Be aware of ransomware targeting NoSQL Databases
Be aware of ransomware targeting NoSQL Databases

HKCERT was aware that a rising trend of ransomware attack targeting publicly accessible NoSQL Databases in Jan 2017. To minimize the potential security risk, user should take proactive actions for these online Databases.
What happened?
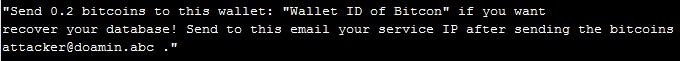
Recently a cyber-attack is targeting online NoSQL Databases with loose access control. An attacker can exploit this vulnerability to perform arbitrary operations on these Databases as a privileged user, without authentication. He/she will clone the whole Database and then remove or destroy all data from it. Then he/she will demand ransom from the victim in Bitcoins.
Is my Database affected?
Any Databases without adequate security control may have potential risks on ransomware infection. HKCERT urges Databases administrators to pay attention to their system security. List of known affected NoSQL Databases:
MongoDB, Redis, ElasticSearch, Hadoop, Cassandra and CouchDB.[1,2]
Impacts
Victim may:
- Lose access to data stored on the Database system.
- Be extorted by attacker to pay ransom to get back access of data.
- Have sensitive information leakage.
A sample ransom message [3]
Advisory
To minimize the risk of this attack, make sure you have done these basic protections for your Database:
- Configure network access control for your Database to block any unnecessary network exposure for the system. If there is no need to be accessed publicly, place it inside a closed LAN; otherwise, it should be protected by firewall.
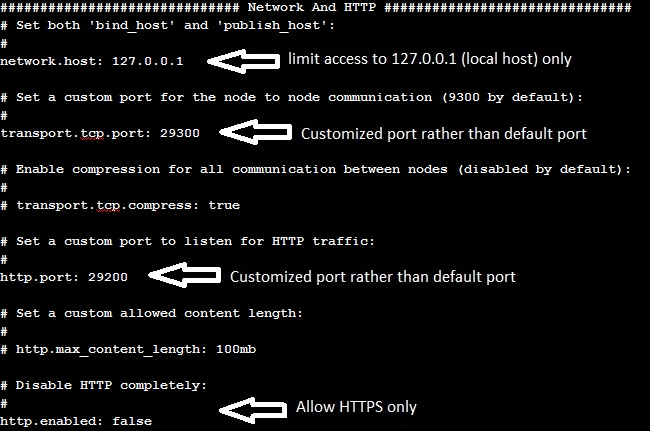
- Consider to harden your system configuration by using customized service port (not using default port 9300 in Elasticsearch for example). You may perform a network security scanning on your Database to verify its effectiveness.
- Change default security configuration of your Database from access granted to everyone to only authorized authenticated users. You may consider implementing Role-Based Access Control and granular control to better manage the permission of each Database user, for example the Role “general user” can only “read” the “client” Database, while the Role “privileged user” can “read” and “write” the “client” Database. [4]
- Upgrade the Database to the latest stable version.
- Operate a comprehensive data backup plan (with an offline copy) and business continuity plan.
Note: Please refer to your product documents for detailed guidance.
The screen capture below is a reference hardening configuration in Elasticsearch:
Reference
[1] The compendium of database ransomware
https://blog.binaryedge.io/2017/01/18/the-compendium-of-database-ransomware/
[2] Database Ransom Attacks Hit CouchDB and Hadoop Servers
[3] Now attacker turns to ElasticSearch
[4] Role-Based Access Control in NoSQL
http://www.dummies.com/programming/big-data/role-based-access-control-in-nosql/
Protecting Against Attacks that Hold Your Data for Ransom
https://www.elastic.co/blog/protecting-against-attacks-that-hold-your-data-for-ransom
Security Checklist — MongoDB Manual 3.4
https://docs.mongodb.com/manual/administration/security-checklist/
Ransomware groups have deleted over 10,000 MongoDB databases
Share with
