Potential threats of Universal Plug and Play (UPnP) service exposure to the Internet
Some people are using UPnP to play digital media content on TV or play online games but they may not be aware of that. A recent research conducted by Rapid7 reveals that around 40-50 million network-enabled devices are at risk due to vulnerabilities found in the Universal Plug and Play (UPnP) protocol, which are exposing millions of users to attacks that could lead to a remote compromise of the vulnerable device. Please read this article to check out if you are affected by the vulnerabilites, and how to mitigate the security risks.
(A) What is UPnP?
Universal Plug and Play (UPnP) is a set of networking protocols designed to free users from configuring network devices at home and corporate environment. It allows networked devices to discover each other automatically, configure themselves so that they can talk to each other seamlessly without human intervention. UPnP supports a wide range of device categories such as network-attached printers, Internet gateways, and consumer electronics equipment.
The UPnP standardization organizations have standardized a few profiles which are in widespread use. The most used profiles are:
- Internet Gateway Device (IGD) profile
- Audio/Video (A/V) profile for media management, discovery and control, which is the basis for Digital Living Network Alliance (DLNA) standard
If you are interested in how UPnP works technically, you can read Appendix I: "How does UPnP work?"
(B) When do we use UPnP in Internet Gateway Device (IGD)?
Network Address Translation (NAT) is commonly used nowadays in IPv4 network. It allows multiple internal hosts with different private IP addresses to share a single public IP address of a router. The router keeps track of the outgoing traffic of internal hosts. With this knowledge the router can reroute return traffic to individual hosts. However, the router cannot support Internet protocols such as VoIP that requires end-to-end connectivity initiated from both sides. UPnP provides the NAT-enabled router a specific configuration (e.g. port mapping/forwarding) to support such protocols to allow incoming packets reaching the correct internal hosts.
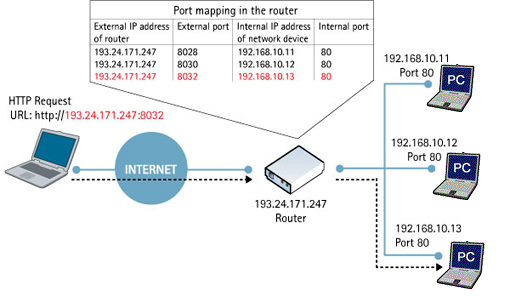
Picture 1: Port mapping/forwarding configurations are required for incoming traffic
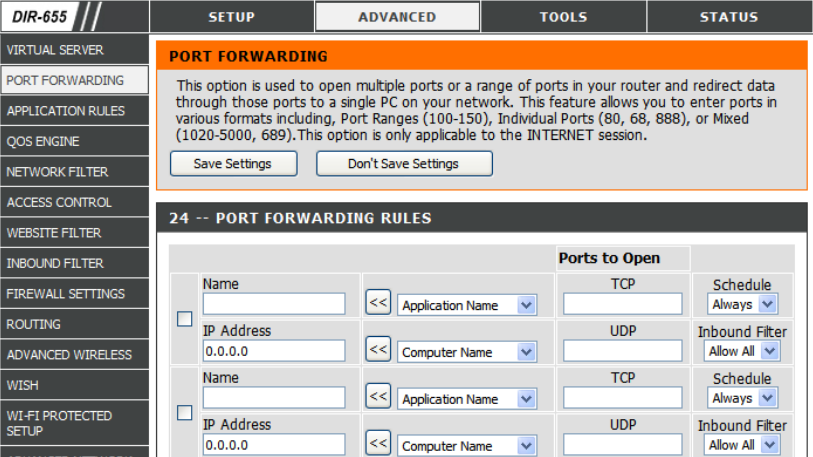
Picture 2: Port mapping/forwarding settings in router configuration page
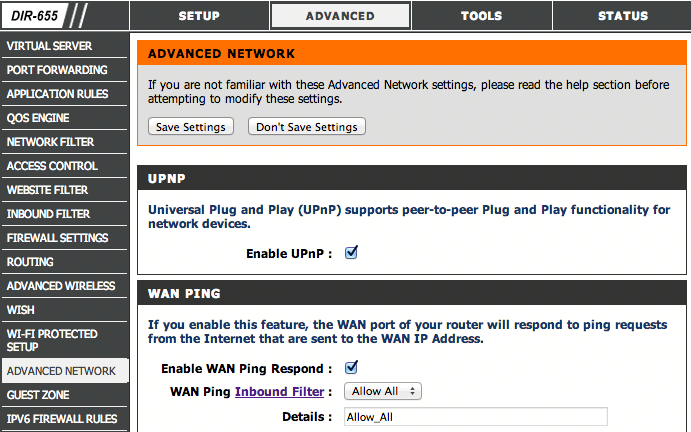
Picture 3: UPnP option in router configuration page
Thus, an UPnP controller behind the IGD can enable traversal of the IGD from an external address to an internal client by adding a port mapping. For example, applications with UPnP support (e.g. Skype) take care of port forwarding automatically for you. You just launch the application and activate the preset rules. It can tell the router when to forward and when to stop forwarding automatically and you do not need to change the port mapping settings in the router. Otherwise, without UPnP support, you need to specify port forwarding rules for incoming connections in the router manually.
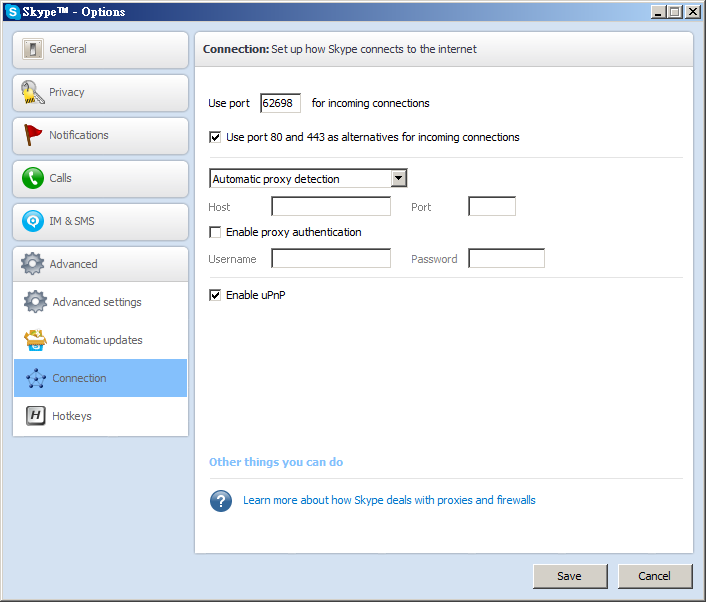
Picture 4: UPnP option in Skype configuration
(C) Security vulnerabilities of UPnP
In January 2013, Rapid7 revealed that at least 40-50 million of network devices were at risk due to security flaws in the UPnP protocol. More than 6,900 product models produced by 1,500 different vendors were found containing at least one known vulnerability, with 23 million systems housing the same remote code execution flaw.
