Please sign them. Smart contracts?
Smart contract is a program stored in the blockchain. Different from traditional contracts, it does not require third-party intervention. When the contract conditions are met, the program will automatically execute the contract and it cannot be changed
In the past, there were some smart contract-related attacks that involved exploiting the vulnerabilities in smart contracts. Hence, when developing or using smart contracts, users must pay attention to avoid program execution results that are different from expectations, and understand the potential risks involved and the corresponding security recommendations

After introducing NFT storage methods and NFT cyber attacks in earlier articles, we truly believe that our readers now have a basic understanding of blockchain and NFT. In addition to NFT, blockchain can also be applied elsewhere, with smart contract being one of its core technologies. However, what is a smart contract? What is the difference between a smart contract and a traditional contract? How do we apply it? And most importantly, what are the cyber security risks? Next, we will share with you about these.
The origin of smart contracts
The concept of smart contract was first floated in 1994 by Nick Szabo, a scholar who was also a cryptographer and computer scientist. He advocated the digitisation and stylisation of contracts in which the terms and conditions could be digitally embedded in a specific area. However, the concept did not draw significant response until the emergence of blockchain [1].
One top of being a core technology of blockchain, smart contract is also a special protocol. Users can programmatically write contract clauses into the blockchain. When certain conditions of the contract are met, the program will be triggered to execute automatically.
A real-life example is a vending machine. The contract condition of the vending machine is that when a certain amount of money is being slotted into the machine, the program will be triggered to sell a can of soft drink. All operations do not involve third parties and complicated procedures, so the cost is low.
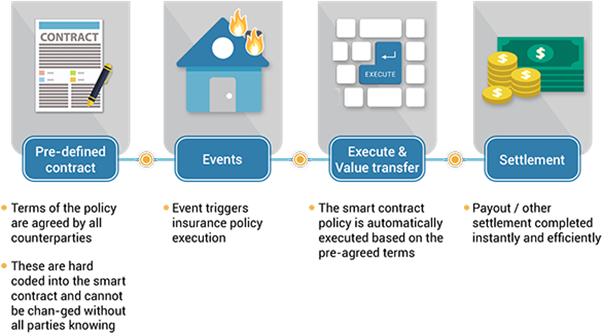
Differences between traditional contracts and smart contracts
In daily life, we often come into contact with traditional contracts. For example, when buying a house, we need to go through procedures such as signing a contact with the real estate agents, bank mortgage approval, and legal services.
Traditional contracts are often based on trust, involving the intervention of a third party as a witness, and then both signed parties perform their contractual obligations. The whole process is complicated and involves additional costs.
The design of smart contracts is to solve the above problems. In addition to saving costs for third parties, it also ensures that the contract content is effectively executed. This is because it is a technology developed not based on mutual trust, but on the content of the contract agreed by both parties.
Since the smart contract is programmed and written into the blockchain, the blockchain has the characteristics that it cannot be tampered with. Also, once the conditions defined by the smart contract are met, the content will be executed immediately and automatically, protecting the interests of both parties and saving time and cost.

Source: https://kustard.io/blog/are-smart-contracts-really-smart/[3]
Therefore, smart contracts have the following characteristics:
Automation
Execute automatically when the conditions are met.
Save time and cost
Reduce the involvement of third parties, thereby reducing the costs involved, such as time costs and third-party expenses.
Reliability
The content is written into the blockchain. Therefore, it is based on the content of the contract, not the trust of both parties.
Commonly used smart contract programming languages
Vyper
Solidity
// SPDX-License-Identifier: GPL-3.0
pragma solidity >= 0.7.0;
contract Coin {
// The keyword "public" makes variables
// accessible from other contracts
address public minter;
mapping (address => uint) public balances;
// Events allow clients to react to specific
// contract changes you declare
event Sent(address from, address to, uint amount);
// Constructor code is only run when the contract
// is created
constructor() {
minter = msg.sender;
}
// Sends an amount of newly created coins to an address
// Can only be called by the contract creator
function mint(address receiver, uint amount) public {
require(msg.sender == minter);
require(amount < 1e60);
balances[receiver] += amount;
}
// Sends an amount of existing coins
// from any caller to an address
function send(address receiver, uint amount) public {
require(amount <= balances[msg.sender], "Insufficient balance.");
balances[msg.sender] -= amount;
balances[receiver] += amount;
emit Sent(msg.sender, receiver, amount);
}
}
Example: Solidity programmed smart contracts: https://ethereum.org/en/developers/docs/smart-contracts/languages/[4]
Past cyber security incidents involving smart contracts
Smart contracts are written in programming language and executed by the Ethereum Virtual Machine. Many security incidents are caused by hackers finding vulnerability in the programs.
