Personal Internet Service Account Security Management Guideline
To prevent your personal information stolen by hackers, account management is very important. Using a strong password can help to against brute force attack launched by hackers. However, nowadays, a strong password is not enough to protect your account from cyber criminals. HKCERT advises users to take the following suggestions to improve security in personal Internet service account management, and web / software developers to enhance the protection of their customer's account information.
Threats of personal account - Phishing
Nowadays, cyber criminals usually lure users to input login information through phishing. They launch many kinds of phishing attacks. For instance, they send you a phishing email which redirect you to a phishing site and lure you to input login information; some websites would ask for your social account to unlock partially hidden contents.
Emerging many kinds of phishing, users should pay special attention and be cautious before entering account information. In addition, HKCERT provides the following information for users to improve the management of personal account.
Suggestions on Personal Account Security Management
1) Use 2-factor authentication / 2-step verification
2-factor authentication or 2-step verification requires a user to input 2 sets of information of different nature for user authentication. Usually it is a combination of something you know and something you have (e.g. Security token, mobile phone). For example, when you perform a login process on a platform, the platform requires you to input username and password (something you know). Then you will be asked to authenticate using something you have. This is usually in 2 forms: (1) It may be a mobile phone, via a one time password sent by SMS to your phone. (2) It may be a security token app installed on your mobile phone, via a unique OTP generated by this token.
To enable 2-factor authentication / 2-step verification feature, users are required to activate the service on your service platform. Because of the differences of 2-factor authentication / 2-step verification features among the platforms, users should understand the operation before activating the service.
Information on 2-factor authentication / 2-step verification features of different platforms is listed below.
- Facebook: https://www.facebook.com/help/413023562082171
- Google: https://www.google.com/landing/2step/
- iCloud: https://support.apple.com/en-us/HT204152
- Microsoft: http://windows.microsoft.com/en-hk/windows/two-step-verification-faq
- Twitter: https://support.twitter.com/articles/20170388
- Yahoo: https://help.yahoo.com/kb/SLN5013.html
Some Internet services supports using hardware for 2-factor authentication. To enable the hardware 2-factor authentication feature, users need a specified hardware, FIDO U2F security key. Currently, this feature is commonly supported for Google account sign-in on Chrome (ver. 40 or above) browser.
Please refer to the articles about Google supporting FIDO U2F security key:
- https://support.google.com/accounts/answer/6103523
- https://fidoalliance.org/google-launches-security-key-worlds-first-deployment-of-fast-identity-online-universal-second-factor-fido-u2f-authentication/

Fig1) FIDO U2F Security Key
2) Use App Passwords / Temporary Passwords
Nowadays, many websites (or applications) support federated login using OAuth protocol. With OAuth, a user does not need to sign-up an account for each website. He only logins to a specific service account that supports OAuth, such as Facebook, Google, Microsoft, Twitter, and Yahoo account, then he is able to be authenticated without the need of signing up as a member. Using OAuth login process, the websites have the authentication token of the service account only. They do not know the user's original username and password.
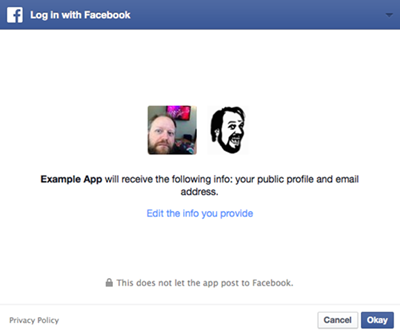
Fig2) Login interface using Facebook OAuth
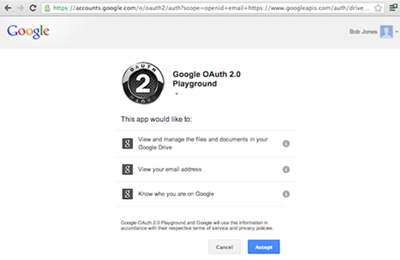
Fig3) Login interface using Google OAuth
Unfortunately, some phishing websites pretend to be an OAuth login interface and lure users to input login information. To avoid leaking the password of the internet service account, the internet services supporting OAuth also have a feature called App Passwords or Temporary Passwords. Users can generate an independent and one-time password for each website and each application. This App Password is totally different from the password of the service account. Even if the App Password is stolen, the original account is not affected.
App Passwords feature of different platforms:
- Facebook: https://www.facebook.com/help/413023562082171
- Google: https://support.google.com/accounts/answer/185833
- Microsoft: http://windows.microsoft.com/en-hk/windows/app-passwords-two-step-verification
- Twitter: https://support.twitter.com/articles/20170388
- Yahoo: https://help.yahoo.com/kb/generate-separate-password-sln15241.html
3) Monitor suspicious login attempts
Some Internet services provide notifications for suspicious login attempt. It sends an email and/or SMS to you if the system detected a suspicious login attempt. Also, pay attention to login alerts generated by Internet services. They may indicate someone attempting to break in your account.
4) Use different passwords for different services
Some users usually use the same set of password for different account. This is highly not recommended, as when one of the accounts is stolen, the hacker will try using the same password to login other common services. For example, a hacker successfully steals a social network account, and he will try to use the same password to login other services, like email service, online banking, etc. This will cause a chain of influence. So, we suggest users not to use the same password for different services.
5) Remember to sign-out
To avoid leaving your record on the computer, except your personal computer, you should sign-out the service after use. Do not use "Remember password" option on public computer. Users can use "incognito" or "private" mode when browsing. To ensure no browsing history left, you should remember to close all browsers after use.
6) Remove unused account permanently
For the older or not commonly used services, the account management for users may be insufficient. It becomes easier for hackers to steal the accounts. Thus, we suggest users remove the not commonly used accounts, in order to reduce the risk of account being stolen.
7) Think twice before entering the password
To reduce the risk of account being stolen, the most effective way is to improve security awareness. Users should be particularly vigilant before entering the password every time. If in doubt, users should not enter any account information until further verifying the service.
Suggestions on Storing passwords for Website / Software developer
Web / Software developers also need to carefully handle user / customer account information. Not only do they need to follow the Hong Kong Personal Privacy Ordinance1, they are also responsible for providing a degree of security to information from their users / customers. Therefore, HKCERT proposes the following guideline to developers.
- Do not store plain password in database
- Password should be hashed and stored using strong hash function like bcrypt with salting.
#Remark: MD5 and SHA1 are considered as insecure hash functions. - Consider to use multiple times of hash (Iterations) on password
- Limit the number of password attempts in the system
- System should provide login history for users
- Evaluate the system through security assessment regularly. Avoid database from being hacked due to the common vulnerabilities, like SQL injection.
Please refer to articles about securely storing passwords:
- https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet
- https://patrickmn.com/security/storing-passwords-securely
https://www.pcpd.org.hk/english/data_privacy_law/ordinance_at_a_Glance/ordinance.html
Share with
