Protecting Critical Infrastructures: IT/OT Convergence vs MITM Attacks
As more industrial systems connect to the Internet, there is an increasing prevalence of the convergence of information technology (IT) and operational technology (OT). While the benefits of this convergence are numerous and include increased productivity and efficiency, it also brings new cyber security risks.

Recent developments in cyber security indicate that malware, which previously mostly targeted IT systems, has expanded to target OT systems [1]. This new risk to OT systems has drawn the world’s attention to the involvement of modern cyber attacks – Man-in-the-Middle (MITM) attacks. This blog has elaborated on the risks of the convergence of IT and OT systems, how Man-in-the-Middle (MITM) attacks are involved, and provided security best practices to mitigate them. We also highlight the importance of adopting a secure architecture to protect against cyber security threats and the need for security measures for IoT devices. By incorporating these points into daily practice, users can gain insights into the challenges and risks of IT/OT convergence and the actions that can be taken to mitigate these risks.
What is a Man-in-the-Middle (MITM) attack?
An attacker can use the MITM attack to intercept the communication between two devices, and gain control to perform malicious actions such as reading and writing data, or even execute commands. MITM attacks can be carried out through various methods, such as ARP spoofing, DNS spoofing, SSL stripping, etc. |
IT/OT convergence
IT and OT systems aim to have different priorities for security considerations. While security on IT systems focuses on protecting user data, OT systems primarily emphasise system availability, physical safety during operations, and the completeness of data. Since most OT systems have longer lifecycles than IT systems, this may result in some legacy OT systems still running in factories. As OT systems are usually located in an isolated network environment, security has yet to be fully considered during the network design phase, resulting in a lack of protective measures and cyber defense.
A Cyber Security Case Study on IT/OT Convergence
Previously, HKCERT collaborated with Dr. LUO Xiapu, Professor of the Department of Computing at The Hong Kong Polytechnic University and his undergraduate student, Mr. TANG Ho Tim, to conduct a cyber security case study on standard Programmable Logic Controllers (PLCs) to raise public awareness of the importance of strengthening IoT security in critical infrastructures, explicitly focusing on MITM attacks.
Testing Target and Expected Outcomes
The test involved developing a light traffic system to create a testing environment. The simulated MITM attack aimed to show how attackers can intercept and change communication between the PLC and its components, potentially leading to unauthorised access and compromise of the system.
Testing Target
The test focused on the web server of the PLC system rather than the PLC itself, assuming that the web server features were enabled as the default.
Expected Outcomes
It was predicted that the test would identify security flaws like buffer overflows or command injection that could let an attacker run malicious code on the target machine to carry out an MITM attack.
Testing Environment and Equipment
The test was to simulate the scenario of using a PLC and remote controlling it through a web-based network environment. The devices used in the testing environment include:
Pre-setup Environment
- A powered-on PLC setup connected with traffic light bulbs and a network switch
- Setup PLC with web management feature and the settings remain with factory default
Hacker
- Laptop connecting with the network switch (Same network environment with PLC)
- The laptop has been installed and is running Windows 11 operating system and Burp Proxy software
Assumption
- The hacker hijacked and gained initial access to the internal network where the PLC was placed.
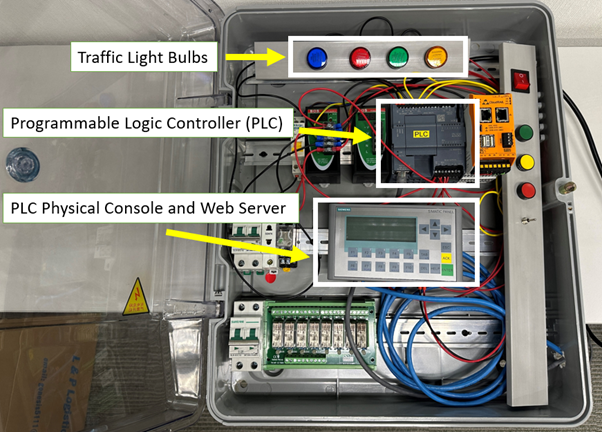
Testing Method and Steps to Simulate a MITM Attack
A simulation of a hacker launching a MITM attack would be separated into two steps – Reconnaissance and Weaponisation, in the use of Burp Proxy software:
Reconnaissance – Sniffing and Analysis of Network Traffic
- To prepare for launching MITM attacks, The hacker would set up a proxy and lure the user to connect through it.
- The hacker uses the Burp Proxy to intercept traffic between the user's browser and the web server. A POST request is sent to the web server when the user tries to log in again.
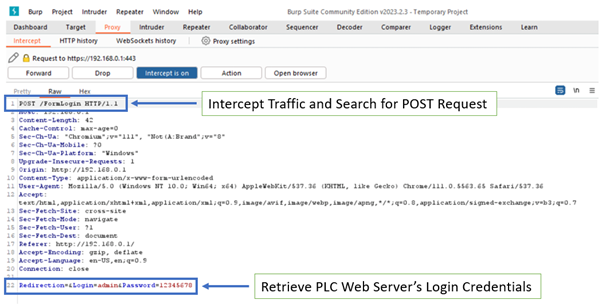
- The hacker views the login credentials displayed in Burp Proxy, showing encryption between the browser and PLC before sending the login credentials.
