Be Aware of Spam Emails spreading Jaff Ransomware
While the world's attention is focusing on the WannaCry ransomware, another ransomware, called Jaff, is spreading through massive spam emails.
HKCERT would like to alert the public to be aware of spam emails, not to overlook the threat. As of today, one Jaff infection report was received.
Propagation by Spam Campaign
The spam campaign was first observed on 11 May. Observed email subjects include the following:
- Copy_[Random Numbers]
- Document_[Random Numbers]
- Scan_[Random Numbers]
- File_[Random Numbers]
- PDF_[Random Numbers]
- Scanned Image
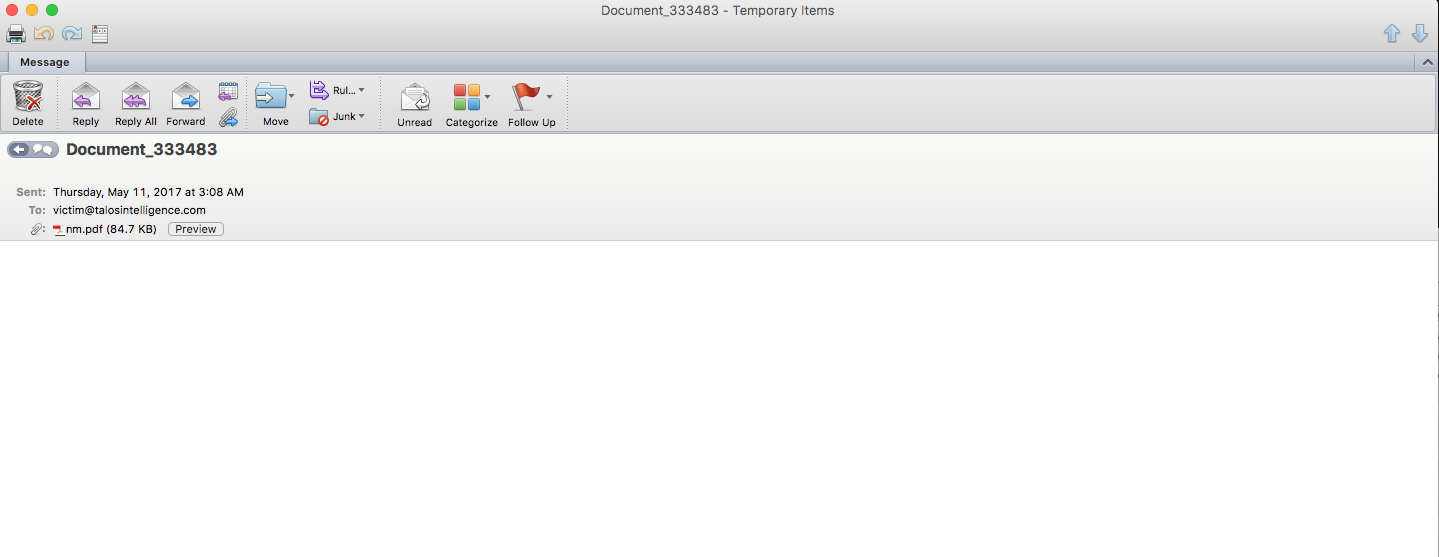
The email contains a short or even no message body, with a malicious pdf attachment named nm.pdf or [Random Numbers].pdf.
