IoT Device (Webcam) Security Study
Background
Today, more and more gadgets, devices and systems are connected to the Internet. Known as the “Internet of Things (IoT)”, this trend has made networked connections more meaningful through greater convergence of people, processes, data and many things else. By turning information into action, new capabilities, richer experiences and unprecedented economic opportunities for individuals, businesses and the community have come about as a consequence.
Yet, our growing dependence on Internet applications has made us more vulnerable to cyber attacks involving IoT devices in recent years.
For example, towards the end of 2016, there was a large scale distributed denial-of-service (DDoS) attack launched by an IoT botnet - Mirai. The Mirai malware scanned the Internet for telnet servers, then attempted to login and infected the IoT devices by exploiting a list of hard-coded passwords. Most of the passwords corresponded to Internet connected CCTV systems and routers.
Last year, researchers discovered another IoT botnet Reaper. Created partially based on the code of Mirai, it can spread through different vulnerabilities of IoT devices. Although Reaper is still spreading in a dormant way today with unknown intention, it is found to contain an update mechanism for the attacker to turn it into an offensive weapon at any time.
Recently more sophisticated botnets based on Mirai have also come to the fore. The attack of these botnets can be cross-platform (e.g. attack other Linux platforms) or aims to leverage the processing power of the IoT device to perform activities such as crypto-mining.
IoT Device (Webcam) Security Study
Among all IoT devices, webcam is one of the most popular IoT devices used in Hong Kong. However, these devices may not be installed securely in household.
In August 2016, there was a public uproar over an exhibition in the UK showing still images of webcams from around the world, including Hong Kong, as the images were collected without the webcam owners’ consent, seriously infringing their privacy. While such action was wrong, two points were highlighted from this incident:
- Security awareness of people to protect personal privacy needs to be raised.
- Security controls of webcam should be reviewed.
These are the reasons behind this Webcam study by the Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) of the Hong Kong Productivity Council.
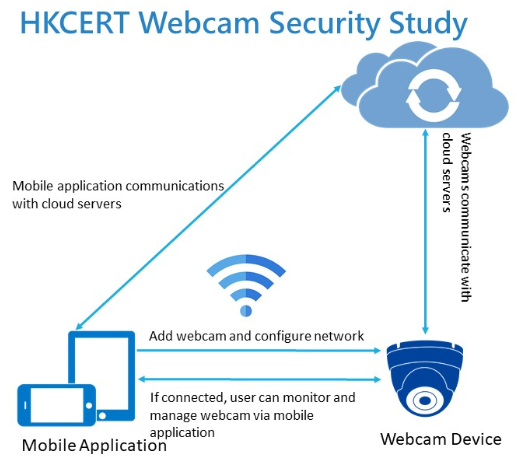
The objective of the study is to assess the security level of common webcams available in Hong Kong. HKCERT selected 10 webcams of commonly available brands in the fourth quarter of 2018, some featuring a mobile application and a cloud-based server service. HKCERT adopted a technical approach to test three security aspects of the webcams, namely:
- Security of the mobile application (if available)
- Data transmission security between the webcam, mobile application and cloud server (if available)
- Security of the webcam itself
Findings
1. Mobile Application Security
- Over half of the webcams (6 out of our 10 samples) tested come with a mobile application to manage and view images of the webcam. While these mobile applications require login ID (username) to identify users, most of them do not have password complexity requirements, i.e. users can use simple password like “123456” or “password”, etc. as login password.
- Besides username and password, all webcam mobile applications do not provide strong authentication scheme like 2FA (Two-Factor Authentication). During our test, only one webcam was found to feature the good security practice of re-authentication (using existing password) when changing to a new password.
- One good practice found in most mobile applications tested was that they did provide brute force attack protection such as delaying login response when they encountered multiple login failures.
