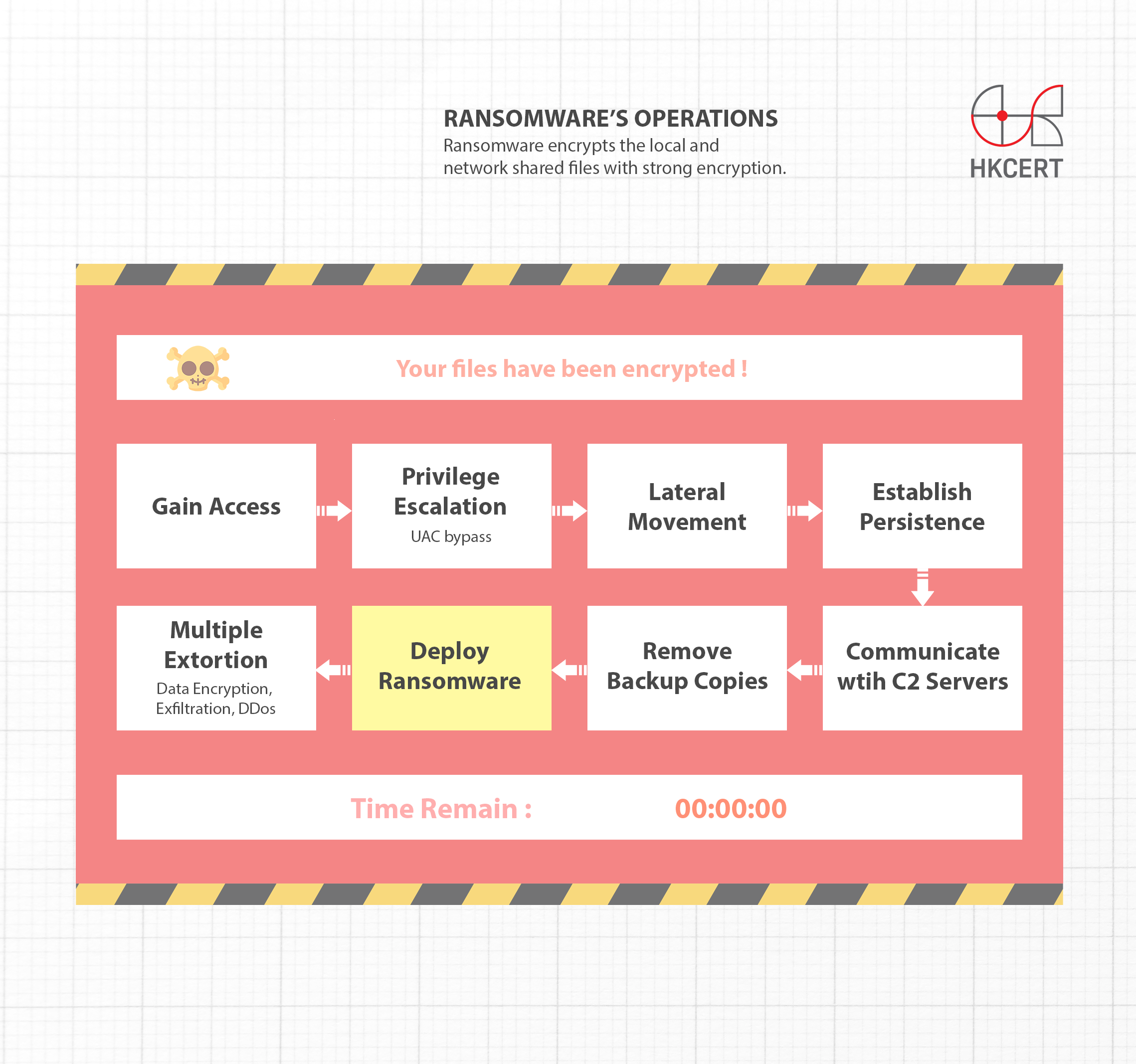
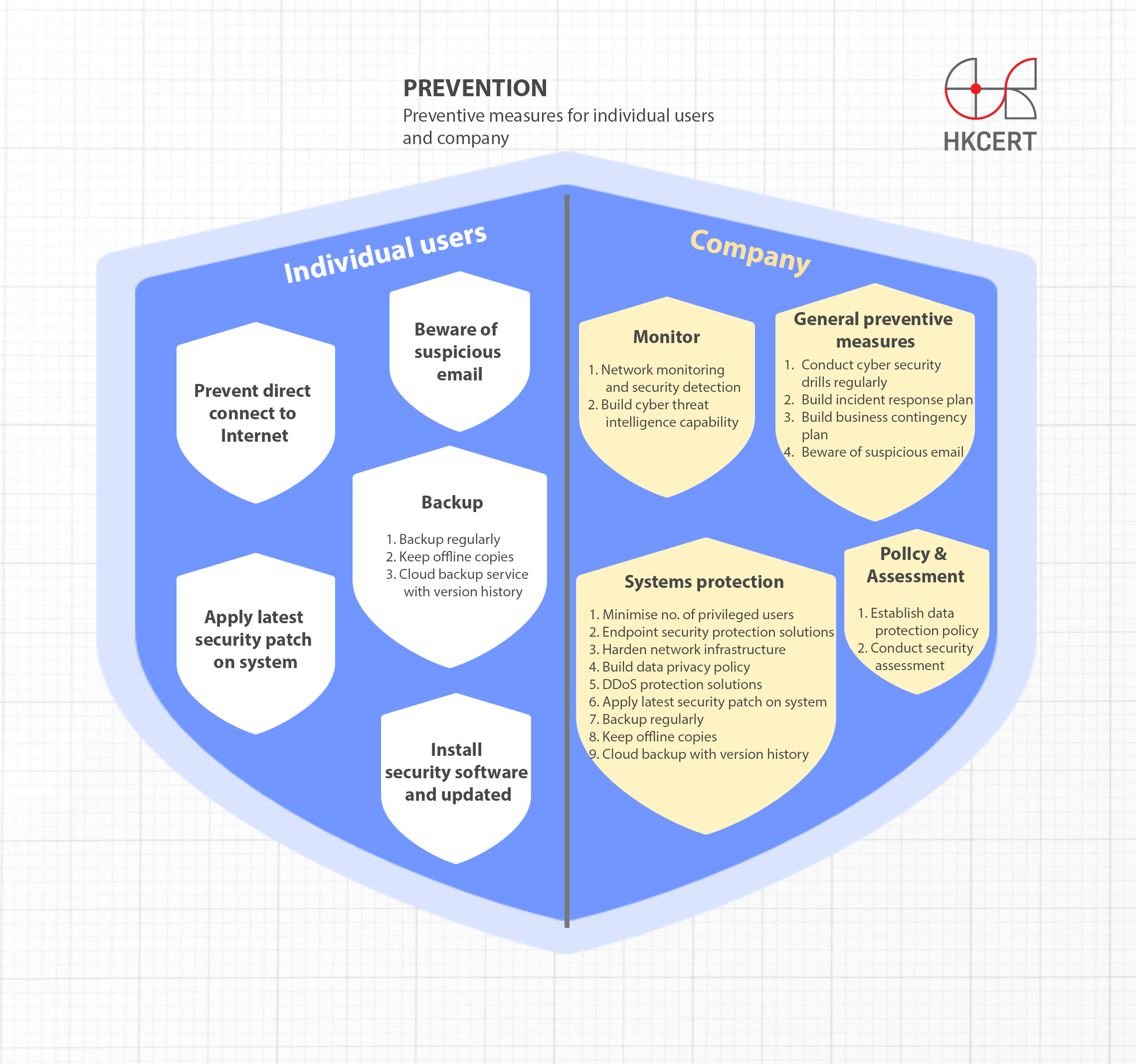
Fight Ransomware
Different Types of Ransomware
| Ransomware | Ransom Message | File Extensions | Primary Infection Vector | Decryptable Versions* |
| Akira | A file named "akira_readme.txt" asking victims to contact the hacker to pay ransom. | The extension is ".akira". |
| Akira |
| AstraLocker | A file named "How To Restore Your Files.txt" asking victims to contact the hacker to pay ransom. | The extension is ".Astra " and ".babyk". |
| AstraLocker |
| BianLian | A file named "Look at this instruction.txt" asking victims to contact the hacker to pay ransom. | The extension is ".bianlian". |
| BianLian |
| BlackByte | A file named "BlackByte_restoremyfiles.hta" asking victims to contact the hacker to pay ransom. | The extension is ".blackbyte". |
| BlackByte |
| Cactus | A file named "cAcTuS.readme.txt" asking victims to contact the hacker to pay ransom. | The extension is ".cts" followed by a digit. For example ".cts1". | exploited vulnerabilities of Fortinet VPN devices,
exploited vulnerabilities of Qlik Sense. | No descryption tool for Cactus |
| Cerber/Magniber | A message asks victims to buy 'Cerber/My Decryptor' for decryption via Tor browser. | V1-V3 is “.cerber”.
