Compromised RDP Servers in Hong Kong Sold in xDedic Underground Marketplace
On 15 Jun 2016, security researchers of Kaspersky announced an operation to take down an underground marketplace called ‘xDedic’ which is for trading compromised servers with remote desktop protocol (RDP servers) 3. Some Hong Kong servers were on the list, and HKCERT is working with Kaspersky to handle them.
xDedic website (source: Kaspersky)
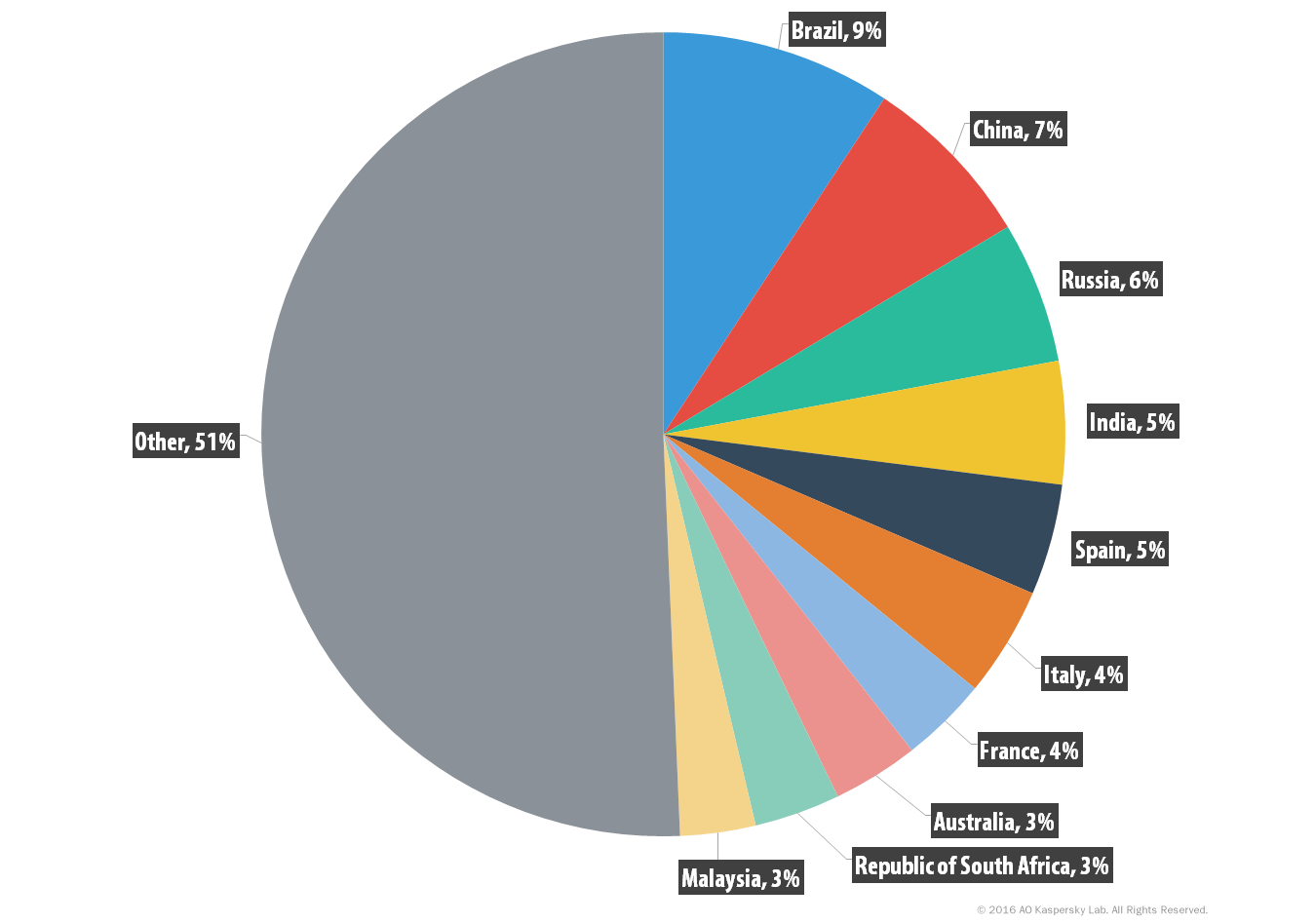
The researcher found that the compromised servers belong to ordinary corporations, educational institutes and even government departments around the world. The marketplace let hackers trade the RDP server compromised by them at as low as US$6.
Top countries with servers on sale (source: Kaspersky)
Servers in Hong Kong also found traded in xDedic marketplace
HKCERT has obtained a list of 160 compromised server IP addresses in Hong Kong. Since we do not have any clue on the usage of those compromised servers, which may involve financial or sensitive data, we already notified the related ISP today. We have urged the ISP to contact their customers as soon as possible, since their customers might encounter serious data leakage.
Security risks of servers being traded in xDedic marketplace
A number of software was installed in the compromised servers for the buyers (who paid to take control of the compromised servers) to take benefits:
| Software installed on compromised servers | Security impacts |
| SCCLIENT trojan and some other patches with registry modifications | Servers are controlled by the buyers to perform illegal activities such as fraudulent transactions, impersonating identity to login online services with stolen credentials, sending spam, or launching DDoS attack. |
| Brute force tools | Brute force and compromise more servers for sale |
| Bitcoin mining tool | Exhaust processing power |
| POS malware (on servers believed to be point-of-sale terminals) | Theft of financial data such as credit card information |
Besides, the buyers might also be able to access any computer in the same network as that of the compromised server, which could mean that there might be was potential data leakage from other computers in the organization.
How to detect servers compromised for trading
You can check whether your servers have been compromised by detecting the following malwares:
- SCCLIENT Trojan (/Windows/System32/scclient.exe), also registered as a service
- xDedic Socks System (\AppData\Local\Temp\pxsrvc\pxsrvc.exe)
- Tools such as DUBrute and XPC (detected as Hacktool.Win32.Bruteforce) for brute force attacking other servers
Please note that the buyers would have different usages on different compromised servers. So even if you cannot find the above malware, you should check if other malwares are detected.
How to handle compromised servers
- If you receive notification or detect that your server has been compromised for xDedic trading, please isolate it from the network immediately.
- The buyers could have installed anything or make any modification on the servers. It could not be guaranteed that the servers are threat-free even after you have removed any malware found. It is recommended that you should wipe and re-install the server OS from scratch.
- If your servers have software which process financial or sensitive data, please evaluate the risk of financial/sensitive data leakage, and even consider escalate the issue according to your organization policy.
- Please also check the computers/servers on the same network. When necessary, please also evaluate the risk of data leakage from these computers/servers. Mitigation or remediation procedures (e.g. scanning of the computers/servers, reset all user passwords etc.) should also be carried out.
Prevention of incidents involving RDP servers
Apart from xDedic attack, we receive from time to time incidents (e.g. ransomware infection) involving RDP servers. From our experience, many of these incidents were caused by insecure configuration such as improper access control, weak password, insufficient restriction on public access etc. Many of these incidents could be avoided by tightening their security in the first place. HKCERT urges server administrators to take measures to strengthen the protection of their systems, including deploying a firewall, applying minimum access permission to servers, changing default settings, setting up strong password and patching the systems regularly. Here are some useful references as the starting point:
- http://wikisites.cityu.edu.hk/sites/netcomp/articles/Pages/Hardeningstepstosecureremotedesktopaccess_1.aspx
- https://security.berkeley.edu/resources/best-practices-how-articles/securing-remote-desktop-rdp-system-administrators
Reference
Share with