"Tailor-made 1-time" PayPal Phishing Link
To make a phishing site live longer, cybercriminals use various tactics to avoid exposing the site to investigators, e.g. a phishing site hosted in Hong Kong but targeting German users can only be viewed from Germany, so that the investigators in Hong Kong cannot verify the site at first sight.
In Q1 2014, HKCERT handled a "tailor-made 1-time" PayPal phishing incident, in which the cybercriminals used a more sophisticated method to escape the investigation. For quite some time, from our monitoring and incident reports, we saw the following phishing URL:
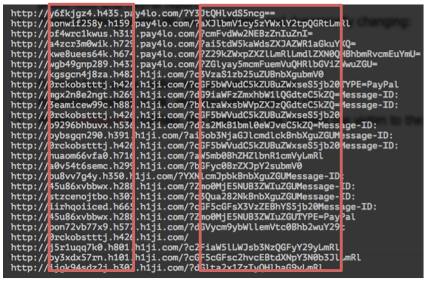
When opening the URL in a browser, it was redirected to Google search result page. No phishing content was displayed.
You can see the links have a similar pattern: http://somedomain/?xxxxx, where "xxxxx" looks like some encoded text. Then we threw the "xxxxx" into some decoder, it turned out to be a base64 encoded email address:
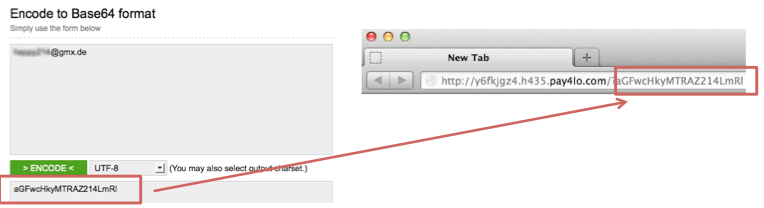
With this new clue, we thought the phishing content might only be displayed when clicking the link from an email message by target recipient. Actually we found that the phishing link could be accessed once with arbitrary email address.
Summary of the trick
- The phishing link contained encoded email address targeting the recipient. When the recipient clicked the link the first time, the phishing page was displayed.
- If such phishing link was accessed the second time, mostly likely by investigators, the phishing link redirected to Google webpage, so no phishing evidence could be gathered.
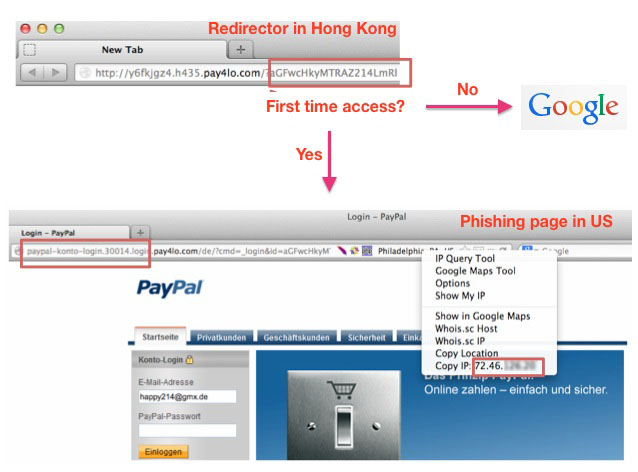
Sophisticated architecture
Further to this trick, we also found that the whole phishing campaign had a quite sophisticated architecture:
- "Redirector" part (Hong Kong):
- Check whether the recipient came from Germany.
- Generate "1-time" phishing link by checking whether the email address was used before.
- The recipient who clicked the link was redirected to a US server hosting the phishing content.
- This part was hosted in several servers located in Hong Kong.
- Phishing page rendering (US):
- Before phishing content was displayed, a "1-time" subdomain for the phishing webpage URL was generated dynamically. Phishing content was displayed under this subdomain.
- This part was hosted in the US.
HKCERT follow-up
We found that at least 3 domains (fij1.com, h1ji.com, pay4lo.com) were registered for the campaign. They were all registered in Russia with different email addresses. We referred the incident and provided our finding to Hong Kong Police for their investigation. Currently the said URL and servers in Hong Kong and US cannot be accessed, and we have not detected any similar links since Q1 2014.
Share with
