Lessons learnt from VTech -- Is your website secure?
Hong Kong-based toy maker VTech reportedly encountered data breach in November. More than five million names, email addresses, passwords, and home addresses of parent customers, and around 200,000 first names, genders and birthdays of kids were reported to be exposed.
According to the online magazine Motherboard, the hacker indicated he took advantage of the vulnerability at the VTech's Web applications to compromise the website, and gained “root” privilege and access to the system with full control.
Attacks targeting websites were on the rise locally last year. According to the Hong Kong Security Watch Report 2015 Q3 (Figure 1), over 11,000 Web servers in Hong Kong were found defaced or compromised to host malware and phishing. The statistics were gathered from global security researchers.
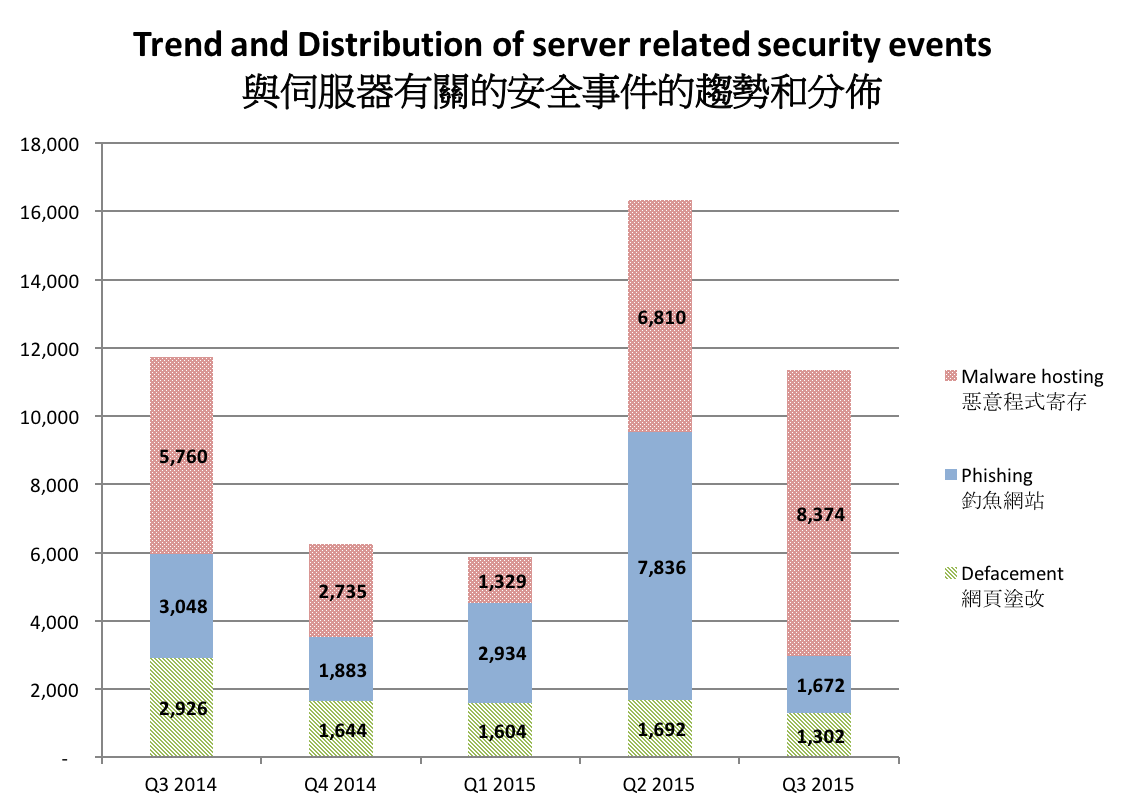
Figure 1. Trend and distribution of server related security events in Hong Kong
Rising risk from Web applications
One major class of the web security attacks is SQL injection. Attacker takes advantage of the loophole of Web application to inject SQL codes—popular database query language—to be executed on Web servers. The injected code is executed using the Web application account. If the Web application is run with a privileged account, the attacker can even take full control of the server, acting just like the administrator entering commands on the server console.
There are many other possible security vulnerabilities on Web servers. The attackers can potentially pick any vulnerable path through the Web application to harm the owners’ business or organization. (Figure 2)
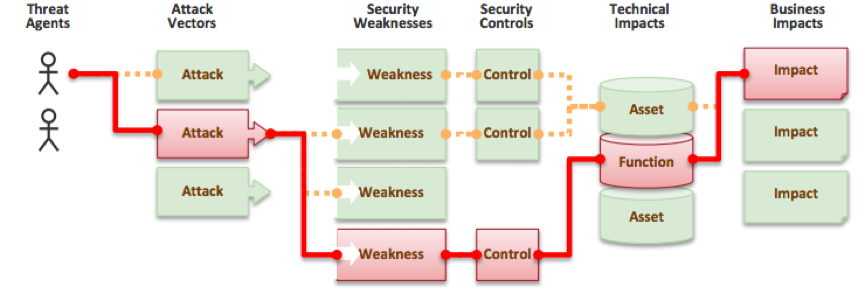
Figure 2. Security risks of web application (Source: OWASP Top 10 - 2013)
The Open Web Application Security Project (OWASP) published the Top 10 application security risks in 2013. These risks warrant your attention. The security loopholes in your websites should be promptly detected and closed. Most Web security scanners can detect the OWASP Top 10 risks and also provide links to patch outdated Web server and application components. Website administrators can use these tools to help secure their websites.
Combating Web injection attacks
The Web server and applications can be hardened in many ways. As a rule of thumb, developers should validate any user supplied input. Besides, we should use a non-privileged account to run them, removing unused application modules and extensions, separating Web and database servers, and restricting access to the Web administration page.
Web application firewalls can be deployed in front of the Web servers to filter attacks and buy time for patching. For critical applications, the website owner should consider more in-depth Web security assessment methods, such as source code scanning and penetration tests.
If your website requires users to input personal data or sensitive data, make sure you use SSL encryption for privacy and confidentiality. Due to technical advancement and the existing vulnerabilities in older and weaker encryption protocols, attackers can use huge computing resources to break weaker encryption protocols. Hence you need more updated security protocols. Old algorithms like RC4, 3DES, MD5, SHA1 should be upgraded to AES and SHA2.
Furthermore, you can easily see if your Web server is employing good SSL encryption via the SSL Server Test, like Qualys. It is a free service that scans your website and grades your Web server from A to F. You can follow the advice in the report to improve the SSL implementation.
To aid small and medium enterprises (SME) in Hong Kong, HKCERT is planning an SME Web Health Check project. Aiming to promote SMEs’ awareness of website security threats and protection, the project will provide SMEs with websites vulnerability scanning and advice on improving security.
These exercises are expected to help SMEs gain better understanding on the importance of Web security and the threats and vulnerability they are facing. Through helping them to mitigate the associated risks, we hope to help them build a more secure business environment in Hong Kong.
Share with
