"Transaction Security of Mobile Apps in Hong Kong" Study Report
In the mid-September, the Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) and the Professional Information Security Association (PISA) published a study on “Transaction Security of Mobile Apps in Hong Kong”. In this study, 130 Hong Kong online transaction service apps commonly used locally were tested. Over one-third of them lack adequate encryption security in processing credential or transaction data, and are vulnerable to man-in-the-middle (MITM) attackers, that makes transmitting data leakage.
The objective of the study is trying to identify vulnerability in the implementation of SSL (Secure Sockets Layer) in commonly-used mobile apps in Hong Kong; and raise the awareness of the public, apps owners and developers on the SSL issue of mobile apps.
Our scope of testing is set to the Hong Kong apps which provide online transaction. They would handle personal information, credential and password, or payment information. The mobile apps were downloaded from the official iOS App Store and Android Google Play Store between April and July this year. After our pilot test, total 130 mobile apps which are running HTTP or HTTPS transfer protocol are collected. They are 64 Android apps and 66 iOS apps; and they are classified into the following 7 categories:
● Mobile Banking (32 Apps)
● Cinema Ticketing (26 Apps)
● Financial Securities (24 Apps)
● Online Shopping / Group Buy (16 Apps)
● Travel Booking Service (13 Apps)
● Online Food Ordering (11 Apps)
● Digital Wallet / Payment Service (8 Apps)
There are 4 areas to be studied:
● Does the app use SSL connection
● If it uses SSL, does the app handle invalid SSL connection correctly
● Does the app apply advanced MITM resistant protection (e.g. Certificate Pinning)
● Does the app encode/encrypt sensitive data on application layer
The testing environment simulates MITM attack between mobile client and the server through a proxy. See the below figure.
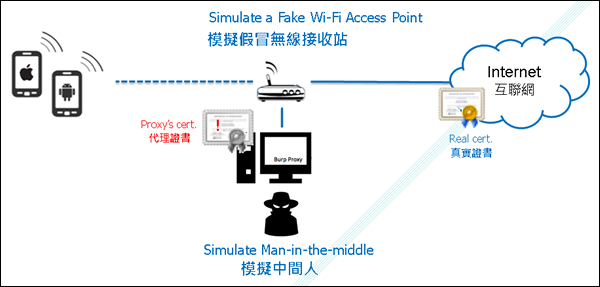
During the test, each app is rated according to the following grading scheme.
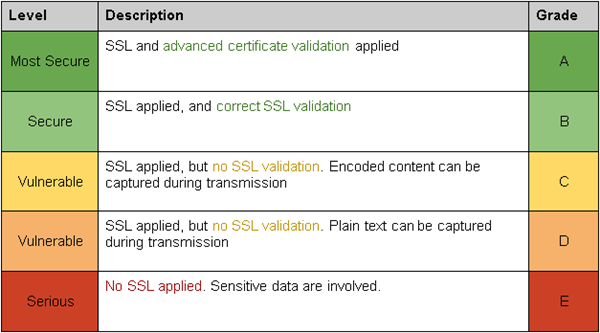
The following is the statistic result after the test.
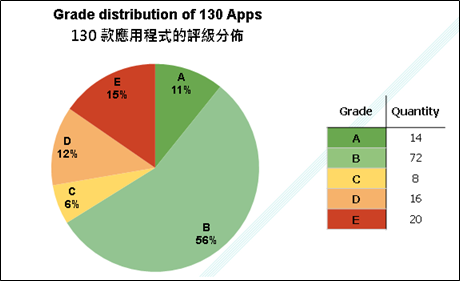
The Study found that 34% of the mobile apps tested did not apply SSL or validate the digital certificate used in encryption. Analysis into the seven types of services offered by these apps revealed that digital wallet/payment service and mobile banking apps feature better encryption security, with over 87% attaining “secure” and “most secure” grading. The transaction security of cinema ticketing and online food ordering apps was in the medium level. Over half of the financial securities, online shopping/group buy and travel booking service apps tested were found to be “vulnerable”, or even “serious”, with no encryption at all.
For the detail, please refer to "Transaction Security of Mobile Apps in Hong Kong" Study Report
[Download]
Hong Kong Computer Emergency Response Team (HKCERT) and Professional Information Security Association (PISA) have compiled the “Best Practice Guide (SSL Implementation) for Mobile App Development” to help apps owners and developers to improve apps security. This document mentions common practices which help mobile application developers to handle SSL connection with appropriate ways to provide secure channel between mobile app and server and also prevent from MITM attack.
Best Practice Guide (SSL Implementation) for Mobile App Development
[Download]
Share with