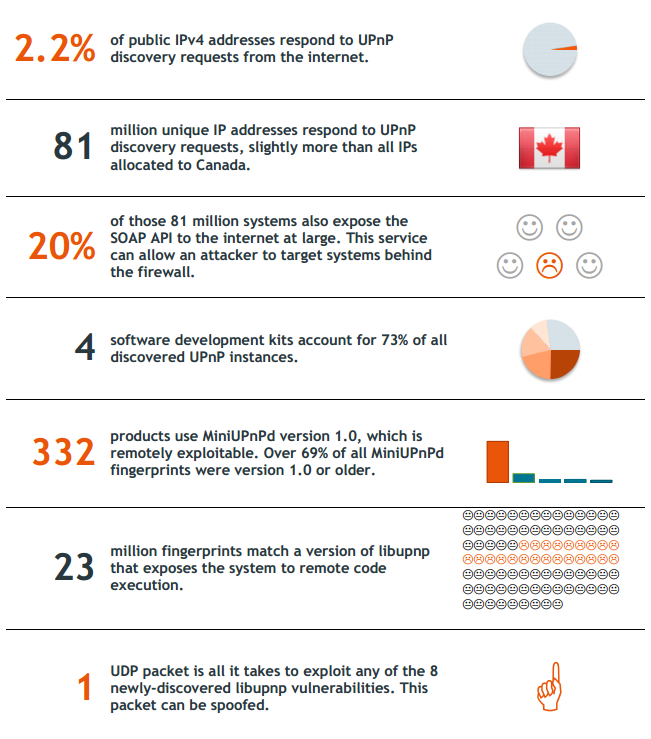
Picture 5: Summary statistics from Rapid7
UPnP is designed to allow easy communication between computers and network-enabled devices over the local network. This protocol is enabled by default on millions of systems. The huge number of UPnP-exposed systems connected to the Internet with exploitable vulnerabilities result in severe security impact. These issues potentially expose millions of users to remote attacks that could result in theft of sensitive information or further assaults on connected machines.
Widespread Exposure of the UPnP SSDP Service
The UPnP SSDP is designed to allow device discovery over the local network. This service exposes version information and network configuration details over UDP port 1900. There were 81 million unique IP addresses respond to UPnP discovery requests, equivalent to 2.2% of all public IPv4 addresses. In other words, these devices potentially allow malicious party to collect their system information and network configuration.
Widespread Exposure of the UPnP SOAP Service
The UPnP SOAP service provides access to device functions that should not be allowed from untrusted network, including the ability to "open holes" through the firewall. There were 20% of the 81 million systems (i.e. approximately 17 million systems) exposing the SOAP service to the Internet which potentially allow malicious users to attack them.
Exploitable Vulnerabilities in UPnP Implementation
Over 73% of all UPnP instances discovered through SSDP were derived from four software development kits such as Intel/Portable SDK for UPnP Device (libupnp) and MiniUPnP. The heavy concentration substantially increases the impact of any vulnerabilities found within these implementation. For example, over 25% of all exposed SSDP services (approximately 23 million systems) are using Portable SDK for UPnP Device (libupnp) versions with exploitable vulnerabilities.
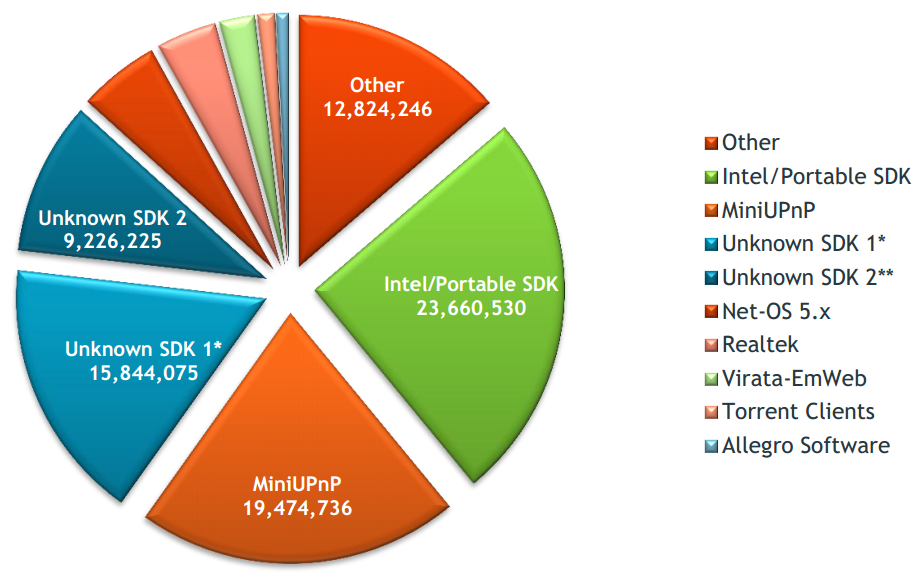
Picture 6: Distribution of exposed UPnP implementationsNetwork Devices use Outdated UPnP Implementation
System information such as software library version may be exposed in the SSDP response. The analysis result showed that the majority of exposed devices are using UPnP libraries that are over four years old. Even devices that were recently manufactured were still using outdated UPnP software libraries, which were vulnerable to attack.
