Beware of Scam Email Impersonating HKCERT with Malware Attachment
HKCERT received an incident report related to a scam email on 25 Jan 2013. The scam email utilized our alert email sent to public about some extremely critical vulnerability such as monthly Microsoft patch or previously wildly exploited Adobe Flash Player vulnerability.
The content of the scam email is in Chinese, and urged the recipient to install the so called "Adobe Flash Player patch" attached in the email. The file is already verified as a malware by our analysis.
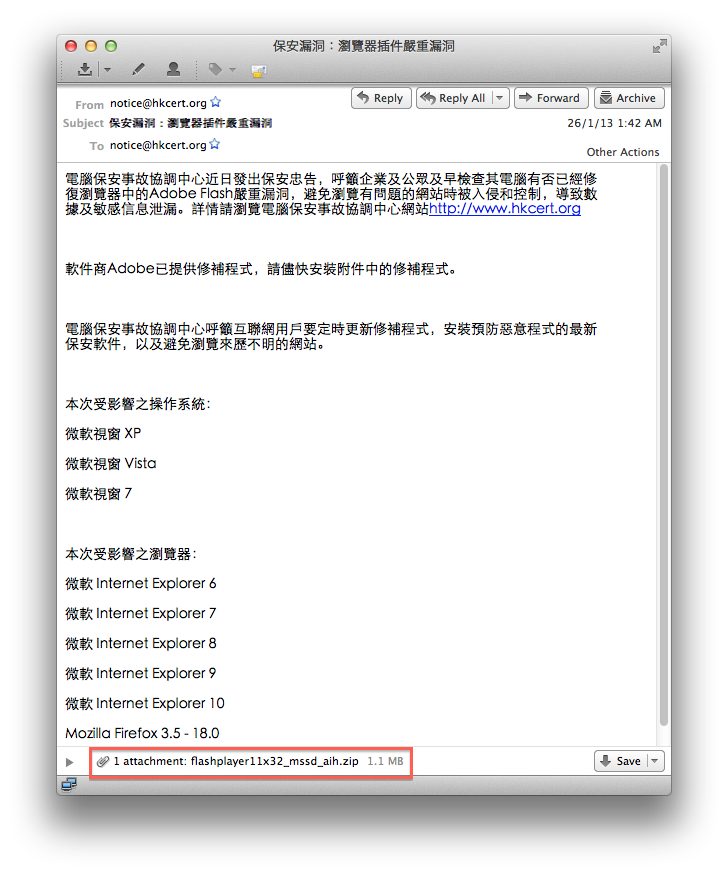
Please note:
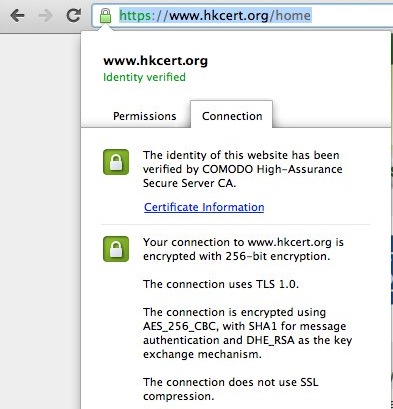
- HKCERT does not attach any patch or executable file in any alert email. In our alert email, we will only provide link to HKCERT website for security bulletin. HKCERT website is protected by SSL. You can verify the digital certificate by double clicking the "pad lock" beside URL:
- HKCERT have never sent our alert email on behalf of "[email protected]" (as showed in the image above). Our official email address is [email protected].
- Our alert email is PGP signed. You can find our PGP key in the following webpage:
https://www.hkcert.org/pgp-key - Do not open any file attached in this email.
Please report to HKCERT at tel: (852) 8105 6060 or email: [email protected] if you come across or are infected by the malware from the scam email.
Share with
