Document Malware Defense Guideline
What is Document Malware?
Everyone should familiar with the term “Malware”; however, many people may not know how malware works. “Malware” is a general terminology and can be classified based on its operating mechanism. Most common malwares are Trojan, Worm and Botnets.
Basically, malware can infest computer by the following two ways:
- Users execute malware
- Users directly execute a malware file.
- Auto execute malware file while plug in the USB flash drive to computer.
- Auto execute malware file via the vulnerabilities of browser or operating system.
- Users open files containing malware (i.e. Document Malware).
In this article, we will focus on Document Malware - user open a non-executable files with containing malware. Document Malware is designed to exploit the vulnerabilities of application program. When user opens the document file which embedded with malicious code with a non-patched application program, the malicious code will silently install malware and take control on the system.
Which types of file could be affected by Document Malware?
Any types of file can possibly be used to create Document Malware. The key is applications which are used to open the files contain vulnerabilities. The file types associated with Microsoft Word, Excel, PowerPoint and Acrobat PDF Reader are the most commonly used by Document Malware. Multimedia files types such as wmv, mp3, mp4 and wav are also possible to be used by Document Malware.
What are the risks of Document Malware?
Many users are unaware of the document files which are used for works, studies and entertains may be infected by Document Malware. They just directly open it without checking. You may receive a file which contains Document Malware from your friend through email or instant messenger when his computer was compromised. If you open the file without examining it, your computer may also be compromised, and the malware will spread across your office’s network through the internal network. Malicious attacks using Document Malware usually target popular applications. The attackers are closely monitoring the application vulnerabilities. Once they find the related fix or patches are not released, they would actively initiate attacks in order to gain a higher chance in succeeding the attacks.
Preventive measures against Document Malware
Do not open Suspicious files
When receiving emails with attachments, ensure whether you know the sender and the content of the email is normal. Some emails with brief content (e.g. funny document) or emails with only attachments are suspicious. The emails may possibly send by compromised computers which malicious people intent to compromise email receivers’ computer by tricking them to open the attached files. Even if the content of the email seems normal, do not open the attached files directly. Save the attached files first, and then scan the file with file scanning tools of security software (eg: antivirus software) before opening it with appropriate applications.
Be cautious when using external USB flash drive
Whenever you insert your external USB flash drive to your computer or open any file from the external USB flash drive, make sure to use file scanning tool of security software to scan all the files stored.
Keep the systems, security applications, and application programs up-to-date
Do not stop auto update function of the system and application program and visits our website for up to date security news and alerts. Be careful of the application programs that found to be vulnerable to zero-day exploit. If there is no patch or fixed version for that vulnerable application program, use alternative application program to open the files temporary.
Use alternative application programs to avoid common attacks
For example, using OpenOffice instead of Microsoft Office; Using Foxit Reader instead of Adobe Reader to open PDF files. However, keep in mind that, by installing more application programs, managing more security updates will be required.
Enable the security setting on the application programs
In order to provide better services and enhance effectiveness, many applications allow program code to be executed in within files; however, it is risky as it also allows malicious users to exploit the application vulnerabilities via the embedded program code. Disable the code execution option in applications if you do not need to run the embedded program in documents.
In the section below, we would demonstrate how to disable the program code execution in some common applications, Microsoft Office and Adobe Reader, to further strengthen the security of your system.
Preventive settings against document malware for Microsoft Office
You should always install the latest patches for Microsoft Office to fix the found vulnerabilities.
You may amend the following settings to attain a higher level of security:
- For Microsoft Office Word 2003, Macro Settings could be set as follow:
- Click “Tool” -> “Macro” -> “Security”
- Select the setting to “High”
- For Microsoft Office Word 2007/2010,Macro Settings is located in Trust Center:
- Click “Microsoft Office” or click “File”, “ Options”
- Click “Trust Centre”, click “Trust Centre Settings”, and then click “Macro Settings”
Under Macros Settings, select “Disable all macros with notification”
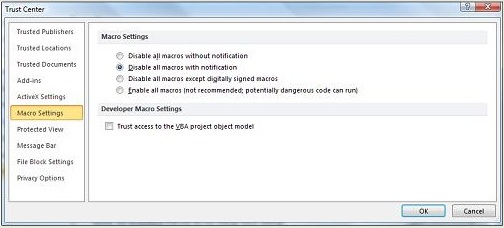
Microsoft Office 2010 new security functions
Microsoft Office 2010 added multiple security functions, for details you may visit the link as follow:
http://www.microsoft.com/security/pc-security/office2010.aspx
A summary of the security features are list as follow:
- When opening a file contains active content (ActiveX controls, Macro, data connection, Add-ins and Spreadsheet links), Office 2010 displays a warning, and let user decide whether the source is trustworthy.
