ZeroAccess Botnet Detection and Cleanup in Hong Kong

HKCERT estimated that about 2,500 computers in Hong Kong are infected by ZeroAccess botnet. To avoid your computers become the hacker tools, you can detect if you are infected and clean up your computer with the steps below.
1. HKCERT operation on ZeroAccess botnet infection
In Nov 2013, HKCERT received report from Symantec Security Response and Shadowserver about computers in Hong Kong infected with the ZeroAccess botnet. About 2,500 HK IP addresses were reported to have connected to the sinkhole detection system set up by security researcher. These computers may have been infected by the ZeroAccess malware to become part of ZeroAccess botnet and made those call home connections. Upon receiving the reports, HKCERT had notified the related ISP who administrated those IP addresses to alert their customers about the infection.
2. Impact of ZeroAccess botnet
ZeroAccess, also known as Sirefef, max ++, is currently one of the largest Peer-to-Peer (P2P) botnet with about 2 million infected computers worldwide. The United States is the country most affected, accounting for 28.76% [1].
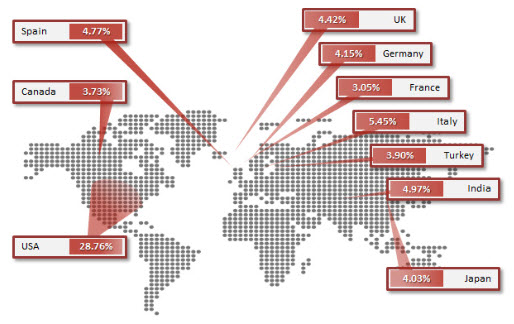
Fig 1: Top 10 infected countries (Image source: Symantec)
ZeroAccess is a malware targeting Windows operating system which was first discovered in 2011. It mainly spreads through the channels below [2]:
- Open malicious email attachments/links
- Install software license cracking programs
- Open fake media files
- Visit website embedded with Exploit kits
It will create a malware delivery platform in infected computers, download and install other malicious plug-ins via P2P network to perform different tasks. A difference with general malware, it does not steal credentials in the computers directly to gain profit but use the infected computers to perform the following tasks for financial gain, including:
- Pay-per-install, i.e. Selling to other hackers to install software on the infected computer
- Click Fraud
- Bitcoin mining
According to the estimation of security researchers, ZeroAccess botnet using the above method, a bot master can earn tens of millions US dollars per year. In addition, the researchers found it perform tasks on infected computers will consume additional power, the estimated daily electricity consumption throughout the ZeroAccess botnet is 3,458 MWh which is enough to supply the power for 111,000 households [3].
3. How to detect and remove ZeroAccess malware
If you suspect that your computer was infected by ZeroAccess malware, please follow the steps below to perform a full system scan with Microsoft Safety Scanner:
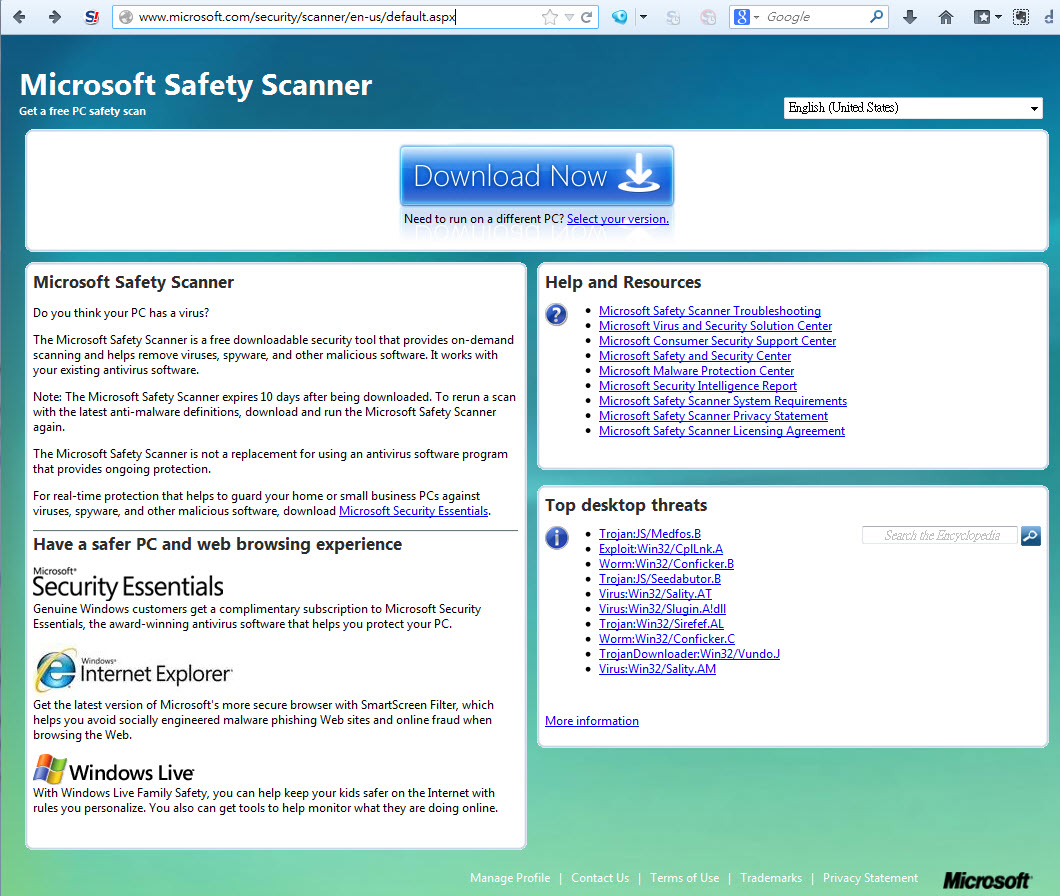
- Visit http://www.microsoft.com/security/scanner/en-us/, and click "Download Now" to download Microsoft Safety Scanner.
