Watch out for "WannaCry" on the Linux platform
Release Date: 29 May 2017
2369 Views
While the impact of WannaCry worm to Windows users is still so fresh in memory, a similar vulnerability of the Samba service was discovered in Linux platform. This newly discovered remote code execution vulnerability (CVE-2017-7494) affects all versions newer than Samba 3.5.0 that was released on March 1, 2010. It is commonly known as SambaCry.
What is Samba service?
Samba is an open-source software that runs on the majority of operating systems. It allows non-Windows operating systems, like GNU/Linux or Mac OS X, to share network folders and network printers, and use the same TCP 445 port as the Windows SMB service.
How to exploit?
Exploit the vulnerability is very simple. The exploit code is only one line, provided the following conditions are met:
- The server has opened TCP port 445
- “Write” privileges to the network folder on the server is granted
- The file path on the server is known or can be guessed
When all the conditions are met, the remote attacker can upload arbitrary code and cause the server to execute, and get the root privileges of the server. If a Samba server open direct access to the Internet, the attacker may exploit it remotely.
Our Center had issued a security bulletin for this vulnerability:
The situation in Hong Kong?
We tried to search via the Shodan Internet device search engine and found that there were 349 devices in Hong Kong having potential security problems. This is worth our attention.
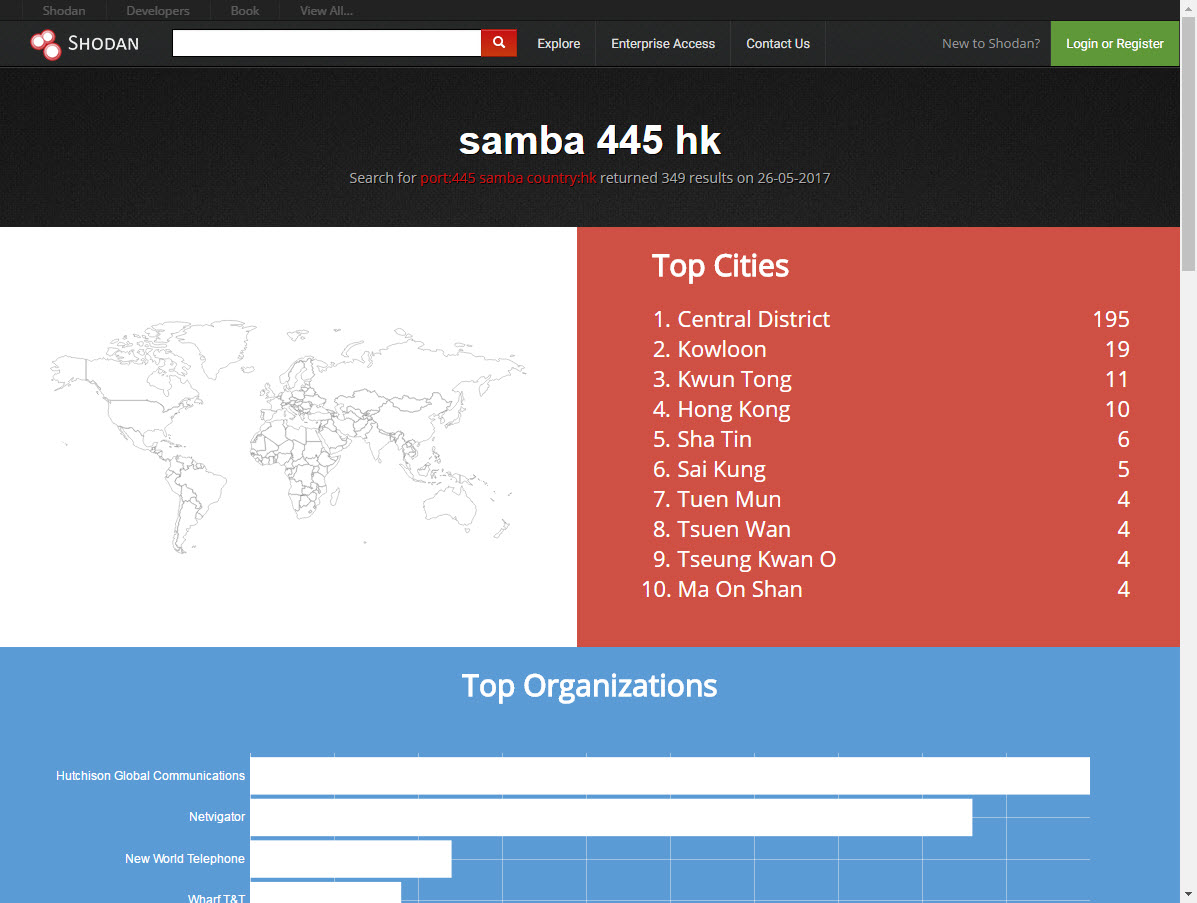
Please refer to https://www.shodan.io/report/ion4k1BS
Conclusion
As the vulnerability of the exploit code has been published, and the difficulty of the attack is extremely low, we cannot take it lightly. Many networks attached storage devices, such as Synology or QNAP that are popular are also affected. Please check for the devices whether security update is available and install as soon as possible. If you set up your own Samba, please install security patch as soon as possible.
If you cannot apply security patch immediately, you can add the following settings to the smb.conf configuration file and restart the Samba service to temporarily stop the problem.
- nt pipe support = no
Share with
