Handling Email Storm generated from Worms with Spoofed Sender
Description
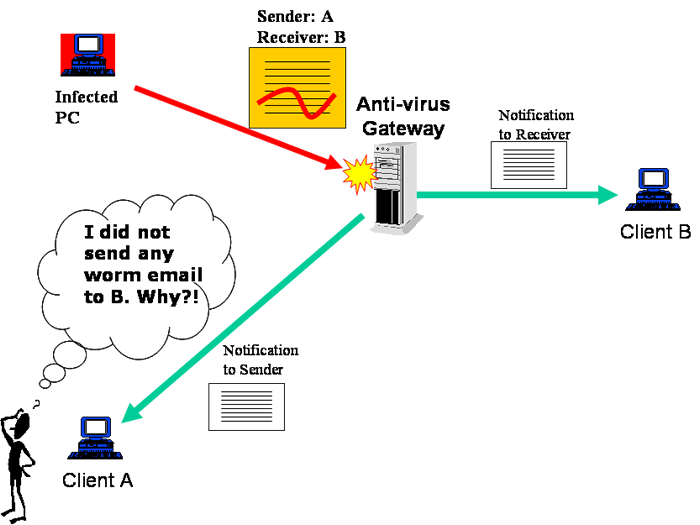
- Latest computer viruses employed email harvesting techniques to get email addresses from the victim's hard disk, and insert these email addresses in both the sender and recipient fields of the infected email and it is therefore difficult to trace the origin of the sender. The name of the sender appeared on the infected email is also a victim.
- For companies that installed an anti-virus gateway, the gateway may intercept the infected email and send a warning message to both the sender and recipient. As both email addresses are spoofed, the warning messages are of little help to rectifying the situation but create a spamming effect to both parties.
The attacks could potentially impose a huge burden on the network infrastructure and the email servers. They also caused the mailboxes of users overloaded and lowered user productivity.
The spoofed sender email address confuses the receiver the source of worm email. It also caused nuisance to the email address owner of the spoofed address who did not send out any worm mail.
Recommendations
- Installing anti-virus software and to keep its virus definition file up-to-date is still the most effective means to detect and clean the latest virus. At the initial stage of outbreak of the virus, a lot of users did not update the virus definition file in time and caused a high rate of infection. Scan the computer after installing the latest virus definition file.
- System Administrators can configure their anti-virus gateway configuration temporarily not to send notification messages to sender email address. It will minimize the spamming caused by spoofed worm email being sent out.
- System Administrators can also configure their anti-virus gateway configuration temporarily not to send notification messages to receiver email address if the users received so many notifications that impact their productivity.
- For companies have installed anti-spamming software on the email server, if the pattern of the spamming notification messages can be easily identified, system administrators can configure the anti-spamming software to filter these messages. This helps reducing spamming to the end-users of the email system.
Note: Since the notification messages to sender and receiver are useful in other cases, system administrators are reminded to remove settings in recommendations 2, 3 and 4 once the peak of the worm attack is past, so that they can receive their messages again.
For 24-hour enquiries and incident reporting, please contact:
Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT)
Tel : 8105 6060
Fax : 8105 9760
Email : [email protected]
Web Page : http://www.hkcert.org/
Share with