In January 2022, a research report by a cyber security company stated that hackers have created fraudulent tokens to lure users into buying[5]. If hackers exploited incorrect settings and code bug in the smart contract, they could subsequently defraud the funds in the smart contract, for example, using the emergencyWithdraw function in the figure below to steal 57 times from the smart contract:
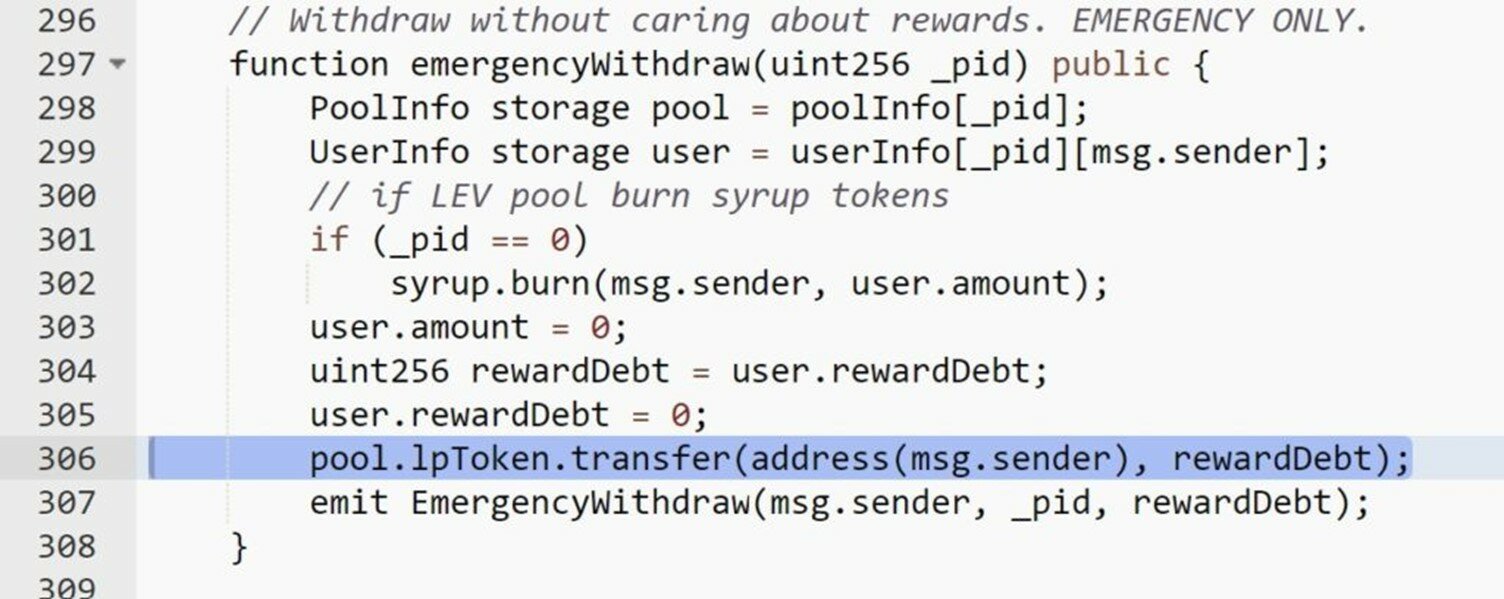
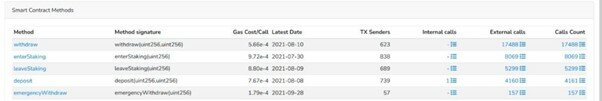
In addition, the report mentions the following four examples of token fraud cases:
When the purchase fee of some tokens reaches 99%, hackers defraud all the funds in the purchase stage;
Some tokens do not allow buyers to resell, only token holders can resell;
When some tokens are sold for 99%, hackers defraud all the funds during the sale stage;
Some tokens allow holders to create more tokens for sale
In June 2016, The DAO was hacked due to a code error during development, resulting in about US$ 50 million of Ether being stolen.
Source:https://www.wired.com/2016/06/50-million-hack-just-showed-dao-human/[6]
Normal contract process
- Ask the DAO contract to withdraw DAO Token
- Transfer the DAO Token to the user
- Update DAO Token extraction record
Exploit process
- Ask the DAO contract to withdraw DAO Token
- Before updating the DAO Token withdrawal record, request to withdraw the DAO Token again
- Keep repeating step 2
- The contract records only one withdrawal record in the end, and loses the withdrawal record during the period
The DAO incident is a “Reentrancy” attack. The following is an example of the attack code, which is similar to The DAO incident.
mapping (address => uint) private userBalances;
function withdrawBalance() public {
uint amountToWithdraw = userBalances[msg.sender];
(bool success, ) = msg.sender.call.value(amountToWithdraw)(""); // At this point, the caller's code is executed, and can call withdrawBalance again
require(success);
userBalances[msg.sender] = 0;
}
"Reentrancy" attack example: https://consensys.github.io/smart-contract-best-practices/attacks/reentrancy/[7]
From the above example, it can be seen that before calling the external code via msg.sender.call.value(amountToWithdraw)(""), userBalances[msg.sender] is not reset to zero first. If the external is a malicious program, it can then call withdrawBalance() repeatedly to transfer assets equal to the value of userBalances[msg.sender].
Also, in November 2021, the multi-chain decentralised exchange MonoX was hacked[8]. The hacker used the bug in the program to make the smart contract increase the value of MONO coin, and then to buy other assets. In the end, MonoX suffered a loss of US $31 million.
Notes on using smart contracts
- When signing a smart contract, review the contract content carefully. If unsure about signing the request, use official channels to contact the platform’s technical support;
- If not too familiar with smart contracts, use the official smart contracts on the trading platform or marketplace for transactions;
- After the transaction, check the crypto asset immediately to ensure the amount of assets transferred is correct and the transaction has been settled in accordance with the smart contract;
- When writing smart contracts, you should refer to the best practice guidelines[9] to avoid common attack methods, such as reentrancy, denial of service attacks, etc.[10];
- Conduct security assessment or auditing against smart contracts to examine the code for security issues. The result could also be shared to users for transparency.
Reference
[1] https://www.fisc.com.tw/Upload/b0499306-1905-4531-888a-2bc4c1ddb391/TC/9005.pdf
[3] https://kustard.io/blog/are-smart-contracts-really-smart/
[4] https://ethereum.org/en/developers/docs/smart-contracts/languages/
[6] https://www.wired.com/2016/06/50-million-hack-just-showed-dao-human/
[7] https://consensys.github.io/smart-contract-best-practices/attacks/reentrancy/
[9] https://consensys.github.io/smart-contract-best-practices/
[10] https://consensys.github.io/smart-contract-best-practices/attacks/
Related Tags
Share with