Weaponisation – Modify the Sniffed Network Traffics and Send Back to PLC
- The hacker could change the intercepted packets by dropping or sending them out. By using Burp Proxy, the hacker could copy the intercepted requests and manipulate its session cookie to obtain control of the PLC.
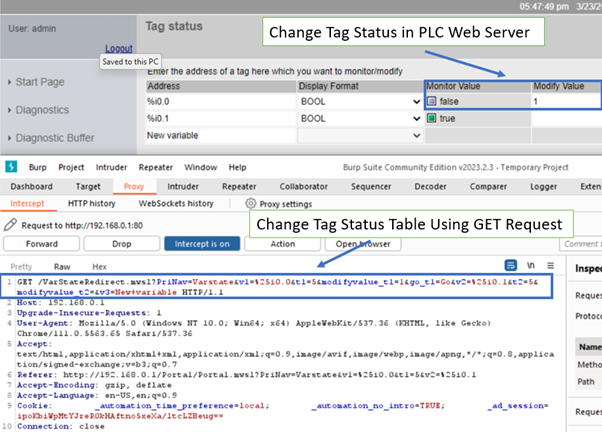
- To take control of the PLC, the hacker would send some manipulated requests with CURL - a simple command line tool to send custom web requests. Some customised web requests were tested and changed the state of the PLC successfully as shown below:
- The hacker could change the tag status table to watch or alter the operation of the PLC system by sending a GET request.
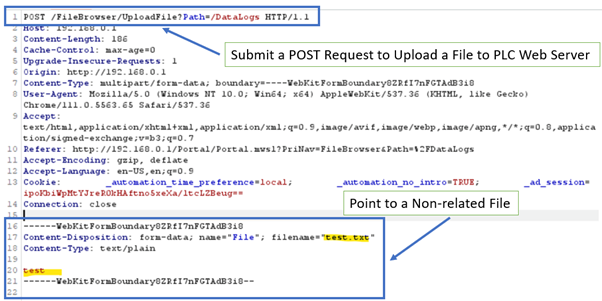
- The hacker could change uploaded files by changing the file name or content by sending a POST request, causing them to become unavailable or infect other facilities or devices.
- The hacker could remove files by sending a GET request to change the file name from one to another or performing a brute force with a dictionary attack.
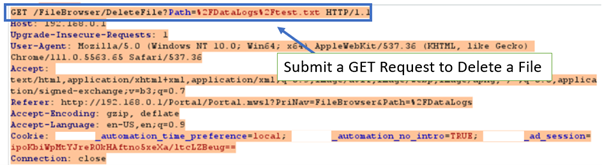
After performing the MITM attack, the findings were significant. The above findings proved how the hacker could use Burp Proxy to gain access to sensitive information, change CPU operations, and upload malicious code to the device. This showed that the hacker can successfully perform a MITM attack using the Burp Proxy software in the scenario of IT/OT convergence.
Other Risks Found in the Study
The study found both successful and risky findings. On one side, the project performed a replay attack on a web server and a dictionary attack on web applications. However, the study also found several vulnerabilities in the test PLC that pose significant risks. These vulnerabilities include the ability of an attacker to use the Industrial Exploitation Framework (ISF) to perform a replay attack on the test PLC [2]. Additionally, the study proved how an attacker could use an injector tool to perform a Denial of Service (DOS) attack on the PLC.
Conclusion
Before converging IT and OT systems, sufficient preparations are required to reduce the risks. The lack of technical professionals with complete understanding of all the systems can make the convergence of IT and OT systems challenging. Therefore it is necessary to update the company's security, operation, and maintenance policies after the convergence.
It is important to note that the study focused on the web server of the PLC system rather than the PLC itself, assuming that the web management features are enabled as the default. Overall, this case study serves as a reminder of the importance of securing IT/OT convergence systems against potential cybersecurity incidents, particularly those related to MITM attacks.
Security Best Practices for Mitigating Risks in IT/OT Convergence
Organisations should take a proactive approach to cyber security to mitigate the risks associated with IT/OT convergence, explicitly focusing on mitigating Man-in-the-Middle (MITM) attacks. The following are some best practices that organisations should consider:
- Conduct regular network and security assessments to find potential vulnerabilities and risks;
- Develop a risk assessment report finding the risks associated with MITM attacks in their IT/OT convergence environment;
- Formulate a strict implementation plan that addresses and prevents the identified security risks and vulnerabilities in the first place, such as implementing secure communication protocols, encryption, and strong authentication and access control measures;
- Update operational policies to reflect new security measures and best practices for detecting and preventing possible attacks;
- Adopt a secure architecture, such as the Purdue Reference Model or the "Zero Trust" architecture, with clear boundaries and strict access controls to prevent unauthorised access and limit the attack surface;
- Use intrusion detection and prevention systems to watch network traffic and detect and prevent potential MITM attacks before they cause harm to IT/OT convergence systems:
- Perform patch management to ensure that IT/OT convergence systems are regularly patched and updated to address known vulnerabilities;
- Refer to HKCERT’s "IoT Security Best Practice Guidelines" to adopt security best practices in the use of IoT devices, and formulate the incident response plan in their environment by referring to HKCERT’s "Incident Response Guideline for SMEs".
Reference
Related Tags
Share with
