Flashback malware infecting hundreds of thousands of Mac computers
Once upon a time there was a myth like this “Mac OS is safe and does not need antivirus”.
Today this myth has been challenged by the “Flashback” malware. According to a Russian security antivirus product provider, “Flashback” malware had infected more than 600,000 Mac systems worldwide, with most in the U.S. and Canada. Attack against Mac systems one after one, a new malware "SabPub" was discovered.
 Background
Background
Flashback was discovered in September 2011 and masqueraded as legitimate software “Flash player installer” to trick Mac user to update the Flash player. It evolved quickly and now it uses drive-by download1 technique to infect computer without user attention. Flashback malware steals passwords and other information from users through their web browser and other applications.
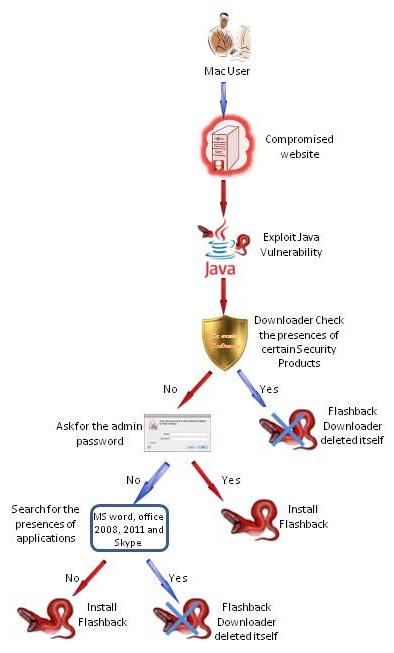
The flow of infection is as follows. Firstly, when a user using a Mac computer visits a website which has been previous compromised, the exploit script embedded in the web page determined it is a Mac OS and served an exploit that targeted the unpatched Java vulnerabilities (CVE-2011-3544 and CVE-2008-5353). A success in the exploit will cause a trojan downloader installed. The trojan will detect if certain security products (Little Snitch, Xcode, VirusBarrier, iAntiVirus, avast!, ClamXay, HTTPScoop and Packet Peeper) installed on the Mac PC. If so it will delete itself and do nothing, otherwise it will prompts for the administrator password.
If the user provided the administrator password, the trojan will download and install Flashback components to the machine. Otherwise the trojan will search for the presences of Microsoft Word, Office 2008 and 2011 and Skype applications. If the application is found, the Trojan will stop and delete itself to avoid compatibility problem. If none of the above applications is found, the Trojan will download and install Flashback on Mac computer. When Flashback is successfully installed, it will report to the botnet command and control server.
Detection and Removal
It appears that Flashback is designed to infect the Mac computers which do not install security software. It will stay quiet and become part of a botnet. You are immune of this malware infection if you have installed the above mentioned security products on your Mac.
There are many tools and scripts for Flashback detection and removal on the Internet. Some involve manual procedure to check the system file. Some automate the process by simply click and run. You can refer to the following web sites for the detection and removal tools.
- F-Secure Flashback Detection and Removal Tool
This tool can detect and remove Flashback malware. - Kaspersky Lab Flashfake Detection Tool
Simply input the Mac’s Hardware UUID on the web site to check if you are infected.
Kaspersky Lab Flashfake Removal Tool
This tool can detect and remove Flashback malware. - Dr. Web Anti-Flashback web site
Simply input the Mac’s Hardware UUID on the web site to check if you are infected
Dr. Web Light Scanner for Mac OS X
Free antivirus software for Mac and it can detect and remove FlashBack Malware. - Apple Java security update
This Java security update removes the most common variants of the Flashback malware but it only support OS X 10.6 and 10.7. You can refer to the abovementioned tools, if your Mac running OS X 10.5 or earlier.
http://support.apple.com/kb/HT5243
http://support.apple.com/kb/HT5244
http://support.apple.com/kb/HT5246
Preventive Measure
 Patching the vulnerability is a race against time and malicious hackers. Obviously Apple did not handle this vulnerability timely. Oracle issued a patch in September 2011. Apple has her own way of patch release. She has no managed patching schedule and releases security update on demand. Apple released the patch in end of March 2012, leaving a six month opportunity window to the hackers.
Patching the vulnerability is a race against time and malicious hackers. Obviously Apple did not handle this vulnerability timely. Oracle issued a patch in September 2011. Apple has her own way of patch release. She has no managed patching schedule and releases security update on demand. Apple released the patch in end of March 2012, leaving a six month opportunity window to the hackers.
Microsoft, on the other hand, has a well informed security update schedule on every second Tuesday of each month. This practice has been adopted by other software suppliers like Adobe and Oracle. In the Flashback incident, others security companies also released detection and removal tools for this malware earlier than Apple. It seems that Apple has to abandon the myth of security and learn a tough lesson from the Flashback incident to improve Mac security.
We recommend Mac user to run the software update to patch the Java security flaw immediately and disable the Java in your web browser if it is no longer in use. No system can be immune from every threat. Malware are growing and evolving rapidly. Not only Windows, all other platforms such as Linux, Unix, Mac OS and mobile OS should be protected seriously. We highly recommend Mac user to install security suite (including antivirus, personal firewall with intrusion prevention features) on their Mac computers; to turn on real-time protection and to schedule periodic scanning on their computers. Mac users should keep their system updated with security patch and security suite update with security signatures. You can refer to HKCERT Malware Defense Guideline (/my_url/en/guideline/12022902) on our web site.
Last of all, users of any platform should be cautious when browsing and should not open unsolicited attachments.
Reference:
1. Please refer to our Malware defense guideline for the technique of Drive-by-download.
Share with
