Should we worry about the Android "QuadRooter" Vulnerabilities?
On August 7 2016, Check Point disclosed details of four vulnerabilities (code name “QuadRooter”) of the Qualcomm chipsets at the hacker conference DEFCON 24 and attracted global attention. HKCERT also issued a security bulletin for it with extremely critical severity level. However, users do not need to be over worried at the moment because there is no evidence of these vulnerabilities are being exploited in the wild or being packaged into functional malware at the time of publication. The problem is expected to be fixed when the mobile device manufacturers release the updates.
Why is QuadRooter a severe problem?
The problem was believed to affect 900 million Android devices using the Qualcomm chipset. If any one of the four vulnerabilities is exploited, an attacker can obtain full control of devices and unrestricted access to all data in the device, including sensitive personal information. At the time of publication, no Android device manufacturer claimed to patch all security holes. This was why HKCERT issued a security bulletin for it with extremely critical severity level. In 2016, HKCERT had issued 10 security bulletins with “extremely critical” severity level, including two for ransomware and four for Adobe Flash.
Affected Android Devices
65% of LTE modem baseband Android devices use the affected vulnerable Qualcomm Chipsets, including some popular Android devices:
- BlackBerry Priv
- Blackphone 1 and Blackphone 2
- Google Nexus 5X, Nexus 6 and Nexus 6P
- HTC One, HTC M9 and HTC 10
- LG G4, LG G5, and LG V10
- New Moto X by Motorola
- OnePlus One, OnePlus 2 and OnePlus 3
- Samsung Galaxy S7 and Samsung S7 Edge
- Sony Xperia Z Ultra
Is my Android device at risk?
You can install the “QuadRooter Scanner” app provided by Check Point from the Google Play Store to check if your device is affected.
URL: https://play.google.com/store/apps/details?id=com.checkpoint.quadrooter
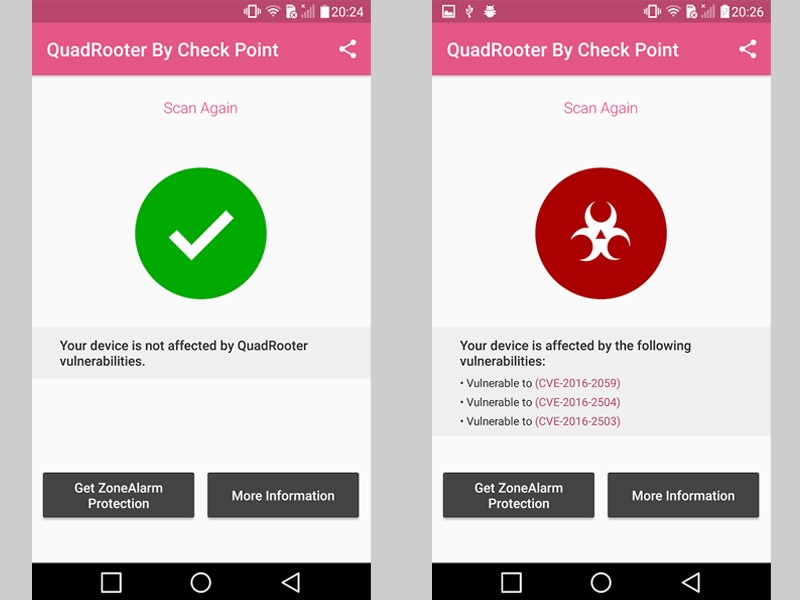
Progress of patch development for QuadRooter
Qualcomm has released all four fixed driver packs. Google has provided the security patches on three of the four vulnerabilities in the Android system in the August 2016. The last one is expected to be fixed in the September patch. Because the mobile device manufacturers and distributors have customization over the generic Android system, users have to wait for the firmware update provided by the device manufacturers accordingly.
- Updated on 2016-09-08:
Google has released fixes for two remaining vulnerabilities (CVE-2016-2059 and CVE-2016-5340).
https://groups.google.com/forum/#!forum/android-security-updates
Below is the patch deployment flow in the Android ecosystem.
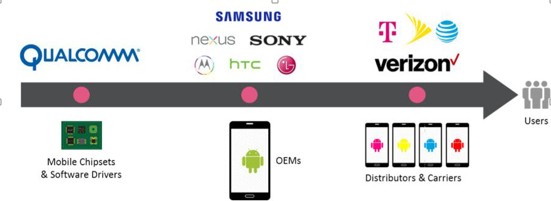
Vulnerability Patching Ecosystem in Android Devices (Reference from: www.checkpoint.com)
In July 2015, a similar extremely critical vulnerability for Android name “Stagefright Media Library Remote Code Execution” (/my_url/en/alert/15072901) had similar situation. Even though Google had provided patches to the vulnerabilities, it took some time for various device manufacturers to deploy the firmware.
Defending against the exploit of malicious mobile app
Even if your Android device has one or more of the four vulnerabilities, it does not have immediate problem unless you are lured by the attacker to install a malicious mobile app to exploit the vulnerabilities.
Google claimed that the “Verify Apps” feature of Android is able to block QuadRooter. When a malicious app exploiting QuadRooter is installed, Android will display a message "Installation has been blocked" and ban the installation. This should happen on all Android devices running 4.2 and up with Google Play Services. This feature is enabled by default in all Android versions 4.2 Jelly Bean (since 2012) and it is kept updating. As of the most recent stats available, more than 90 percent of active Android devices are running version 4.2 or later. You can enable this feature manually in old version. And on older versions of Android going back to 2010's Gingerbread release, you can enable Verify Apps under "Security" in the Google Settings app.
Security Advices
Users are advised to install firmware with security update when it becomes available. Before the problem is fixed, users should stay vigilant on mobile app installation and updates.
- Download and install the latest Android firmware updates as soon as they become available. These include important security updates that help keep your device and data protected.
- Avoid side-loading Android apps (.APK files) or downloading apps from third-party sources. Instead, practice good app hygiene by downloading apps only from trusted vendor in Google Play.
- Do not use unknown public Wi-Fi networks to install and update Android apps
- Use Android security apps to protect your devices to block the install of malicious and unwanted apps, even if they come from Google Play.
Share with