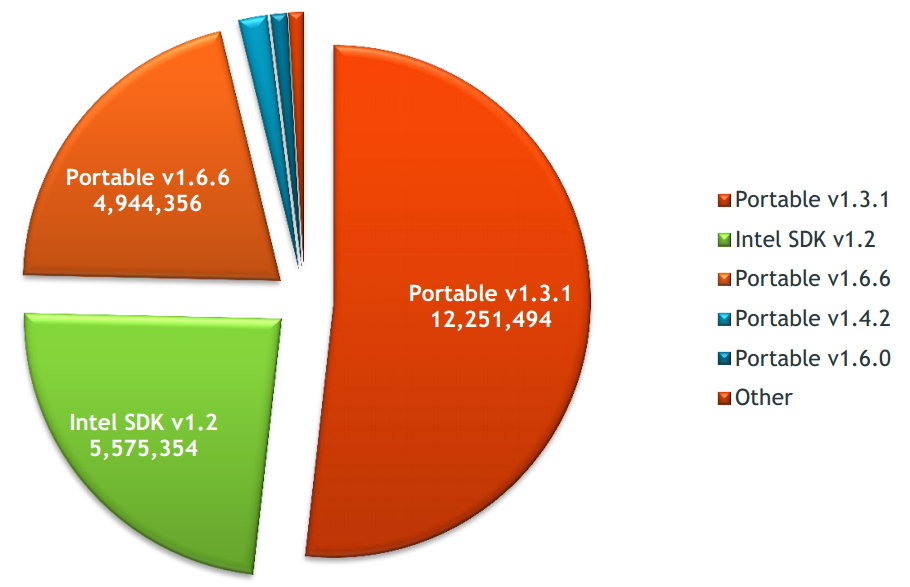
Picture 7: Version distribution - Portable SDK for UPnP Devices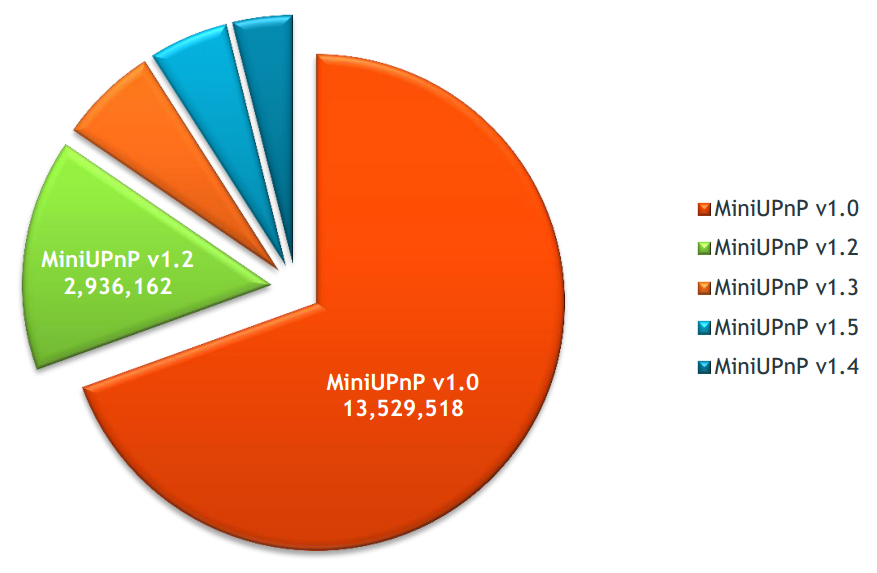
Picture 8: Version distribution - MiniPnP
(D) Mitigating security risks related to UPnP security vulnerability
The major problem is the exposure of UPnP service to the Internet. We have to close this exposure and patch the security vulnerability.