The infection Process
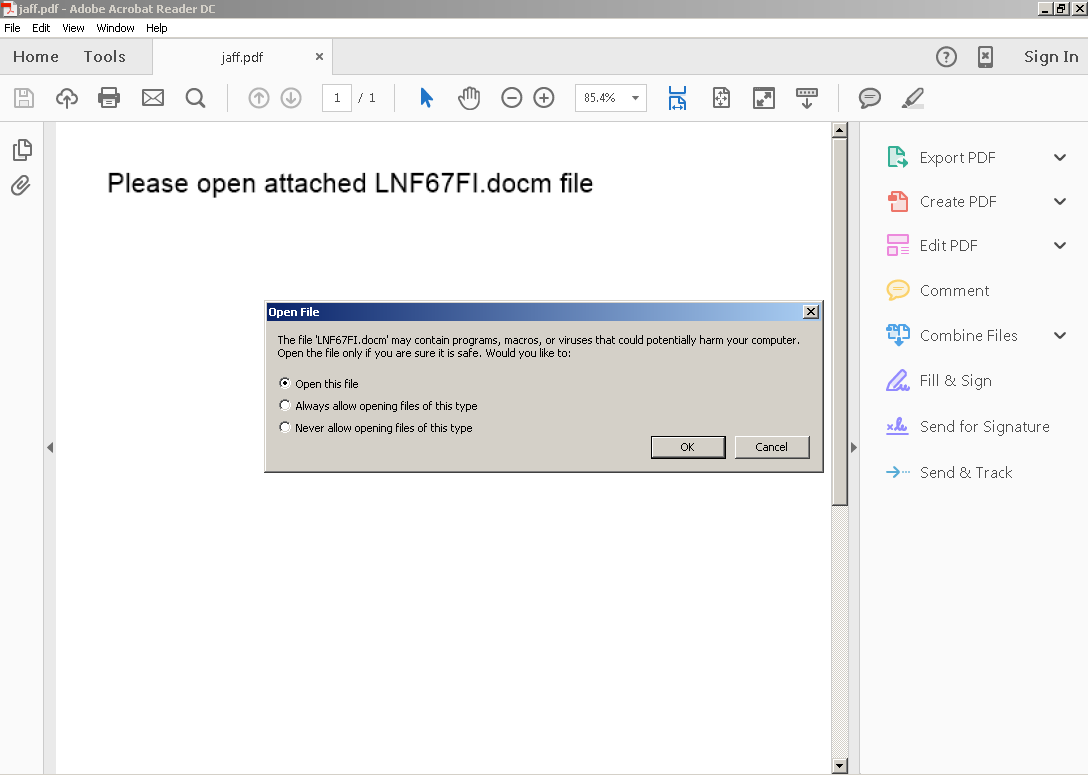
The infection process requires several user interactions, the user would need to open the malicious pdf file to start the process. The pdf then would ask the user to open the embedded Microsoft Word document.
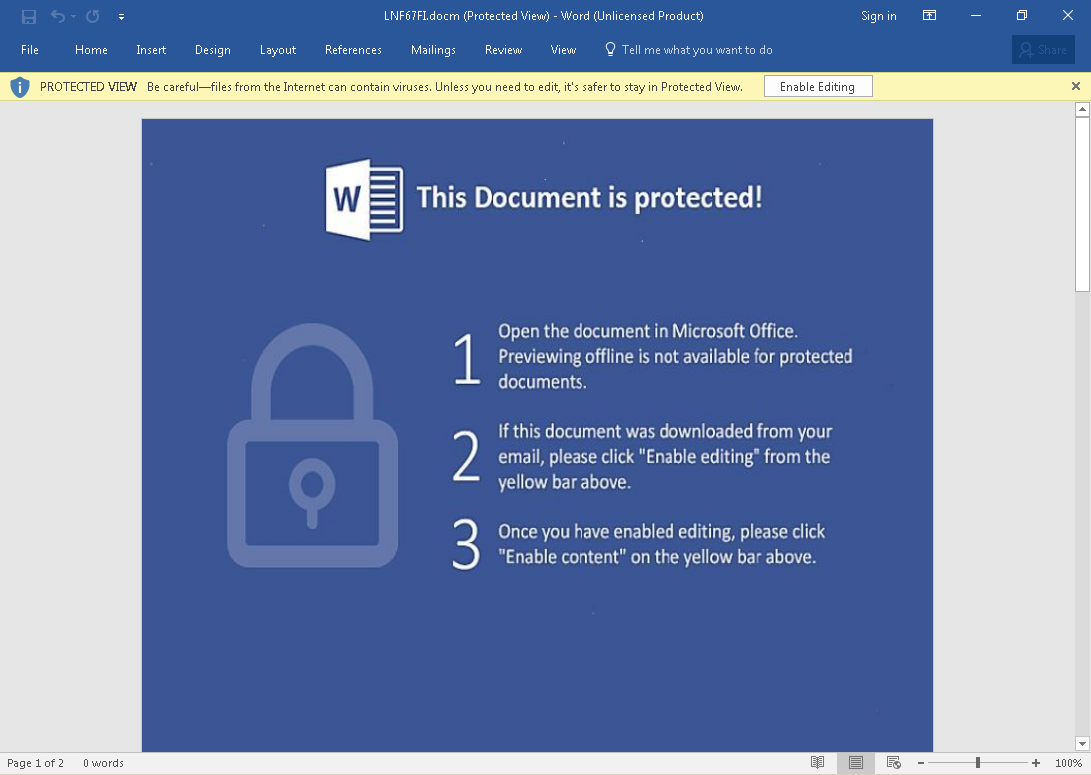
Once the document is opened, it will further ask the users to Enable Editing in order to view the content.
