Buying and installing tips for Smart Device
In recent years, Internet and things (IoT) device usage grows rapidly, There are reports that expect the related devices will grow to about 21 billion in 2020, and will exceed the number of personal computers very soon. In last year, hackers noticed that many of these devices had security vulnerabilities or problems. In September and October 2016, hackers intruded many vulnerable devices and conducted a large-scale denial-of-service attack. They used a malicious program called "Miari"#1. The attack told us that the Internet of Things device has become a new generation of network attack tool.
After this incident, a number of security teams began to study the problem of vulnerable devices globally and the results were far beyond imagination. HKCERT also conducted a series of thematic studies#2 on Internet and Internet of Things between 2015 and 2016. It also found that a large number of devices were opened to the Internet directly, and some of them had security vulnerabilities.
What are the problems?
The security issues of Internet and Internet of Things devices include:
- There are vulnerabilities in the system and attackers can perform remote code execution or remote control
- The products only provide a small amount of security features or no security features at the time of shipment
- The product default password is too simple or user cannot change the default password
- There is no obvious advise that the user need to change the default password or need to install a firmware update to fix security issues
It is easy to find a lot of unsecure devices on the Internet, and these devices are deployed in many different environments, including industrial equipment, infrastructure equipment and household equipment and so on. Due to the birth of Miari, these unsecure devices are easily recruited to form a huge botnet, and can issue large scale denial-of-service attack to block operation on targeted internet service.
End users also can also contribute
In fact, as a end user, we can also contribute to the security of the internet. We can start from product selection and installation. Let us provide some tips to you.
To select the product, you need to:
- Understand the brand's credit
- Understand the product issues and handling methods of vendor in the past two years
- Understand the frequency of firmware update provided by the vendor
- Whether the product has an official verification#3
- Make sure the network connection is using encryption
- You can download the user manual to find out if enough security controls are provided
- Make sure the management interface is using encryption
- The device is easy to update the firmware
- The device is easy to install
Regarding device installation you should:
- Install in internal network, not connecting the internet directly
- Separate trusted and untrusted network. If possible establish an additional separate network for smart devices
- Disable the Universal Plug and Play (UPnP) function on the router
- Keep the firmware up-to-date, check at least twice a year whether the manufacturer's website has new firmware updates
- Use a strong password and change it regularly. If possible use one password for one device
- Management interface should not open directly on the Internet. Only open necessary service
- If the device is not necessarily connected to the cloud, please disable it. Enable cloud connection will increase security risk
- When internet service is not in use (such as SmartTV), unplug the network connection
- Use the search engine (such as Google) regularly. Try to enter the equipment brand name and model to search if there are any security issues.
To enjoy the benefits of new technology, we need to pay attention to security. So we can have peace of mind.
Additional information
#1
If you want to learn more about this malware, you can browse "Mirai Malware Cleanup and Prevention"
#2
If you want to learn more
- Some Home routers in Hong Kong prone to security issues
- Security of Hong Kong Home Routers
- Vulnerabilities in Hong Kong Internet Devices
- Security Risks of Network-Attached Storages (NAS)
- Security Risks of Networked Industrial Control System (ICS)
#3
Related to communication encryption and product certification
The smart devices are generally divided into two types, one can operates independently or one need connect smart gateway to operate. Independent operating smart devices are mainly using Wi-Fi connection, some others may use Bluetooth. They are using IEEE 802.11 communication standards with encryption technology. For the other type that need to connect smart gateway, they are divided into two parts. One is device-gateway connection and other is gateway-router connection. Device-gateway connection will use emerging IEEE 802.15.4 communication standards and mainstream is using Zigbee or Z-Wave protocols. Because this communication protocols are relatively new, encryption option may not be available for early products. The gateway-router connection is generally using Wi-Fi, the situation same as Independent operating device. But because the smart gateway will be connected to the cloud, you can check whether the connection is using encryption properly. See the diagram below.
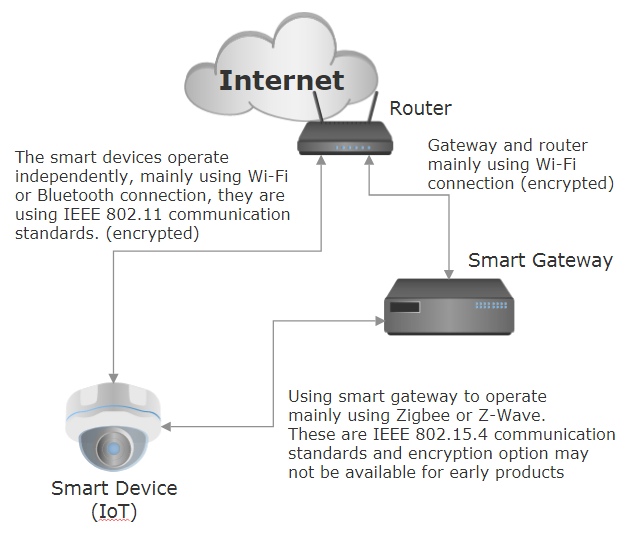
It is recommended to purchase products that are certified and newer.
The following information is Zigbee and Z-Wave's certified products trademarks and Verify website:

http://www.zigbee.org/zigbee-products-2/

Share with