2. Data Transmission Security
- When examining the network traffic, most data transmissions between mobile applications and webcams are found unencrypted. Perhaps, the developers were assuming that the mobile applications were talking to the webcams in a secured local network, thereby making encryption not important? It is a good practice to assume the network is hostile in nature and enforce encryption where possible. In our study, we managed to obtain the password in 2 webcams from unencrypted traffic in local network.
- However, most traffic between mobile applications and cloud servers were encrypted. This may be due to enforcement of HTTPS connections in mobile applications from mobile platform developer likes Google and Apple.
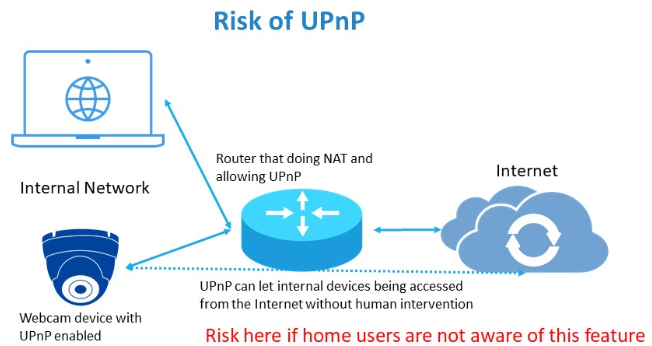
- Some webcams also had their Universal Plug and Play (UPnP) function enabled permanently. UPnP is a set of network protocols that permits networked devices discover each other’s presence on the network. Given that UPnP has a long history of security vulnerabilities, if the Internet gateway router has enabled UPnP by default, the webcam would be exposed to the Internet without the user’s knowledge. (See appendix for problem of UPnP).
3. Webcam Device Security
- Most webcams (8 out of 10 in our samples) have open port that can be exploited in the network. Many of them had a web interface that required username and password to login. However, some can login with default username/password, such as “admin” or “password”. One webcam can even login by Telnet without using username and password while several of them (3 out of 10 in our samples) did not have brute force attack protection.
- The good thing was, some webcams (2 out of 10 in our samples) did not have open ports discovered in network and they could avoid common network attack.
Recommendations
1. End Users
- Purchase webcams from official channels. Select those webcams with firmware upgrades and bug fixes.
- Change the default password of webcam when using it the first time. Password should be changed regularly with complexity. Do not reuse the same password in mobile applications. Complex password may be something like “dfgP94$Z”.
- Ensure the network used by webcam to be secure. For Wifi, use WPA2/WPA3 encryption. Do not monitor or administrate the webcam in public network.
- Download the mobile application for webcam only from official app stores. Do not use mobile application from unknown source.
- Check the webcam settings regularly. If settings are changed unexpectedly, reset the account of webcam immediately and keep on monitoring.
- Disable UPnP function in broadband router.
- Update firmware of webcam to the latest version.
- Do not set the webcam to monitor private or sensitive areas. Turn off the webcam when not in use.
- Regardless of the connection method used (such as RTSP, HTTP(S)), the authentication function should be enabled.
- Beware of security alerts of webcams.
2. Product Developer
Apply Security by design to tighten security measures:
- Enforce change of default password for user using the webcam for the first time
- Enforce password complexity, e.g. at least 8 characters long and must include upper and lower cases characters, digits and special characters.
- Enforce Two Factor Authentication
- Prevent brute force attack, e.g. lockup the account when password failed for 10 times
- Ensure the encryption of both data and password in transmission.
- Make UPnP an option to disable.
- Do not open unused network ports.
- Enforce password complexity for terminal password and restrict terminal access rights.
- Keep release security patches of webcam. Keep firmware of webcam up-to-date.
Summary
- IoT attacks are on the rise as the number of IoT devices continue to grow in the coming years.
- Webcam is one of the IoT devices that is commonly exploited by hackers.
- Study by HKCERT indicated contrasting security level of webcams that are commonly available in Hong Kong shops
- Users need to exercise caution in webcam selection. Need to choose webcams with good security features carefully.
- Webcam developers can do more to improve the security of their products.
Appendix – Risk of UPnP
Share with
