Introduction of QR code attacks and countermeasures

QR code, first used by car manufacturers to trace parts, is now widely applied across different sectors. Not long along, we introduced some basic information and common applications of QR code, as well as their related security threats and advices. In this blog, we would discuss the security risks and recommendations of two use cases, user authentication and data storage, to provide reference for enterprises when using QR code for business operation and system development.
A. User Authentication
Quick Response Code Login
Quick Response Code Login (QRL) is a technology that uses QR codes to authenticate users. Users only need to scan the QR codes displayed on the web applications to log in, instead of entering the usernames and passwords. The simple steps are as follows:
- User accesses the web application and requests for login
- The web application generates a unique QR code for the session. The code may contain a server URL, token and expiry time
- User uses the QR code scanner in the related mobile app to scan the QR code shown on the web application
- The mobile app transmits the token and credential information to the web application
- The web application validates the token and authenticates the user
Advantages of adopting QRL
- Nowadays, online services are becoming more common, and almost each of them needs its users to create a set of account and password, making their management more difficult. In order to properly manage the account passwords, some users will set the same passwords for multiple accounts, but another problem arises as result. If the password of one account is stolen, other accounts may also be affected. QRL can provide a password-free login method as the user only needs to scan the QR code to log in automatically.
- If the password login is stolen, hackers can reuse account information and imitate real user login. For QRL, a one-time QR code will be provided. After each login, the QR code will be refreshed to avoid replay attacks.
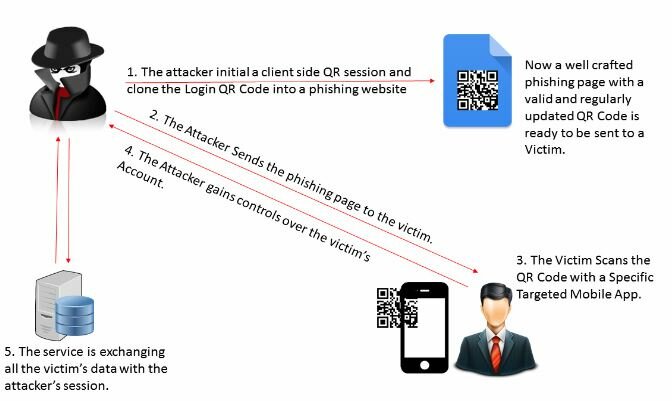
What is QRLJacking?
Quick Response Code Login Jacking (QRLJacking) is an attack that targets QRL. The user scans the QR code provided by the hacker instead of the service provider, enabling the hacker to gain control of the user account.
Source: https://owasp.org/www-community/attacks/Qrljacking
QRLJacking can be divided into 5 simple steps:
- Hackers pretend to be users to obtain legal QR codes from service providers and put them on fake websites
- Send the URLs of fake websites to the victims
- The victims scan the QR codes on the fake websites
- Hackers log in the victims’ accounts
- Hackers gain unauthorised access to all data of the accounts
Impacts of QRLJacking
- Account Hijacking
- When a user, unfortunately, scans the QR code on a fake website, the user's account will be controlled by hackers.
- Information Disclosure
- During the login process, other information may be provided to log in, such as GPS location, mobile phone information, SIM card, etc. Hackers can obtain additional information by QRLJacking.
Protection against QRLJacking
- Session Confirmation
- Service providers can send a notification email/SMS to the user. It could include the login IP address, location or the name of browser for the user to verify.
- Location Based Restriction
- Service providers can compare the location of the mobile device with that of the web application which requests for the QRL (via the location of the IP addresses or location sharing feature of the devices). If they do not match, for example, different countries or regions, the service providers should proceed with additional authentication steps.
- Multi-factor authentication
- After the user scans the QR code, an additional authentication method is required to log in. For example, Sound-based Authentication can be used as the second factor. Sound-based Authentication will generate a recording after scanning the QR code, and the recording needs to be played back to the login page to complete the login. Fake websites require more functions and more permissions on the browser, which greatly hinders the effectiveness of hackers and increases their costs.
