Hong Kong Security Watch Report (Q4 2022)
HKCERT is pleased to bring to you the "Hong Kong Security Watch Report" for the fourth quarter of 2022.
Highlight of the 2022 Q4 Report
16,108
+47%
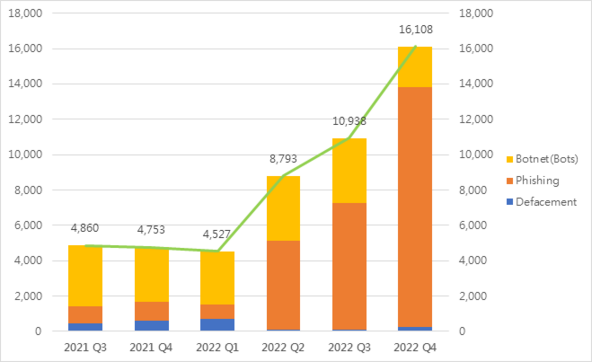
Event Type | 2021 Q4 | 2022 Q1 | 2022 Q2 | 2022 Q3 | 2022 Q4 | quarter-to-quarter |
Defacement | 595 | 718 | 118 | 113 | 249 | +120% |
Phishing | 1,061 | 806 | 5,033 | 7,141 | 13,574 | +90% |
Botnet (Bots) | 3,097 | 3,003 | 3,642 | 3,684 | 2,285 | -38% |
| Total | 4,753 | 4,527 | 8,793 | 10,938 | 16,108 | +47% |
Major Botnet Families in Hong Kong Network
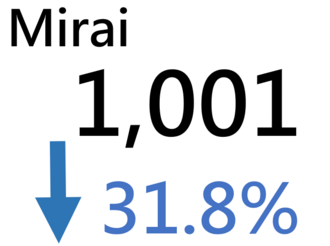
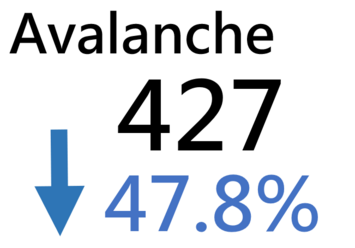
Conficker | 207 | -7.2% |
Nymaim | 165 | -48.1% |
Conficker | 120 | +421.7% |
Tinba | 116 | -64.8% |
Bankpatch | 105 | +54.4% |
VPNFilter | 37 | -15.9% |
Sality | 22 | -88.5% |
Cozi | 23 | +14.3% |
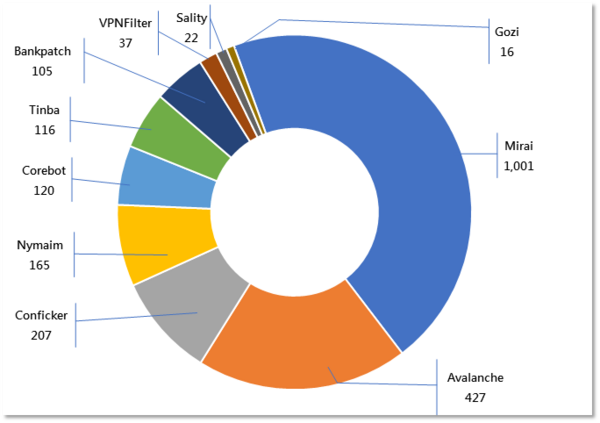
* Individual botnet’s size is calculated from the maximum of the daily counts of unique IP address attempting to connect to the botnet in the reporting period. In other words, the real botnet size should be larger because not all bots are activated on the same day.
Phishing Events Exceed 10,000! Public Must Be More Vigilant on Deception
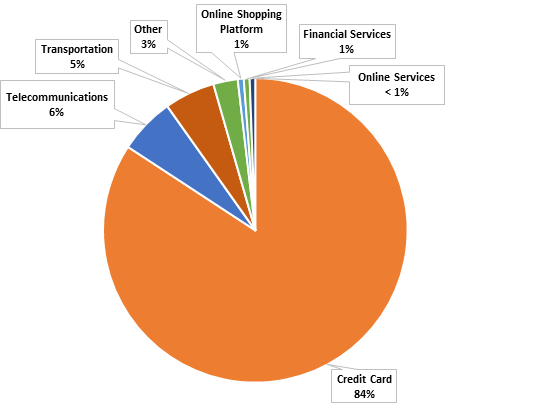
Phishing events have risen for three consecutive quarters and have exceeded 10,000 for the first time, recording a quarter-on-quarter increase of 90% and a year-on-year increase of 11+ times. Data reported that 84% of the phishing websites were credit card websites; 6% and 5% were related to the telecommunications and transportation industries respectively. Although at the time of compiling the report, random testing have revealed that these websites have already been shut down or are no longer accessible, it is believed that hackers intend to defraud users’ credit card information or other personal information through the websites for illegal purposes.