Detection
You may use the following “UPnP Router Security Check” online tool to test your router and identify whether your UPnP is exposed to the Internet.
Visit the page “UPnP Router Security Check” online tool ( http://upnp-check.rapid7.com/scan )
Picture 9: “UPnP Router Security Check” online toolIf your UPnP router is exposed to the Internet and probably vulnerable to security flaws in the UPnP protocol, you may get similar warning message as shown.
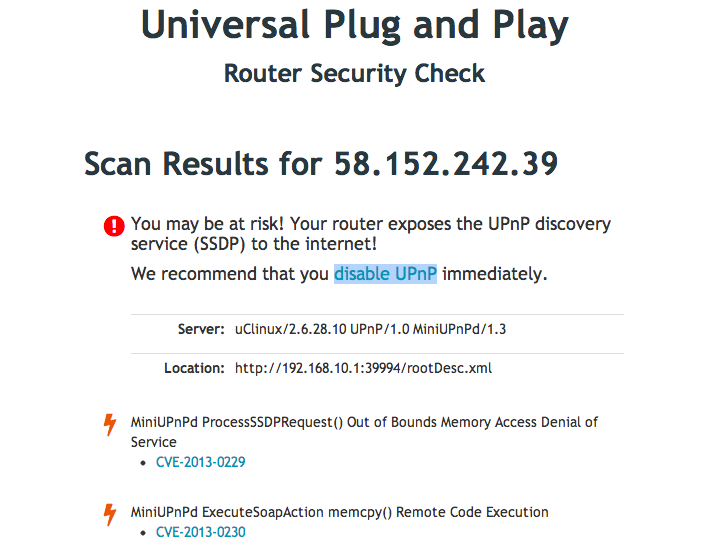
Picture 10: Warning message will be shown due to UPnP exposureYou are suggested to disable UPnP feature in your router.
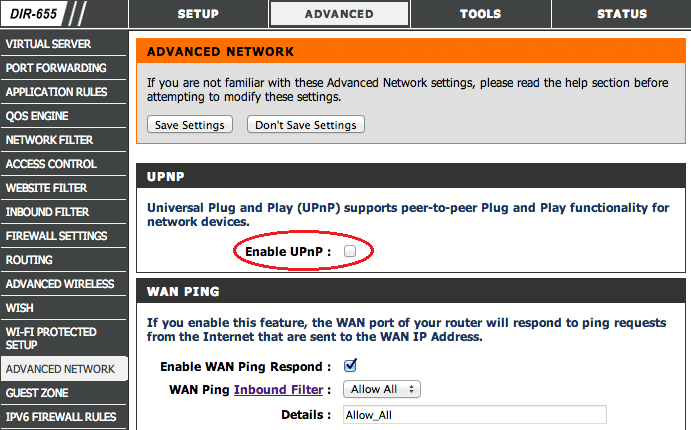
Picture 11: UPnP option in router configuration pageIf your router does not have UPnP exposed to the Internet or have UPnP disabled already, you should get the following scan result.
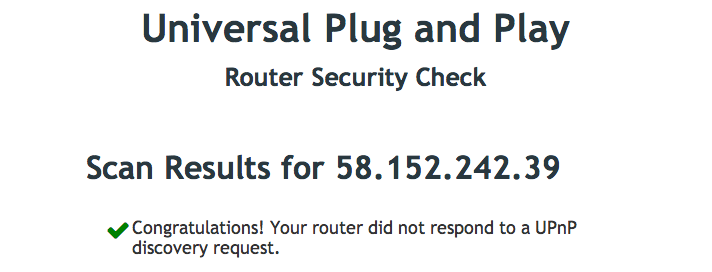
Picture 12: Scan result showing UPnP is not exposed
Prevention
Apply Firewall policy
- You may consider deploying firewall rules to block accessing UDP port 1900
Disable UPnP
- You may consider disabling UPnP especially request from the Internet

Picture 13: UPnP option in router configuration page
Apply patch update for UPnP vulnerabilies
Apply patch update for affected system/device once available from vendors. Check vendor announcement and products for UPnP, consider disabling UPnP if flaws are identified in vendor devices.
