Keep Everything Up-to-date against Exploit Kit Attacks
An exploit kit (EK) is a type of software system used in downloading and executing malicious codes. When the browser of a victimized computer is redirected to a website where an EK is hosted, it attacks the security vulnerabilities of the browser and related applications (e.g. Microsoft Silverlight, Oracle Java, Adobe Flash, Adobe Reader, etc.) Successful exploitation can stealthily infect the system with malware.
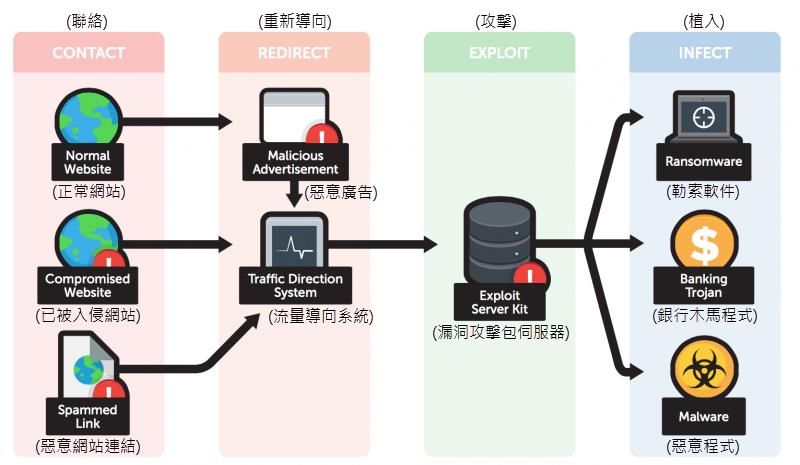
Four stages of a typical exploit kit infection chain
(Source: Trend Micro)
Ranked #8 in Top 10 Botnets according to our Hong Kong Security Watch Report Q4 2015, the trojan Bedep is widely spread through one of the notorious exploit kits – Angler EK. The exploit kit was first seen in end of 2013 and has become one of the common attack tools used by cyber criminals in recent years, due to its strong ability to evade detection and comes with different add-ons for infection. In addition, security researchers have found that two-thirds of the malware carried by Angler EK is ransomware, which earns the criminals 34 million US dollars each year1. Therefore, it is really no joke about the threat of exploit kits.
Exploits kits are developed from the known security vulnerabilities of software and applications. To avoid being one of the victims, users should regularly patch their software and systems. Effective security defense tools such as anti-virus software and intrusion prevention systems are also needed as the frontline protection.
Reference
Share with