In general, the public holds the view that phishing websites are fake websites created by hackers being directed to through hyperlinks in emails, to lure the victims to enter relevant login names, passwords and other personal information. Hackers then use the information to carry out illegal activities, such as stealing deposits and borrowing money.
However, some members of the public recently reported to have received a text message from a supermarket chain on their phones, instructing them to click on a hyperlink in the message. The name on the text message was the name of the organisation, and the past messages were also the ones that the user had clicked into or used. So, is the phone broken? Are your phone being hacked? Or have hackers hacked the agency? These hackers’ tactics have really made it difficult for the general public to differentiate and identify the source. Anyone who clicks on it carelessly will become the target of hackers. With hackers constantly updating such attacks to maximise their victims’ count, HKCERT has compiled a short piece on their tactics in online shopping and areas for online shoppers to be vigilant in order not to fall into these phishing scams.
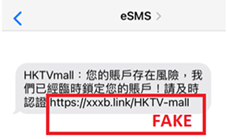
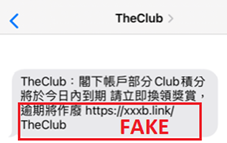
Phishing Instant Messages
The recent common phishing attack method is mainly to send malicious shortened URL links of the phishing sites through smartphone system built-in and third-party instant messaging apps. As most of those messaging apps allow for the setting up of the sender’s name, the hackers could pretend to be a legitimate brand. Below are some examples of instant messages of attacks.
Phishing Sites with URLs similar to Legitimate Sites
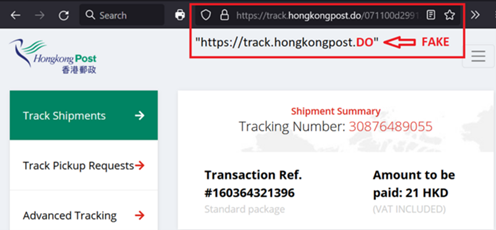
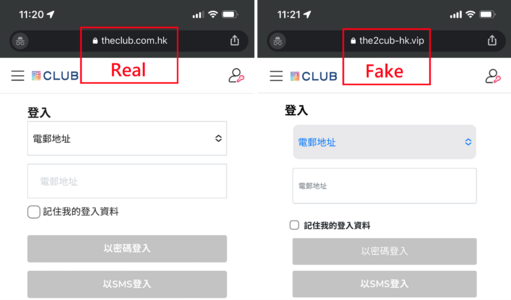
To trick the victims into assuming the phishing sites were legitimate and proceeding to input information, the hackers would register domain names similar to the brand's legitimate website. Such an example is shown below, in which whereas the legitimate domain name of Hong Kong Post should be ‘hongkongpost.hk’, the hacker has hosted the phishing site with the domain name of ‘hongkongpost[.]do’.
Phishing Sites with Replication of Legitimate Sites
Besides having a domain name and a URL similar to those of a legitimate website, the hackers have recently been replicating part of the legitimate websites, such as the login pages. Since this technique would reduce the efforts for designing a new web interface of the phishing site, most hackers would usually change the backend of the web page after replicating from the legitimate website to fit their needs. This would make the users harder to verify whether the browsing page was legitimate.
Phishing Page in Social Media Platform
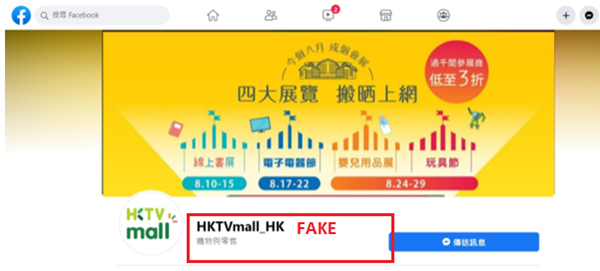
With the widespread public use of social media platforms such as Facebook and Instagram, some hackers would create fake pages on these social media platforms. Most of them would publish some fake promotions on the page attached with links to the phishing sites.
The image below was a Facebook page of HKTVmall created by a hacker, where the design was similar to the official Facebook social media page of HKTVmall. The second image would be the genuine Facebook page of HKTVmall that is being verified by Facebook with a blue badge.