Best practice of security
As a best practice of security, you should not enable any feature that you do not require. If you are not sure if you need UPnP, you can disable it in your router for some time to verify.
Reference information about UPnP products
- Devices using Portable SDK for UPnP Devices (libupnp)
https://docs.google.com/spreadsheet/ccc?key=0ApUaRDtAei07dFdOWXdKRUVaUTdRYndnbW5zajRyTmc#gid=0 - Devices using MiniUPnP
https://docs.google.com/spreadsheet/ccc?key=0ApUaRDtAei07dDhwelZDQlYyQVJhbWRtUEIwVEVyRFE#gid=0 - Devices with SOAP API Exposure
https://docs.google.com/spreadsheet/ccc?key=0ApUaRDtAei07dGxkSHN1cEN3V2pmYW4yNkpZMlQ0Rmc#gid=0 - Cisco Security Advisory: Portable SDK for UPnP Devices Contains Buffer Overflow Vulnerabilities
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20130129-upnp
- https://community.rapid7.com/docs/DOC-2150
- https://community.rapid7.com/community/infosec/blog/2013/01/29/security-flaws-in-universal-plug-and-play-unplug-dont-play
- https://community.rapid7.com/servlet/JiveServlet/download/2150-1-16596/SecurityFlawsUPnP.pdf
- http://www.kb.cert.org/vuls/id/922681
- http://support.microsoft.com/kb/323713/en-us
References
Appendix I: How UPnP works?
(Note that this part may be a bit technical.)
Six processes are involved in UPnP Networking
- Addressing: UPnP-capable devices need to be hot-plugged in the network, it tries to get an IP address through DHCP when getting connected to the network.
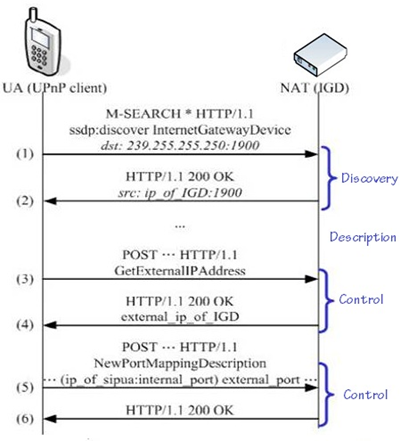
Picture 14 - Discovery: Discovery is handled by the Simple Service Discovery Protocol (SSDP). When a device is attached to the network and addressed appropriately, it will advertise its services to control points on the network. It sends out a discovery message to the multicast address on port 1900 via the UDP protocol. Similarly, control points can also discover services provided by devices on the network.
- Description: Once the devices are discovered, control points can retrieve device description and detailed service information from the URL provided by the devices in the discovery message. The description may include the product name, model name, serial number, vendor ID and embedded services, etc.
- Control: After a control point has retrieved a device description and detailed service information, the devices can be manipulated by control point through control message expressed in XML using SOAP. Requesting a service is done by sending a SOAP message to the control point with the right parameters, which process the request and return output which is again encapsulated as a SOAP message.
- Event notification: "State variables" are used for keeping some form of state in UPnP devices and programs. A program can subscribe to state changes: if there is any update on services provided when a state variable is changed, event message with the new state is sent to all programs/devices that have subscribed to the event.
- Presentation: The presentation layer refers to the human controllable interface, for example, the web interface on a router so that users can configure and control the devices
Share with