- When reading a document, Office 2010 provides “Protected View”. Most of the features are disabled to minimize the security risk under this mode.
- When a program attempts to execute code within the memory space dedicated for data storage, Office 2010 stops the execution by Data Execute Prevention (DEP).
- Office 2010 provides a convenient interface to manage security and privacy settings.
Preventive settings against document malware for Adobe Reader
You should always update the Adobe Reader to the latest version.
You may strengthen the security setting of Adobe Reader by the following settings:
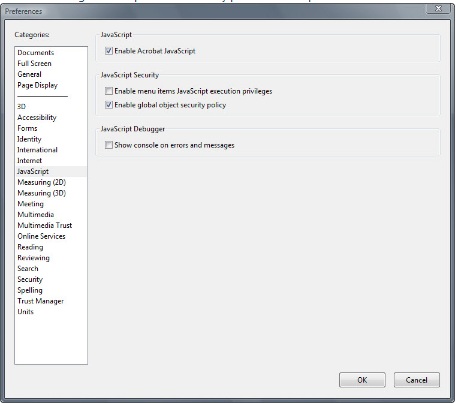
Disable “JavaScript” and “Allow using external application to open non PDF file”
- Click “Edit”, “Preferences”
- In “Categories”, click “JavaScript”
Under “JavaScript”, uncheck “Enable Acrobat JavaScript”
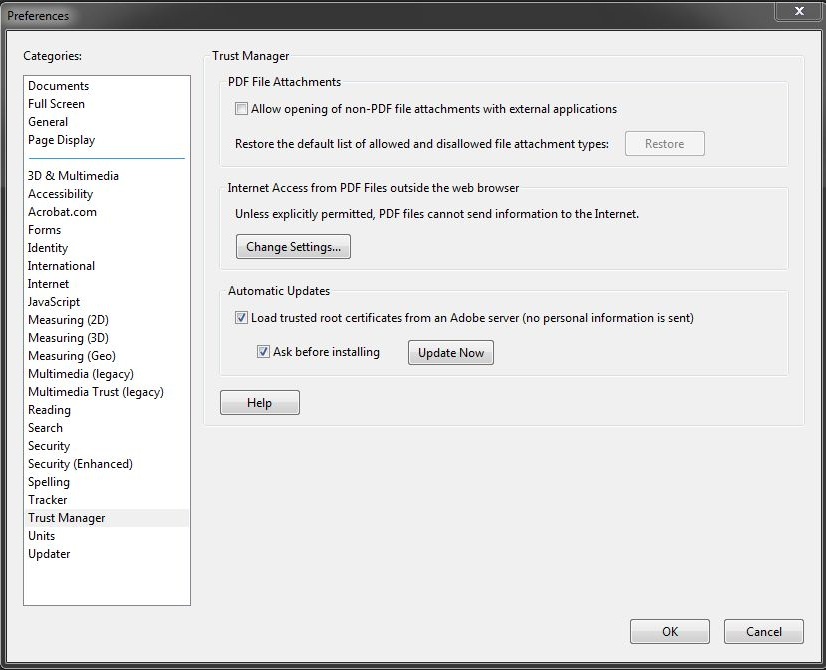
- In Categories, click “Trust Manager”
Under “PDF File Attachments”, uncheck “Allow opening of non-PDF file attachment with external applications”
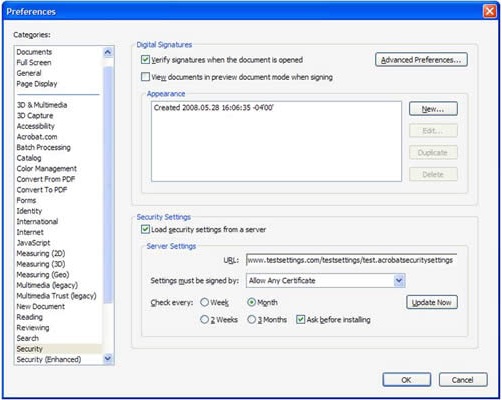
Enable “Verify signatures when document is opened” and “Enable Enhanced Security” option is enabled
- Click “Edit” -> “Preferences”
- In Categories, click “Security”
Under “Digital Signature”, ensure “Verify signatures when the document is opened” is checked.