Tips for Safe Online Shopping
- Don't click on any links or attachments from an unknown sender. Always enter the URL of the online shopping platform directly in your browser or use bookmarks. Be careful with the legitimacy of the links and emails. For example, check for spelling and grammatical errors in the URL, or whether the sender is trustworthy. If the website does not use HTTPS for encryption, please be careful and do not provide sensitive information.
- Change the account password of the online shopping platform regularly. Use different passwords for different accounts to prevent from cascading impact if one of them is compromised.
- Enable multi-factor authentications to enhance account security.
- Place orders or check order status from the official website or mobile app only.
- If you receive a suspicious email or instant message, please verify the details at official channels. Do not provide sensitive information to an unknown sender.
- Check your online payment records regularly for suspicious transactions.
- Verify the social media page of an online shop by using the social media verification badge function (Such as the Blue Badge in Facebook and Instagram);
- Adopt anti-phishing feature in web browsers to help blocking phishing attacks; and
- Use the free search engine “Scameter” of Cyberdefender.hk to identify frauds and online pitfalls through email, URL or IP address, etc.
Cyber Focus: Verify from Various Sources to Ensure Security When Searching for Answers with AI

Recently, the artificial intelligence (AI) ChatBot, ChatGPT, has taken the Internet by storm. It is reported that the tool already has 100 million users. Most users say that compared with the traditional search engines which only rely on input queries to provide websites of highly relevance, ChatGPT allows users to ask questions in the format of a person-to-person dialogue and then output responses. In addition, the generated answers are very accurate with detailed explanations, saving the time to search for information after using search engines.
While its developer, OpenAI, says the current free ChatGPT is still in research preview, its popularity marks a major success in bringing AI and machine learning technology to the masses. Recently, major information technology companies have announced plans to integrate AI into their online services: for example, Microsoft will integrate AI technology more powerful than ChatGPT with Bing search engine and Edge browsers; another search engine giant Google will also incorporate its conversational AI service Bard in its products in the coming weeks. It can be seen that, in the near future, more AI technologies will be integrated into different online services and become more involved in our daily lives.
The wide applicability of AI, on the one hand, has made work or life more time-saving and convenient. For example, some people have used ChatGPT to write programmes and articles faster and less error-prone, and the content of the articles generated is also rich and well-organised; but on the other hand, there have also been criminals who used ChatGPT to create phishing email content and even write malware. Although the system developer has added a security mechanism to prohibit the generation of malicious content, cyber criminals have developed evasion methods and sold them as a Crime-as-a-Service (CaaS). Therefore, the potential security issues cannot be ignored.
At the latest annual information security outlook briefing held in February 2023, HKCERT also predicted that attacks utilising AI and CaaS will be among the five major security risks in 2023. It even listed various possible scenarios of how criminals use AI to attack. On top the above-mentioned examples, AI fraud and poisoning of AI models are also included. In summary, risks involving AI are as follows:
- Data privacy and confidentiality: AI requires vast amounts of data for training, which can include sensitive information such as personal details, financial information and medical records. This may raise privacy concerns, as AI models may be able to access and generate sensitive information.
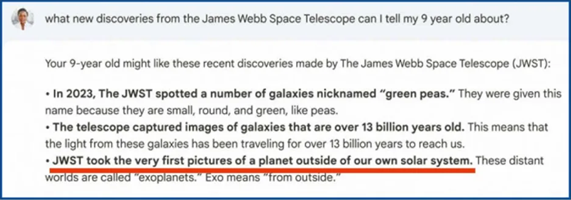
- Misinformation: AI may insert false or misleading information in order to produce coherent and smooth results. Users rely on such information without verification may be at risk of being convinced the misinformation. In addition, the accuracy of the message will also be affected by the training data it receives. For example, the training data of ChatGPT only goes up to 2021, so when asked about the most recent World Cup champion, it will answer France (2018 champion), not Argentina (2022 champion). Other examples of misinformation include a Google ad promoting its ChatBot Bard, which was found to contain misinformation in an answer to a question about the “James Webb Space Telescope.”
- Bias issues: AI training data may come from the Internet, some of its information may contain biases and discriminatory elements. This can lead to AI models producing biased and discriminatory responses. In addition, criminals can also use biased data to train AI models to generate malicious responses. This method is called Adversarial Perturbation.
- Copyright issues: It is important to consider the rights of third parties, for example, owners of any copyrighted material that may be involved in responses output by ChatGPT. Violation of the rights of others, including unauthorised use of their copyrighted material, may result in legal liability. Therefore, when using ChatGPT, please consider and respect the intellectual property rights of its developers and others, and ensure any use of ChatGPT responses complies with laws and regulations.