In Magniber, the common extentions are ".ypkwwmd", ".ndpyhss", ".wmfxdqz", ".axlgsbrms", ".nhsajfee", ".mqpdbn", ".damdzv", ".qmdjtc", ".mftzmxqo", ".demffue", ".dxjay", ".fbuvkngy", ".xhspythxn", ".dlenggrl", ".skvtb", “.vbdrj”, “.fprgbk”, ".ihsdj", ".mlwzuufcg" or ".kgpvwnr" |
| Cerber V1
Magniber: Some extensions are supported by the decryption tool.
|
| CrySIS/Dharma/Phobos | A file named "FILES ENCRYPTED.txt" or ransom notes with .HTA and .TXT extension in encrypted folder shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | The common extensions are ".java", ".arena", ".bip" and ".phobos". |
| Some extensions are supported by the decryption tool. |
| DarkSide/BlackMatter | In DarkSide, ransom notes named "README.[victim's_ID].TXT", asking victims to pay ransom for decryption on a designated webpage via Tor browser.
In BlackMatter, ransom message is posted on a black screen wallpaper. Ransom notes named "[random_string].README.txt" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | In DarkSide, the extension is victim's ID.
In BlackMatter, the extension is random. |
| DarkSide
No descryption tool for BlackMatter |
| Djvu | Files named "_openme.txt", " _open_.txt" or "_readme.txt" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | The common extensions are ".djvu", "djvu*", ".djvuu", ".udjvu", ".djvuq", ".uudjvu", ".djvus", ".djuvt", ".djvur" and ".DJVUT". |
| Some extensions are supported by the decryption tool. |
| eCh0raix | Ransom notes named "README_FOR_DECRYPT.txtt" or "README_FOR_DECRYPT.txt", asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The commaon extension are ".encrypt" and ".encrypted". |
| No descryption tool for eCh0raix |
| ESXiArgs | Ransom notes named "ransom.html" or "How to Restore Your Files.html", asking victims to contact the hacker to pay ransom. | The commaon extension is ".args". |
| ESXiArgs-Recover |
| GandCrab | A message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | In V1, the extension is ".GDCB". In V2 and V3, the extension is ".GRAB". In V4, the extension is ".KRAB". In V5, the extension is random |
| GandCrab V1, V4 and V5 up to V5.2 |
| GlobeImposter | A file named "HOW_TO_BACK_FILES.txt" or "how_to_back_files.html" in encrypted folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | In 1.0 version, the common extension is ".CHAK". In 5.1 version, the common extension is ".IQ0005". |
| GlobeImposter 1.0 |
| Hades | A file named “README_RECOVER_FILES_[victim_id].html”, "README_RECOVER_FILES_[victim_id].png" or "README_RECOVER_FILES_[victim_id].txt" in each folder containing encrypted files, which shows victim’s personal identification ID, the link for purchasing the decryption password and hacker's email address. The message asks victims to hacker's provided link, then pay ransom according to hacker's instruction. | The common extension is ".MafiaWare666", ".jcrypt", ".brutusptCrypt", ".bmcrypt", ".cyberone", ".l33ch". |
| Hades |
| HermeticRansom | A file named “read_me.html” on the victim’s Desktop folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | The common extension is ".[[email protected]] .encryptedJB". |
| HermeticRansom |
| Hive | A file named "HOW_TO_DECRYPT.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The version 1 extension is ".hive" The version 2 extensions are ".w2tnk" and ".uj1ps" All random string extension of version 3 and 4 |
| Hive |
| LockBit | A file named "Restore-My-Files.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".abcd". |
| LockBit |
| LockerGoga | A file named "README-NOW.txt" or "README_LOCKED.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".locked". |
| LockerGoga |
