Impact of terminating the DNS server of DNSChanger
Recently, the Information Security News reported that the U.S. Federal Bureau of Investigation (FBI) would shut down those domain name servers (DNS - Note 1) associated with the DNSChanger Botnet on March 8. What is the impact of this incident to the Internet users? Hong Kong Computer Emergency Response Team Coordination Center (HKCERT) would like to give some the background information of DNSChanger, method to detect infection and solution for the affected users to handle it in time.
[Updated on Mar 7, 2012]
|  |
Background
The DNSChanger botnet malware has more than 2000 variants (Ref. 1). It is estimated that there are over four million infected computers worldwide, affecting more than 100 countries. This botnet was allegedly operated by an IT company called “Rove Digital” in Estonia since 2007, until the mastermind of cybercrime ring was arrested in 2011 (Ref. 2). |
What is the Impact of DNSChanger infection?
DNSChanger malware primarily spreaded when a user accesses a particular website or downloads online video viewer software and get infected. The DNSChanger malware will secretly alter the DNS settings on the affected computer pointing to the DNS server established by cybercrime ring to completely control DNS to resolve the desired IP address. The cybercrime ring can use DNS Changer botnet to route the users to access specific web sites unknowingly, including replacing the advertisements on web sites that are loaded by users to generate click-fraud or implant other malicious software. |  |
 | Why is it March 8?
In November 2011, in the "Operation Ghost Click" (Reference 3), FBI successfully shut down the DNSChanger Botnet. According to a court order, in order to avoid the infected computers to lost connection with Internet immediately, FBI was authorized to set up a number of temporary DNS server to maintain the DNS services for the victims to this issue within 120 days. This order would be expired on March 8, 2012. If FBI decide to close these temporary DNS servers as scheduled, several millions of the DNSChanger bots worldwide would not be able to connect to the Internet. To properly handle this problem, we must help the victims clean up the malware as soon as possible. |
Am I affected?
The DNSChanger malware can infect the Microsoft Windows and Apple Mac OS X operating systems. It also attempted to use the default login name and password of the small office or home broadband routers to break in and change the DNS settings. To check if your computer or broadband router is affected or not, you can use the following two methods:
Method 1 – Use the DCWG EyeChart:
Open the web browser (e.g. Internet Explorer, Firefox, Chrome or Safari) to access the testing site provided by DNS Changer Working Group (DCWG) (Ref. 3):
 If the test result is green, it indicates that your computer is normal. |  If the test result is red, it indicates your computer or broadband router's DNS server setting was pointing to the known rogue server. Affected computers are recommended to follow the instruction in "How to deal with the infected computer and Broadband Router” for detailed examination. |
Method 2 – Manual checking:
1. Find out the IP address of DNS server
Computer
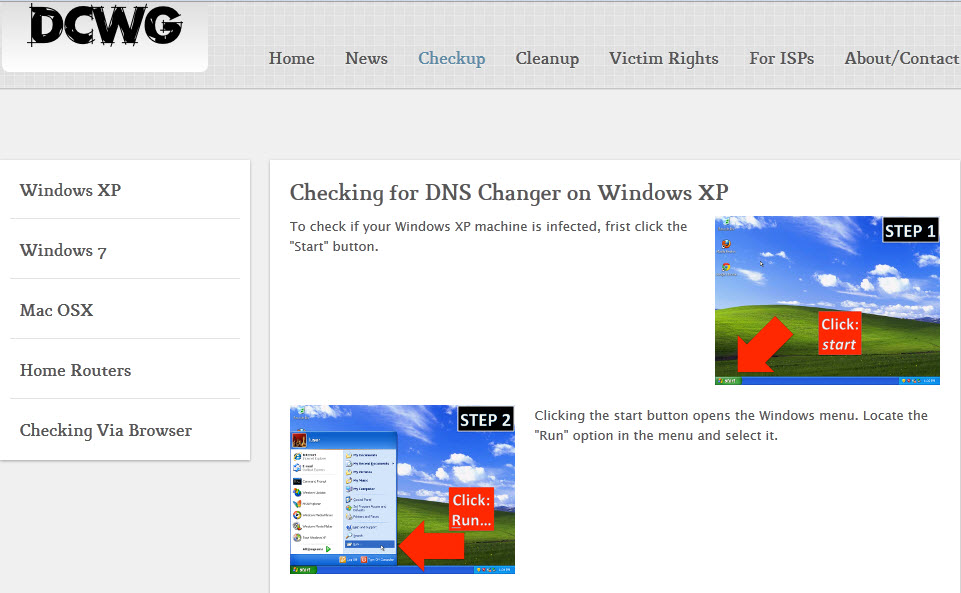
Follow the instructions in the DCWG web page below, select your operating system and follow the steps to check the IP address of your current DNS server
http://www.dcwg.net/checkup.html
Broadband Router
To check the DNS server IP address used by your broadband router, please refer to the documentation provided by the vendors.
2. Check if the DNS server IP address is used by DNSChanger
Enter the IP address found from previous checking in online checking tool web page provided by FBI
https://forms.fbi.gov/check-to-see-if-your-computer-is-using-rogue-DNS
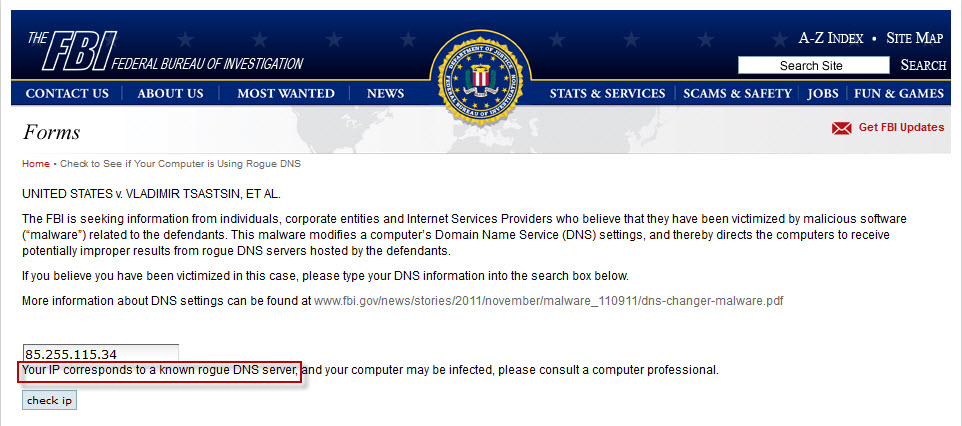
If the result is "Your IP corresponds to a known rogue DNS server", your computer or broadband router's DNS server setting was pointed to the known rouge server. It is recommended to follow the instruction in “How to deal with the infected computer and Broadband Router” for detailed examination.
 |
How to deal with the infected computer and broadband router?
Computer
|
Broadband Router
Suggest to follow the documentation provided by the vendors to reset the DNS server settings and change the password of default administrator account.
Reference:
- http://www.paloaltonetworks.com/researchcenter/2012/02/dnschanger-rogue-dns-servers-taken-down/
- http://blog.trendmicro.com/esthost-taken-down-biggest-cybercriminal-takedown-in-history/
- http://www.fbi.gov/news/stories/2011/november/malware_110911
- http://www.dcwg.net
- http://threatpost.com/en_us/blogs/us-judge-extends-life-ghost-click-infected-machines-030612
Note:
- DNS (Domain Name System) - A distributed database of domain names and IP addresses mapped to each other, can make people more convenient to access the Internet, without having to remember complicated and unfriendly IP address.
Share with