Once the content is enabled, it would download and install the actual ransomware to infect the computer.
Jaff ransomware will then start to encrypt user files in the computer. A ransom note will be shown when the encryption is finished.
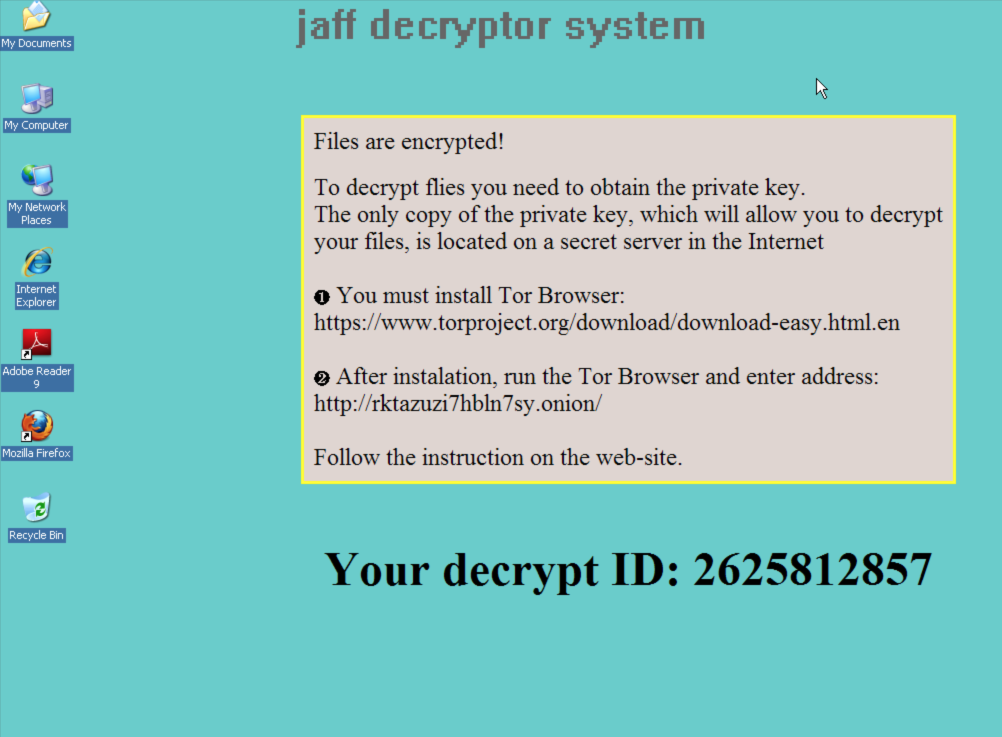
Jaff ransomware asks for about 2 bitcoins ransom in exchange of the decryption key. The ransom worths more than 28,000 HKD as of writing.
Mitigating Risks of Jaff Malware
Users are advised to take these steps to mitigate the risks:
- Regularly backup data stored on your computer, and keep an offline copy of the backup.
- Delete any suspicious-looking emails you receive, especially if they contain links or attachments.
- Always keep your security software up to date.
- Keep your operating system and other software updated.
- Install security software
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Do not enable it if in doubt.
- Once infected, isolate the infected computer from the network and external storage immediately. Do not open any file before clearing the malware.
- Do not pay the ransom.
Reference
Share with