Actually, AI is a neutral tool and there is no right or wrong in itself. Just like when ChatGPT is asked if it has security risks, its final response is “However, it is important for users and developers to be aware of these security concerns and take appropriate measures to mitigate them.” The ultimate responsibility must lie with the users. Finally, when using AI, please maintain a mentality of checking everything and verify facts from various sources.
HKCERT Security Tips: Always Keep System Security Up-to-Date to Prevent Customer Data from Becoming Phishing Feeds

Local photo printing chain, Fotomax, fell victim to a ransomware attack and malicious encryption of its database in October last year, resulting in the leakage of over 600,000 customer data, including name, gender, date of birth, phone number, email address, contact address and delivery address. The Office of the Privacy Commissioner for Personal Data recently published an investigation report into the incident which found the company to be in breach of the Personal Data (Privacy) Ordinance, thereby issuing an Enforcement Notice to Fotomax, directing it to remedy and prevent recurrence of the contravention.
InvestigationFotomax purchased a firewall in 2018 and enabled its SSL VPN in the following year. Shortly afterwards, the firewall manufacturer announced the discovery of a security vulnerability in the SSL VPN function and urged users to disable it immediately until the operating system had been updated and all account passwords had been reset. It also recommended multi-factor authentication. However, Fotomax did not update the system immediately, which subsequently led to the system being hacked and leakage of customer data. |
The incident reflects the importance of maintaining system security all the time. When learnt of potential threats, appropriate follow-up actions must be taken immediately, and any threats should never be treated lightly. Hence, system administrators should pay attention to the following advice to enhance system security:
- To keep software, operating system, and anti-virus up-to-date and install security patches regularly, especially for systems exposed to the Internet (e.g., firewalls, VPN servers, etc.).
- Avoid using end-of-life products.
- Enable multi-factor authentication to protect network and system accounts.
- Refer to HKCERT’s Incident Response Guidelines for SMEs to establish and review security incident response plan.
- Refer to the concept of zero trust and network segmentation to reduce the attack surface and the scope of affected network.
- Back up all critical data, at least one local backup and one remote backup.
- Encrypt all sensitive data.
Also, as the incident involves leakage of personal data, HKCERT believes that the data will be or has already been used for phishing attacks and scam incidents. The public is advised to pay extra attention to suspicious emails and calls. HKCERT also reminds enterprises and users:
- To pay attention to the spelling of the URL, carefully check for errors or suspicious elements, and verify the authenticity of the website.
- Not to assume that websites using the HTTPS protocol must be authentic and credible websites, and phishing websites can also use the HTTPS protocol.
- Not to open any links or attachments at will and think twice before providing personal information.
- To confirm the identity of the sender and the content before opening attachments and links in emails or instant messages;
- To regularly update the login password and enable multi-factor authentication for each account.
In addition, if the public has doubts about the phone number, email address, website URL and IP address, they can use the “Scameter” (https://cyberdefender.hk/en-us/scameter/) by CyberDefender to check whether they are frauds/online pitfalls or not.
For more details, please refer to:
https://www.hkcert.org/blog/always-keep-system-security-up-to-date-to-prevent-customer-data-from-becoming-phishing-feeds
Analysis Report: Analysing AgentTesla Spyware

According to Israeli cyber security solution provider Check Point’s “Global Threat Impact Index” monthly report published in early November, it was reported that AgentTesla continued to be one of the “Most Wanted Malwares” in the world, affecting over 7% of enterprises. In this regard, HKCERT collected a sample of AgentTesla to analyse its attack vector and operations. Security advice is also offered to help the public to protect against the threat.
What is AgentTesla?First appeared in 2014, AgentTesla is a spyware developed using .Net framework and designed for stealing user credentials. Hackers use this malware to spy on victims, intercept all user inputs in programs and browsers, and then transmit the information stolen to the Command-and-Control Server. |
Investigate the Malicious Email Attachment
Hackers usually send phishing emails to lure victims to download and execute the malware. In the collected sample, hackers used an email attachment named "PRE SHIPPING NOTICE.zip" to try to guide victims to download and open it.
After downloading and opening the “PRE SHIPPING NOTICE.zip” file, a file named “PRE SHIPPING NOTICE.exe” was extracted.
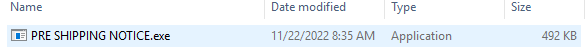
To check on VirusTotal website, a SHA256 hash value of the file is required. The PowerShell cmdlet Get-FileHash was executed to get the hash value of “PRE SHIPPING NOTICE.exe” which was uploaded to the VirusTotal.