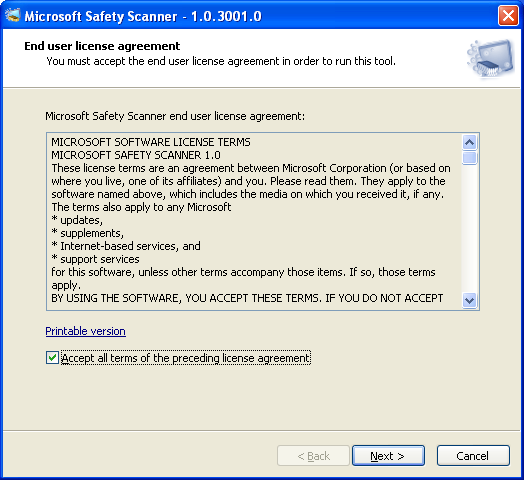
- Double click and run msert.exe. You need to accept the license agreement by checking the "Accept all terms of the preceding license agreement" check box before installation process. If you have accepted the agreement, click “Next” to proceed.
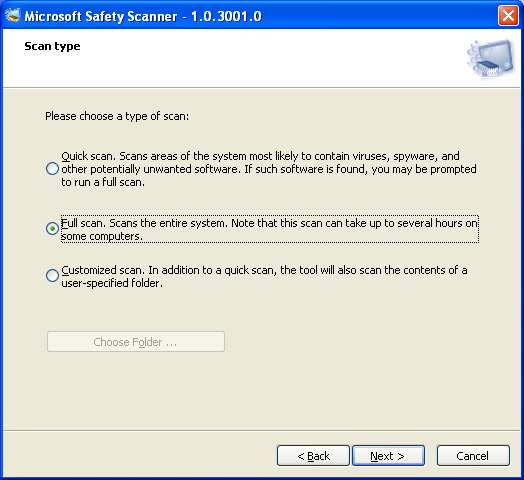
- Select “Full scan” and click “Next” to start scanning.
- Scanning is in progress. It can last for several hours depending on how many files you have in your computer.
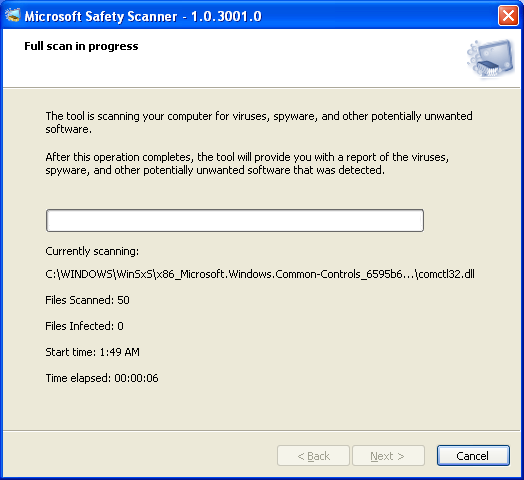
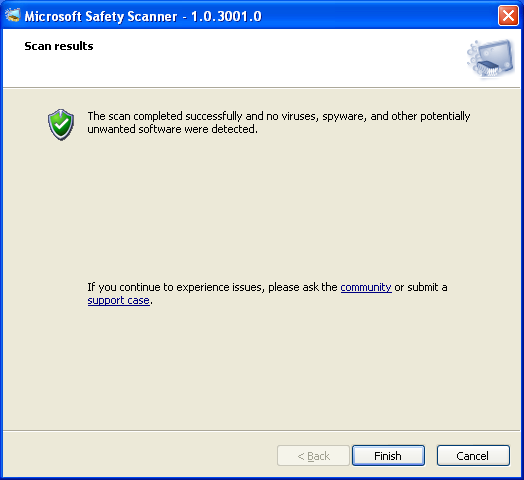
- If your computer is not infected with any malware, the result will show that no viruses, spyware, and other potentially unwanted software were detected.
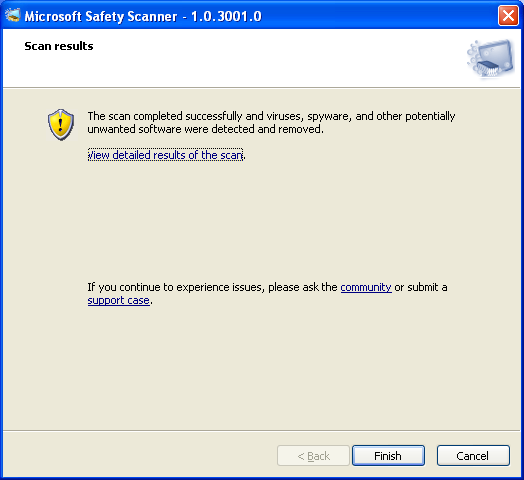
- If your computer is infected with ZeroAccess malware, it will be detected and removed by the scanner.
Other removal tools:
 |
| https://security.symantec.com/nbrt/npe.aspx |
|
| https://download.sp.f-secure.com/tools/F-SecureOnlineScanner.exe |
|
4. Reference
You can find the reference noted above and other technical details about ZeroAccess botnet below.
- Microsoft, Europol, FBI and industry partners disrupt notorious ZeroAccess botnet that hijacks search results
- [PDF] ZeroAccess Indepth, Symantec
- [PDF] The ZeroAccess Botnet – Mining and Fraud for Massive, Sophos
- [PDF] ZeroAccesss, F-Secure
Share with
