Hong Kong Security Watch Report (Q4 2013)
HKCERT is pleased to bring to you the First "Hong Kong Security Watch Report". After this official launch, we will continue to publish this report on a quarterly basis.
Nowadays, a lot of “invisible” compromised computers are controlled by attackers with the owner being unaware. The data on these computers may be mined and exposed everyday and the computers may be utilized in different kinds of abuse and criminal activities.
The Hong Kong Security Watch Report aims to provide the public a better “visibility” of the situation of the compromised computers in Hong Kong so that they can make better decision in protecting their information security.
The report provides data about the activities of compromised computers in Hong Kong which suffer from, or participate in various forms of cyber attacks, including web defacement, phishing, malware hosting, botnet command and control centres (C&C) and bots. Computers in Hong Kong is defined as those whose network geolocation is Hong Kong, or the top level domain of their host name is “.hk” or “.香港”.
Highlight of Report
This report is for Quarter 4 of 2013.
In this period, there were 12,536 unique security events related to Hong Kong used for analysis in this report. The information is collected with IFAS1 from 19 sources of information2. They are not from the incident reports received by HKCERT.
Server related security events
Server related security events include malware hosting, phishing and defacement. Their trend and distribution is summarized below:
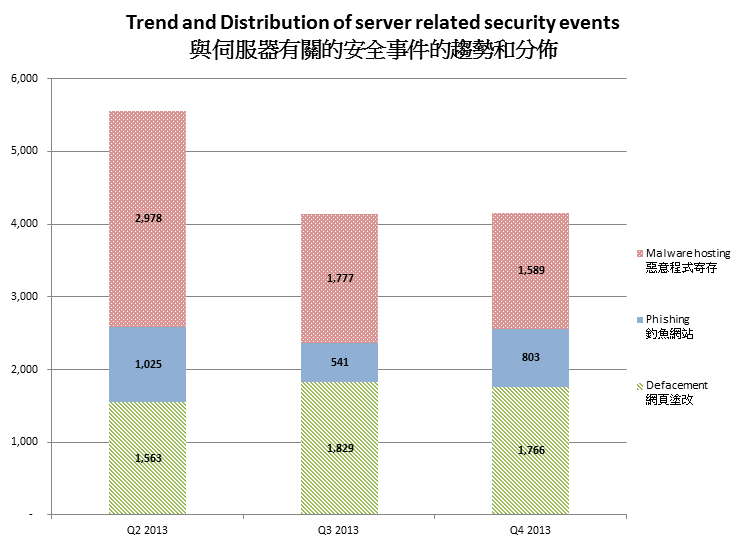
Figure 1 –Trend and distribution of server related security events distributions
The number of server related security events has been dropped since Q3 2013, and kept steady thru Q4 2013.
The number of malware hosting security events had a clear dropping trend across three consecutive quarters. The number of defacement security events held steady in this quarter while it was still slightly higher than that of Q2 2013. The number of phishing security events had grown significantly in this quarter by 48%. The number of phishing security events bloomed in Nov and Dec of Q4 2013 (Figure 2). It might be related to the holiday season which the cybercriminal took advantage to launch phishing campaigns to steal the consumers’ accounts and credentials.
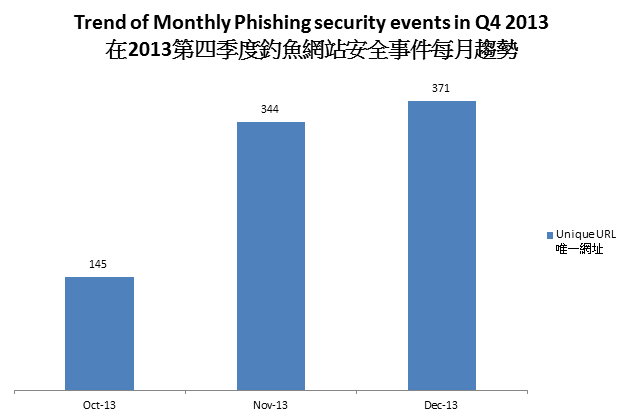
Figure 2 Trend of Monthly Phishing security events in Q4 2013
From HKCERT’s experience in handling server related incidents, in about 50% of the reports, the server or application owners did not have good web application or server management. That opened opportunity for cybercriminals to take advantage of, resulting in their servers becoming launchpads of cyber crimes.
| HKCERT urges system and application administrators to protect the servers. |
|
Botnet related security events
Botnet related security events can be classified into two categories:
- Botnet Command and Control Centres (C&C) security events – involving small number of powerful computers, mostly servers, which give commands to bots
- Bots security events – involving large number of computers, mostly home computers, which receive commands from C&C.