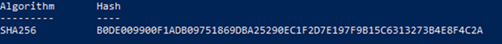
In the VirusTotal search result, 51 cyber security companies can identify the file as malware and AgentTesla.
# Search conducted on 24 November 2022
Analysing “PRE SHIPPING NOTICE.exe”
It is determined the file “PRE SHIPPING NOTICE.exe” is an executable file developed by VB.NET. Also, it is noted that no software packing technique is applied to the file.
What is Software Packing?
Software packing is a method of compressing or encrypting an executable. Packing an executable will change the file signature in an attempt to avoid signature-based detection.
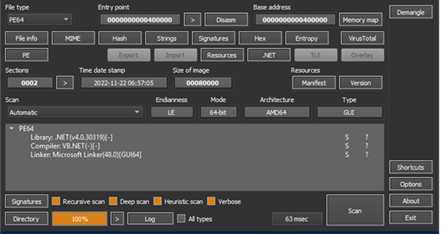
Once the programming language used was determined, reverse engineering technique was applied to get the code of “PRE SHIPPING NOTICE.exe”. A part of the code of “PRE SHIPPING NOTICE.exe” has shown that AgentTesla is using Windows ntdll.dll to inject the payload.
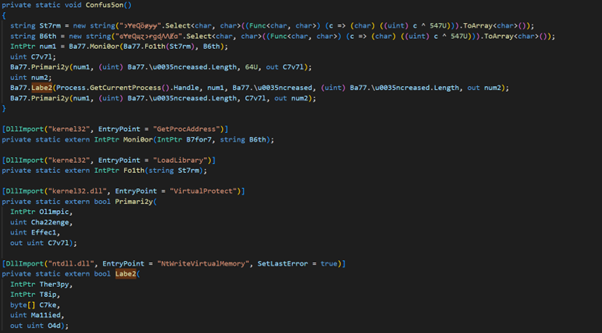
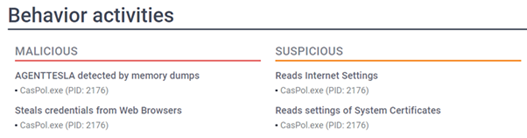
After the payload had been executed, the behaviour detection of AgentTesla on the victim computer showed that it will steal the computer setting, credentials of system and browsers.
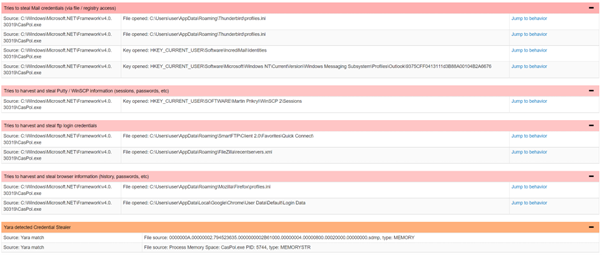
Further deep dive into the stolen data using YARA malware research and detection tool found that it included mail profile setting (e.g. thunderbird, incredimail, MS Outlook), remote server credentials (e.g. WinSCP, FileZilla) and the login password stored in browsers (e.g. Firefox, Chrome)
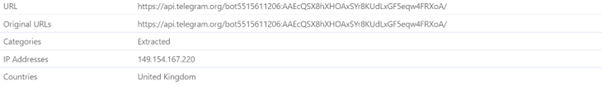
AgentTesla would transfer the stolen data via Telegram API to the hacker’s Telegram account.
Security Advice
Malicious email is one of the spreading channels of AgentTesla. Moreover, different variants of AgentTesla have already appeared on the Internet. Hence, HKCERT recommends users to:
- Always keep the system, software, and antivirus software up to date
- Do not open unknown files, web pages and emails
- Confirm the legitimacy of sender and the content of the email before opening the attachments and links in the email,
- Check the file extension to avoid being misled by the file name. Do not open any executable file or Microsoft Office files with macros obtained from unknown source.
- Executable file extension: .exe, .vbs, .js, .bat, msi, .ps, psc1, .cmd, .wsf, .jar, .reg, etc.
- Microsoft Office files with macros can be contained in all kinds of Office files (e.g. .doc/.docm, .xls/.xlsm, .ppt/.pptm). Users are advised to disable all macros from auto-run in the security settings.
- Use password management tools to manage the passwords instead of storing them on browsers.
- Use lower privileged accounts for daily use instead of system administrator accounts.
- Set up "multi-factor authentication" (MFA) to enhance the account security.
For more details, please refer to:
https://www.hkcert.org/blog/analysing-agenttesla-spyware
-End-
Download Report
< Please click to download Hong Kong Security Watch Report>
Related Tags
Share with
