Information Security Outlook 2013
The major security threats that built up the information security environment last year will continue to pose threats to the Internet this year. HKCERT has analyzed the situation of 2012 and projected the security outlook for 2013.
Cyber Attack
2012 saw the increasing number of cyber attacks using the Distributed Denial-of-Service (DDoS) tools as the means. Cyber attacks targeting small-to-medium sized enterprises (SMEs) were made headlines in Hong Kong early 2012 when a number of members of the Chinese Gold and Silver Exchange were attacked and blackmailed to pay ransom money. Later, attacks targeting at other organizations, including HSBC websites were reported. The motives of these attacks were mainly financial, though there were also attacks because of political or ideological disagreement. Nation or State sponsored attacks were on the rise.
For 2013, we expect the number of local attacks will continue to grow. Hacktivism activities due to cyber conflicts will increase. Because of the low preparedness, small-to-medium-sized enterprises (SMEs) will also become targets of attack. Organizations should conduct a risk assessment on whether they will be a possible target and make preparation on the response actions.
HKCERT Statistics
In HKCERT, we have received more incident reports relating to hacking and web defacement in 2012. Comparing to 2011, there is an increase of 124.6% of web defacement cases, and an increase of 29.1% of hacking incidents (See figure 1 and 2 ).
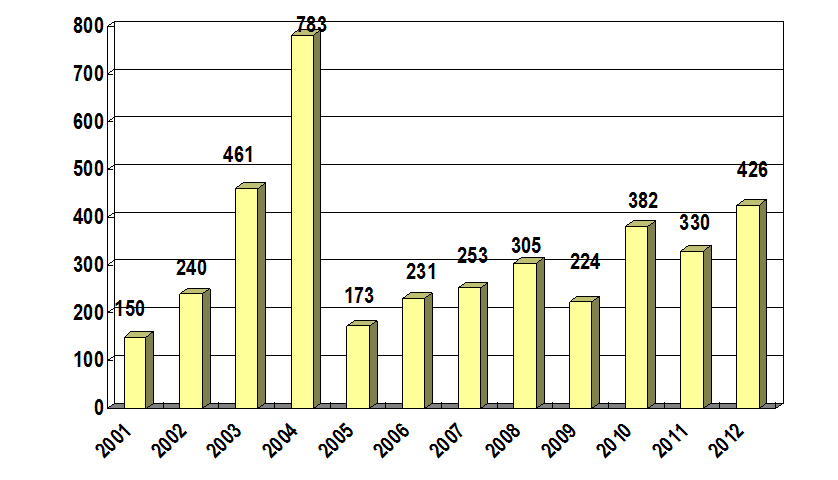
Figure 1 - Number of Hacking Incidents
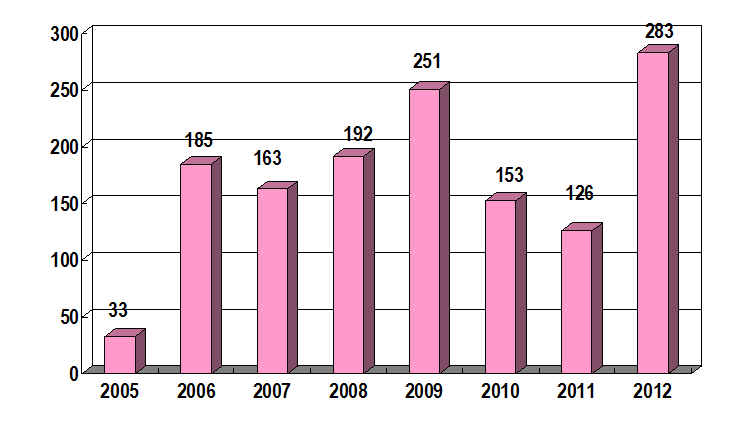
Figure 2 - Number of Defacement Incidents
The increase indicated that the protection mechanisms deployed by many organizations are still not adequate. At the same time, hacker groups continued to identify new ways to intrude into systems so that they can make use of these systems to launch attacks or to host malicious contents.
In addition, there were 429 security alerts published by HKCERT in 2012, which is an increase of 25.1% compared to 2011, indicating the seriousness of vulnerabilities identified (See figure 3). Hackers usually exploit these vulnerabilities to gain access to ill-prepared computers.