B. Data Storage
Given the large storage capability of QR codes and the popular use of mobile devices, merchants would like to use QR codes for promotions and interactions with consumers. For example, they would store their websites, product information, contacts or even company addresses in QR codes for better promotion. Other real-life applications include the use of QR codes in catering industry for self-service ordering, and retail industry for membership rewards programs.
What is “Quishing”?
"Quishing" is QR code used in phishing email. When a user scans the QR code, he/she will then access the phishing website. A US cyber security firm, Abnormal Security conducted a phishing attack drill with its partner in September 2021 in which a .WAV file attached in a phishing email was sent. If the user opens the file, he/she will be re-directed to the phishing website. The attachment was successfully detected and deemed as a threat by the partner. A month later, the drill was repeated but this time the phishing email only had QR codes, which successfully bypassed the security measures of the partner. Since a QR code is an image, current security measures may not be able to detect it as a threat. "Quishing" may therefore become a new normal in the future.
On December 9, 2021, Cofense published a report that two German banks (Sparkasse and Volksbanken Raiffeisenbanken) have been used for "quishing". Hackers pretended to be the banks and claimed that new security measures are being put in place, which require the users to scan the QR codes to examine their bank accounts. However, the QR codes were actually linked to phishing websites requesting for bank account information.
QR code Misappropriation
In October 2021, a diner at a local sushi restaurant uploaded the order QR code to the social media platform. Netizens took advantage to order food in a frenzy, resulting in unnecessary losses.
Security Measures
- Control or restrict to use
- Merchants should regularly check the QR codes in their shops and on their products. For example, they should check if the original QR codes have been replaced with unknown ones. Based on above mentioned case, the restaurant can provide manual ordering or equipment for customers to place orders instead of using a static QR code for ordering. If a restaurant must use QR codes for self-service ordering, the developer can add a random hash to the QR code data to prevent the QR code from being used by non-diners. In addition, every time the diners enter the restaurants, a QR code should be generated and become invalid after the diners settled their bills in order to avoid QR code reuse.
- Encryption of data
- One of the QR code encryption technologies is Secured QR code (SQRC). It is an encrypted QR code which divides information behind the code into public and private parts. On appearance, SQRC is no different from the traditional QR code, but the private part has been encrypted. Using general equipment, such as scanning SQRC with a mobile phone, only the public part of the QR code can be obtained. The encrypted part requires a key and a supporting SQRC device to obtain the information behind it. SQRC can provide data permission control, and only authorised devices can read entire information.
- Anti-counterfeiting
- A digital signature can be used as one of the security measures. When the user scans the QR code, the application will first check whether the QR code is valid or not. Modifying the content behind the QR code will invalidate the digital signature in the QR code. The QR code can be added with digital signature to prevent the QR code from being modified and faked.
- Dynamic QR code
- Dynamic QR codes have better security than static QR codes. Applications that use dynamic QR codes will ask the server to refresh the QR code, and the previously generated QR code will be considered invalid. The dynamic QR code is one-time only and can effectively reduce the risk of QR code being compromised.
- Aging Time
- If the user does not activate and use the QR code within the specified time, the QR code will become invalid and cannot be used again.
- Information Privacy
- The user's personal information and other sensitive information should not be stored in QR codes.
Reference:
[1] https://www.comparitech.com/blog/information-security/what-is-QRLJacking/
[2] https://owasp.org/www-community/attacks/Qrljacking
[3] https://hakin9.org/QRLJacking-new-social-engineering-attack-vector/
[4] https://abnormalsecurity.com/blog/qr-code-campaign-bypass-security
[6] https://cofense.com/blog/german-users-targeted-in-digital-bank-heist-phishing-campaigns/
Related Tags
Share with