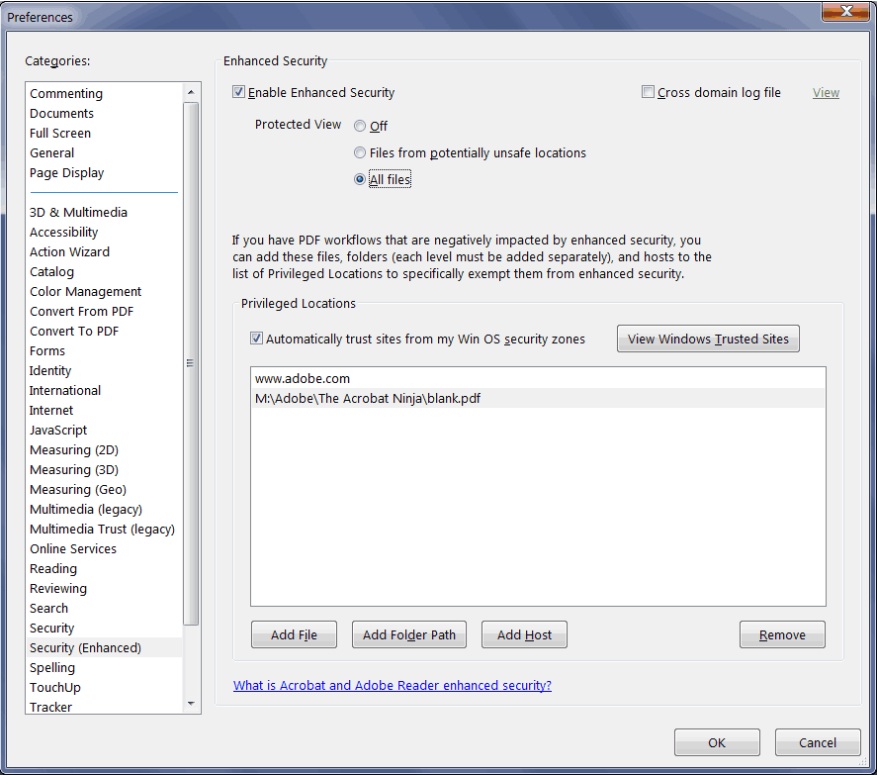
- In Categories, click “Security (Enhanced)”
Under “Enhanced Security”, ensure “Enable Enhanced Security” is checked.
Security setting in Microsoft Window Media Player
Follow the steps below to configure the setting to stop all executable code, and display warning when enhanced content is played:
Click “Tool” -> “Options”, and then click “Security” Tab
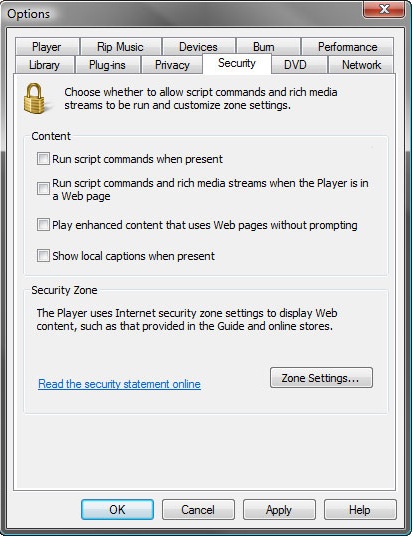
Uncheck the setting for the following (By default, it is all unchecked)
- Run script commands when present
- Run script commands and rich media streams if the Player is in a Web page
- Play enhanced content that uses Web pages without prompting
For details on how configuration settings affect security in Window Media Player, you may refer to the article:
Share with
