Hong Kong Networks Abused to Host More Than 22,000 Phishing URL
In 2015, HKCERT has handled 1,931 cases on phishing site hosting, accounting for 40% of all security incidents handled. Compared with 594 similar cases handled in the same period last year, the increase is 233%. The surge was caused by a phishing campaign targeting banks in mainland China, by abusing hosting service located in Hong Kong.
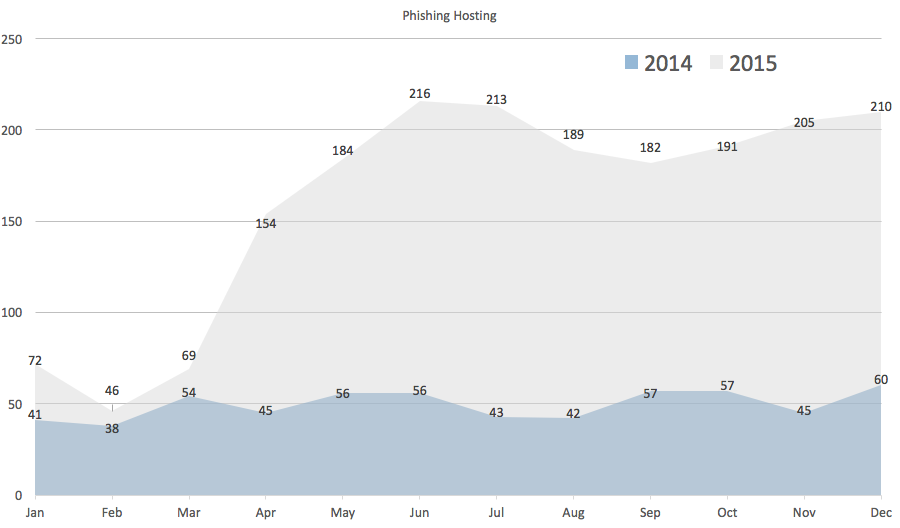
Figure 1: Comparison of phishing site hosting cases in 2014 and 2015
Surge caused by new phishing tactics
The sudden surge of the phishing incidents is caused by a new tactic employed by the cybercriminals:
- These phishing attacks targeted mostly bank customers in mainland China. According to this news article, the end users were tricked to visit the phishing sites through scam SMS or email.
- A large volume of phishing links in those scam messages were hosted on Hong Kong IP addresses. In 2015, about 22,576 URL were resolved to IP addresses in Hong Kong.
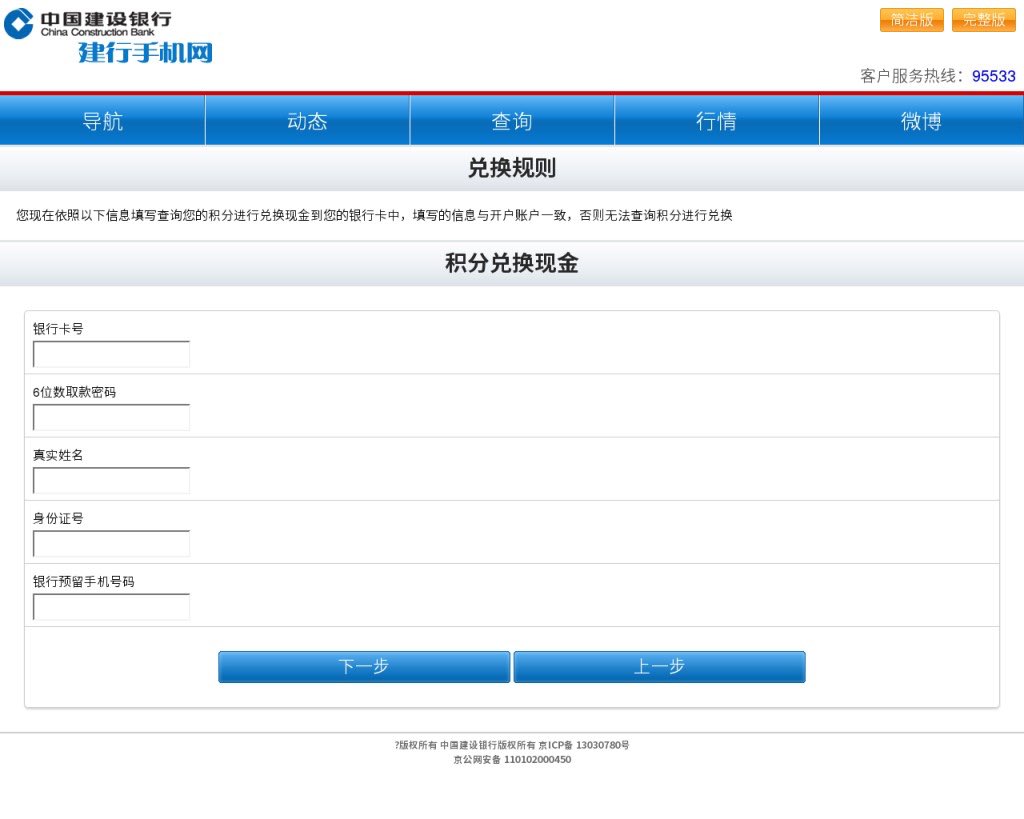
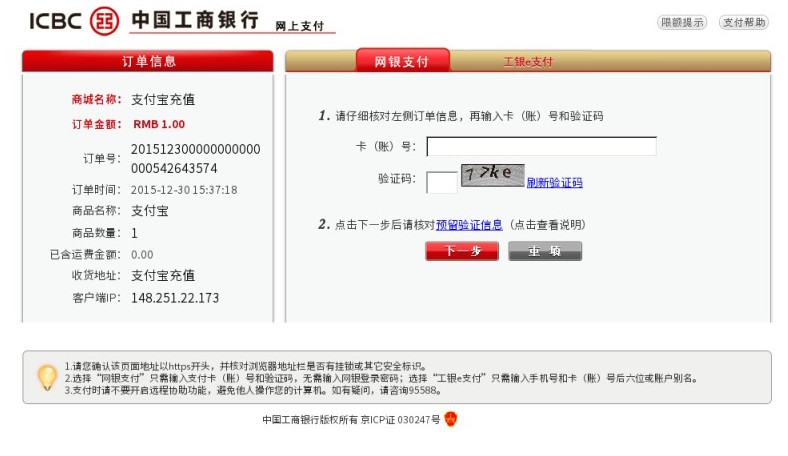
Figure 2: Example screenshots of phishing sites targeting China Construction Bank and ICBC
- The domain names used in the phishing links were formed by randomly picked letters. Only 1 day is needed from domain registration to actually using it for hosting phishing site.