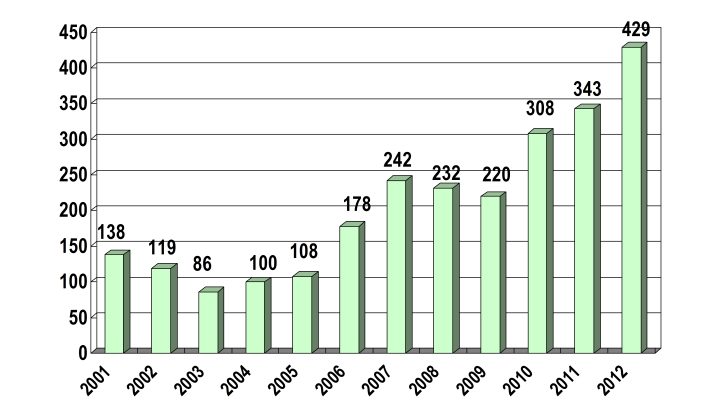
Figure 3 - Number of Security Alerts Published by HKCERT
Malware and Botnet
Malware and Botnet are the major root causes for most of the security problem found today. For 2013, we envisage that there will be more Advanced Persistent Threats (APT) targeting government and large enterprises around the world. These APT attacks use sophisticated malware that will stay undetected for months to gather sensitive information for future attacks.
Massive compromise of websites and individual machines will continue. Typically popular content management systems like Wordress, Drupal and Joomla will be targeted. Hackers will use these 24x7 available machines launch DDoS attacks, and to send out phishing or spamming messages. In some cases, the data stored in these compromised machines were also stolen, resulting in leakage of personal data. Owners of these compromised machines usually do not know the occurrence of such incidents.
Some common platform vulnerabilities such as Java will be targeted Mac computers were previously rarely attacked, will be target of attacks due to the popularity.
Smartphone and Mobile Devices
With the wide adoption of BYOD (Bring Your Own Device), mobile devices especially smartphones have become obvious targets for criminals. There were also increasing number of malicious apps found in application stores, in particular those “unofficial” ones. We have noted the financial loss reported in other places that were caused by “Toll Fraud” and “Premium SMS”. Mobile spyware and information theft will grow. Compromised mobile device was seen forming a botnet was seen in 2012. These cases may also happen in Hong Kong.
We are also aware that the financial institutions will jointly promote the mobile payment using Near Field Communications (NFC) and other technologies. We are sure that the cyber criminals will try to take the opportunities to exploit any vulnerability they can find in these new services to obtain financial gains.
Cloud Computing
The concerns on the availability of cloud services and possible leakage of corporate information did not reduce, based on our observations of cloud service outages in 2012.
At the same time, cyber criminals will try to exploit the vulnerabilities found on cloud services in order to take control of the system or steal valuable information, as they do for computers nowadays. They will make use of the huge resources available from the cloud services to crack passwords, to host malicious websites and botnets, and to control these botnets to launch widespread attacks.
On the other hand, new security service offerings which is enabled by cloud computing emerges, such as web application security filtering services. We expect to see more security features provided by cloud service providers so as to differentiate themselves from the competitors.
Information Leakage
Since the widely published report on information leakage back in 2006, there were still a lot of reports on information leakage today despite of those guidelines, practices and advice published. We expect new reports on information leakage on year. New channels like smartphone and mobile devices, social networking platforms, and cloud computing. For corporations and individuals, they have to keep updated on these technologies and review regularly on the possibilities of information leakage through these channels.
Advices for the Public
We are seeing more sophisticated security attacks. We should take security seriously and be prepared of large scale attacks. Corporations should have a policy to classify sensitive data, access security risks and to define the relevant data protection measures.
Besides deploying technologies like malware detection and prevention, firewall and intrusion prevention systems, users should always stay updated in security patches to minimize the opportunity for the attackers.
It is a security best practice to limit your security exposure. Users are advised to uninstall unnecessary application, for example if you do not run any application based on Java, you can uninstall Java from your machine.
Users should also be aware of threats of emerging technologies, e,g. cloud computing, mobile computing and social networking.
Here are some useful security guidelines from HKCERT:
Share with
