Response to attacks targeting to 0-day vulnerability of web browsers
 Web browser is our essential software in daily Internet browsing. Exploiting web browser vulnerability is one of the most commonly used methods by cyber criminals. Security vulnerabilities have been identified in some mainstream web browser, such as Microsoft Internet Explorer, Mozilla Firefox, Google Chrome and Apple Safari before the release of security patch or updated version by software vendors. It is a high risk period used to carry out the exploit.
Web browser is our essential software in daily Internet browsing. Exploiting web browser vulnerability is one of the most commonly used methods by cyber criminals. Security vulnerabilities have been identified in some mainstream web browser, such as Microsoft Internet Explorer, Mozilla Firefox, Google Chrome and Apple Safari before the release of security patch or updated version by software vendors. It is a high risk period used to carry out the exploit.
How to protect your computer under web browser 0-day vulnerability attack?
Although we cannot predict the occurrence of attacks target to 0-day vulnerability of web browser, we can do some security measures to help us to continue internet browsing under a safety environment:

- Use other web browser software
We recommend users to install an additional trusted web browser software for replacement and make sure security update are applied.
- Upgrade to the latest version of web browser
If your operating system supports, a new version of the browser will not only avoid the vulnerability, but can also provide additional security features in general, such as sandbox and malicious website blocking.
- Use security tool to protect from attacks temporarily
Microsoft Enhanced Mitigation Experience Toolkit (EMET), for example, is a free security tool to provide an in-box mitigation to help to prevent the applications being exploited.
You can download EMET security tool version 3.0 from the website below:
http://blogs.technet.com/b/srd/archive/2012/05/15/introducing-emet-v3.aspx
After installation, configure to add the application which need to be protected, such as Internet Explorer.
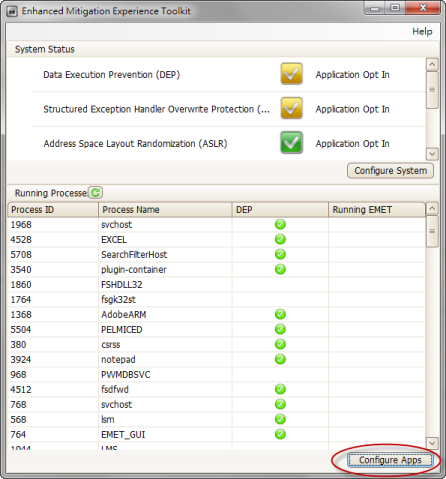
1. Click "Configure Apps".
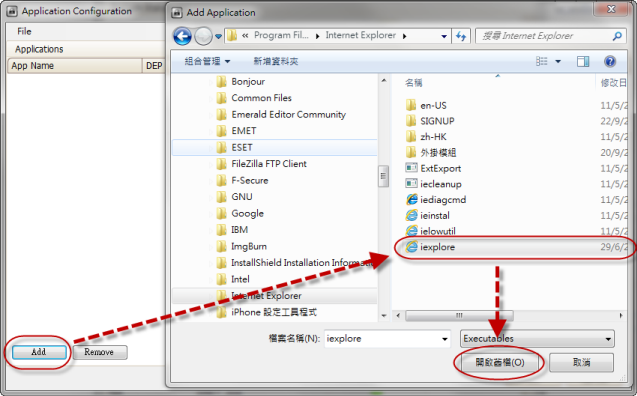
2. Click "Add", select the executable file (explorer.exe) of Internet Explorer, Click "Open File" to add.
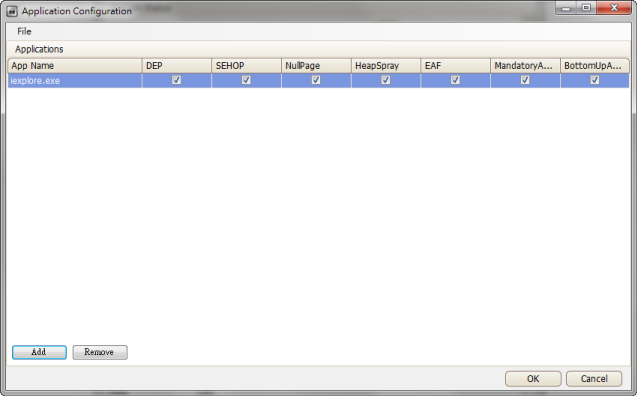
3. Click "OK" to finish.
- Disable or remove unused plugins, e.g. Java, Adobe flash player etc.
- Disable HTML browsing feature in email client software.
- Do not open the website links from untrusted source.
- Install security software and keep it updated.
Internet Explorer 0-day vulnerability exploits
Recently, a new Microsoft Internet Explorer 0-day (No patches) vulnerability (CVE-2012-4969) was found to affect the Microsoft Windows using Internet Explorer versions 6 to 9. The exploit code for this vulnerability has been widely available. This vulnerability poses a great security threat to the Internet users in Hong Kong because Internet Explorer 8 and 9 are the most popular web browsers used in Hong Kong, according to "statcounter.com". Until Microsoft releases the security update, you can follow the above recommended security measures to protect your computer.
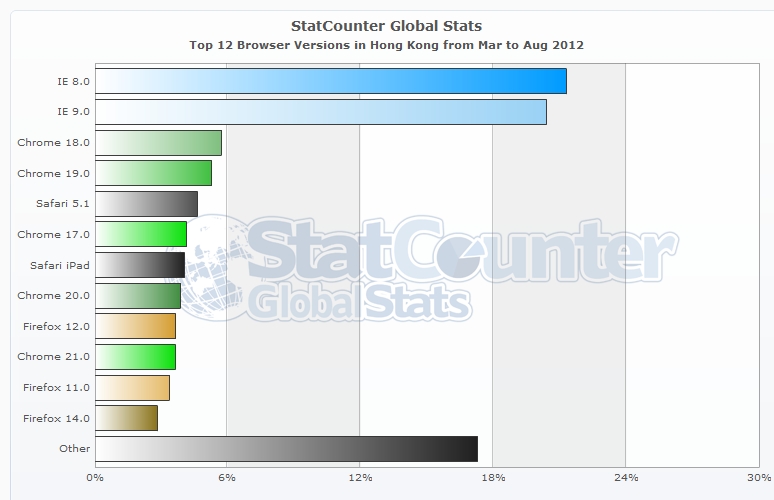
Fig 1: The top web browsers ranking in HK from Mar to Aug 2012 (Source from statcounter.com)
Share with