- The cybercriminals found a way to register many domains so that they can maintain their phishing campaign even each domain only lived a few days. Most of these domains became inaccessible within 1 week.
Attention from worldwide authorities
Major banks in mainland China such as China Construction Bank, ICBC, China Merchants Bank, Agricultural Bank of China etc. were targeted in the phishing campaign. Such wide and persistent phishing campaign captured the attentions of many organizations. We have received reports from CNCERT/CC (China), People’s Bank of China and various security service representatives of those banks. Authorities outside China such as JPCERT/CC (Japan) and US-CERT (US) also detected the incidents and had referred incidents reports.
Fake registration information facilitated the network abuse
The main obstacles to effectively stop the campaign are:
- We could not locate the ISP to shut down the phishing sites. A valid contact could not be obtained from the public WHOIS record; even if we could, the ISP was actually located in mainland China, but just rented the networks in Hong Kong, and they usually responded very slowly. HKCERT experienced similar problem half year ago in handling a brute force login attack, in which fake contact information were used in ASN registration.
- The huge number of phishing domains also costed us a lot of resources to handle. We have sought assistance from CNCERT/CC and CNNIC on this issue, as the contacts of registrant and registrar mostly originated from mainland China.
Impact on Hong Kong
The phishing campaign does not target Hong Kong customers. How can it affect users in Hong Kong?
Advices to users
If you plan to find or already subscribed a hosting space, HKCERT advised you to take special note on the following issues:
- If your website or email server is hosted on those networks being abused, they may also be blacklisted (like in this example). Browsers such as Chrome and Firefox also block blacklisted sites by default. When your visitors browse your blocked website they will very likely see the following image:
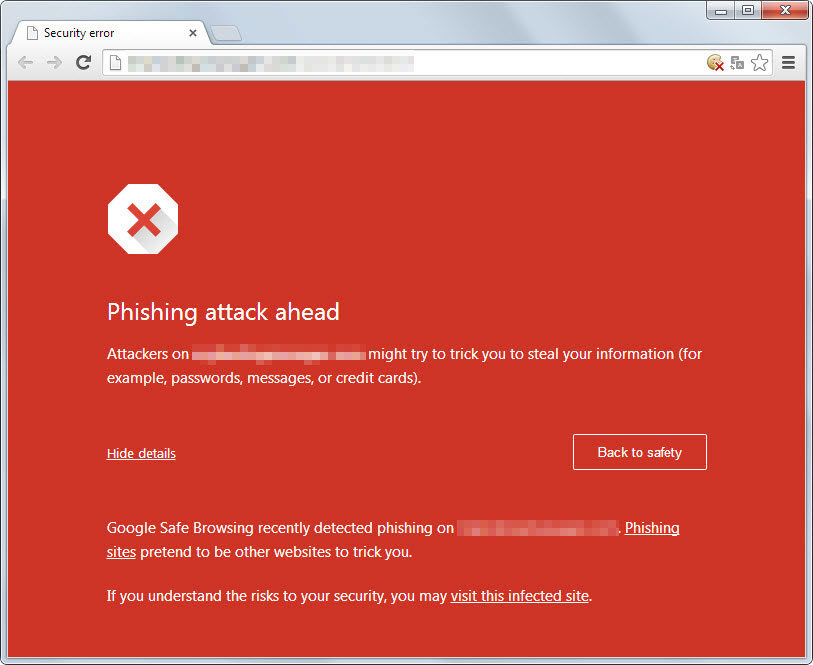
Figure 3: Example screenshot of Google Chrome blocking phishing site
- If any local or overseas law enforcement or authorities decide to take action against the network service providers involved in such campaigns, it is possible that the whole abused network is shut down. This would imply the suspension of your website or your email server, which in turn heavily impacts your business operations.
- There is probably no firewall between your website or email server and hosting space used by the cybercriminals, they can attack your facilities directly. If your network service provider does not clean up, that may imply some management problems of the hosting service.
Advice to service providers
- Please take down the phishing sites as soon as possible, once receiving the notification from HKCERT or security service representatives of the brand owners.
- Please identify or blacklist the customers who likely abused your service.
- If you have any query, please contact HKCERT via [email protected] or hotline +852-81056060.
Share with