Botnet Command and Control Servers
The trend of botnet C&C security events is summarized below:
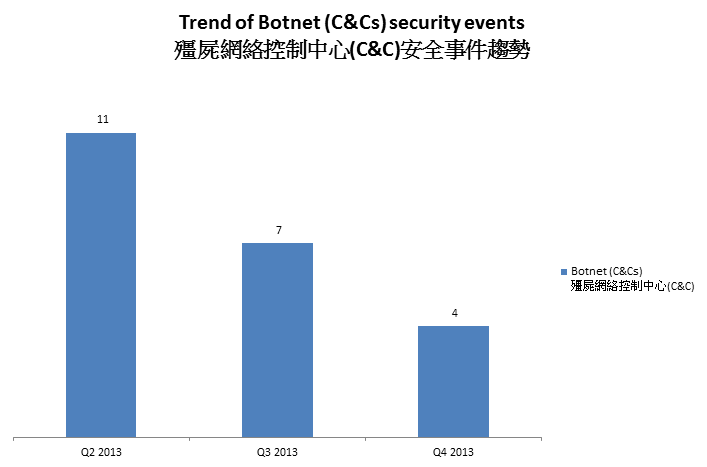
Figure 3 –Trend of Botnet (C&Cs) related security events
Number of botnet Command and Control Servers was decreasing across the three quarters.
There were 4 C&C servers reported in this quarter. Two of the reported servers were identified as Zeus C&C servers, while 2 others were IRC bot C&C servers.
The trend of botnet (bots) security events is summarized below:
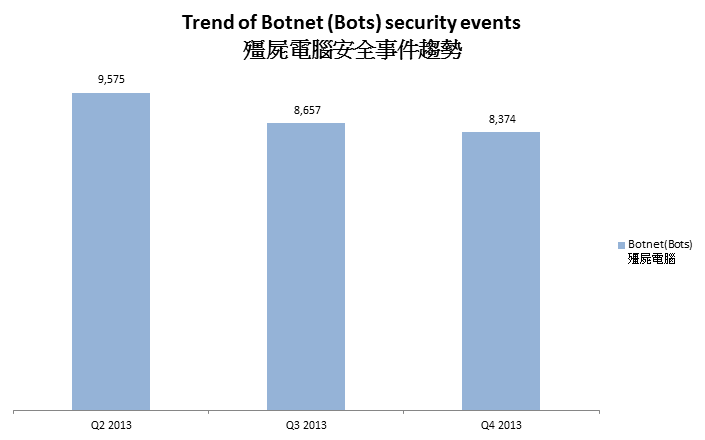
Figure 4 - Trend of Botnet (Bots) security events
Number of Botnet (bots) on Hong Kong network was decreasing across 3 quarters.
In Q4 2013, Conficker continues to be the largest botnet. The maximum number of Conficker machines online on a day in Q4 2013 was 3,175.It has to be noted that Conficker has been around since 2008 and it keeps a high infection rate till now. Some of the reasons are that users are using an unpatched or an unlicensed Windows system that has no security update, and without a working copy of security software. Other studies revealed that the biggest attack vector is credential based attack, then exploit of system vulnerability and autorun3 . According to the Security Intelligence Report (SIR), credential based attacks accounted for 54% to 89%; exploit of system vulnerability accounted for 19% to 43%, and attack via autorun accounted for 1% to 11%. Conficker is designed with a small dictionary to perform bruteforce attack to crack the admin password to propagate on the network.
| HKCERT urges users to protect computers so as not to become part of the botnets. |
|
| Users can use the HKCERT guideline to detect and clean up botnets |
|
Download Report
< Please click to download Hong Kong Security Report >
1Information Feed Analysis System (IFAS) is a HKCERT developed system that collects global security intelligence relating to Hong Kong for analysis.
2 Refer to Appendix 1 for the Sources of Information
3 According to Microsoft Security Intelligence Report (SIR), Volume 12, published on December 2011, credential-based attack account for 54% to 89% while exploit system vulnerability account for 19% to 43%, and attack via auto-run account for 1%-11%. (http://www.microsoft.com/security/sir/archive/default.aspx)
4 How to disable the Autorun functionality in Windows, Microsoft, Knowledge Base http://support.microsoft.com/kb/967715
Share with