| Maze | Ransom message is posted on a screen wallpape. A file named "DECRYPT-FILES.html", asking victims to contact the hacker and follow the hacker's intrution to pay ransom. | The extension is random. |
| No descryption tool for Maze |
| MegaCortex | Victims with data encrypted by versions 2 through 4 need the ransom note (e.g. “!!READ_ME!!!.TXT”, “!-!README!-!.RTF”, etc) present. | The extension is “.aes128ctr”. |
| MegaCortex |
| MortalKombat | It changes the desktop wallpaper to give it a Mortal Kombat theme and generates a ransom note called | The extension is “..Remember_you_got_only_24_hours_to_make_the_payment_if_you_dont_pay_prize_will_triple_Mortal_Kombat_Ransomware” | spreads through phishing emails and targets exposed RDP instances. | MortalKombat |
| Muhstik | A message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is ".muhstik". |
| The device whose ID includes in below keys list can be decrypted. |
| Nemty | Nemty’s ransom message is [extension]-DECRYPT.txt. The message asks victims to pay ransom for decryption on a designated webpage via Tor browser. | In Nemty, the extension is ".nemty". |
| Some file types encrypted by specific versions of Nemty can be decrypted. |
| Netwalker | A file named "{ID} – Readme.txt" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is random. |
| No descryption tool for Netwalker |
| Rhysida | A file named "CriticalBreachDetected.pdf" asking victims to pay ransom for decryption on a designated webpage via Tor browser. | In Rhysida, the extension is ".rhysida". |
| Rhysida |
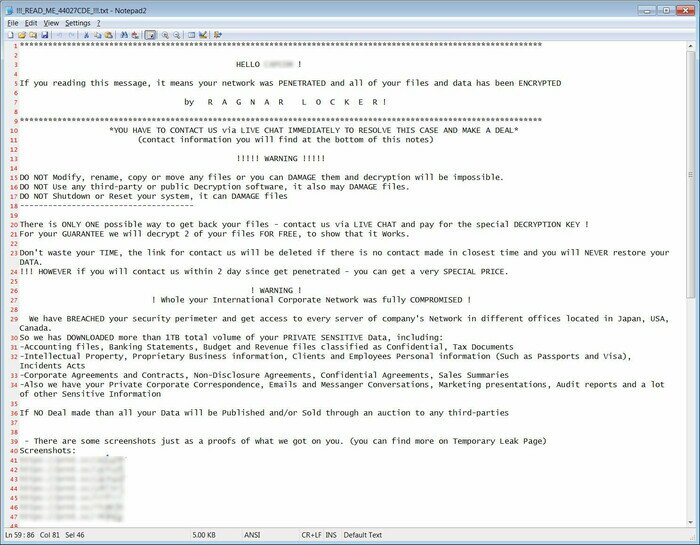
| Ryuk/Conti | In Ryuk, files named "RyukReadMe.txt" or "RyukReadMe.html" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom.
In Conti, a file named "CONTI_README.txt" shows contact information of the hacker. The message asks victims to contact the hacker to pay ransom. | In Ryuk, the extension is ".RYK".
In Conti, the extension is ".CONTI", ".KREMLIN", ".RUSSIA", ".PUTIN". |
| No descryption tool for Ryuk and Conti
Some of the versions of Conti with extention ".KREMLIN", ".RUSSIA", ".PUTIN" can be decrypted. |
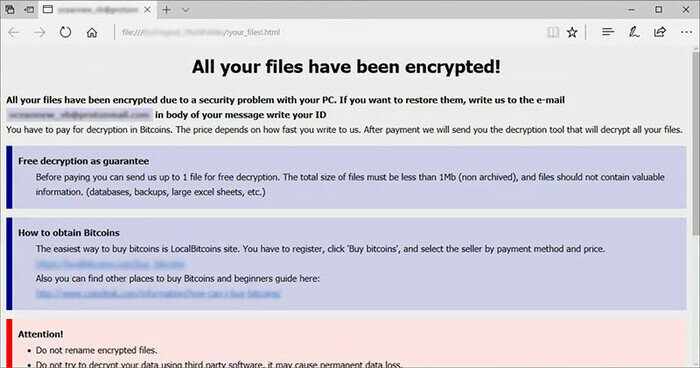
| Sodinokibi/REvil | Ransom message is posted on a blue screen wallpaper. Ransom notes are placed in each folder with the message asking victims to pay ransom for decryption on a designated webpage via Tor browser. | The extension is random. |
| Sodinokibi/REvil decryption tool |
| STOP | A file named "_openme.txt" or "_readme.txt" in encrypted folder shows victim’s personal ID serial number and contact information of hacker. The message asks victims to send ID serial number to hacker's email address, then pay ransom according to hacker's instruction. | The common extensions are ".puma", ".pumas", ".coharos" and ". STOP". |
| Some extensions are supported by the decryption tool. |
| Trigona | Trigona’s ransom note is dropped to the system with the name how_to_decrypt.hta. The HTML code in this file contains embedded JavaScript functionality. | The extension is "._locked". | exploited software vulnerabilities | No descryption tool for Trigona |
| WannaCry | A file named "info.hta" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".WannaCry". |
| WannaCry |
| Yanluowang | A file named "README.txt" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".yanluowang". |
| Yanluowang |
| Yashma | A file named "Restore_Files.html" shows contact information of the hacker, asking victims to contact the hacker to pay ransom. | The extension is ".AstraLocker" or 4 random alphanumeric-characters. |
| Yashma |
*You can identify ransomware and download decryption tools from the website below. HKCERT makes no guarantee of the tools for successful recovery of the files. *
https://www.nomoreransom.org/en/index.html